Phishing Email Alerts
Catch of the Day: Amazon Fake Invoice Phish
Chef’s Special: Ultraviewer Phone Scam
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Does Your Email Provider Do This?
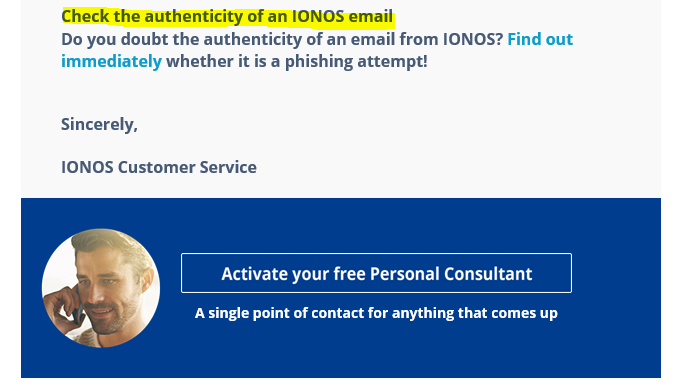
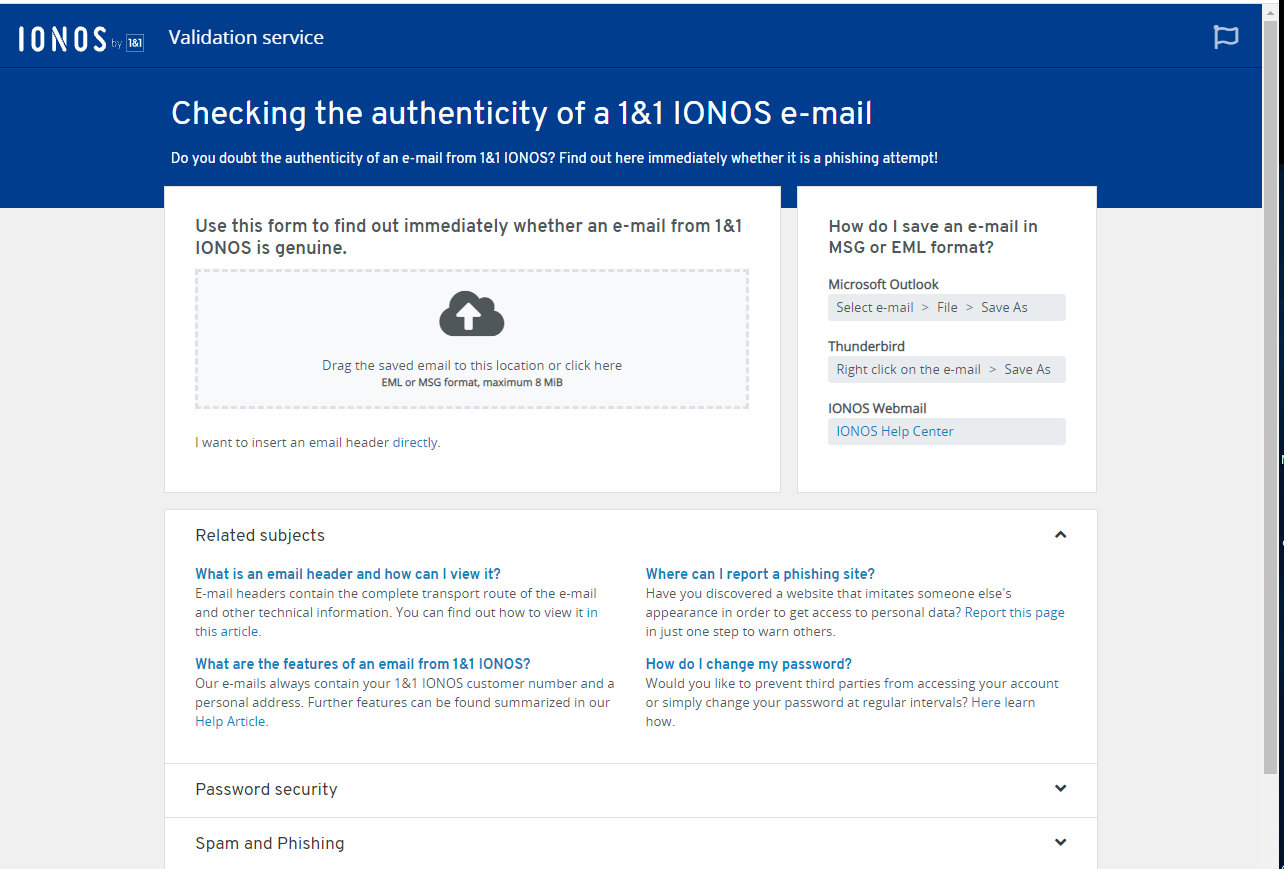
I received an email from my email and web host, IONOS. They can provide me with an email authentication service that will identify genuine IONOS emails, and fake IONOS phishing emails.
