 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
People’s Republic of China State-Sponsored Cyber Actors Exploit Network Providers and Devices
Original release date: June 7, 2022
CISA, the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) have released a joint Cybersecurity Advisory (CSA) to provide information on ways in which People’s Republic of China (PRC) state-sponsored cyber actors continue to exploit publicly known vulnerabilities in order to establish a broad network of compromised infrastructure across public and private sector organizations. The advisory details PRC state-sponsored targeting and compromise of major telecommunications companies and network service providers. It also provides information on the top vulnerabilities associated with network devices routinely exploited by PRC cyber actors since 2020.
CISA, NSA, and the FBI encourage organizations to review People’s Republic of China State-Sponsored Cyber Actors Exploit Network Providers and Devices to learn about PRC tactics, techniques, and procedures and to apply the recommended mitigations.
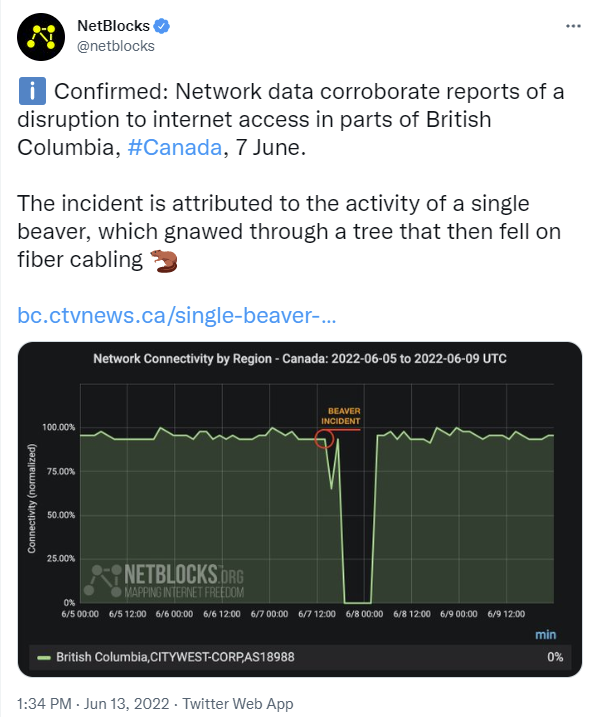
Beaver Kills Internet in Western Canada
Usually its squirrels if rodents are disrupting communications or electrical power.
Know your enemy! Learn how cybercrime adversaries get in…
[Bob says this is a great, must-read article and report from Sophos]
Here’s how 144 recent attacks actually went down in real life. Don’t let this happen to you!
Sophos expert John Shier dug into the incident reports of 144 real-life cyberattacks investigated by the Sophos Rapid Response team during 2021.
What he found might not surprise you, but it’s vital information nevertheless, because it’s what really happened, not merely what might have.
Cybercriminals use automated bot to bypass 2FA authentication at wide scale
Cybercriminals are bypassing two-factor authentication using fraudulent online bot services automating phone calls, targeting multiple countries. Read more about how to protect from this threat.
BABY YOU CAN DRIVE MY CAR —
Gone in 130 seconds: New Tesla hack gives thieves their own personal key
You may want to think twice before giving the parking attendant your Tesla-issued NFC card.
SSNDOB Market domains seized, identity theft “brokerage” shut down
The online identity “brokerage” SSNDOB Market didn’t want people to be in any doubt what it was selling.
Smartphones and Civilians in Wartime
Interesting article about civilians using smartphones to assist their militaries in wartime, and how that blurs the important legal distinction between combatants and non-combatants:
The principle of distinction between the two roles is a critical cornerstone of international humanitarian law—the law of armed conflict, codified by decades of customs and laws such as the Geneva Conventions. Those considered civilians and civilian targets are not to be attacked by military forces; as they are not combatants, they should be spared. At the same time, they also should not act as combatants—if they do, they may lose this status.
The conundrum, then, is how to classify a civilian who, with the use of their smartphone, potentially becomes an active participant in a military sensor system. (To be clear, solely having the app installed is not sufficient to lose the protected status. What matters is actual usage.) The Additional Protocol I to Geneva Conventions states that civilians enjoy protection from the “dangers arising from military operations unless and for such time as they take a direct part in hostilities.” Legally, if civilians engage in military activity, such as taking part in hostilities by using weapons, they forfeit their protected status, “for such time as they take a direct part in hostilities” that “affect[s] the military operations,” according to the International Committee of the Red Cross, the traditional impartial custodian of International Humanitarian Law. This is the case even if the people in question are not formally members of the armed forces. By losing the status of a civilian, one may become a legitimate military objective, carrying the risk of being directly attacked by military forces.
New ultra-stealthy Linux backdoor isn’t your everyday malware discovery
Symbiote gives remote access to any account. Normal methods don’t detect it.
Researchers have unearthed a discovery that doesn’t occur all that often in the realm of malware: a mature, never-before-seen Linux backdoor that uses novel evasion techniques to conceal its presence on infected servers, in some cases even with a forensic investigation.
What makes Symbiote different from other Linux malware that we usually come across, is that it needs to infect other running processes to inflict damage on infected machines. Instead of being a standalone executable file that is run to infect a machine, it is a shared object (SO) library that is loaded into all running processes using LD_PRELOAD (T1574.006), and parasitically infects the machine. Once it has infected all the running processes, it provides the threat actor with rootkit functionality, the ability to harvest credentials, and remote access capability. More…
A cybercriminal stole 1 million Facebook account credentials over 4 months
A large-scale phishing attack was uncovered by PIXM, as well as the person who had been carrying out the attacks.
Murder suspect admits she tracked cheating partner with hidden AirTag
O! What a tangled web we weave, when first we practice to deceive. [Bob says the details of this murder case are chilling. Anyone can track you for any reason easily enough with technology like this.]
Share
JUN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com