Phishing Email Alerts
Catch of the Day: IONOS Password Phish
Chef’s Special: FedEx Delivery Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
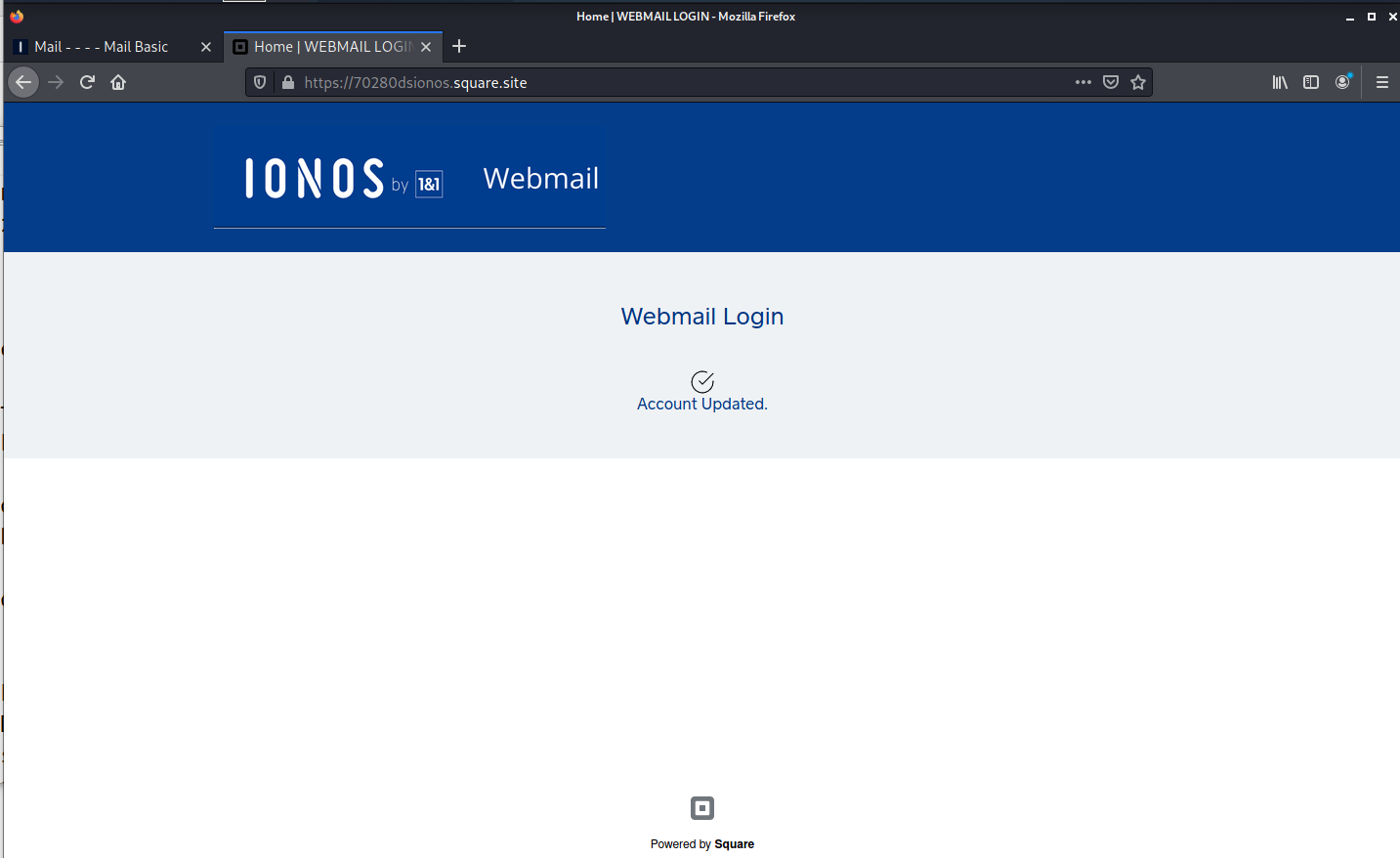
IONOS Password Phish
I received this phishing email, and thought the execution and graphics were pretty decent. The interesting take away is the use of the Square public and free web site platform for the landing pages.
