 One of the Facebook cybersecurity groups that I follow, Cybersecurity Lounge, is set up to provide ideas and advice to people at the start of their IT career, or who are studying for, or have just passed, a certification. One member of the group told a story of a recent interview he had for an IT job. He was first asked how to PING an IP address. That part went well. Then the hiring manager asked him to UN-PING the address. The applicant evidently was stumped, and from the story it was not clear whether he got the job or not. I think not. There is no UN-PING command, or any way to un-ping an IP address. It’s like un-ringing a bell – it just cant be done. It was a mean and nasty old trick question by the interviewer for sure, but the lack of an answer speaks volumes about the candidate’s experience, practical knowledge, and skills.
One of the Facebook cybersecurity groups that I follow, Cybersecurity Lounge, is set up to provide ideas and advice to people at the start of their IT career, or who are studying for, or have just passed, a certification. One member of the group told a story of a recent interview he had for an IT job. He was first asked how to PING an IP address. That part went well. Then the hiring manager asked him to UN-PING the address. The applicant evidently was stumped, and from the story it was not clear whether he got the job or not. I think not. There is no UN-PING command, or any way to un-ping an IP address. It’s like un-ringing a bell – it just cant be done. It was a mean and nasty old trick question by the interviewer for sure, but the lack of an answer speaks volumes about the candidate’s experience, practical knowledge, and skills.
If you are pursuing a career in information technology, computer support, networking, or cybersecurity, then you need to know how to use these networking tools. All of them can be used in a Windows Command session. To open a command prompt in Windows, type command or cmd in the search box on the tool bar. Right click on the cmd.exe icon that is offered, and select Run as administrator from the context menu. This step ensures that you are working at elevated administrative privileges.
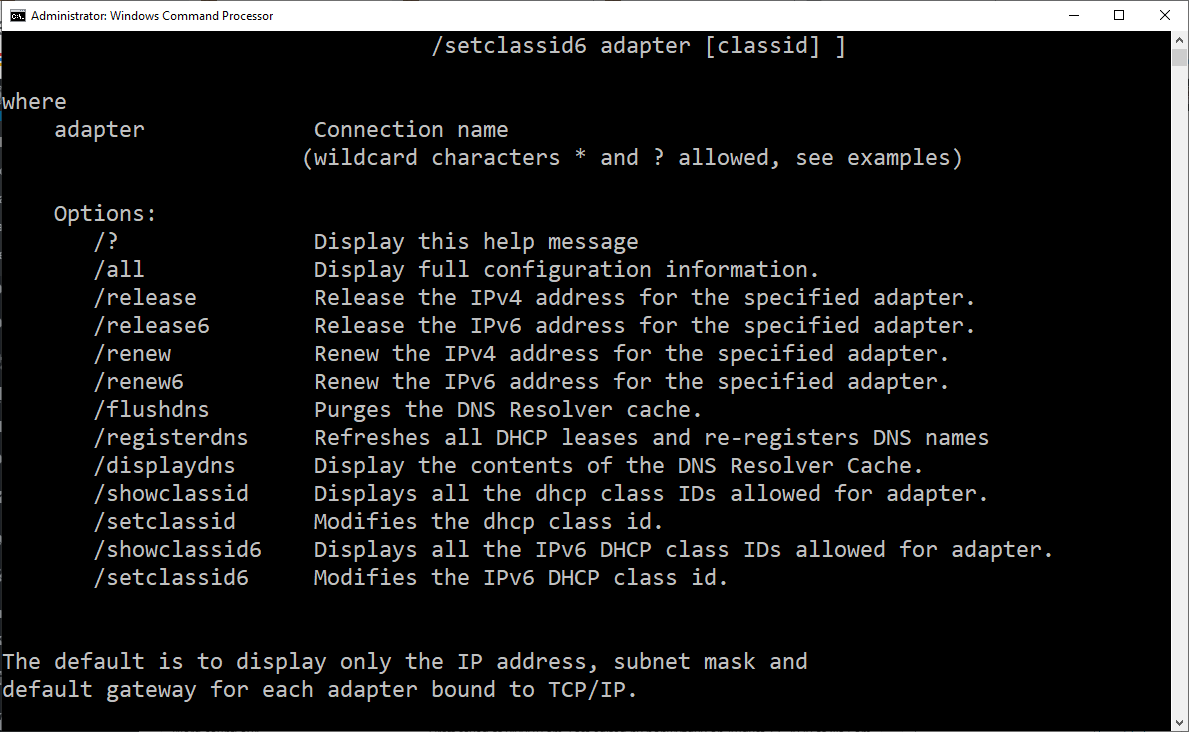
Once you have the command window open, try a few of these commands. The first thing to learn is a trick you can use on many certification exams, how to run HELP. Most of these commands have a number of options and switches to use to get different information. To invoke HELP, simply enter the command, leave an empty space and type the question mark ? or /? or help. This should display a list of options. Here’s a screenshot of part of the HELP files for the IPCONFIG command.
The table below lists common networking commands, and describes what they are used for. If you are new to your IT career, you need to learn how and when to use these commands for information gathering and troubleshooting. If you have time into your career, you probably know these commands already, but look for options you have not used before and learn about them.
| IPCONFIG | The ipconfig command is used to display detailed IP information for each network adapter utilizing TCP/IP. The ipconfig command can also be used to release and renew IP addresses on systems configured to receive them via a DHCP server. The ipconfig command is available in all versions of Windows. |
| PING | The ping command sends an Internet Control Message Protocol (ICMP) Echo Request message to a specified remote computer to verify IP-level connectivity. The ping command is available in all versions of Windows. |
| TRACERT | The tracert command sends Internet Control Message Protocol (ICMP) Echo Request messages to a specified remote computer with increasing Time to Live (TTL) field values and displays the IP address and hostname, if available, of the router interfaces between the source and destination. The tracert command is available in all versions of Windows. |
| NETSTAT | The netstat command is most commonly used to display all open network connections and listening ports. The netstat command is available in all versions of Windows. |
| NBTSTAT | The nbtstat command is used to show TCP/IP information and other statistical information about a remote computer. The nbtstat command is available in all versions of Windows. |
| NET | The net command is used to display, configure, and correct a wide variety of network settings. The net command is available in all versions of Windows. |
| NETDOM | Use Netdom.exe to reset machine account passwords of a domain controller in Windows Server 2008 R2, in Windows Server 2008, or in Windows Server 2003. |
| NSLOOKUP | The nslookup is most commonly used to display the hostname of an entered IP address. The nslookup command queries your configured DNS server to discover the IP address. The nslookup command is available in Windows 8, Windows 7, Windows Vista, and Windows XP. |
So that’s a good start on the subject of networking. If you have an interview coming up, you should not be surprised to get a question about one of these commands, or be given an opportunity to show how they are used. For the rest of us, this is just good information to know for our daily professional lives.
Good luck and stay safe out there.
ShareAUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com