Phishing Email Alerts
Catch of the Day: Fax Phish
Chef’s Special: Voicemail Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
International Internet Day
On October 29th, we celebrate the most important invention in human history.
While the internet may not have been possible without a million other monumental inventions that came before it, it’s hard to find any other invention that has had such a monumental impact on mankind. That’s why, since October 29, 2005, we’ve been celebrating the anniversary of the first internet transmission. It is a chance to celebrate the people who helped build the internet, while also giving us a moment to reflect on all the ways that it has changed our lives forever.
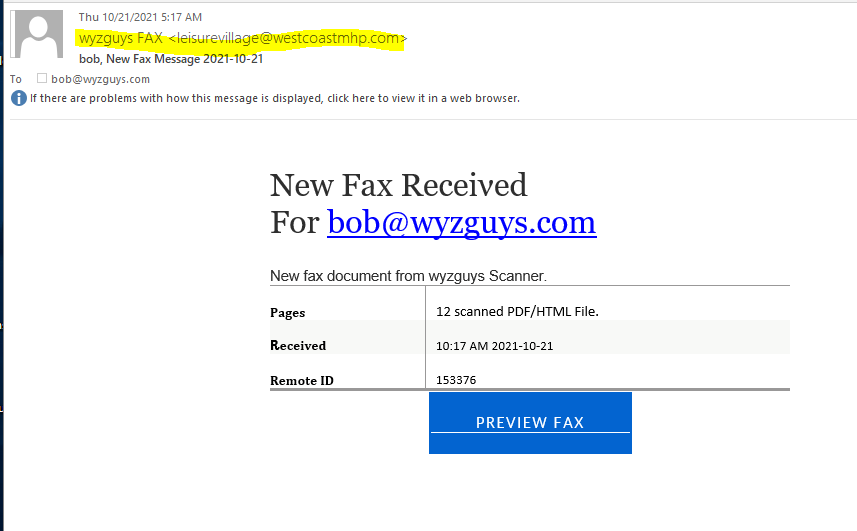
Fax Phish
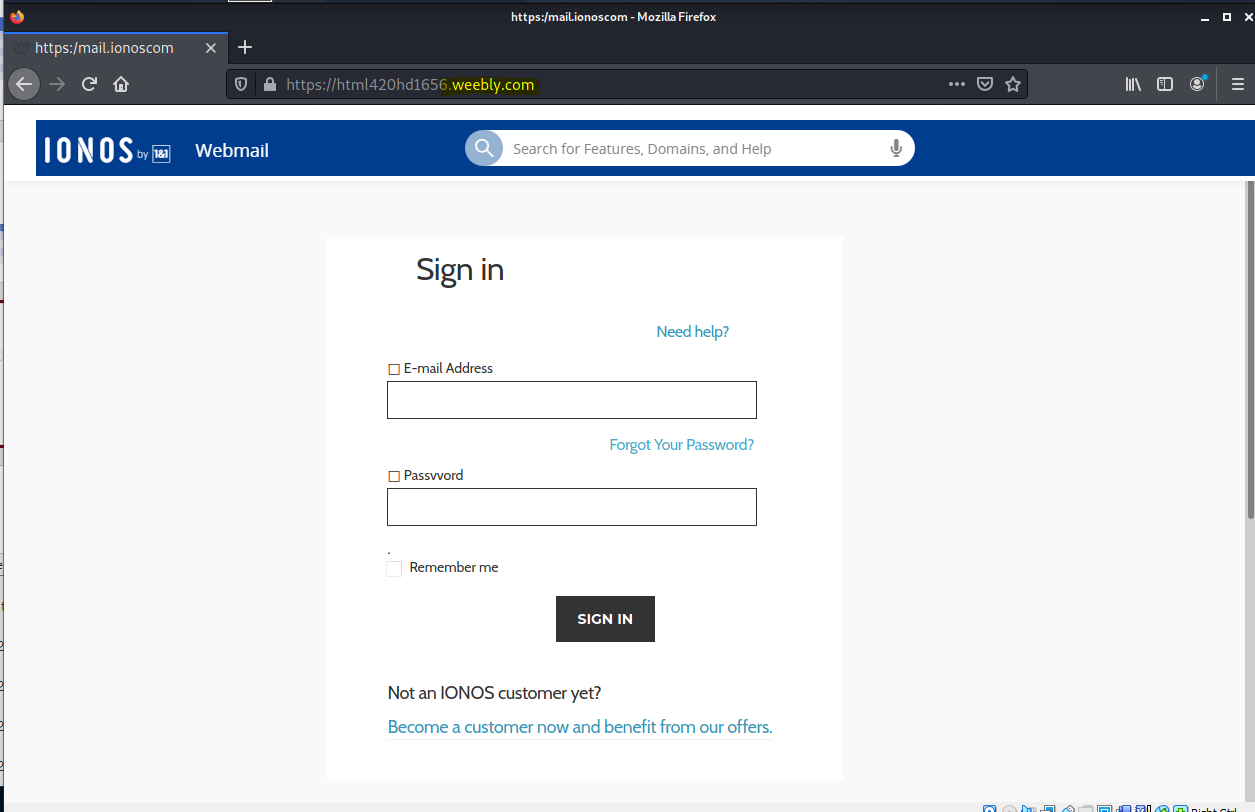
Received this New Fax Received advice. The sender email was the usual first clue, and the Preview Fax but resolved to a Weebly web site at https://html420hd1656.weebly.com/.
The first landing page was a typical credential stealing login web form.
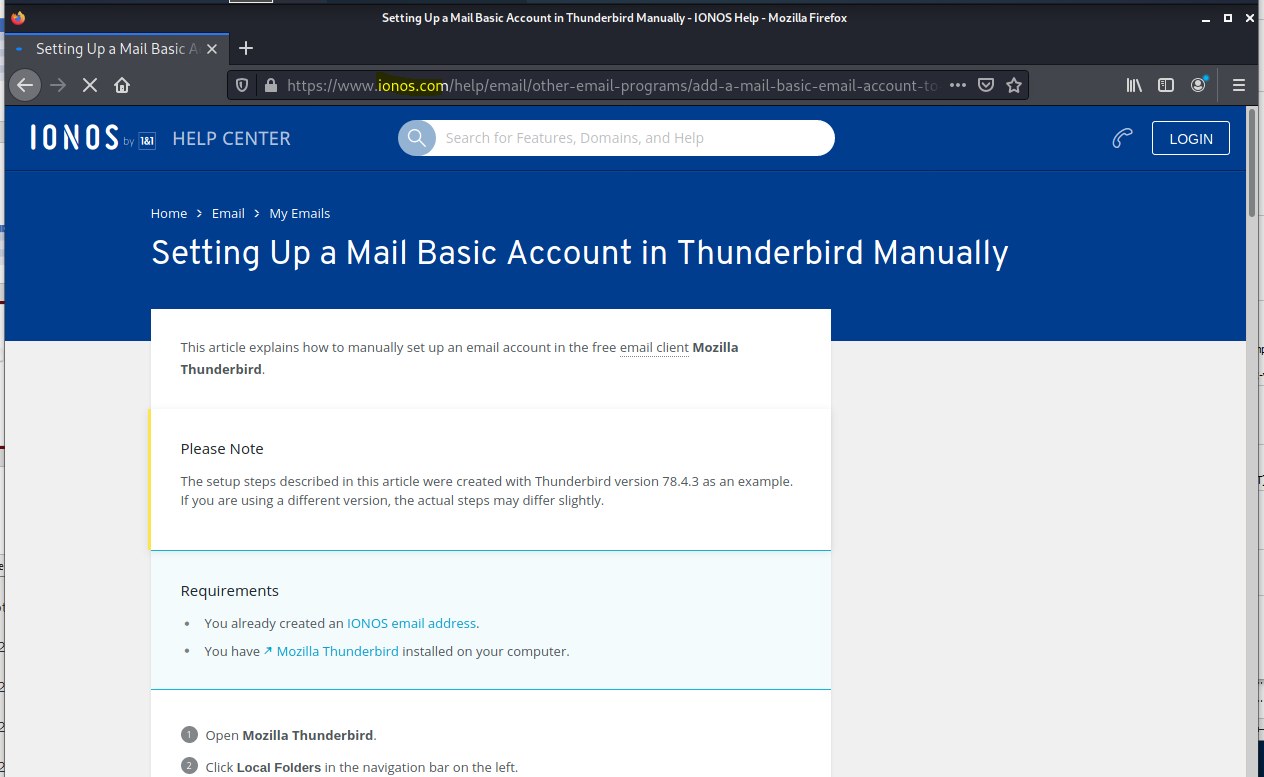
I decided to enter a fake user and password, the the Sign in button took me to an authentic IONOS help page. This bounce out to a genuine page is a good way to keep the target in the dark about having given away their user ID and password moments ago.
