Phishing Email Alerts
Catch of the Day: Resume Phish with Prepending
Chef’s Special: Support Ukraine Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Resume Phish with Prepending
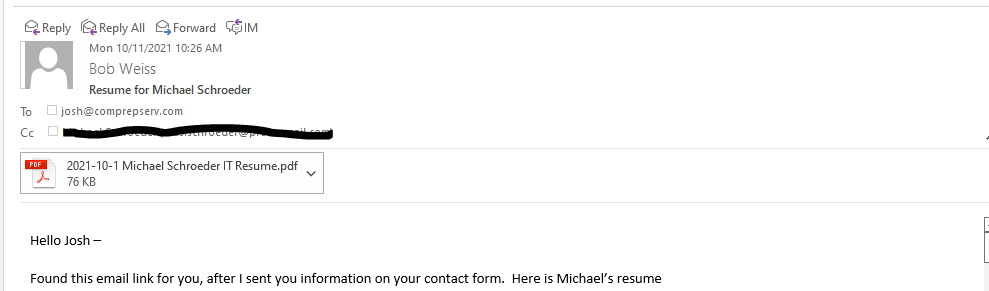
Here is an interesting phishing email that uses real information about an employment candidate. Resume and employment scams have seen an increase this year. And this is my first for the Friday Phish Fry.
This looks very realistic, because the phishing email contained copy/paste text from an actual email I had sent to Josh. There was a lot of additional information about my candidate Michael, but the sender’s email address was from India, and my guy would not be looking to work in India. The company name of Compreserv is correct for Josh, but the rest of the address is wrong. <pavan.kumarvyas@rajasthan.in>
The prepending part is the use of RE on the subject line. This makes the email seem to be a reply to my original email to Josh. But the original TO, FROM, and SUBJECT lines are missing. They would normally appear just after the password and before Hello Josh. The would be the heading information from the original email.
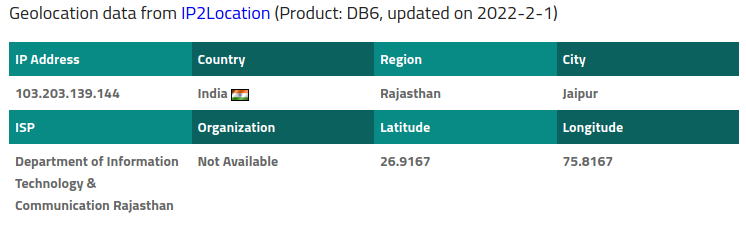
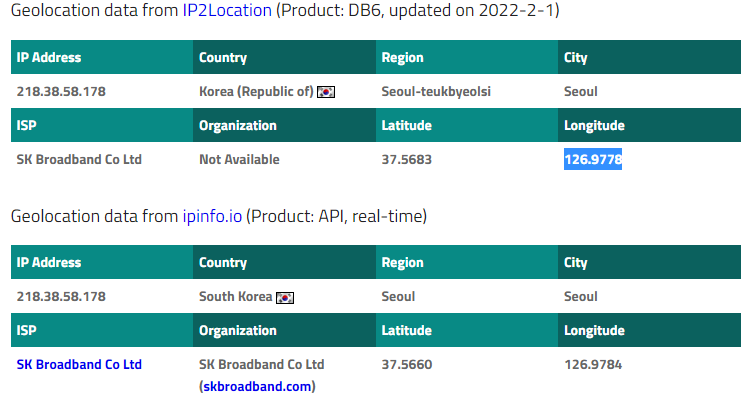
The email headers confirm that this email was sent from India, as did IP2Location
I went back into my email archive and found my original email. How this email and the information in it ended up in the hands of a phisher I do not know, but I suspect Josh’s or Michael’s email account may have been hijacked.
