Phishing Email Alerts
Catch of the Day: OneDrive – DocuSign EFT Phish
Chef’s Special: TSA PreCheck Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
OneDrive – DocuSign EFT Phish
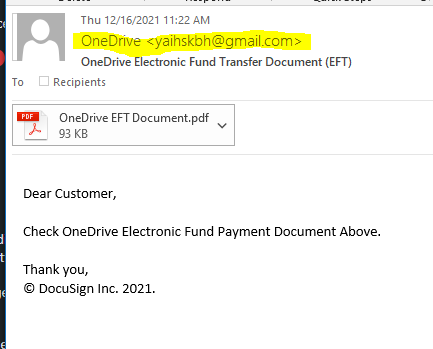
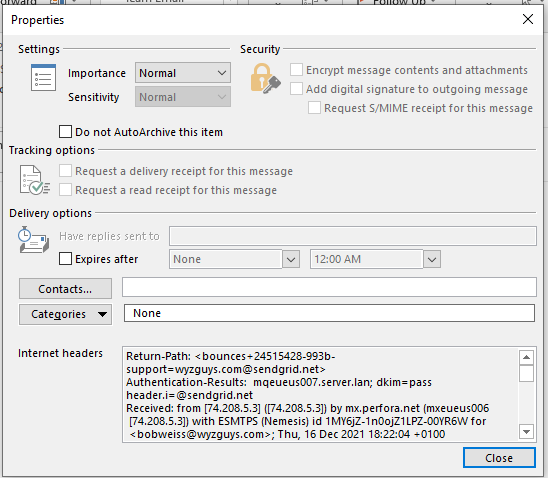
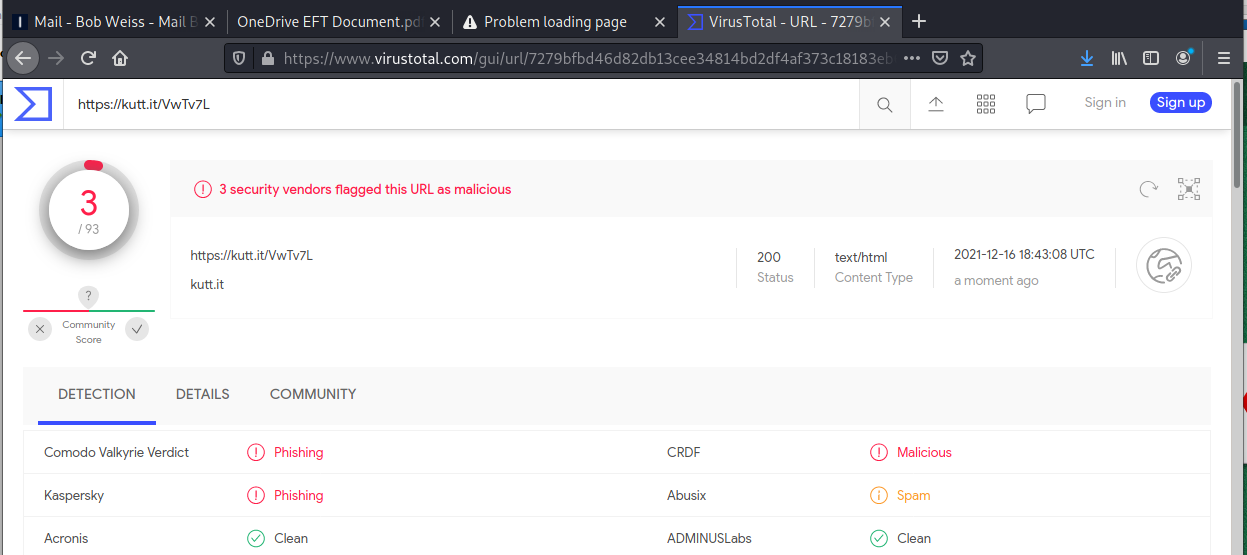
This is a strange credential harvesting exploit. I received the email below, and opened the attachment in Kali. The PDF file had an active button the resolved to https://kutt.it/VwTv7L. My attempts to connect resulted in an unable to connect error message from Firefox. The screen shots are below.
The email
The email headers
The attachments
The PDF attachment with active button link.
Based on the instructions in the attachment, this would have been a fairly sophisticated credential and personal information harvesting exploit, but it was already taken down by the time I got to investigating it. This seems to be happening more frequently
I checked the document and the embedded link on VirusTotal. While the document came up clean, the link was definitely identified as a malicious phishing link.
Tricky New TSA PreCheck Scam Steals Your Personal and Credit Card Details
Doing one of the best jobs impersonating a website ever seen, this new scam attempts to take those renewing or initially signing up through a believable process that most would fall for.
Most of the time, impersonation scams take you to a “website” that’s more than a single web page designed to look like the login page of the impersonated brand. But a new scam centered around registering for or renewing with TSA PreCheck takes the impersonation website to an entirely new level.
According to security researchers at Abnormal Security, this new scam starts out as wonky as most phishing scams with an email that doesn’t quite feel like it’s really from the TSA.
But where it gets interesting is when potential victims click the link and are taken to a pretty believable TSA registration site.
According to Abnormal Security, the scammer went through the trouble of not just collecting the salient personal details they can misuse later, but went as far as to ask nearly all the same questions found in the actual application.
And unlike most scams, they are attempting to take your credit card where payment is solicited for up front. This scam takes “payment” when it normally would – at the end of the process. This scam is one of the reasons KnowBe4 exists – to educate users through new-school security awareness training so they won’t be fooled by these kinds of scams. The sender email address and email copy are dead giveaways – something well-trained users will spot a mile away, avoiding the scam all together.