We noticed the spoofed email sender right away, of course. The Keep Current Password link resolved to http://track.smtpsendemail.com/9052365/c?p=PAptInWOmrXEXEM5x4qCtz66ZGtKEAg1fWy8cX6bbGr2uQo2cNMrNq12TSAKBdwh-asYTiRmXaStEndU95p16UIJXPaitAABsQUIuysYZR51AswyIcZlgLz8MKvfnLPbCZsH6Of_UFQOKg1Bhql0hw== which redirected to https://70280dsionos.square.site/
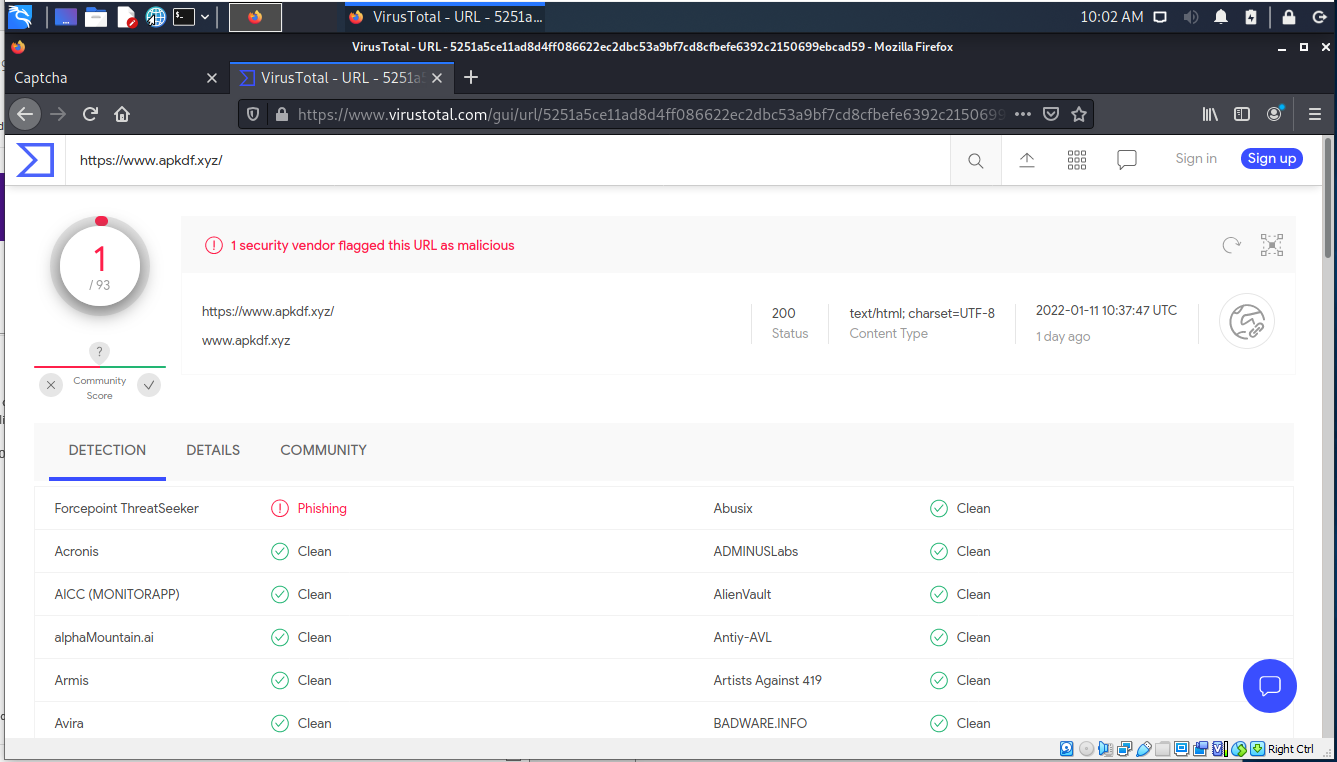
A quick check on VirusTotal gave the square.site address a passing mark, which is the advantage of using these public sites which work hard at keeping the reputation high. The original URL was detected as a malicious phishing link. Here is the phishing email.
The link redirected to a standard credential stealing landing page on the Square web site platform.
I entered a fake user ID and password, and got this follow-up screen. All in all, if you were taken in by the email, this exploit left you in a place the looks reasonably legitimate.
Some of the warning sighs were items such as the spoofed sender address, the malicious link which was identified on VirusTotal, and the fact that IONOS is a web site hosting company in their own right, and would not be using a square.site address for this purpose.
FedEX Delivery Phish
Ah the holiday season, where cyber-attackers dust off older exploits like the tried and true “missed delivery” phish. Here’s on I got this week in my inbox
The phishing email is sent from an email domain fedex-delivery.net. This is a great example of typo-squatting or registering a domain that is close to the actual domain, in this case the real address would be fedex.com. The Review Delivery Address button resolves to https://www.apkdf.xyz/#Ym9iQHd5emd1eXMuY29t which redirects to https://www.fedex-delivery.net/check.php?tap=A6a7t4dSGkEC8pXEa9xfIsdjRcQLRlX7u0eVu6Ht6dbLbqef4RbEpHmajPQz3lZNIUXCRFnvzlnF2xVeqcRmC5TFWQpvR0foihhjivYrl0HUvQqz1bOgbqWwg9rY75V0. The domain name is being used for hosting the landing pages as well. Overall, this appears to be a well-executed phishing exploit. Here’s the email:
Virus total flagged the button address, but the redirection address at fedex-delivery.net was, at the time of this investigation, a pass.
