Phishing Email Alerts
Catch of the Day: IONOS Phish
Chef’s Special: MS Consent Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
IONOS Phishing Attack
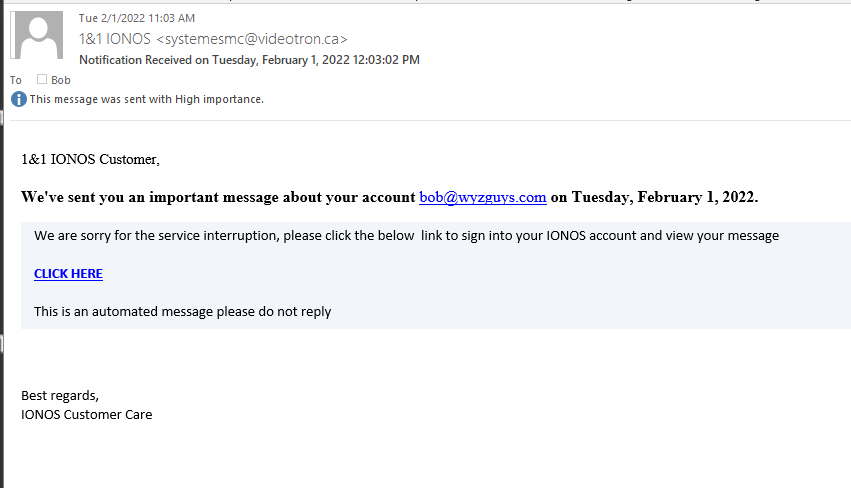
Here’s a phishing email that is allegedly from my web and email host that suggests I may be experiencing some sort of service interruption. The sending email address is obviously wrong for IONOS.
The Click Here link resolves to http://www.mail.ionos–bob.maxhairfiber.com/#bob@wyzguys.com, which redirects to https://38-ww-6-z-5-cvtvxkp-4-h-8-pkghb-5-y-2-wd-1-wjmkqvoze.glitch.me/MvEuy9wLJPsscxmR6wvs-GiizYXnZiGwVj6XFFKJe-gil1lud6L7jd24WBwfpA-uqmWF3MZkYWlXAPjqaxu-g7bzukjJs43m8Bjshpl1.html?%24web_only=true&_branch_match_id=1017164317907915721&utm_medium=marketing&_branch_referrer=H4sIAAAAAAAAA8soKSkottLXz64yTikwLkmsyDZPtywwyc0vSC%2FQSywo0MvJzMvWT9XPjcww9rfwNUzPSwIAoi6t2TMAAAA%3D#bob@wyzguys.com
The use of ionos in the original URL disguises the actual domain of bob.maxhairfiber.com. The redirection goes to glitch.me. VirusTotal found these domains to be clean, at least on the first day.
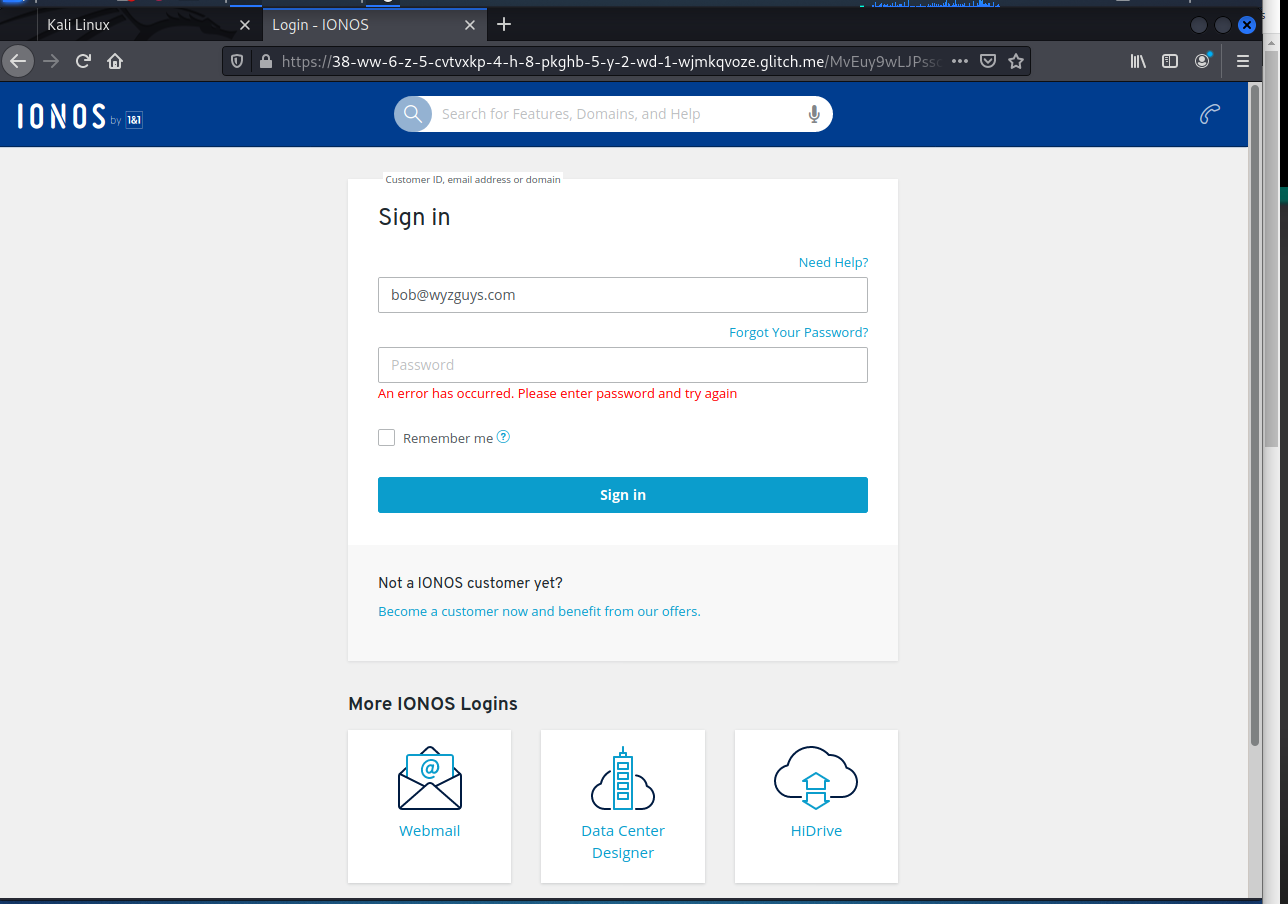
Here is the landing page
This is a typical credential stealing exploit.
Microsoft Warns of Latest “Consent Phishing” Attack Intent on Reading Your Email
Rather than steal your user’s credentials, this latest attack takes the OAuth route to gain access to the victim’s mailbox. This gives cybercriminals continual access, regardless of whether the user is logged on or not.
We’ve seen a number of these kinds of phishing attacks over the last 12 months targeting mailbox access within Microsoft 365 and even posing as Coinbase. If you’re not familiar with these attacks, rather than trick the phishing victim into providing their Microsoft 365 credentials (which can easily be reset), the attack poses as a legitimate app and asks for application access to your mailbox (for reference, Outlook Mobile does this to facilitate continual access for your mobile phone to access your Microsoft 365 mailbox).
In a recent tweet from Microsoft Security Intelligence, a new App – simply entitled “Upgrade” – was identified asking for OAuth permissions that would allow attackers to create inbox rules, read and write emails and calendar items, and read contacts. It’s also noted that suspicious Inbox Rules are created by this access and appear to exfiltrate emails.
The pivotal point where the attack can be stopped is when the malicious app is asking for access. Educating users would help ensure they are aware that – other than something like Outlook Mobile or another legitimate application – no unexpected phishing email EVER needs access to their mailbox.
Blog post with links:
https://blog.knowbe4.com/microsoft-warns-of-latest-consent-phishing-attack-intent-on-reading-your-email
Share
FEB





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com