Comedy, satire, opinion, political humor, and stories for your entertainment
From Larry Parkins on Facebook Check out the Facebook group At The Controls
An early “desktop” computer, the Univac Digital Trainer: a few were built in the 1960s to train U.S. Navy technicians on digital computer technology.
This machine was my first exposure to computer programming as a new Univac employee in 1965. The computer had 512 words of 15 bits each: the user interface was through the Friden Flexwriter, which had a 7-bit paper tape punch/reader, or directly in binary through the front panel register indicator-switches, which were lit with neon bulbs. The instruction set was similar to the production-model 30-bit, 32,768 word (a bit less than 128 KB) computers that used Model 35 teletypes, 556-frame/per inch 10.5-inch reel-to-reel magnetic tape drives with mechanical tape loop buffers, and a 5-MB removable hard drive, which fit snugly in an 8’x16′ room. The credit-card-sized circuit cards ( which filled both front and back on this desktop machine) were built with discrete components–diodes, transistors, resistors, and capacitors, two transistors and a half-dozen diodes for each bit in each register, and the memory was a stacked array of tiny ferrite beads (cores), with three or four wires (row, column, bit plane sense/inhibit) passed through the holes to switch and sense the magnetic direction, one core per bit. The memory arrays were built by hand on a vacuum table to hold the cores in place while threading the wires. The memory units had to be re-tuned periodically to balance the electric currents to run without errors.
AFAIR the ealry teletypes ran at 10 characters per second. Because carriage return (CR) took longer than 100ms to execute, another printing character could not immediately follow the CR. It was usual to follow CR with line feed (LF) which together were guaranteed to execute within 200ms so printing characters could follow the CR LF pair immediately. I think the data rate was 110 baud, i.e. 11 “bits” per character, which were 7 data bits for ASCII plus a spare 8th bit and one start bits and two stop bits givig the familiar serial data format.
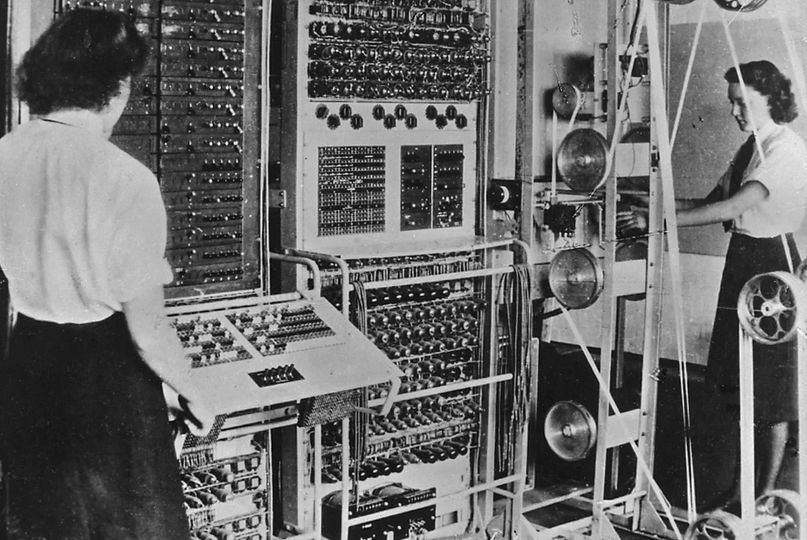
Colossus (UK) computer operators in 1943. Cracking the Enigma codes. Is that punch tape on the right, or telegraph style printed paper strips?
There are plenty of military puns in operating system history.
Unix famously has a whole raft of personnel known as Major Number, who organize the battalions of devices such as disk drives, keyboards and webcams in your system.
Microsoft once struggled with the apparently incompetent General Failure, who was regularly spotted trying to read your DOS disks and failing.
Linux has intermittently has trouble with Colonel Panic, whose appearance is typically followed by lost data, potentially damaged file systems, and an urgent need to turn off the power and reboot your computer.
And a Czech cryptocurrency company doesn’t seem to be getting the sort of reliability you might reasonably expect from a personality called General Bytes.
Actually, General Bytes is the name of the company itself, a business that sadly is no stranger to unwanted intrusions and unauthorized access to cryptocurrency funds.
APR







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com