Phishing Email Alerts
Catch of the Day: Fake PO Phish with Trojan
Chef’s Special: Past Due Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
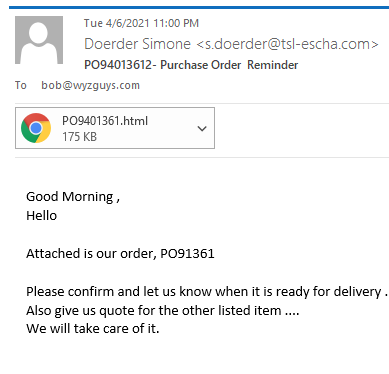
Fake Purchase Order Phish
Who doesn’t like a new customer out of the blue? This “purchase order reminder” is designed to get the target to open the HTML attachment. Doing so would release a Trojan Horse program identified on VirusTotal by Bitdefender (and many others) as Trojan.HTML.Phishing.ARN.
This is a well-executed phishing exploit that uses a tempting attachment instead of the usual malicious link to replica web page on a hijacked web site. Instead, the attachment opens a couple of web pages that are hosted directly on the target’s own computer. One of the pages is a convincing security alert, and the other a replica of an Adobe PDF web page, used to steal your Adobe credentials.
Follow the path of execution below:
The email was sent from an apparently legitimate but hijacked email account Doerder Simone <s.doerder@tsl-escha.com>. The email headers show Return-Path: <s.doerder@tsl-escha.com> Received: from tsl-escha.com ([95.110.214.149]) by mx.perfora.net (mxeueus003).
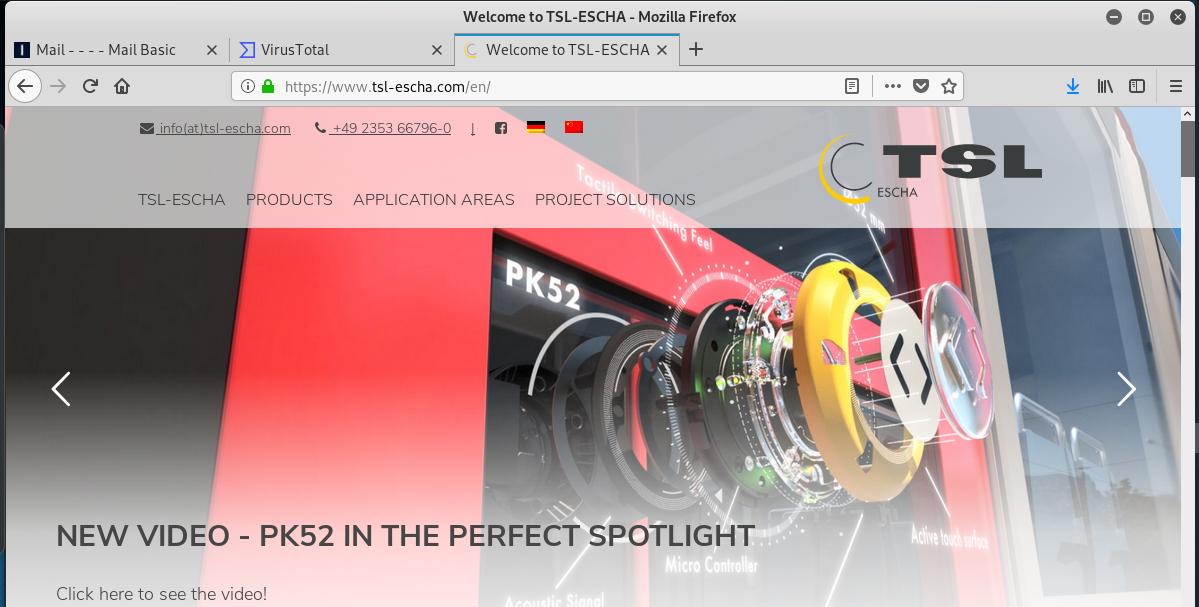
I found a legitimate website for the company at https://tsl-escha.com.