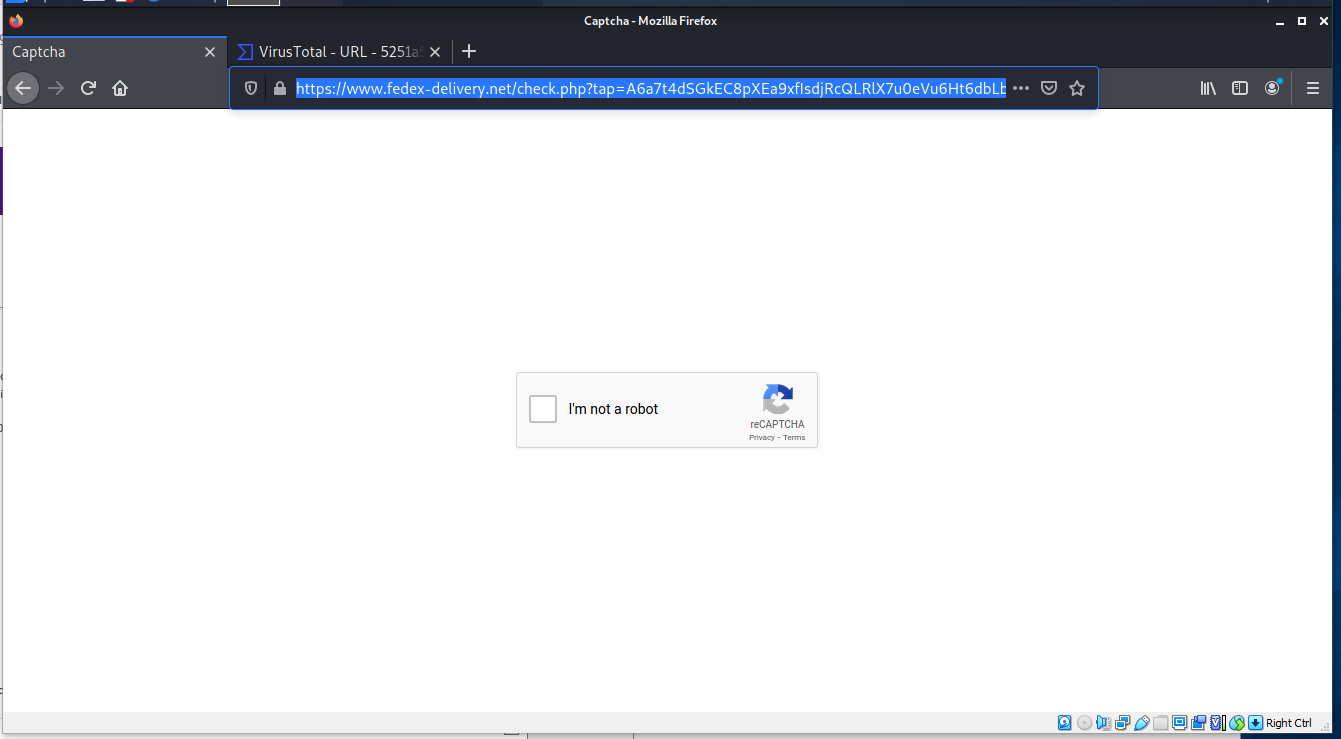
Here is the first landing page of three, and we start with a realistic looking reCAPTCHA screen.