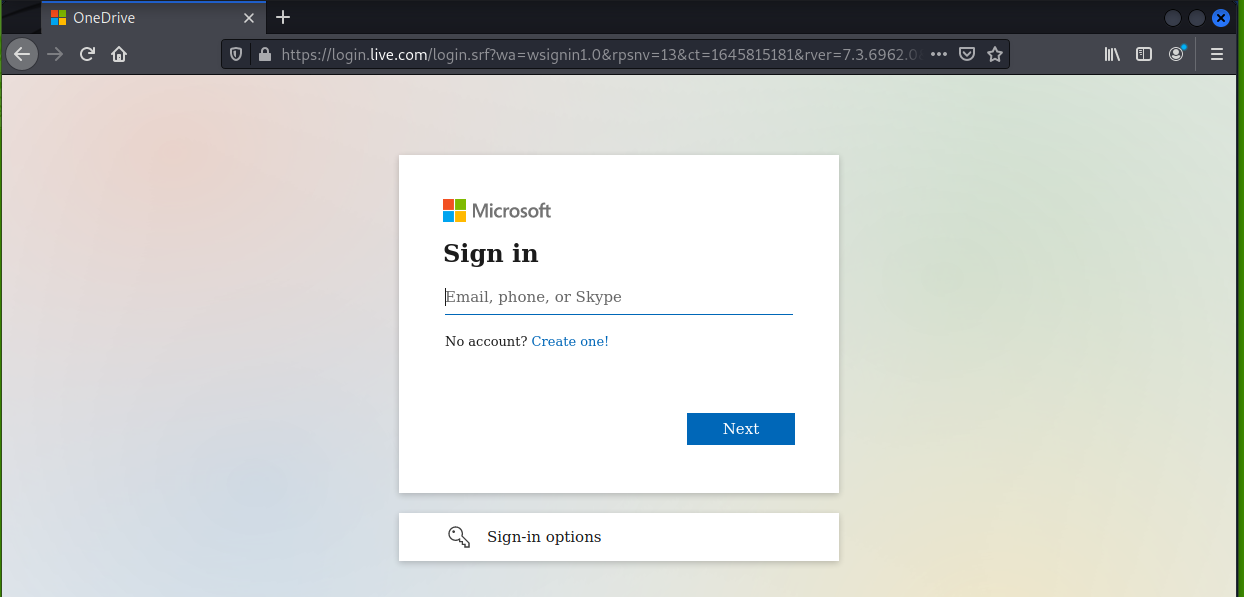
Following the OneDrive link https://onedrive.live.com/download?cid=77F1758961BF83C0&resid=77F1758961BF83C0%21106&authkey=ANDjDx4A6YEqSAg got me to a legitimate Microsoft Office login page.
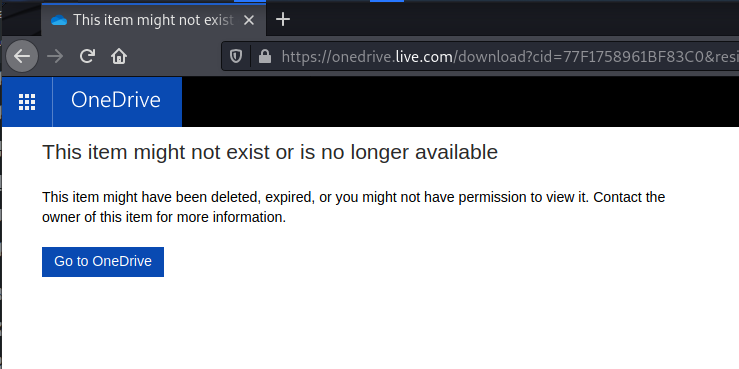
Since I was sure the login screen was authentic, I logged in hoping to find the password protected file, but had already been taken down. The phishers were using genuine Microsoft OneDrive and Office365 services, and Redmond does a pretty good job of closing these exploits down quickly.
Typically, the document will contain embedded malware to create a backdoor in your computer system, or maybe just another malicious link to a fake web page. I wish I had a chance to send it to VirusTotal and check it out.
