Phishing Email Alerts
Catch of the Day: Nigerian Princess Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Nigerian Princess Phish
Sometimes the old ways are the best. Today’s Phish Fry takes a deeper look at an oldie but a goodie, the Nigerian Prince or 419 campaign. This is a straight up social engineering exploit. It usually involves a story of untimely death, inheritance, lottery winnings, and other unexpected sources of generational money. The story always involves the transfer of large sums to you bank by these generous strangers. The goal of these people is to get your banking information so they can relieve you of savings. The one we are looking at today is fairly typical.
I do not see a lot of these types of 419 Nigerian Prince phishing emails any more. I would like too think that these exploits have been explained enough that no one would fall for it, but the fact that the cybercriminals are still doing this indicates that it still works well enough.
The social engineering aspects of this particular exploit rests on a sad story, Christian religious beliefs, our natural desire to help, and of course, greed. A strange blend.
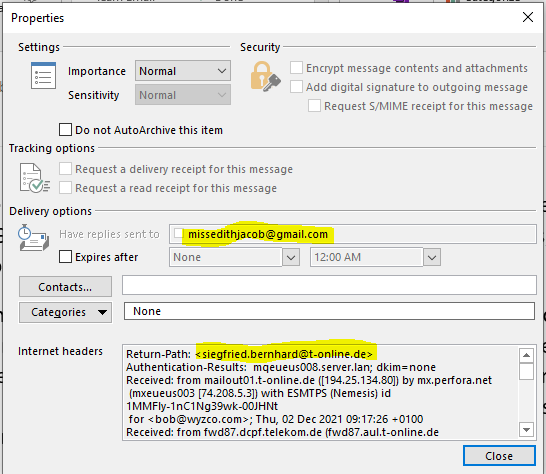
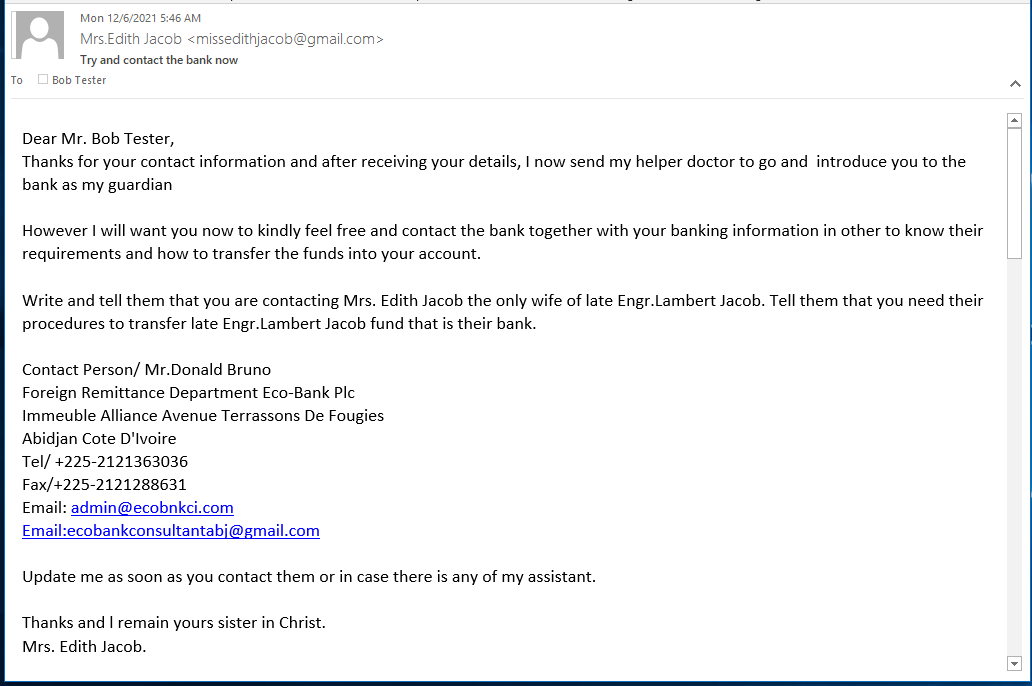
Some interesting bits show up in the email headers. The sending email account is Edith Jacob <siegfried.berhard@t-online,de> and is apparently a spoofed or hijacked email account. T-Online.de is the largest German news site, and provides public email account services. Importantly, the return address is <missedithjacob@gmail.com>. This basically switches the victim to a different email account for the next step in the exploit, the reply.