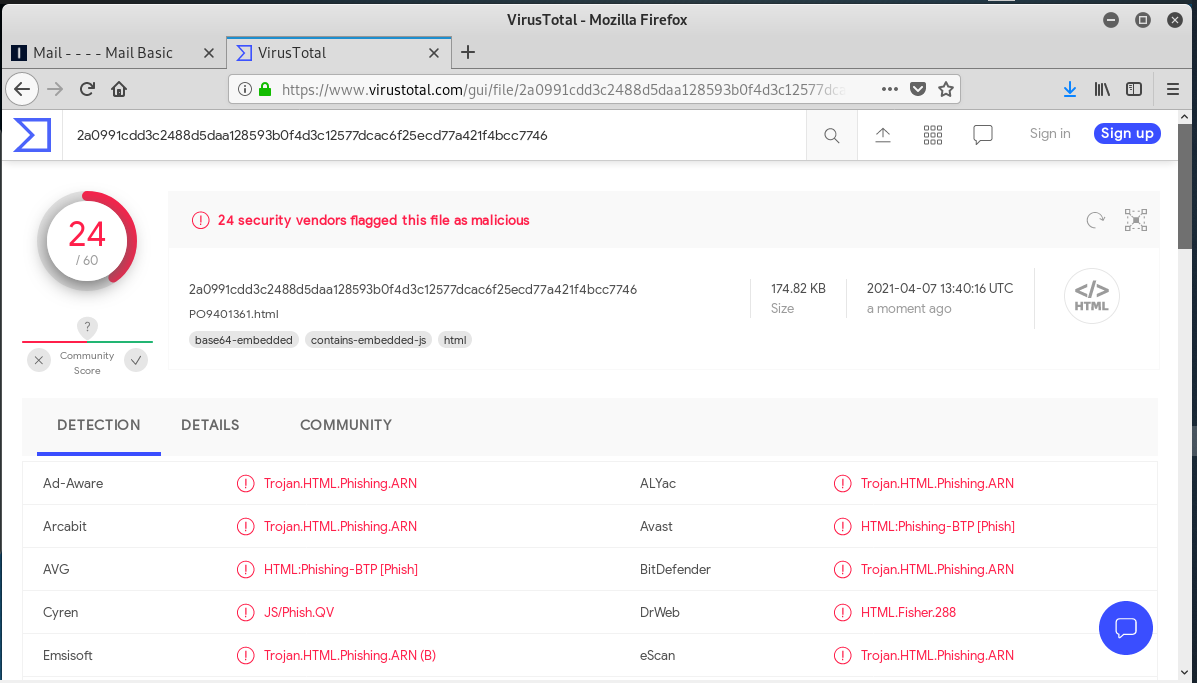
I downloaded the HTML file attachment and uploaded it to VirusTotal for analysis. 24 engines identified it as a Trojan Horse.
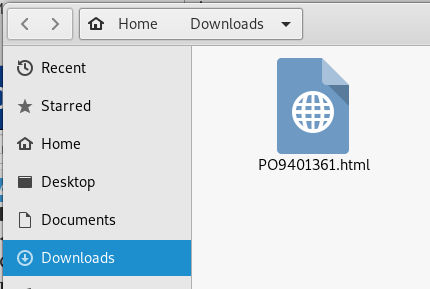
I opened the attachment in my Kali Linux virtual machine. Here is the download screen.
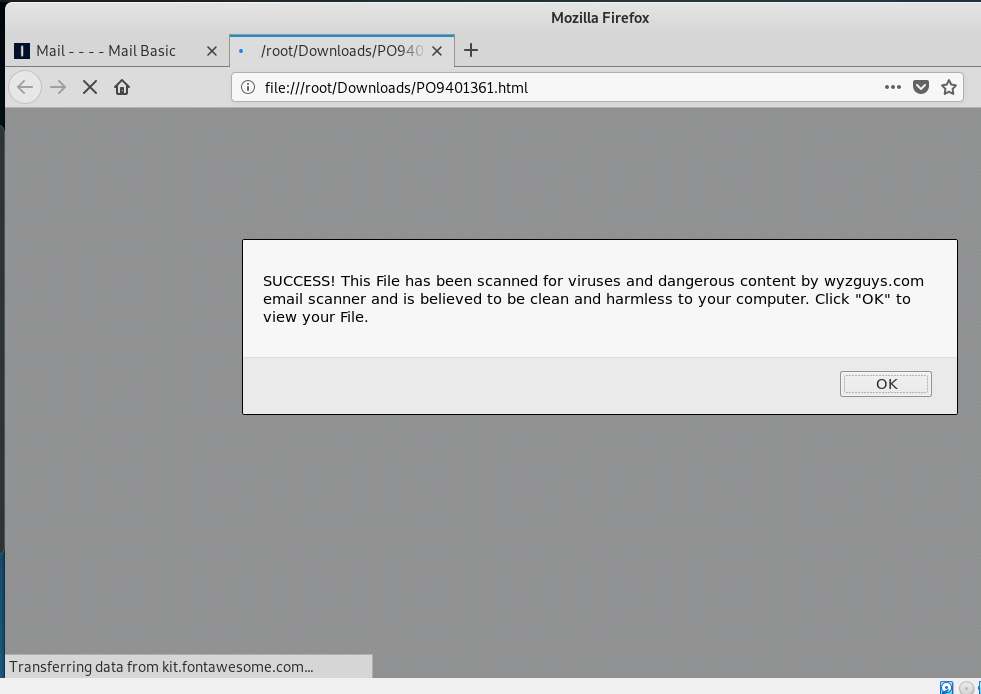
This screen displayed when I opened the file. The security message seemed fake, a nice bit of social engineering to support my decision to open the file. But the message Transferring data from kit.fontawesome.com.. at the bottom of the web page seemed more problematic. But when I checked it out on VirusTotal it turned out to be an innocuous call to a font website.
