 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: This is NOT a phish, it is legit
Chef’s Special: This IS a phish, EFT payment advice
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox.
This is NOT a phish, it is legit
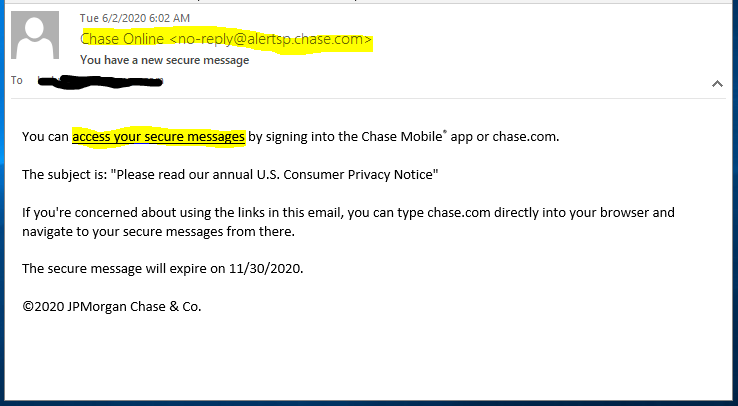
I spend a lot of time showing you what a fake email looks like. This time, I am showing you a legitimate email that looks similar to many phish I have seen, but it legitimate. Here’s how to tell:
- Legitimate email domain for the sender (alertsp.chase.com)
- “Access your secure messages” resolves to https://www.chase<dot>com/securemessages. This is a legitimate Chase landing page.
- They recommend signing in directly, instead of using the link.
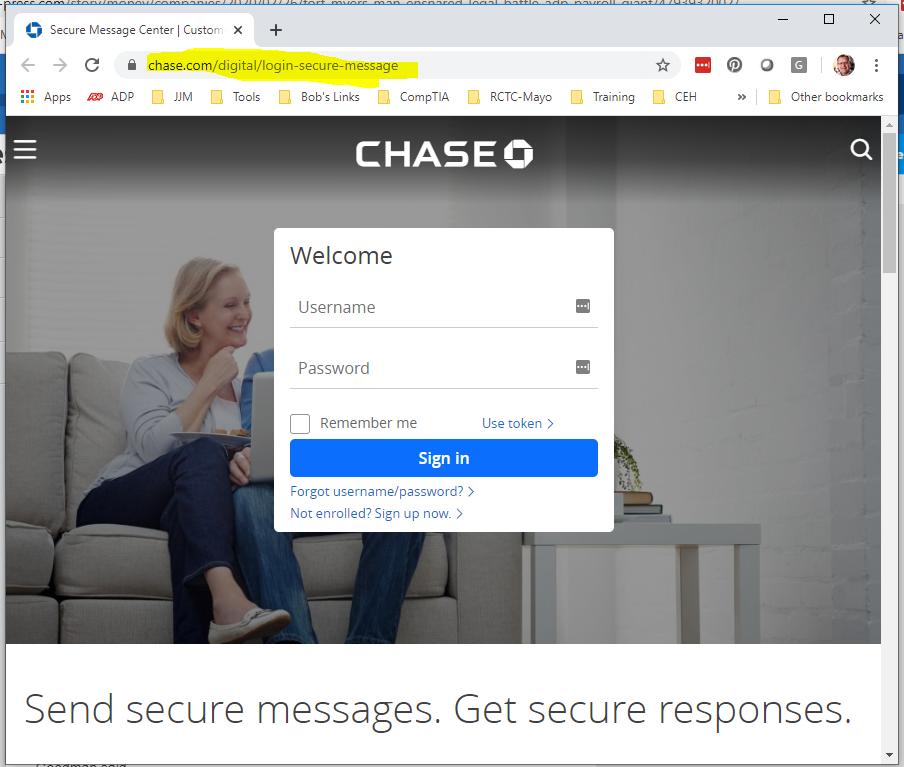
Legitimate landing page. Notice the chase.com web address.
