 Code obfuscation is the process of modifying an executable so that it is no longer valuable to a hacker while remaining fully functioning. Although the procedure may alter method instructions or metadata, it has no impact on the program’s output. To be clear, practically any code can be reverse-engineered with enough time and effort. On a number of platforms, free decompilers for Java, Android, iOS, and.NET (e.g. Xamarin, C#, VB.NET, F#) may quickly and painlessly reverse-engineer source code from an executable or library. Reverse engineering software is difficult and expensive due to automatic code obfuscation.
Code obfuscation is the process of modifying an executable so that it is no longer valuable to a hacker while remaining fully functioning. Although the procedure may alter method instructions or metadata, it has no impact on the program’s output. To be clear, practically any code can be reverse-engineered with enough time and effort. On a number of platforms, free decompilers for Java, Android, iOS, and.NET (e.g. Xamarin, C#, VB.NET, F#) may quickly and painlessly reverse-engineer source code from an executable or library. Reverse engineering software is difficult and expensive due to automatic code obfuscation.
What is the function of a Code Obfuscator?
You can safeguard against trade secret (intellectual property) theft, unwanted access, evading licensing or other constraints, and vulnerability discovery by making a program substantially more difficult to reverse-engineer.
What is the process of obfuscation?
Code obfuscation is a collection of approaches that work together to form a layered defense. It’s best used with intermediate-level programming languages such as Java or.NET languages such as C#, VB.NET, Managed C++, F#, and others. The following are some examples of obfuscation and application security approaches:
Obfuscation should be given a new term.
The names of methods and variables are changed when they are renamed. It makes decompiled source code more difficult to understand for humans, but it has no effect on program execution. Various schemes, such as “a,” “b,” “c,” or numerals, unprintable characters, or invisible letters, can be used in the new names. As long as the names have independent scopes, they can be overloaded. Most.NET (C#, etc.) obfuscators, as well as iOS, Java, and Android obfuscators, use a basic transform called name obfuscation.
Encrypting strings with String Encryption is a technique.
All strings are discoverable and readable in a regulated executable. String references can be used to discover critical code regions by checking for string references inside the binary, even if methods and variables are renamed. This includes any messages displayed to the user (particularly error messages). String encryption hides strings in the executable and only restores their actual value when needed to offer an effective barrier against this type of assault. Decrypting strings at runtime usually has a slight performance hit.
Obfuscation of Control Flow
Control flow obfuscation synthesizes conditional, branching, and iterative components to offer acceptable executable logic but non-deterministic semantic implications when decompiled. Simply said, it translates decompiled code into spaghetti logic, which is extremely difficult for a hacker to comprehend. These strategies may have an impact on a method’s performance.
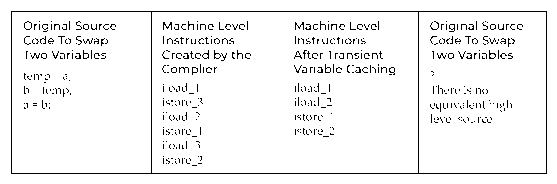
Patterns of Instructional Change
Converts the conventional instructions of the compiler into less evident forms. These are fully functional machine instructions that may or may not translate
well into high-level languages like Java or C#. For transitory variable caching, the Java and.NET runtimes, for example, use a stack-based structure.
Inserting a Dummy Code
Inserting code into an executable that has no effect on the program’s logic but breaks decompilers or makes reverse-engineered code much harder to understand.
Remove any metadata or code that is no longer in use.
Debug information, non-essential metadata, and utilized code are stripped from applications, making them smaller and reducing the amount of information available to an attacker. This approach may marginally increase runtime performance.
Merging/Binary Linking
Multiple input executables/libraries are combined into one or more output binaries with this transform. Linking, when used in conjunction with renaming and pruning, can help you reduce the size of your application. It can also simplify deployment and limit the amount of data that is vulnerable to hackers.
By inserting conditional branches that always evaluate to known results—results that are difficult to predict using static analysis—Predicate Insertion obfuscates. This is a means of adding potentially incorrect code that will never be executed but will confuse attackers attempting to decode decompiled output.
Technology that detects tampering
To verify that your code hasn’t been tampered with, an obfuscator can incorporate application self-protection into it. If tampering is discovered, the application can be disabled, its functionality restricted, random crashes (to obscure the origin of the crash), or any other action taken. It may also send a notification to a service telling it that tampering has been discovered.
Preventing Bugs
When a hacker wants to pirate or counterfeit your program, steal your data, or alter the functionality of a critical piece of infrastructure software, they almost always begin by reverse engineering and debugging it. An obfuscator can layer in application self-protection by inserting code to detect if your production application is running in a debugger. A debugger can corrupt important data (to prevent theft), cause random crashes (to hide the fact that the crash was caused by a debug check), or do any other specific action if it is invoked. It could potentially send a message to a service to send a warning signal.
Is it required that I hide my application?
You should seriously consider utilizing obfuscation and runtime app self-protection if you publish software that contains intellectual property, enables access to sensitive information, or has gated functionality and functions in an untrusted environment. If the code is obfuscated, attackers will have a much tougher time interpreting and studying the software.
Hackers will have a harder time debugging and interfering with your program. The ultimate goal is to add a layer of security to an application that makes it impossible to extract or uncover useful information, such as trade secrets (IP), credentials, or security vulnerabilities. It should also make changing a program’s logic or repackaging it with malicious code more difficult.
Share
JUN







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com