Check out the screenshots at this blog post:
https://blog.knowbe4.com/new-tsa-precheck-scam-seeks-to-collect-your-personal-and-credit-card-details
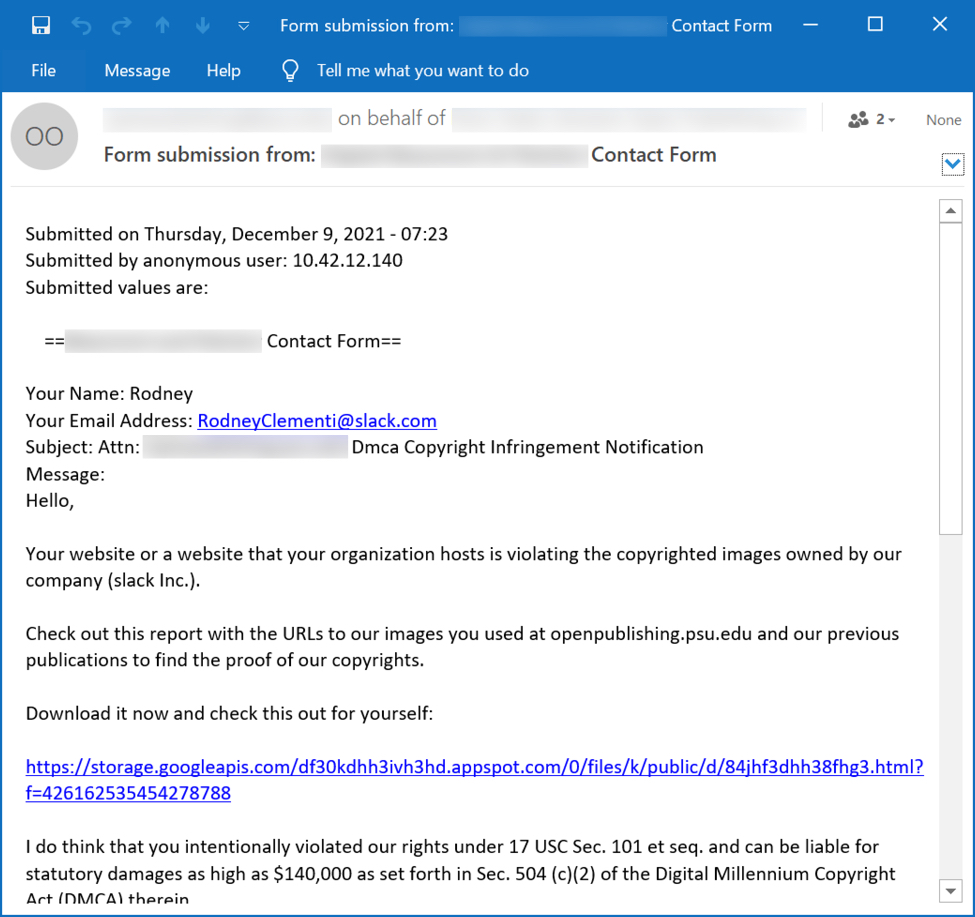
How “Contact Form” Phishing Campaigns Work
“Contact Forms” is a campaign that uses a web site’s contact form to email malicious links disguised as some sort of legal complaint. We’ve seen this campaign push BazarLoader malware and distribute Sliver, but recently it’s been pushing IcedID (Bokbot). Most of the time, the Contact Forms campaign uses a “Stolen Images Evidence” theme, with emails stating a supposed violation of the Digital Millennium Copyright Act (DMCA). Below is an example seen on December 9th, 2021. More…
Phishing Reported in IKEA’s Internal Email System
IKEA has been working to contain a continuing phishing campaign that’s afflicting the furniture and houseware chain’s internal email system. BleepingComputer describes it as a “reply-chain email attack.” This form of attack is unusual but not unknown. The attackers obtain a legitimate corporate email and reply to it.
“As the reply-chain emails are legitimate emails from a company,” they explain, “and are commonly sent from compromised email accounts and internal servers, recipients will trust the email and be more likely to open the malicious documents.”
“There is an ongoing cyber-attack that is targeting Inter IKEA mailboxes. Other IKEA organisations, suppliers, and business partners are compromised by the same attack and are further spreading malicious emails to persons in Inter IKEA,” explained an internal email sent to IKEA employees and seen by BleepingComputer.
“This means that the attack can come via email from someone that you work with, from any external organization, and as a reply to an already ongoing conversations. It is therefore difficult to detect, for which we ask you to be extra cautious.”
The malicious emails have tended to trip filters designed to quarantine threats. But they’re convincing enough to induce employees to release them, quite innocently, from quarantine. IKEA is taking steps to preclude that possibility. IKEA has explained this to the retailer’s employees:
“Our email filters can identify some of the malicious emails and quarantine them. Due to that the email could be a reply to an ongoing conversation, it’s easy to think that the email filter made a mistake and release the email from quarantine. We are therefore until further notice disabling the possibility for everyone to release emails from quarantine.”
As is usually the case, a trained and well-informed employee seems to be the last line of defense. The malicious reply-chain emails do carry certain marks that might alert employees to the possibility they’re being subjected to phishing, and IKEA is working to raise awareness of those marks. For one thing, the links the phishing emails contain end with seven digits.
How the attackers have succeeded in compromising the email accounts isn’t clear. In other cases attackers have exploited ProxyShell and ProxyLogin vulnerabilities to compromise Microsoft Exchange Servers. IKEA has been tight-lipped about the incident, and it’s unknown whether the company’s internal servers were compromised.
Blog post with links: https://blog.knowbe4.com/phishing-reported-in-ikeas-internal-email-system
Share
DEC







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com