Phishing Email Alerts
Catch of the Day: Video Porn Extortion Phish
Chef’s Special: DHL Shipment Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
DHL Shipment Phish
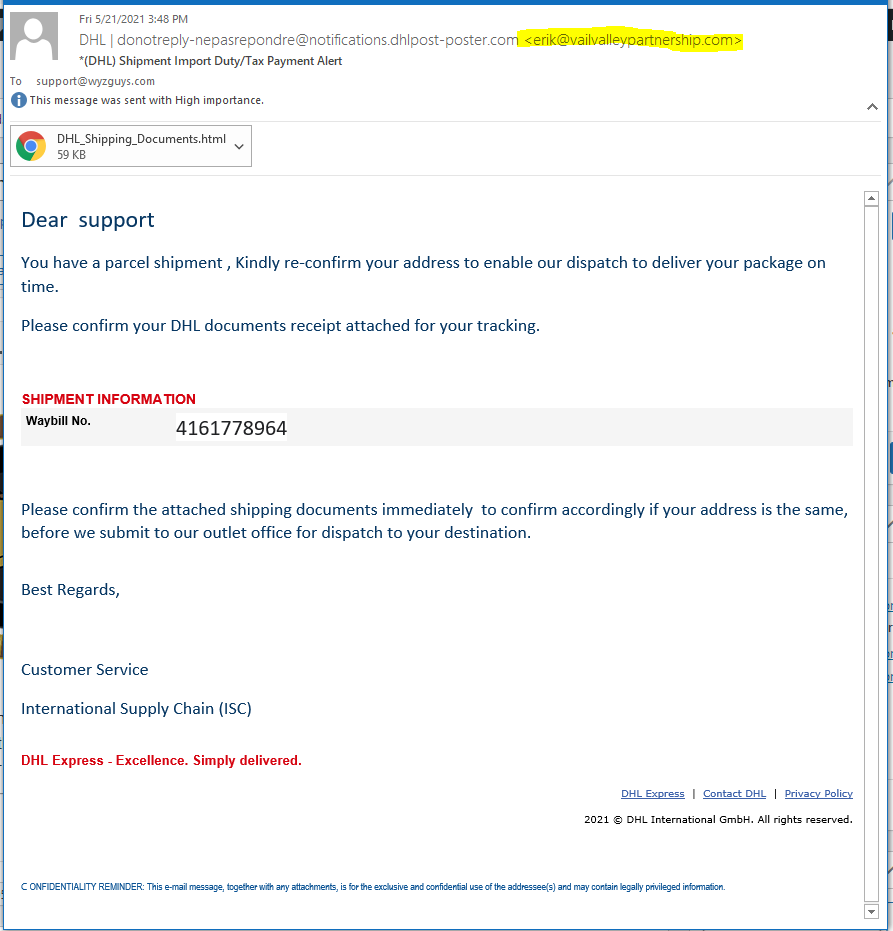
Another HTML attachment bearing a self-hosted DHL login page. Here’s the phishing email:
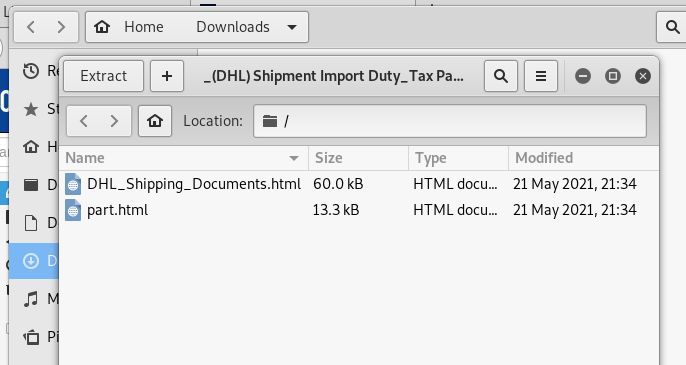
I opened the HTML attachment DHL_Shipping_Documents
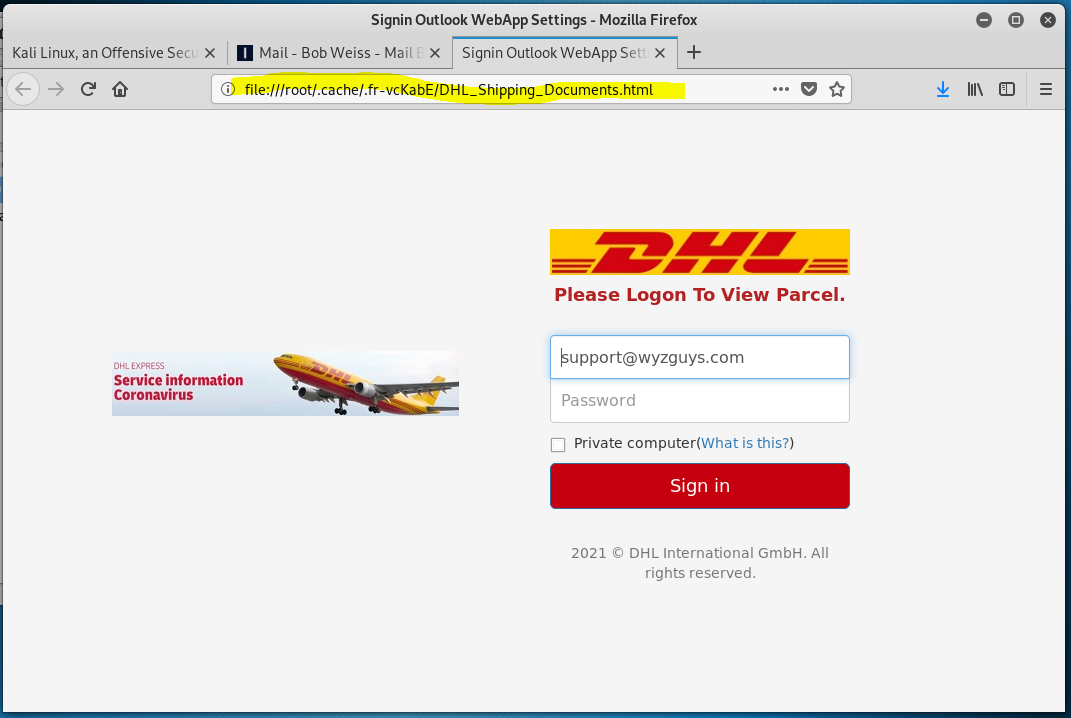
The DHL page looked like this
The other attachment looked like the original email message.
You must be very cautious with email attachments, because they often come with embedded Trojan horse malware than can install a remote access tool that allows your attacker to take over your computer.
Capital One Web Form Phish
This exploit started off as an email sent to me from a web form on one of my own web sites. There are websites online where you can buy applications that will enable a “marketer” to send marketing, spam, and