 Is it a USB cable or a Trojan horse? We have come to consider Trojan horses to be malicious software these days, and part of the virtual world, But the original Trojan Horse was a very physical device. And so is this stunning USB style Trojan.
Is it a USB cable or a Trojan horse? We have come to consider Trojan horses to be malicious software these days, and part of the virtual world, But the original Trojan Horse was a very physical device. And so is this stunning USB style Trojan.
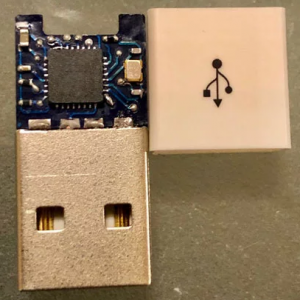
Called the O.MG Cable by its creator, Mike Grover, whose online handle is MG, this device can be plugged into Windows, Linux, or Mac systems, and allow it’s user to execute commands over Wi-Fi from a phone app to the computer the cable is attached to.
The cable appears to the host computer to be a HID or Human Interface Device, basically a keyboard and mouse. Although the device connects to available Wi-Fi networks, the cable can be configured to call out to the attacker over the Internet, creating an exploit called a “reverse shell.” This gives the attacker a terminal or command prompt to work with on the victim computer.
Some of the exploits include:
- Remotely log into the victim system.
- Type commands into the victim system
- Install, update, and run malicious software.
- Disconnect other systems from the wireless network.
- Change the firmware (BIOS) of connected systems.
More information:
And on a related note:
Share
MAR




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com