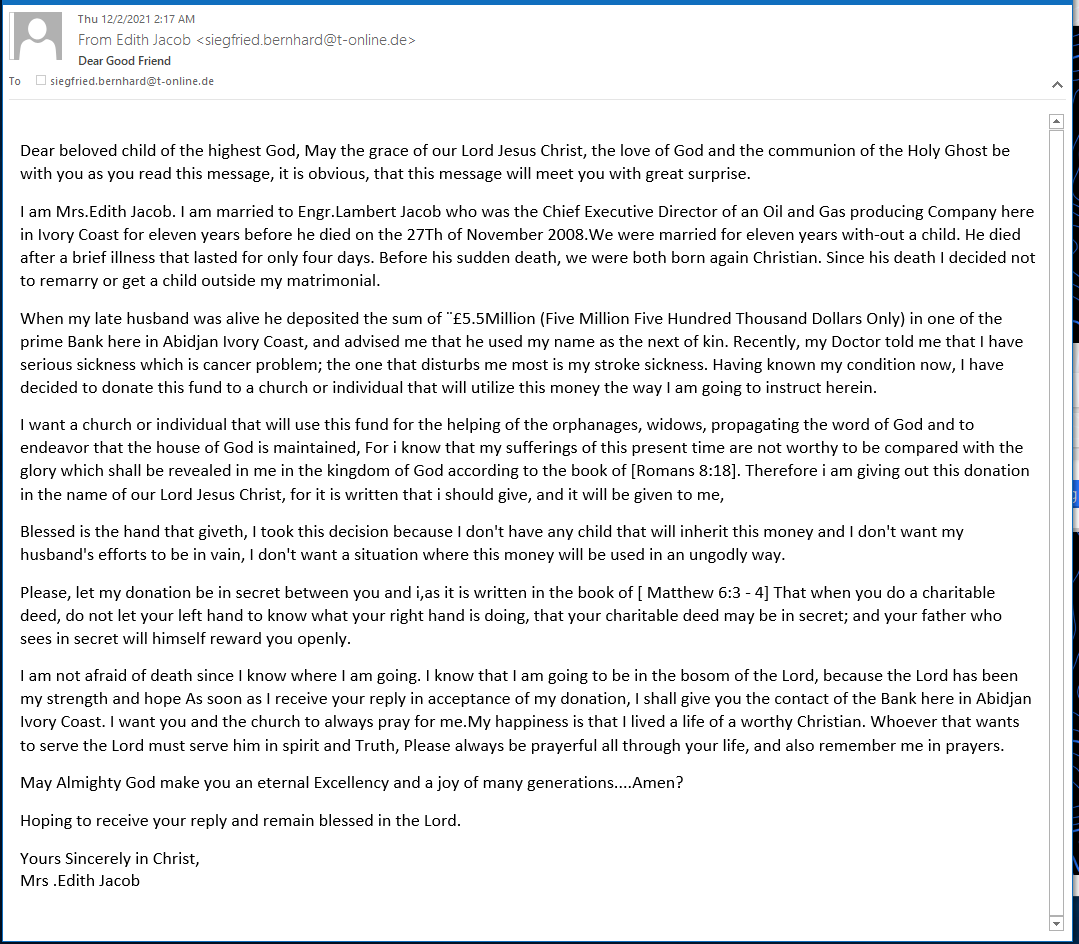
Here is the email I received. You can be assured that receiving the $5.5 million dollars will never happen.
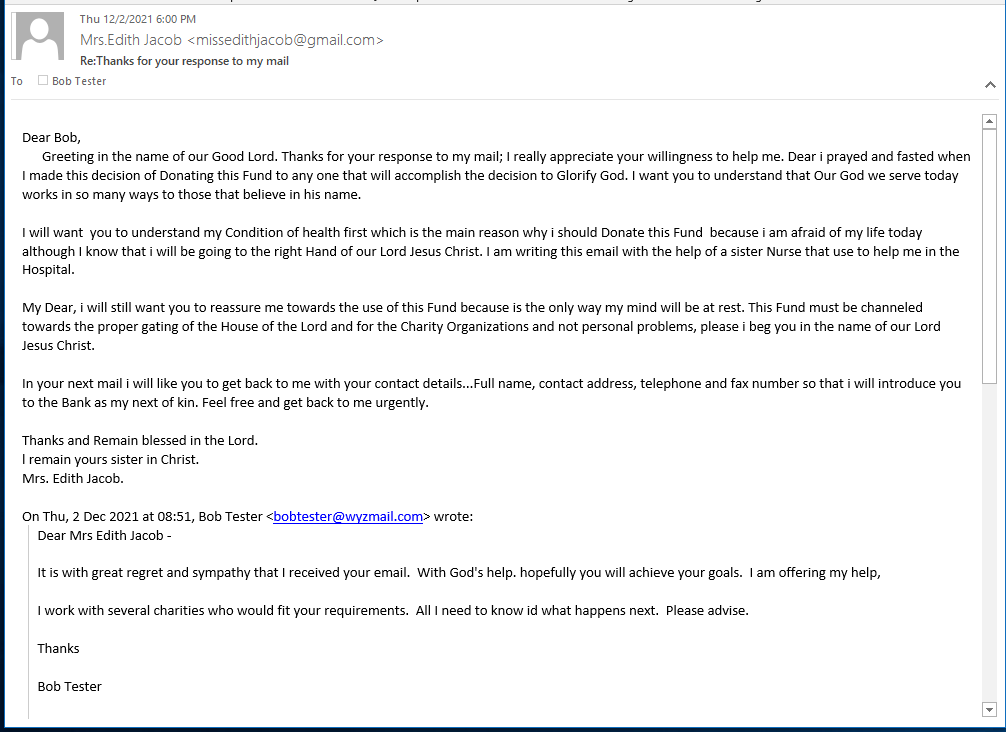
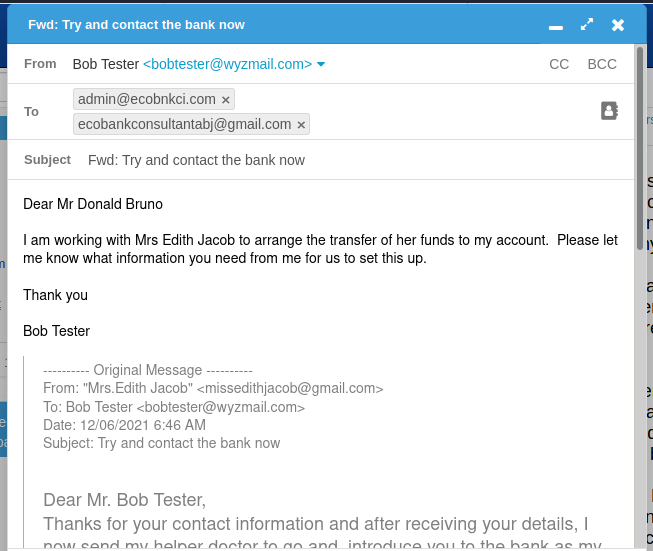
Here is the rest of the exchange with Mrs. Edith Jacob and her cohorts.
I created an alias Bob Tester to use during this investigation
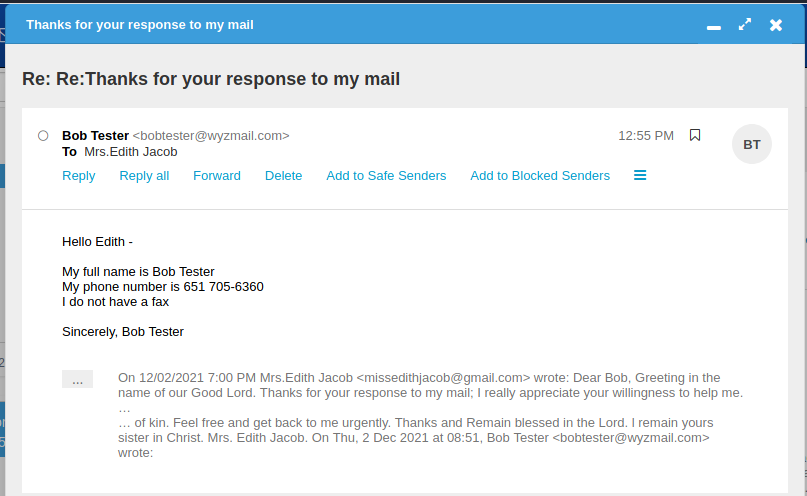
Here begins the request for personal information.