Does your email provider do this? If you are not sure, you should check. If they do you should use this service. This can help prevent the worst type of security breach, the email account hijack or business email compromise (BEC).
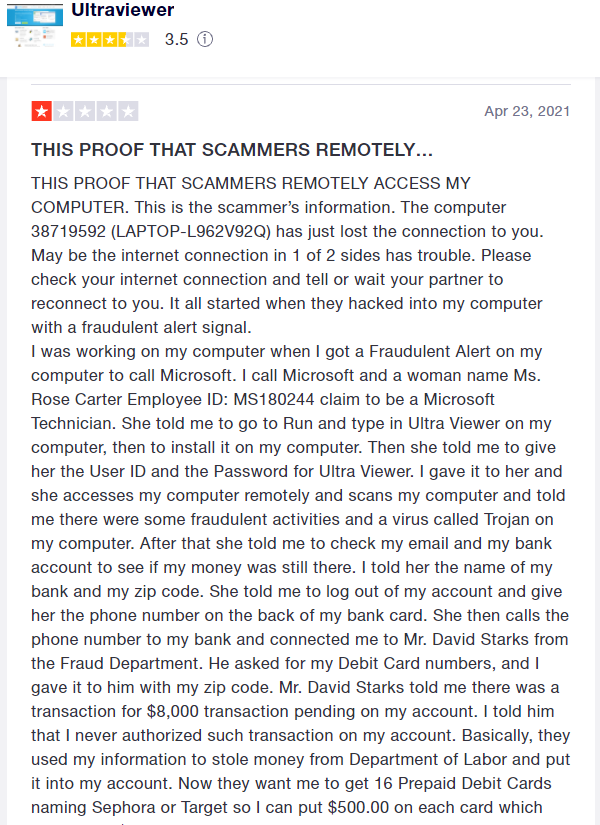
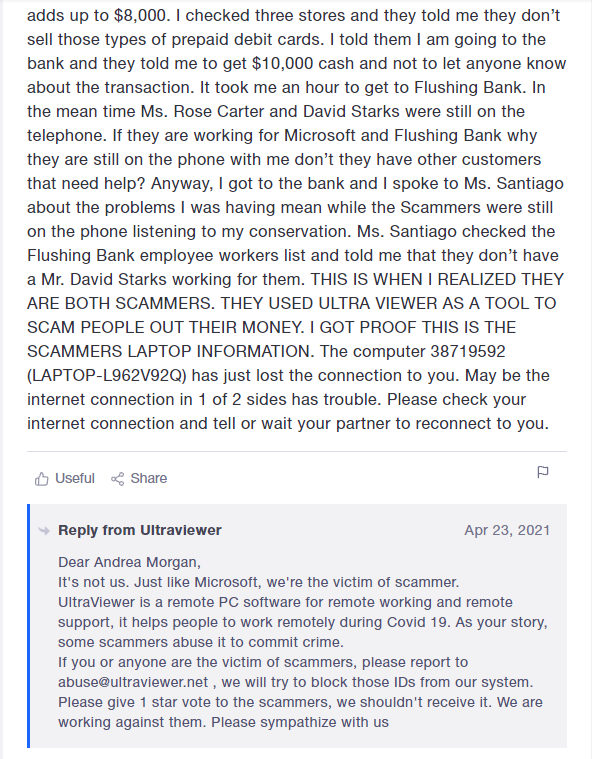
Comcast Ultraviewer Phone Scam
I had a call from a client you was called by “Comcast” and before she knew it, she had given them remote access using a product called Ultraviewer. After showing here Task Manager and Event Viewer screens that “proved” she was infected with a virus, they asked her to go to the store and purchase a gift card in the amount of $600. At this point she realized she was being scam, hung up on them, and called me. I removed Ultraviewer from Programs and Features. She was fortunate that they were only interested in the gift card. Nothing else appeared to have been changed or accessed in her computer.
I looked up Ultravier in Google and clicked on he search result for “Ultraviewer Scams.” The following story and image I copied from Trustpilot. Ultraviewer is innocent in this case. Simialr scams may use other remote control products like Teamviewer.