This IS a phish, EFT payment advice
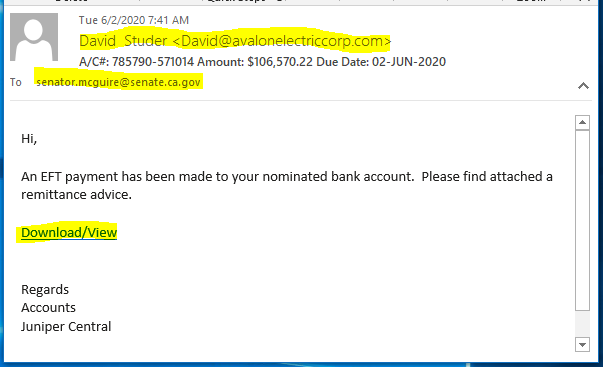
This fake email is masquerading as an EFT payment advice. Look how much is different from the legitimate email above.
- Sending email domain is avalonelectric<dot>com, but the signature is from Juniper Central, a mismatch
- The recipient is a state senator from California. Not sure why this came to me.
- The Download/View link resolves to https://pastorialcommunicationsnetwork.lpages.co/. Again, a mismatch from both the sending domain and the signature.
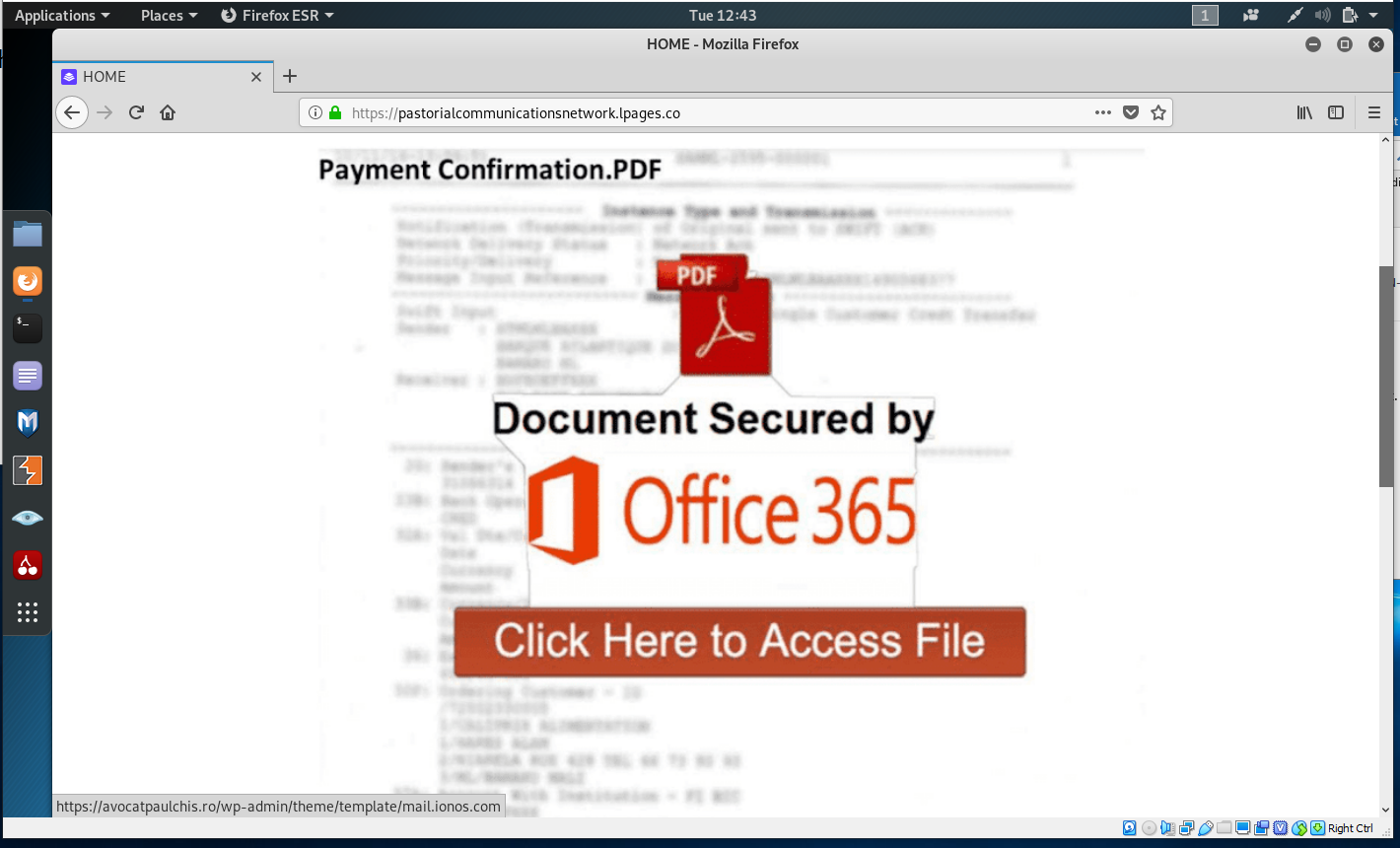
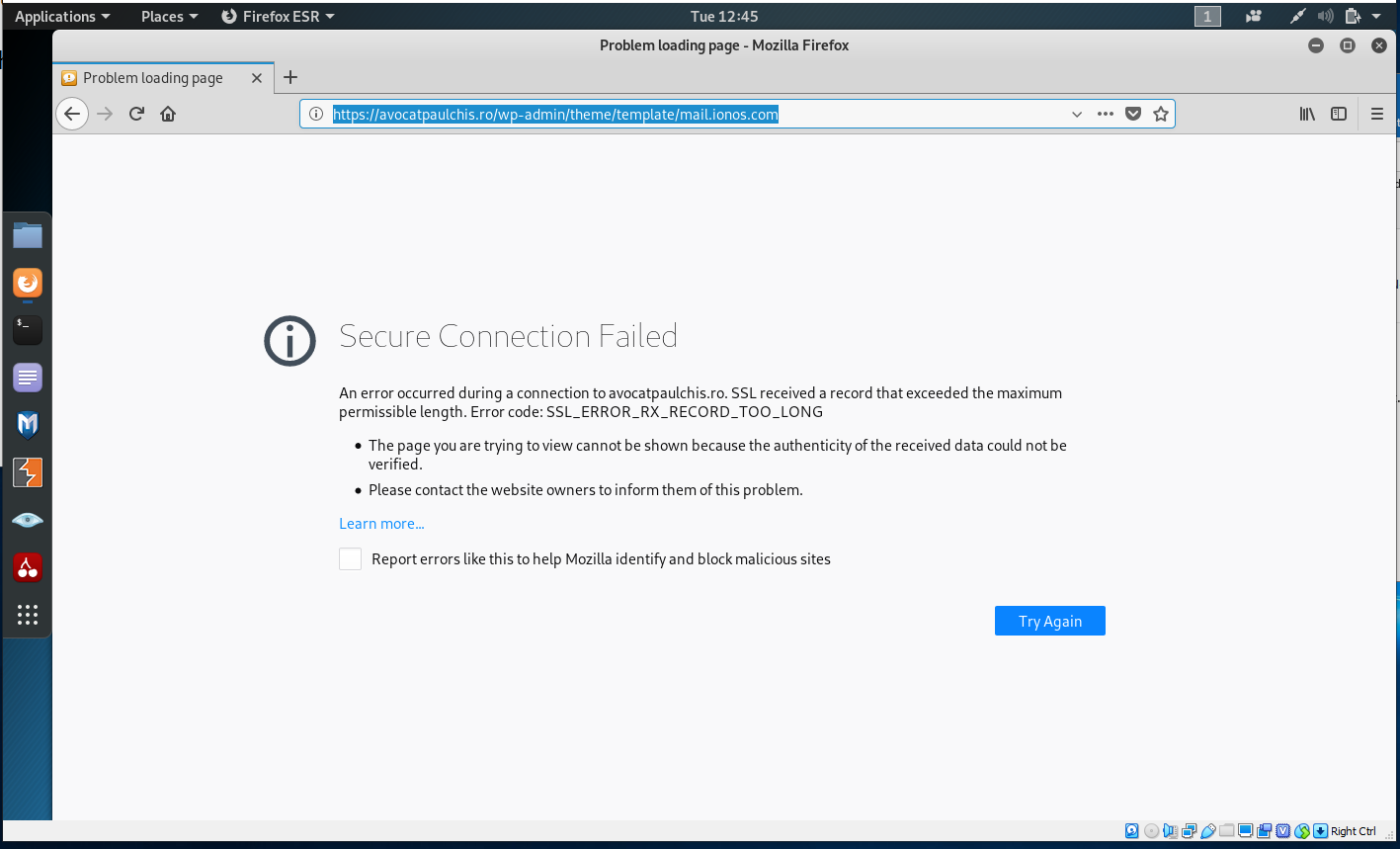
Here is the first landing page
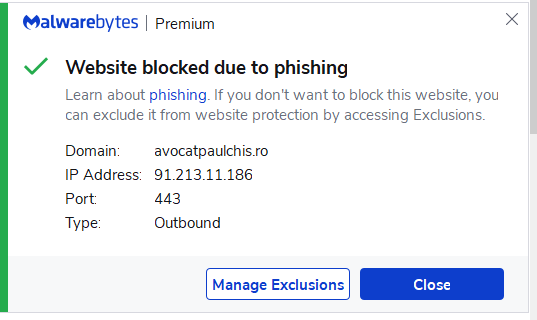
Click Here to Access File took me to https://avocatpaulchis.ro/wp-admin/theme/template/mail.ionos.com. Clicking