 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
NSA Releases Network Infrastructure Security Guidance
Original release date: March 3, 2022
The National Security Agency (NSA) has released a new Cybersecurity Technical Report (CTR): Network Infrastructure Security Guidance. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. Recommendations include perimeter and internal network defenses to improve monitoring and access controls throughout the network.
CISA encourages network architects, defenders, and administrators to review NSA’s Network Infrastructure Security Guidance as well as CISA’s recently published Layering Network Security Through Segmentation infographic for assistance in hardening networks against cyber threats.
Instagram scammers as busy as ever: passwords and 2FA codes at risk
Instagram scams don’t seem to be dying out – we’re seeing more variety and trickiness than ever…
In the past few days, we’ve had a bogus Instagram warnings, complete with Instagram branding, in each of these categories:
- Fake warning: Community guidelines violation. Proposed solution: Contact us to find the content that needs to be removed to clear the block.
- Fake warning: Copyright infringement. Proposed solution: Dispute the claim and cancel the strike against you by filling in the form.
- Fake warning: Suspicious login alert. Proposed solution: If this wasn’t you, click through now to secure your account.
Get ready for security in the age of the Extended Internet of Things, says Claroty
ICS vulnerability disclosures have grown by 110% since 2018, which Claroty said suggests more types of operational technologies are coming online and presenting soft targets.
Operational technology company Claroty makes a big claim about the future of OT and industrial control systems security: Based on data collected over the past few years, the distinction between OT/ICS and the rest of enterprise tech is beginning to fade in earnest, and new security headaches have appeared in their place.
Claroty states is case in its ICS Risk and Vulnerability report for the second half of 2021 (find the first half here), which found among other things that there has been a 110% year-over-year increase in the number of ICS vulnerabilities disclosed since 2018, and that non-OT products made up 34% of ICS vulnerabilities reported in 2021. Click on title link to read entire article.
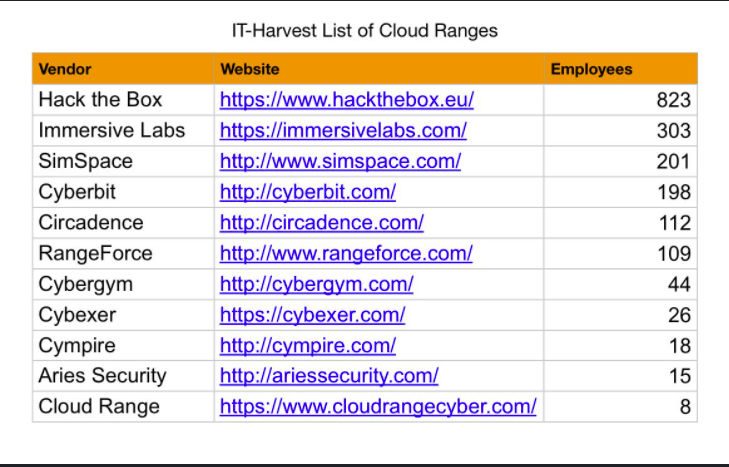
Here’s a Great List of Cyber Ranges
If you are training for the CEH or PenTest+, finding a good practice lab can be an issue. These cyber ranges are for the most part free to use.
CISA’s Zero Trust Guidance for Enterprise Mobility Available for Public Comment
Original release date: March 7, 2022
CISA has released a draft version of Applying Zero Trust Principles to Enterprise Mobility for public comment. The paper guides federal agencies as they evolve and operationalize cybersecurity programs and capabilities, including cybersecurity for mobility. The public comment period will close April 18, 2022.
Executive Order 14028: Improving the Nation’s Cybersecurity, issued May 12, 2021, requires Federal Civilian Executive Branch departments and agencies to adopt Zero Trust (ZT) architectures to protect the government’s information resources, of which federal mobility is an integral part. The guidance highlights the need for special consideration for mobile devices and associated enterprise security management capabilities due to their technological evolution and ubiquitous use.
CISA encourages interested parties to review Applying Zero Trust Principles to Enterprise Mobility and provide comment. See CISA Blog: Maturing Enterprise Mobility Towards Zero Trust Architectures for more information.
Russia Could ‘Absolutely’ Lash Out at US Through Cyber, Lawmaker Warns
NextGov reports: Chairman Sen. Mark Warner, D-Va, gives an opening statement as FireEye CEO Kevin Mandia, SolarWinds CEO Sudhakar Ramakrishna and Microsoft President Brad Smith testify at a Senate Intelligence Committee hearing on Capitol Hill on February 23, 2021.
“Russia is expected to increase its cyber attacks as it continues a military assault on Ukraine, and one lawmaker warns that the U.S. should be prepared for future high level digital attacks.”
Speaking live to The Washington Post on Monday, Senator Mark Warner, D-Va. spoke about Russia’s cyber attacks on Ukraine’s networks and the spread of disinformation as part of the country’s offensive strategy.
“Do I expect Russia to up its game on cyber? Absolutely,” Warner said. “I do think we need to be prepared for high level––his A-Team––attacks against the West whether they start with nations in NATO [North Atlantic Treaty Organization] that have weaker cyber controls or whether they go straight against the United States, Britain, France, Germany.”
Warner hypothesized that Russian President Vladimir Putin did not prioritize launching cyberattacks against Ukraine’s infrastructure, and that the U.S. and other NATO allies should brace for major cyber hacks.
“When a top tier nation uses their top talent to attack in the cyber domain, chances are we will not be 100% effective at keeping the adversary out,” he said. Warner praised Cybersecurity and Infrastructure Security Agency Director Jen Easterly for strengthening protocols and being alert against cyberattacks and ransomware.”
“I think we will probably see that in the coming days and weeks as Putin tries to lash out against these crippling level of sanctions we put on him,” Warner added.
CONTINUED:
https://blog.knowbe4.com/russia-could-absolutely-lash-out-at-us-through-cyber-lawmaker-warns
FBI Releases Indicators of Compromise for RagnarLocker Ransomware
Original release date: March 8, 2022
The Federal Bureau of Investigation (FBI) has released a Flash report detailing indicators of compromise (IOCs) associated with ransomware attacks by RagnarLocker, a group of a ransomware actors targeting critical infrastructure sectors.
CISA encourages users and administrators to review the IOCs and technical details in FBI Flash CU-000163-MW and apply the recommended mitigations.
Share
MAR




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com