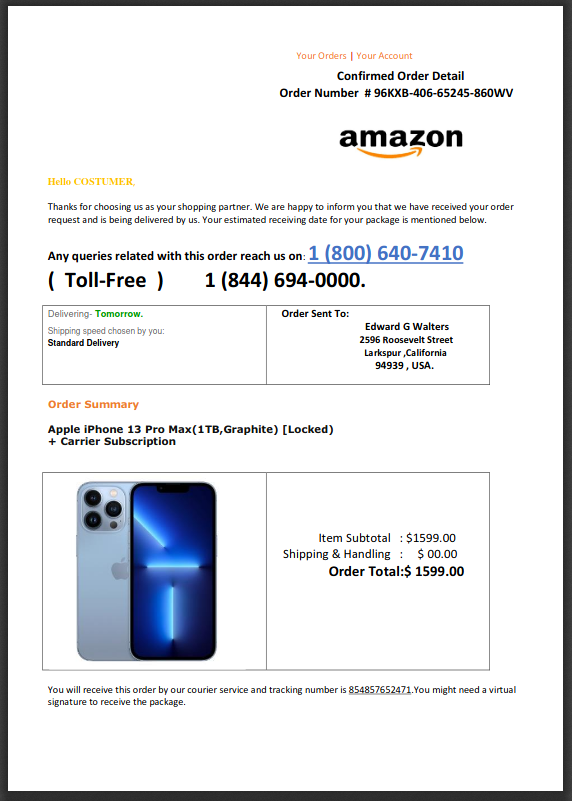
Amazon Fake Invoice Phish
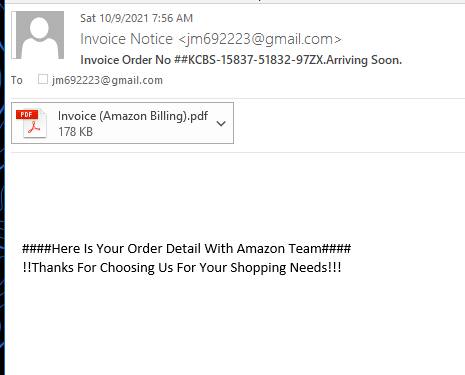
This invoice “confirms” that I spent $1500 ordering an new iPhone 13 for Edward G Walters of Larkspur California. Lucky guy. Hey Edward – Happy birthday or whatever. This exploit relies on the skills of a call center operation, rather than a hijacked website with replica login pages and web forms. This appears to be a big trend in cyber crime groups, and that would seem to indicate that people are more credible and compliant when dealing with another human being, as opposed to a robot.
Here is the email. A little spare in my opinion, but evidently it gets the job done, which is to get the recipient to open the attachment
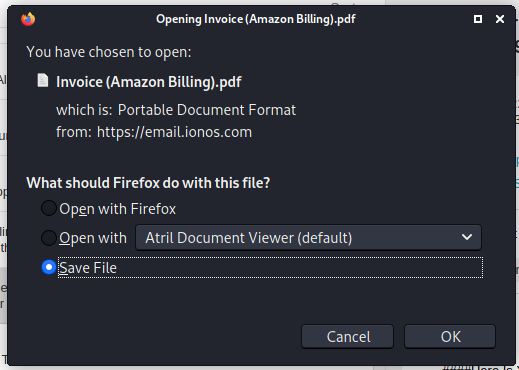
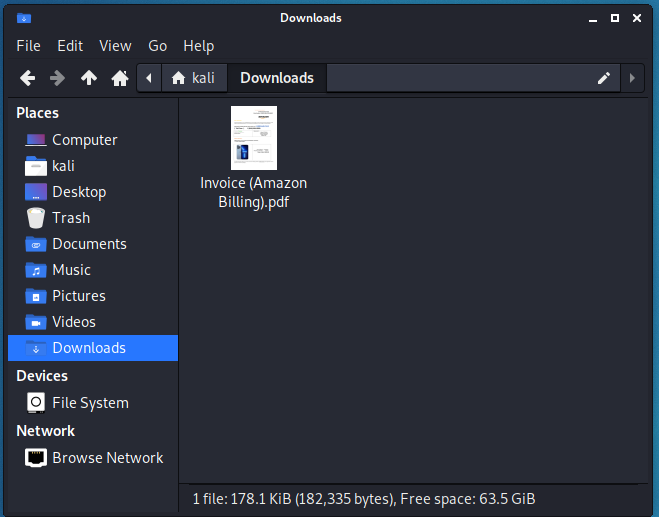
I opened this email in Kali Linux to be on the safe side, downloaded the attachment, and then uploaded it for testing at Virustotal.com
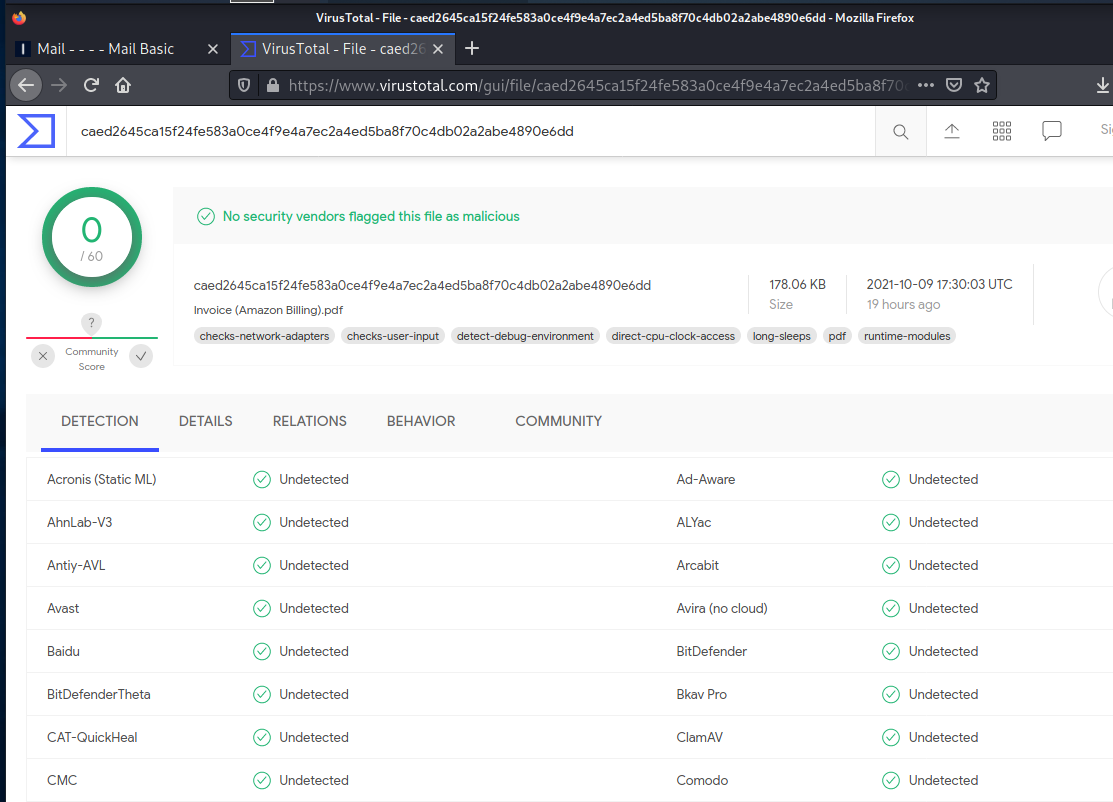
Virustotal indicated the PDF file was free prom embedded malware, so I opened the attachment, and this is what I found
If you want to see how these operators work check out this YouTube video, or search YouTube for “call center scams”
Shortened LinkedIn URLs Are Now Used as Phish Hooks
Scammers are now using shortened LinkedIn URLs to disguise phishing links, according to Jeremy Fuchs at Avanan. LinkedIn automatically shortens links that are longer than 26 characters. The URL is shortened to a “lnkd[.]in” link followed by several characters. Attackers are abusing this feature to avoid detection by users and security filters.