on Try Again popped up a Malwarebytes phishing alert.
Another reason I really like and strongly recommend Malwarebytes.
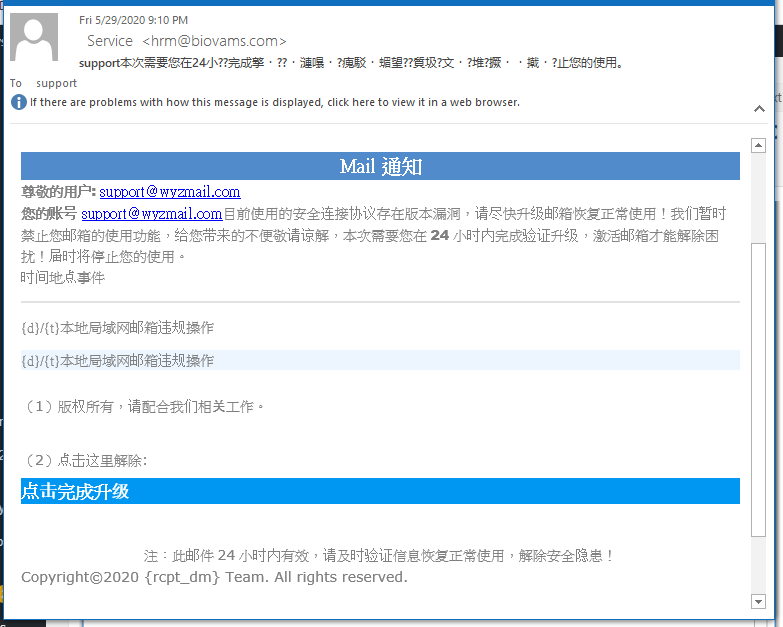
Chinese Support Phish
Oh those pesky Chinese – first the coronavirus, then falling space junk, and now fake support phish. This one was easy to identify as a phish. I used Google Translate read the message.
