 There has been a stream of email alerts arriving at my inbox lately that warned of a variety of new phishing approaches that are using well-known brands (OneDrive and Office 365, FedEx and UPS), trusted sources (Department of Homeland Security, Gmail, Yahoo Mail), secure services (TLS certificates and HTTPS web sites) and curiosity (you received an encrypted message) to trick recipients into clicking a link that leads to a fake replica web page, or open a malware-laced attachment. I thought I might cover a few specific cases.
There has been a stream of email alerts arriving at my inbox lately that warned of a variety of new phishing approaches that are using well-known brands (OneDrive and Office 365, FedEx and UPS), trusted sources (Department of Homeland Security, Gmail, Yahoo Mail), secure services (TLS certificates and HTTPS web sites) and curiosity (you received an encrypted message) to trick recipients into clicking a link that leads to a fake replica web page, or open a malware-laced attachment. I thought I might cover a few specific cases.
Official-looking Government Email – The first warning came from US-CERT and the DHS about a DHS Email Phishing Scam. This exploit uses official looking email from a government cybersecurity agency that asks users into clicking on malicious attachments that look like legitimate Department of Homeland Security (DHS) notifications. The email campaign uses a spoofed email address to appear like a National Cyber Awareness System (NCAS) alert and lure targeted recipients into downloading malware through a malicious attachment. CISA will never send NCAS notifications that contain email attachments.
Other government fake-outs can appear to come from the FBI, IRS or Social Security Administration. I especially enjoyed the one I got from the “FBI” claiming they had found child pornography on my computer, but if I agreed to pay a fine, I would not be arrested.
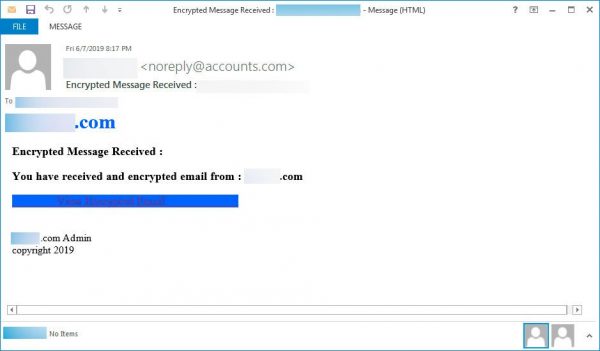
Encrypted Message – This one was reported by the Bleeping Computer website. I have included a copy of the email below. Clicking on the dark blue “View Encrypted Email” link will open an embedded URL web page file, and clicking the blue button there to a very realistic OneDrive login screen. There are more images of the exploit including the attachment web page, and the spoofed OneDrive login page. Entering your user ID and password here would send them directly to the attackers. Since OneDrive is part of your Microsoft ID, this would give them your computer login credentials, and your Office 365 and Outlook email accounts including your inbox, outbox, sent mail, and stored mail, your contacts, calendar, any team sites or SharePoint sites, and your Skype account as well. Not a bad haul for one email.
Real Estate and Mortgage Documents – This is quite similar to the encrypted message scam, but I’ve seen this targeting realtors and mortgage lenders. The email appears to come from a real estate company, realtor, or mortgage company employee. Typically the sender is an actual person that the recipient may know, which lends credibility to the email. The email is not spoofed, but is sent from the actual email account of the apparent sender. There are attached PDF documents that, when opened, spread the infection to the recipient’s computer. Part of the exploit hijacks the recipients email account credentials via a keylogger or other method, then takes over the email account and sends the original email to everyone in the email contact list, spreading the infection further. With the large sums of money that are transferred during real estate transactions, this exploit makes it simple for the attacker to send a request for funds using an email account of a real, known, and trusted realtor or mortgage lender.
TLS Certificates and HTTPS websites – The next warning came from the FBI. It is a warning about cyber-criminals, scammers, and attackers purchasing and using TLS security certificates to make their fake websites appear more realistic but using an HTTPS address. The basic message to computer users here is that an HTTPS website only proves that the session between your computer and the website will be securely encrypted. It is in no way proof that the website itself is secure, legitimate, or uninfected with malware downloads. The fact that the malicious download is encrypted may make it harder for your anti-malware solution to detect and block it.
Attacking SMS 2FA – Toward the end of 2018 there were reports of successful exploits targeted at capturing two-factor authentication codes that were being sent via short message service (SMS) to smartphones. The problem is that SMS is not a secure transmission mode, and there is no encryption. SMS codes can be captured using man-in-the-middle attacks, where the attacker sets up a connection in between yours and the server, or SIM-card swapping to clone your phone. The solution here is to move from SMS 2FA to something that is secure and encrypted such as Google Authenticator.
Shipment Advice – And let us not forget to watch for fake emails from package shippers such as DHL, FedEx, UPS, and the USPS. Often these emails appear to claim the shipment was damage in transit, or the shipment is undeliverable due to a bad address or some other issue. Do not follow links or open attachments in these emails. Shipper email with attachments have launched crypto-ransomware malware in the past, but attachment can contain anything from a remote access Trojan horse, banking Trojan, to crypto-mining software. It is always best to log onto your shipper’s account using your keyboard or a saved browser shortcut. Never click on a link or open an attachment without first confirming the validity of the sender. Virustotal can be a great resource in these cases.
These are some of the specific phishing exploits that you want to be looking for in your Inbox. Again, to protect yourself:
- Never trust a link or an attachment in an email.
- Verify attachment contents by calling the sender.
- Make sure the sender name and sender email address match up and makes sense,
- Use Virustotal to scan links and attachments.
- Login to your accounts directly, rasther than clicking the provided link.
- Confirm that the login page is where you think it is by checking the web address in the browser’s address window.
JUN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com