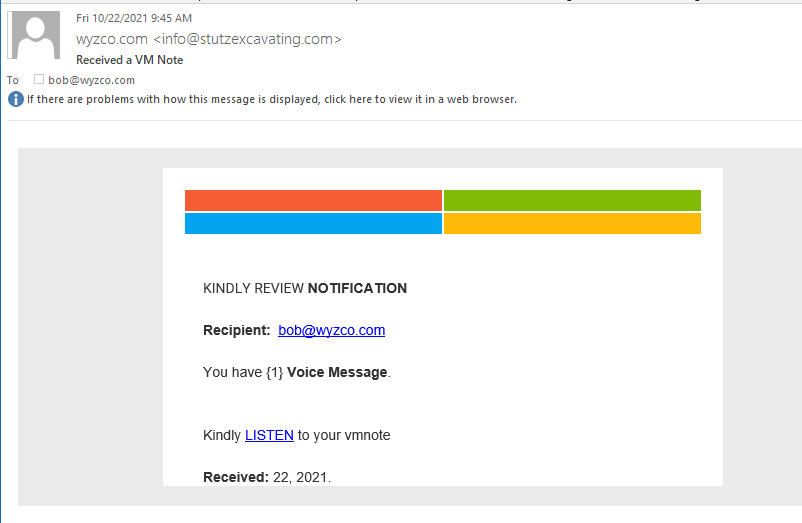
Voicemail Phish
This email arrived in my inbox. The LISTEN link resolved to https://himalayansherpa.com.au/jss/cs.html?email=bob@wyzco.com. By the time I investigated this link, not only was the landing page down, but the entire site was offline.
I tried to open just the himilayansherpa site, but got this warning from Malwarebytes.
The good news is that these hijacked sites and landing pages are being taken down quickly, before many targeted victims would have a chance to become entangled in the exploit.