phishing emails to website owners and admins by automatically filling and sending web contact forms. This is what we see here, an email sent from a web form at one of my own websites:
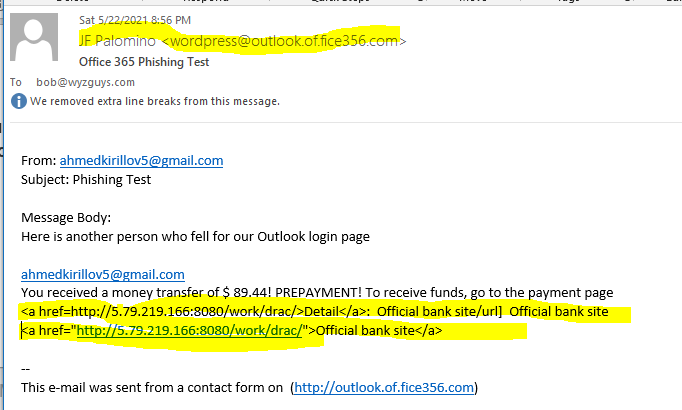
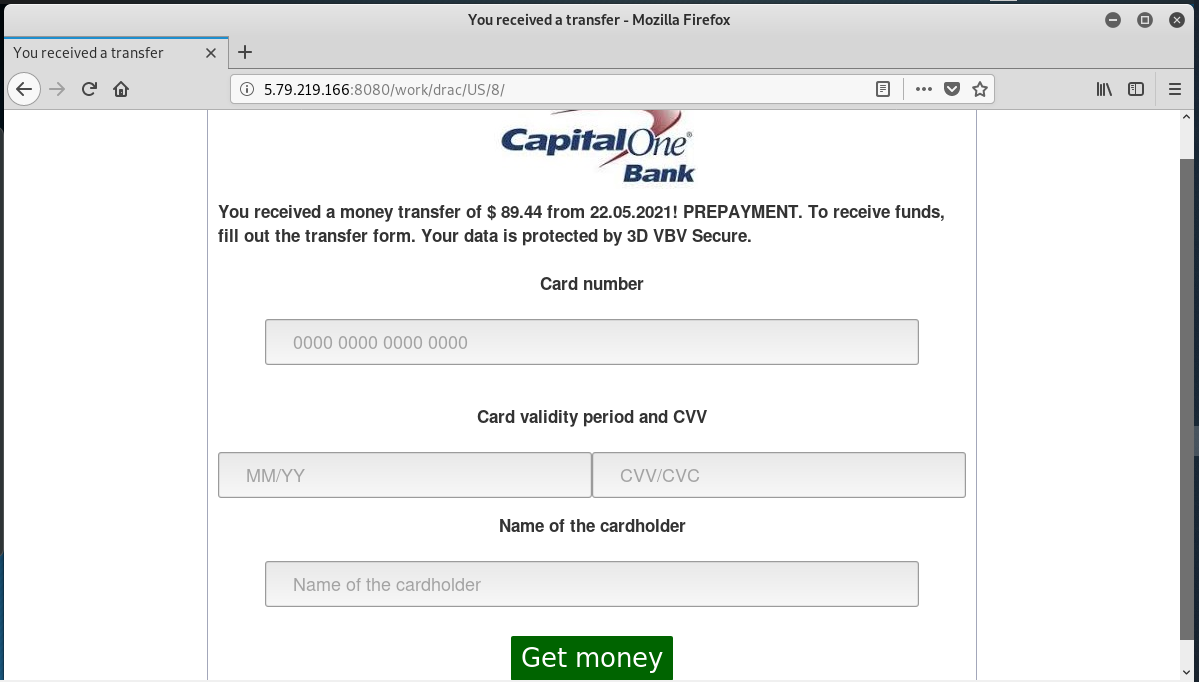
The bait is the opening sentence: You received a money transfer of $89.44! PREPAYMENT! To receive funds, go to the payment page.
The irony of this exploit is that the email was sent from the credential capture form that I created on a phishing training site I maintain at http://outlook.of.fice356.com. Please note the creative use of the subdomains outlook and .of. I registered fice356.com several years ago to use for a phishing detection and training site. When you string the subdomains together with the domain name, you get a URL that closely resembles the URL used to open an Ofice365 email account.
J F Palomino is an alter-ego I use on the web.
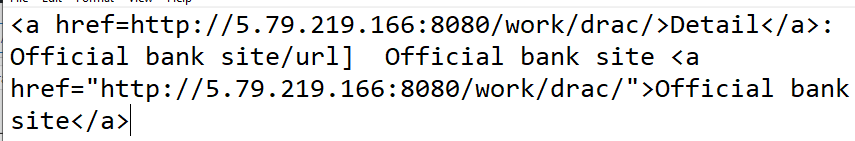
Notice the html code snippet that is highlighted above.
This code should resolve into an HTML email with a link button, but I only allow text emails from the web form. The link resolves to the website shown below.
The goal of this exploit is to have you reveal a credit or debit card number.
If you own or operate a website, and have been dealing with these “Contact Form” marketing emails, you know that because the domain name of the site is generally trusted by your emailing and spam filtering applications, these contact form spam sail right past your defenses and into your inbox. The purpose of the contact form is to allow you to gather information from visitors to your site, not to allow some attacker to use the form against you.
One way to reduce or eliminate this problem is to add a CAPTCHA form to your contact form and any other web forms you maintain. This defeats most of these automated “marketing” mailing applications.