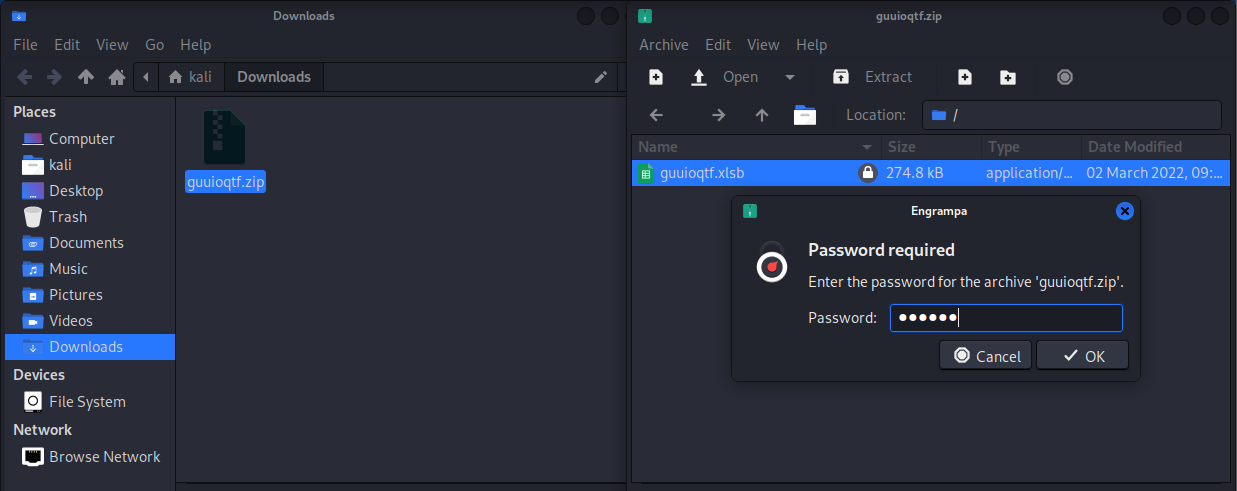
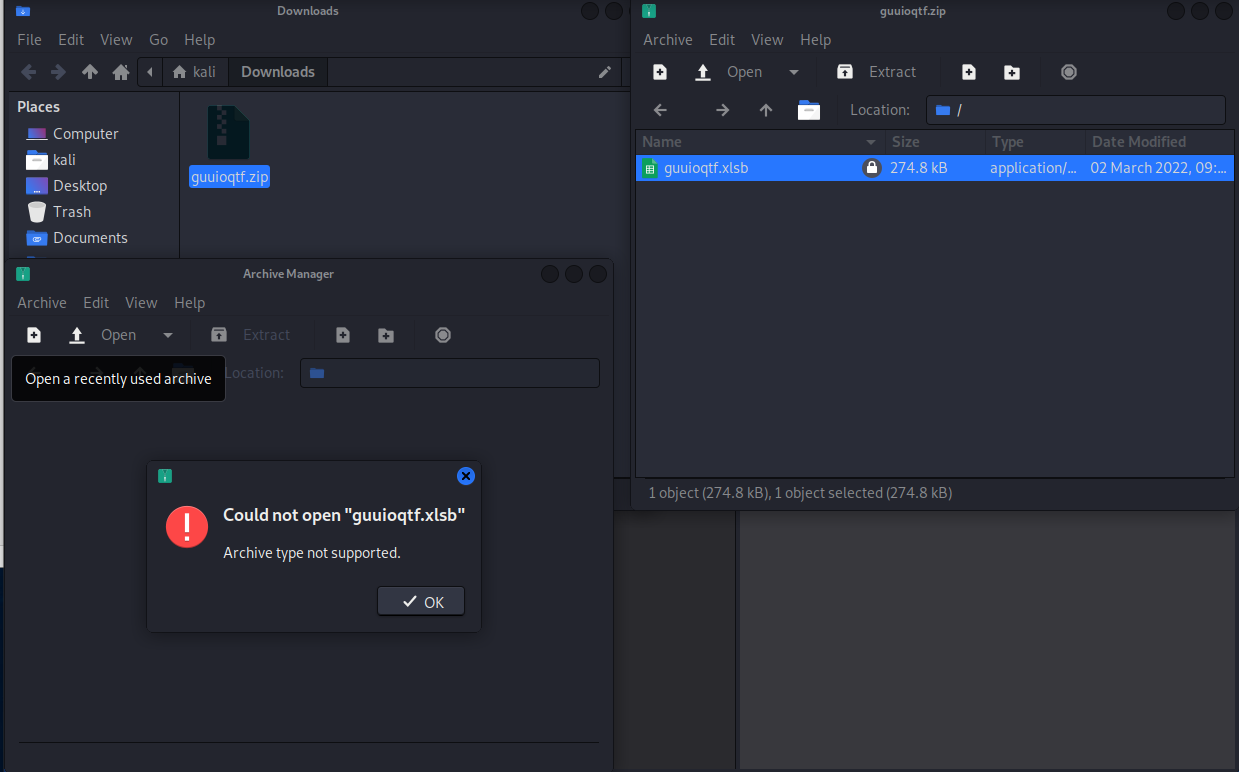
My wish came true. I got the same exploit again on March 2 and I was able to attempt downloading the file This was a ZIP file, and when I unzipped it, it looked like an Excel spreadsheet, but the XLSB file extension is for a BINARY FILE. Malware often is also a binary file.