Avanan spotted a phishing email that states, “Good afternoon. We are having a general upgrade on our new system data for 2021, and we’ll be needing your aid to rectify the missing info below so we can deliver more accurate and reliable service.” Ironically, the bottom of the email contains a warning that email fraud is on the rise, urging users to validate the source before interacting with an email.
If a user clicks on the shortened link, they’ll be sent through several redirects before landing on a phishing page that asks them to download a PDF. By using a shortened link from a legitimate service, users are less likely to be suspicious. Using multiple redirects through harmless sites helps to fool security technologies that check for phishing pages.
“This particular email can target anyone,” Fuchs says. “Though it presents itself as a standard credential harvesting and invoice scheme, the use of a LinkedIn URL may mean that any profession—the market for LinkedIn—could click. Plus, more employees have access to billing and invoice information, meaning that a spray-and-pray campaign can be effective. Whether it’s the “lnkd[.]in” form or the https[://]www[.]linkedin[DOT]com/slink?code=aB-cDeF variation, the idea is to create a link that contains a clean page, redirecting to a phishing page.”
Avanan notes that LinkedIn is among the top ten most impersonated brands in phishing attacks, so users should be on the lookout for these types of scams. New-school security awareness training enables your employees to make smarter security decisions so they can avoid falling for stealthy phishing attacks.
Blog post with Links:
https://blog.knowbe4.com/new-tactic-shortened-linkedin-urls-are-now-used-as-phish-hooks
Share
OCT





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com