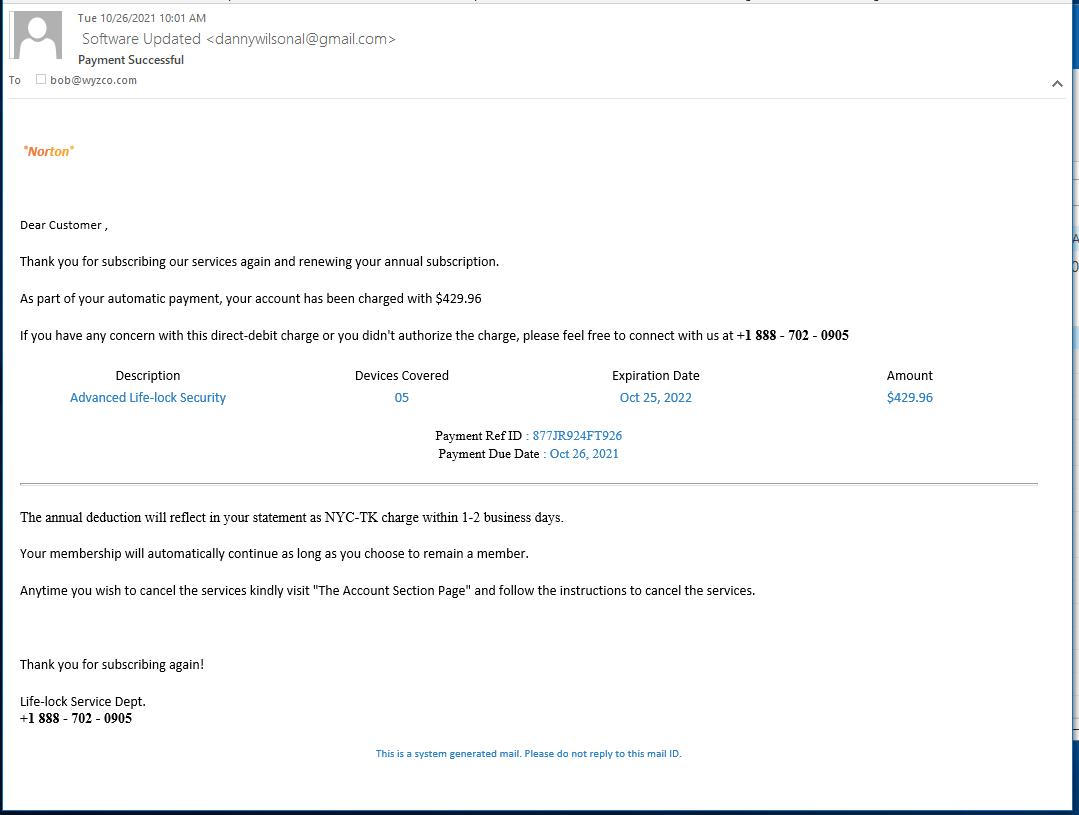
Norton Renewal Phish
Really? Is this the best they can do? This is a fairly pathetic stab at a fake renewal invoice. The goal here is to get you agitated enough over the $500 “charge” that you call the toll free support number.
Do not call the toll-free number!! I did this time, just to see if it was what I expected, and my call was answered by a delightful woman in India, who was going to “look into it” for me, would I please hold. As expected, to reverse the “payment” she would need a credit card to refund the payment to.
New Impersonation Attack Demonstrates That Threat Actors Don’t Need To Get the Logo Correct
A new trend in social engineering and impersonation emerges as cybercriminals take advantage of a user’s inability to properly identify fake corporate logos in phishing attacks.
We’ve all seen the really bad impersonation phishing email attempts (See Norton example above) – you know the ones where you can immediately tell it’s not the vendor it purports to be from. And then there are the really good ones that look perfect. But one of the needs most phishing attacks have is a need to display graphics so copied logos and branding can be displayed in order to fool the recipient.
But security researchers at anti-phishing vendor Inky have spotted an attack where scammers attempting to impersonate Verizon use symbols to represent the “check” portion of the logo, making the entirety of the “logo” appear without the need for downloading images.
You may think, “come on… that doesn’t even look like the Verizon logo at all!” and you’d be right. But new branding research around how well consumers memorize corporate logos correctly shows that most people actually remember a version of the logo enough to recognize it, but most don’t actually know exactly what the logo looks like. Using ten of the most well-known brands, it was concluded that, at best, 30% of people can draw a near-perfect version of the logo, with the average being only 16.6% of people.
This means that it’s far more likely than you think that if a phishing scammer can use some rendition of a logo, it may just be enough to fool them into thinking it’s the company they are attempting to impersonate.
Users that undergo security awareness training are far less likely to fall for phishing attacks, regardless of how spot-on the impersonation. By reinforcing the need to scrutinize unsolicited and unexpected emails for sender details, content, type of request, and – yes – branding, it’s possible to spot nearly every phish a mile away.
Blog post with screenshot and links:
https://blog.knowbe4.com/new-impersonation-attack-demonstrates-that-threat-actors-dont-need-to-get-the-logo-correct
Share
OCT






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com