I entered the password but was unable to get farther. I do not have MS Office loaded on my Kali box.
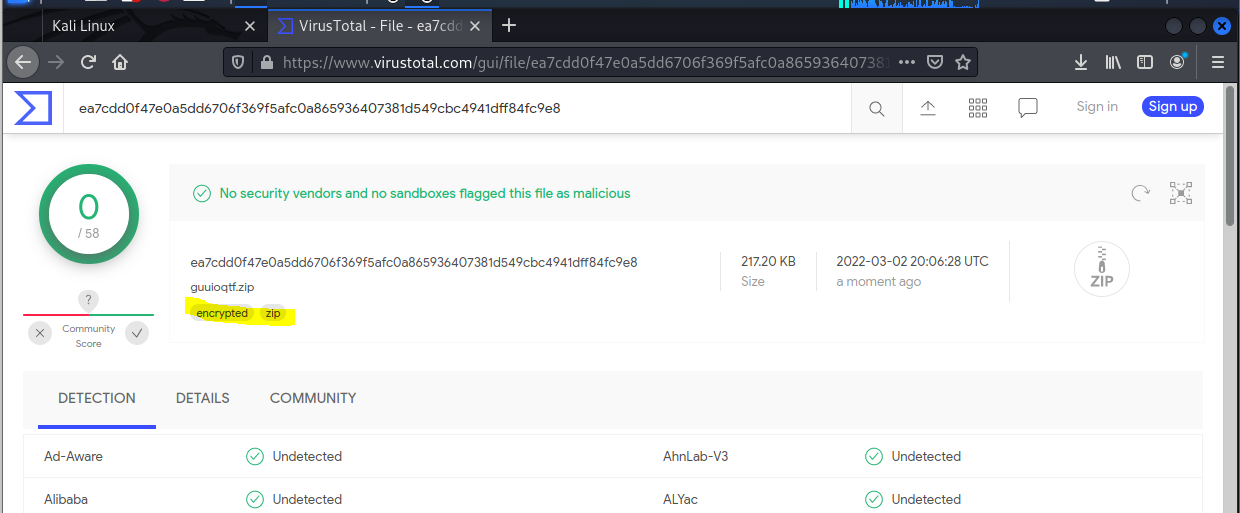
But I uploaded the file to VirusTotal, and even though nothing malicious was detected, VT did show that not only was this file zipped or compressed, it was also encrypted which is another good indication that the file attachment may be malware.
The lesson is beware these sorts of job application scams. It was believable because I know both Josh and Michael and the bulk of the text in the phishing email was written by me, and seemed familiar. I caught it because I always look at the actual sender email address, in this case I smelled a RAT (remote access trojan?)