Another way that web forms are abused is the use of automated bot to use web forms to sent thousands of auto-responder emails to a targeted victim. This is called an email bomb and creates a denial of service attack against the selected victim, and is often used to create a diversion that is hiding the real attack using your stolen credentials to access bank accounts, social network accounts or e-commerce shopping sites, usually to steal money or purchase expensive goods that are easy to resell.
Check out these earlier stories about email bombing.
- Surviving an Automated Sign-up Bot Email Bomb
I have a client who is the victim of an email bomb. She started receiving hundreds of mails from websites all over the Internet. Nearly all of them were the kind of subscription confirmation email you would get after signing up for a newsletter, forum, or other subscription service. When I say…
- What Is An Email Bomb?
You are going through your email, when suddenly forty new messages flood into your Inbox. These emails are all addressed to you, and they are coming by the dozens, and then hundreds, then even thousands. The emails are in a variety of different languages. They keep coming all day, and then the…
Video Porn Extortion Phish
This has been a more interesting week for phishing. Here is an extortion threat using the familiar “naughty behavior” exposure story. Here is the original email. The full text follows the image.
The full text:
Hello Robert Weiss,
You may not know me and you are probably wondering why you are getting this e mail, right? I’m a hacker who cracked your devices a few months ago. I sent you an email from YOUR hacked account. I setup a malware on the adult vids (porno) web-site and guess what, you visited this site to have fun (you know what I mean). While you were watching videos, your internet browser started out functioning as a RDP (Remote Control) having a keylogger which gave me accessibility to your screen and web cam. after that, my software program obtained all of your contacts and files. You entered a passwords on the websites you visited, and I intercepted it. Of course you can will change it, or already changed it. But it doesn’t matter, my malware updated it every time.
What did I do?
I created a double-screen video. 1st part shows the video you were watching (you’ve got a good taste haha . . .), and 2nd part shows the recording of your web cam. Do not try to find and destroy my virus! (All your data is already uploaded to a remote server)
– Do not try to contact with me
– Various security services will not help you; formatting a disk or destroying a device will not help either, since your data is already on a remote server.
I guarantee you that I will not disturb you again after payment, as you are not my single victim. This is a hacker code of honor. Don’t be mad at me, everyone has their own work.
exactly what should you do? Well, in my opinion, $1000 (USD) is a fair price for our little secret. You’ll make the payment by Bitcoin (if you do not know this, search “how to buy bitcoin” in Google).
My Bitcoin wallet Address:
17hQFghTjkDst4kHwtHB27UdKA6TL1spjL
(It is cAsE sensitive, so copy and paste it)
Important: You have 48 hour in order to make the payment. (I’ve a facebook pixel in this mail, and at this moment I know that you have read through this email message). To track the reading of a message and the actions in it, I use the facebook pixel. Thanks to them. (Everything that is used for the authorities can help us.) If I do not get the BitCoins, I will certainly send out your video recording to all of your contacts including relatives, coworkers, and so on. Having said that, if I receive the payment, I’ll destroy the video immidiately. If you need evidence, reply with “Yes!” and I will certainly send out your video recording to your 6 contacts. It is a non-negotiable offer, that being said don’t waste my personal time and yours by responding to this message. Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address. I do not make any mistakes. If I find that you have shared this message with someone else, the video will be immediately distributed. Bye!