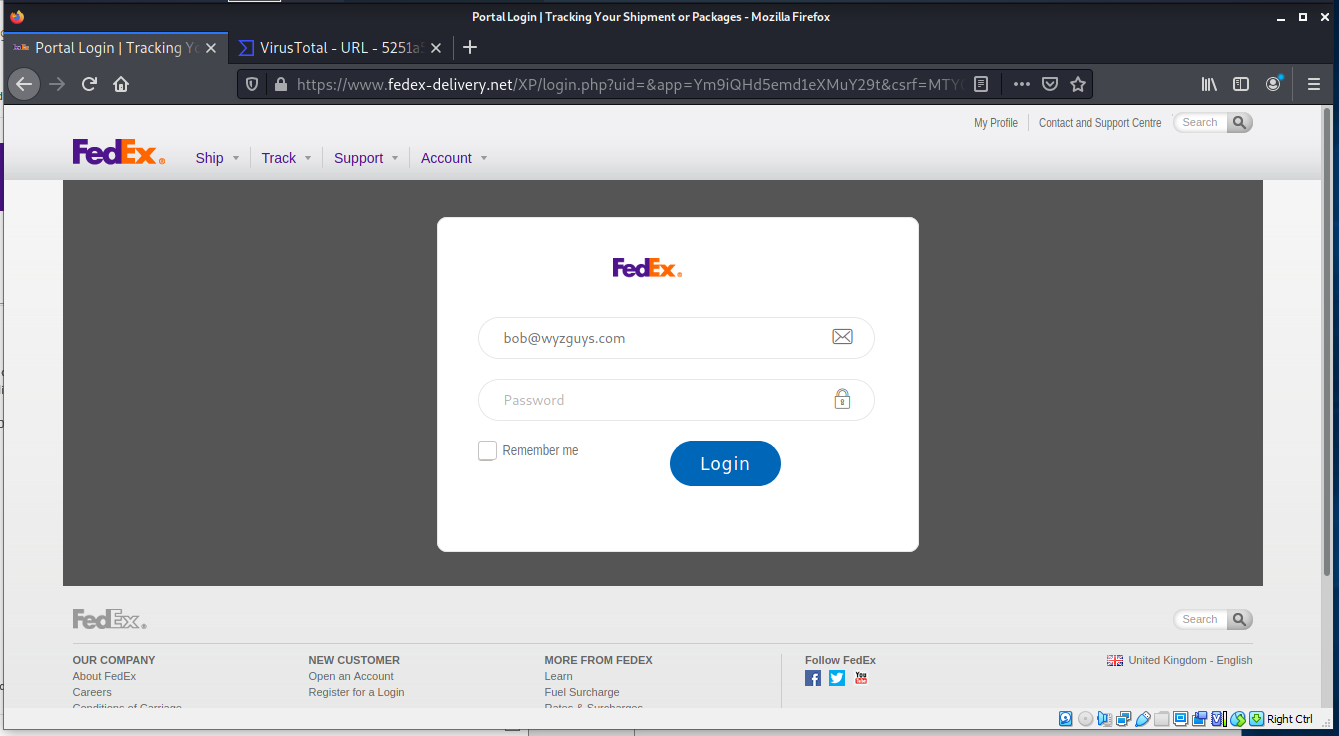
Here is the credential stealing login screen. Again, a very high-quality rendering of the real FedEx site.
My attempt at logging in met with this error message. Game over, and your FedEx credentials are in the hands of the attackers.
Again, don’t trust your senses. This one looks pretty real and will undoubtedly fool many people. Make sure you are not one of them.
Norton LifeLock Renewal Phish
I am seeing a lot more of these “call the toll-free number” scams, and I am assuming that they have more longevity than exploits that use hijacked or free websites and landing pages. My experience has shown that the web sites often come down fairly rapidly, sometimes within a few hours, when the site owner or web hosting company detects the fraudulent activity and traffic.
Again, resist the urge to get angry and call the provided number to dispute the call. Eventually you will be talked into providing something of value, like your credit card information, “so we can refund your account.”
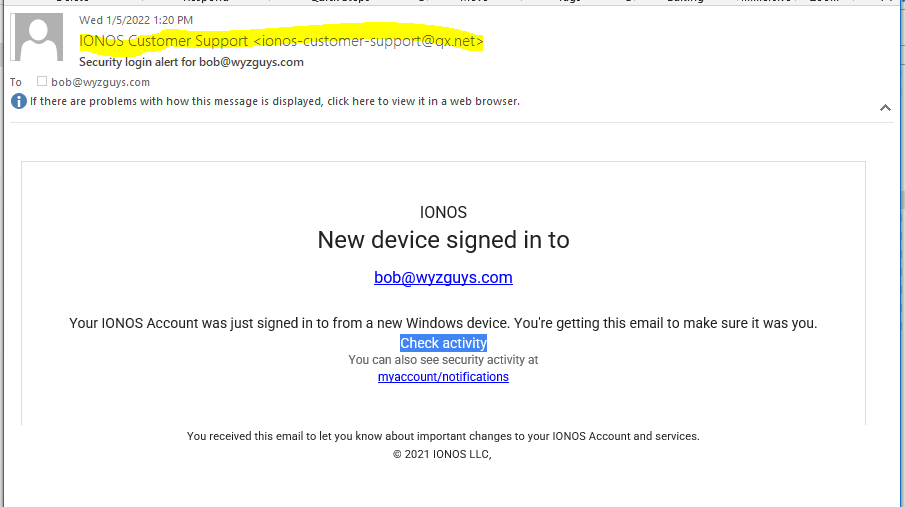
IONOS Security Alert
And here is another phish of the credential stealing variety. The sender email is spoofed from an address that could look authentic enough to fool the target. The Check Activity Link goes tohttps://www.lemeiesta.com/data/sightseeing/image/ionos/login.php?email=bob@wyzguys.com. Here is the email
The lesson here is to avoid links in even legitimate looking emails, and just open your account from the website, and check for any activity that way.
Share
JAN










About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com