Support Ukraine Phish
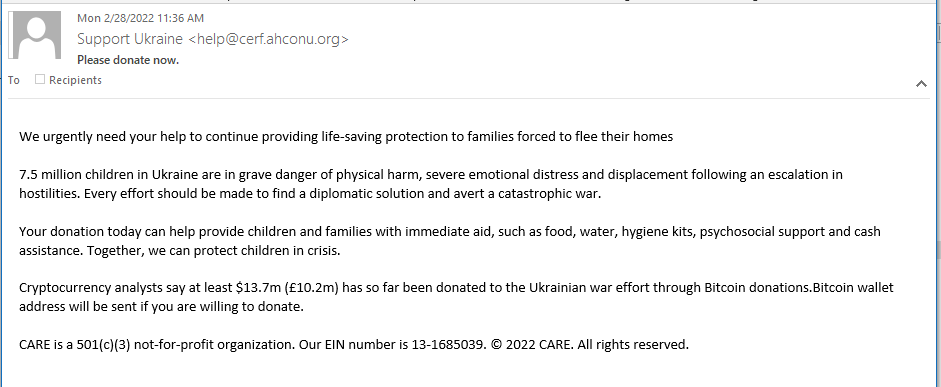
Never is there a tragedy that some clown doesn’t come up with a “charity” scam. The war in Ukraine is no exception. This bad actor is asking for Bitcoin donations to help the people of Ukraine. The Bitcoin wallet address will be sent if you reply. Here’s the email:
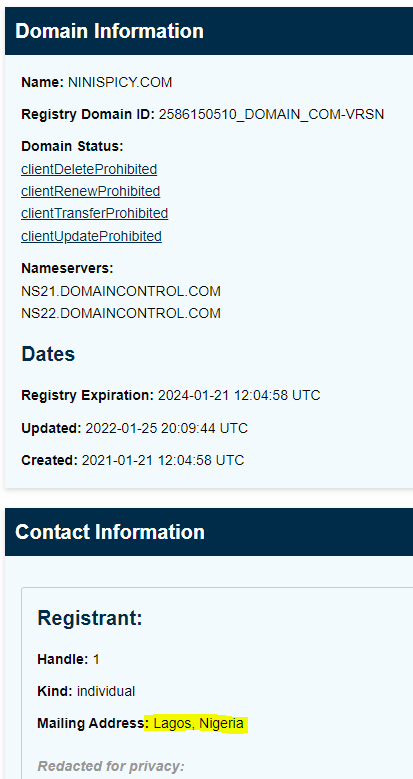
The return address is spoofed, using a domain that has been registered for several years, and is probably not involved directly in this scam. The hidden return email address can be found in the mail headers below. Relies will be delivered to support@ninispicy.com. This domain is registered to a person in Nigeria. Evidently the Nigerian Prince is busy again.
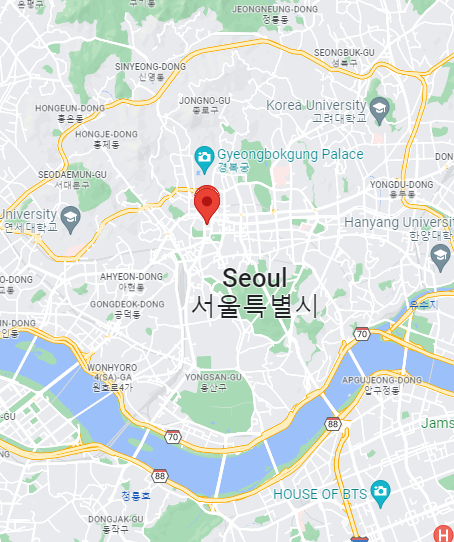
The email was sent on a mail server at designpix.co.kr with an IP address of 218.38.58.178. My trusty IP locator attributes this to South Korea, and the geolocation information brings us to Seoul South Korea.
Here is the location on Google Maps
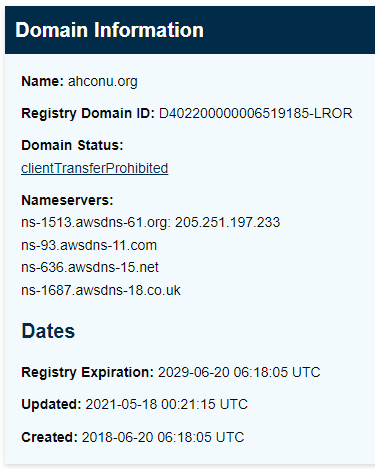
The senders spoofed email domain has been registered since June 2018, not forever, but probably not registered specifically for this exploit. This domain holder may be just another innocent bystander.