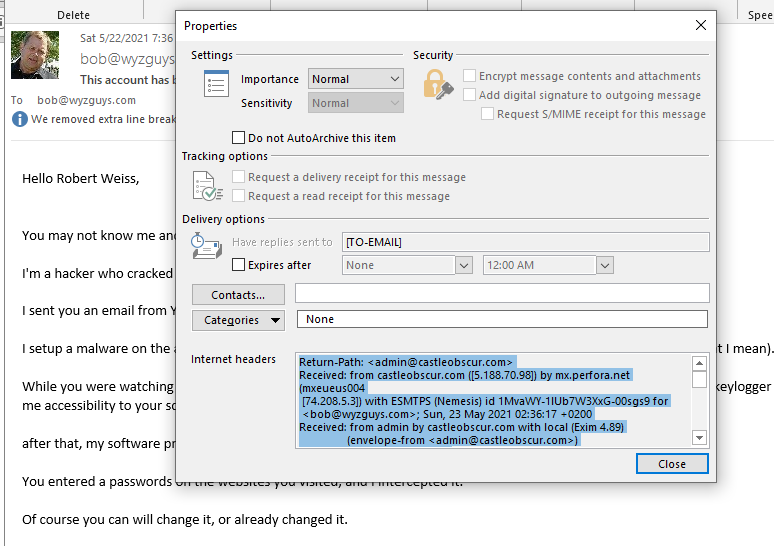
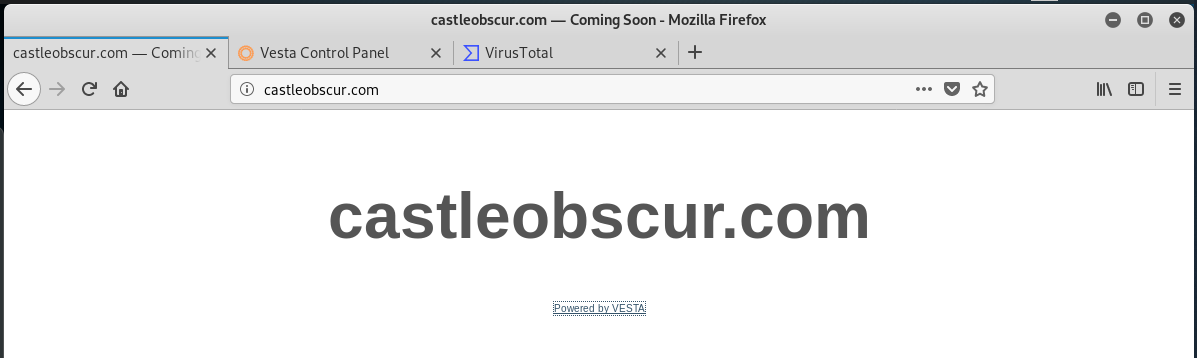
I checked the email headers, and the email originated from a server at castleobscur.com.
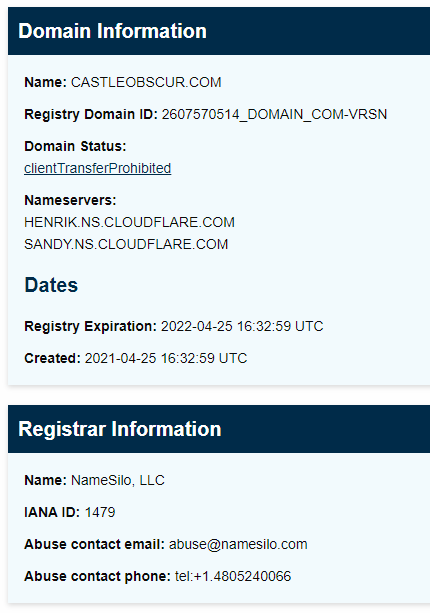
That intriguing name had me on ICANN WhoIs for more information about the domain.
This domain was registered just a few months ago on 2021-04-25. This is often a good indication that this domain is part of a new exploit.
Here is the home page for castleobscur.
And the VirusTotal report
You can safely assume that any emails you receive like this one is bogus, just a straight out extortion gambit.
But many of the techniques the extortionist described in the email do exist. There are some techniques you can use to protect yourself from eavesdropping.
- Cover your web camera when you are not using it. Yes an attacker can hijack your cam and use it to collect videos. I have a sliding gate I can close over my camera aperture.
- Good password hygiene is important too. If you are a frequent flier on this site, then you have seen the hundreds of ways that a phishing email can separate you from your logon credentials. Use care, and when in doubt, changing your password is a good idea.
- Make sure you have a good, updated version of an anti-malware application running on your system. This should detect and remove any malware that the attacker described. Windows Defender is adequate, but a paid-for subscription to Malwarebytes is better.
Share
MAY








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com