Phishing Email Alerts
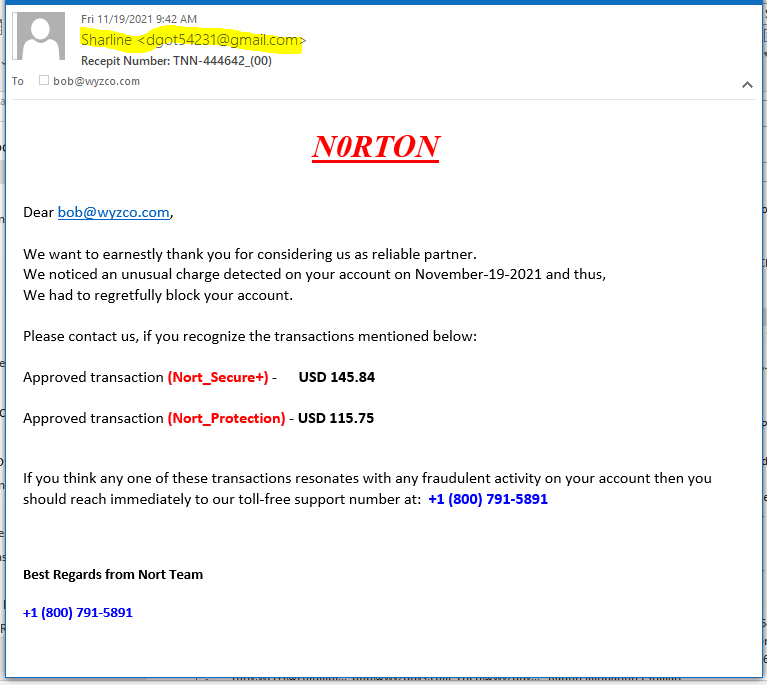
Catch of the Day: N0rton Renewal Phish
Chef’s Special: Fake Retail Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
N0RTON Renewal Phish
I am seeing so many phish like this one, where there is a ridiculous purchase, and a cheery suggestion to call the toll-free number if you want to debate the issue. An interesting move away from automated exploits back to exploits that depend on the skill of humans.
The sender’s email is a Gmail account, not likely to be legitimate.
N0RTON is misspelled, using a zero rather than a capital O
The story is sort of weird too, the warning is one you might expect from a credit card company, not the “vendor.”
Malicious Retail Phishing Sites Spike Ahead of Shopping Holidays
Researchers at Check Point have observed a record number of malicious phishing shopping websites that have been set up over the past two months. The researchers assume these sites were registered in anticipation of Black Friday and Cyber Monday in the US, Single’s Day in China, and Click Frenzy in Australia.
“Since the beginning of October 2021, CPR researchers witnessed the highest amount of malicious websites related to shopping and sales offers,” Check Point says. “On average, over 5300 different websites per week were spotted, marking a 178% increase, compared to the average in 2021, thus far.”
Check Point offers the following advice to help people avoid falling for these attacks:
- “Always shop from an authentic, reliable source. Do not click on promotional links you get over email or social media. Proactively Google search your desired retail or brand
- “Be attentive for lookalike domains. You should notice spelling accuracy in emails or websites, and note unfamiliar email senders or peculiar email addresses you receive promotions from
- “Too good to happen shopping offers are indeed too good to happen. A new iPad will NOT go on an 80% discount this season, unfortunately.”
The researchers add that people should always be suspicious of unexpected password reset emails. “Always be attentive to password reset emails, especially when volumes of traffic online are at a peak, like the November shopping season,” Check Point says. “If you receive an uninvited password reset email, always visit the website directly (don’t click on embedded links) and change your password to something different on that site.
Not knowing your password is, of course, the problem that cybercriminals face when trying to gain access to your online accounts. By sending a fake password reset email that directs you to a lookalike phishing site, they can convince you to type in your account credentials and send those to them.”
Blog post with links:
https://blog.knowbe4.com/malicious-retail-phishing-sites-spike-ahead-of-shopping-holidays
Phishing Emails Use Small Font Size To Bypass Security Filters
Researchers at Avanan have spotted phishing emails that use a font size of one to fool email security scanners. The emails appear to be password expiration notifications from Microsoft 365. The attackers have inserted benign links that are invisible to the human eye, but trick security scanners into viewing the email as a legitimate marketing email.
“In this attack, hackers utilize a number of obfuscation techniques to get a credential harvesting page through to the inbox,” the researchers write. “First, all links are hidden within the CSS. This confuses natural language filters. Natural language filters see random text; human readers see what the attackers want them to see. In addition, hackers put links within the (font) tag, and brought the font size down to one. This breaks semantic analysis, which leads many solutions to treat it as a marketing email, as opposed to phishing. Beyond that, there are invalid parameters, as the ‘Padding Left’ is set to ‘;’ further confusing scanners.”
Avanan concludes that the phishing emails themselves appear suspicious, so a trained user would be able to spot them as malicious. The emails simply state, “Notification for Password 365. Access To Your Email will be Expired.”
“To the end-user, this email looks like a standard request from their IT department,” the researchers write. “The email is designed to fool both Natural Language Processing and human eyes. For a user to spot this attack, they should rely on their phishing training. They should notice the stilted grammar, such as ‘Notification Microsoft 365’ as a red flag. They should also ask their own IT department before resetting any passwords.”
Thus, insecurity by obscurity. Attackers are constantly coming up with new ways to bypass email security filters. New-school security awareness training can give your employees a healthy level of skepticism so they can avoid falling for social engineering attacks.
Blog post with links:
https://blog.knowbe4.com/phishing-emails-use-small-font-size-to-bypass-security-filters
Share
NOV





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com