The ninispicy.com domain is fairly new. But if you were to reply to this email so you could get the Bitcoin wallet information, your reply would go to support@ninspicy.com and our Nigerian Prince
It’s really decent of you should you want to donate to Ukraine relief, just make sure you are donating to a legitimate charity, like the International Red Cross. Otherwise you hard earned Bitcoin will just end up in Nigeria.
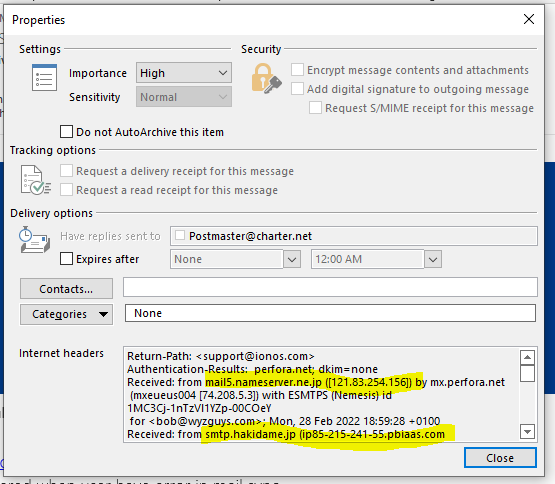
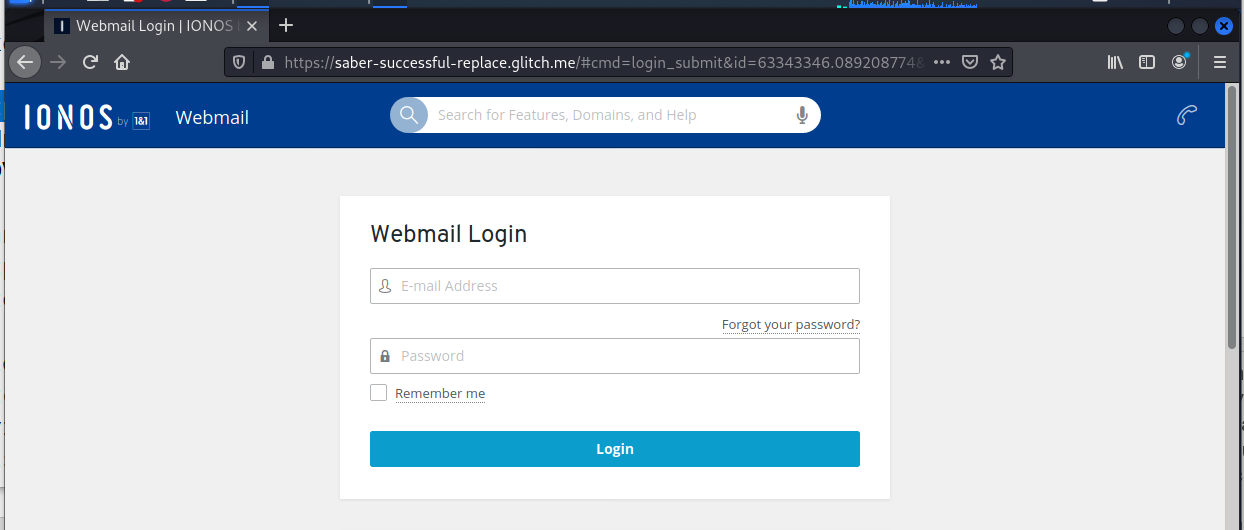
IONOS Email Sync Phish
The landing page errored out when I entered my email address and a fake password. Had I entered my real credentials, they would be in the hands of the phishers. All I can say is learn to be skeptical. If there is any doubt, there is no doubt. If it seems weird to you, it is.
MAR









About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com