This is the point where I need to stop the process. The information they are looking for not only allows them to transfer money into your account, but also OUT of your account.
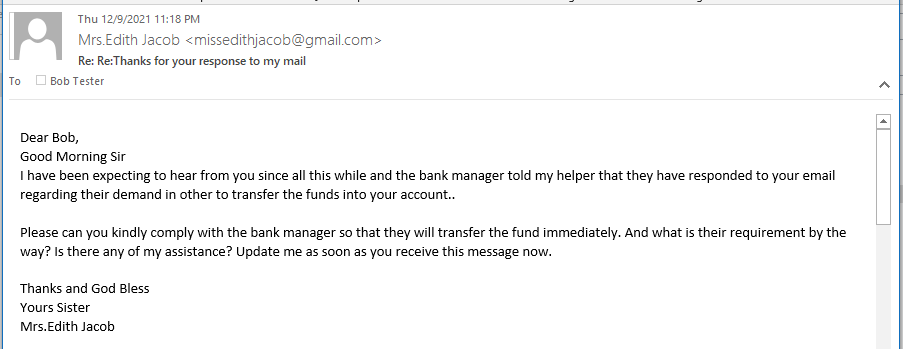
Since I have not be responsive, Edith has sent me the above email, but I am out.
Please do the smart thing, and disregard messages like this one. There are no generous strangers waiting to send you millions of dollars.
ShareDEC







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com