The text translation:
Dear user: support@wyzmail.com Your account support@wyzmail.com currently uses a security connection protocol with a version vulnerability, please upgrade your mailbox as soon as possible to restore normal use! We temporarily ban the use of your mailbox. Please forgive me for the inconvenience. This time you need to complete the verification upgrade within 24 hours to activate the mailbox to relieve the trouble! At that time, your use will be stopped. Time and place events {d} / {t} Local LAN mailbox violation operation {d} / {t} Local LAN mailbox violation operation (1) Copyright, please cooperate with our related work. (2) Click here to cancel:
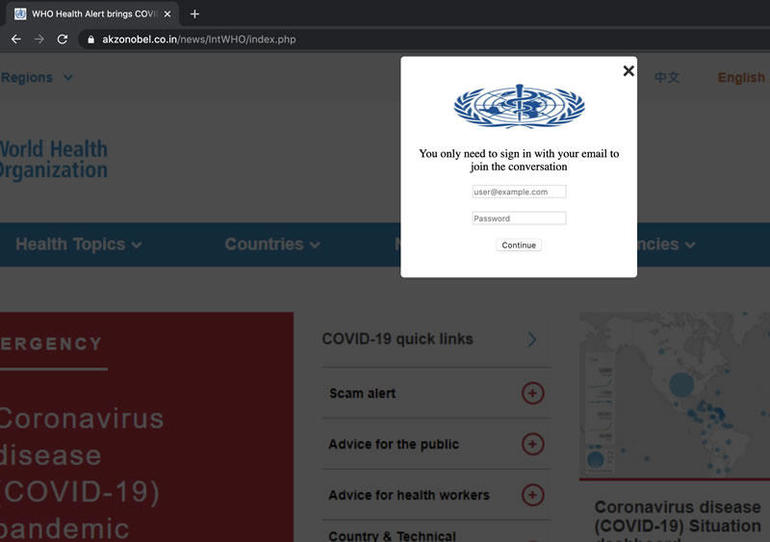
Phishing attack spoofs World Health Organization to steal email credentials
The malicious credential-stealing campaign is aimed at people in general in an effort to grab their email addresses and passwords, says Abnormal Security.
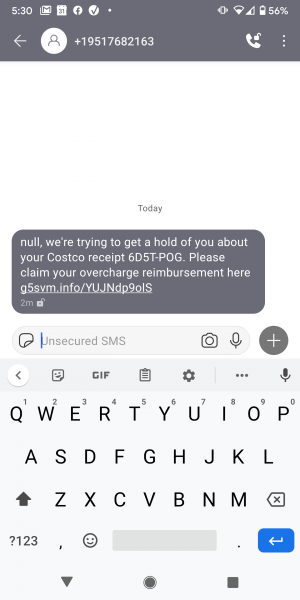
Fake CostCo Refund Smish
This text message is fake. Do not click on the link.
Hurricane-Related Email Scams
Original release date: June 1, 2020
June 1 marks the official start of the 2020 Atlantic hurricane season. The Cybersecurity and Infrastructure Security Agency (CISA) warns users to remain on alert for malicious cyber activity targeting potential disaster victims and charitable donors following a hurricane. Fraudulent emails—often containing malicious links or attachments—are common after major natural disasters. Exercise caution in handling emails with hurricane-related subject lines, attachments, or hyperlinks. In addition, be wary of social media pleas, texts, or door-to-door solicitations relating to severe weather events.
To avoid becoming victims of malicious activity, users and administrators should review the following resources and take preventative measures.
- Staying Alert to Disaster-related Scams
- Before Giving to a Charity
- Staying Safe on Social Networking Sites
- Avoiding Social Engineering and Phishing Attacks
- Using Caution with Email Attachments
If you believe you have been a victim of cybercrime, file a complaint with the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3) at www.ic3.gov.
Share
JUN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com