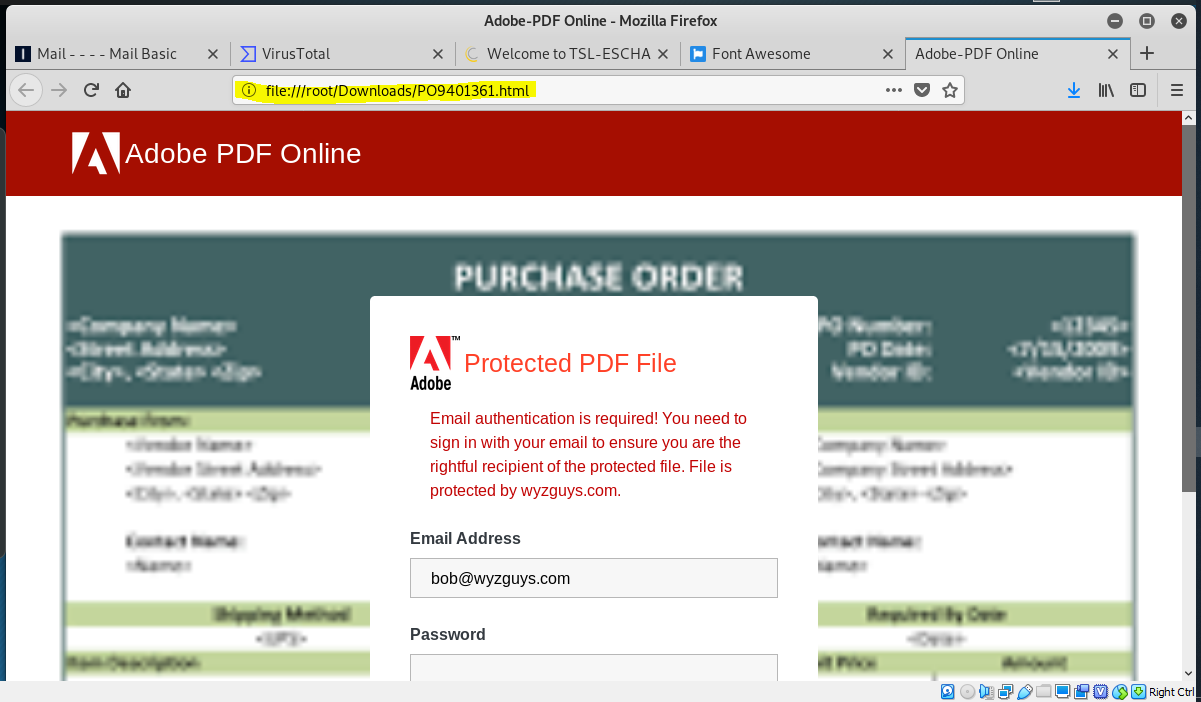
Clicking OK in the opened the following web page. Notice the web address file:///root/Downloads/PO9401361.html is located on my own computer, not on an Adobe web server. We can see the “purchase order” blurred out in the background. This is obviously an Adobe credential stealing scam.
.Business has been difficult for the last year due to the Pandemic. Many businesses are desperate for sales and revenue. Nevertheless, you must be care with emails that look like new business. Many of the arts of this exploit are legitimate (the email address, the company) so it might be easy to fall for this.
Past Due Phish
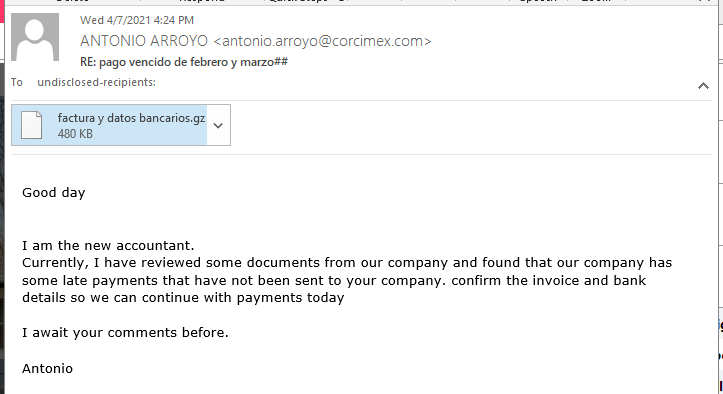
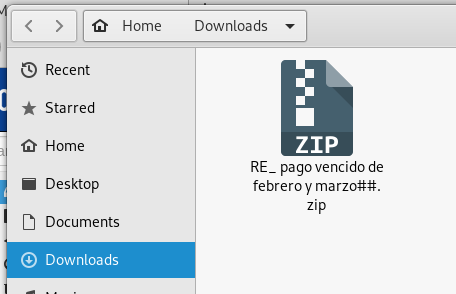
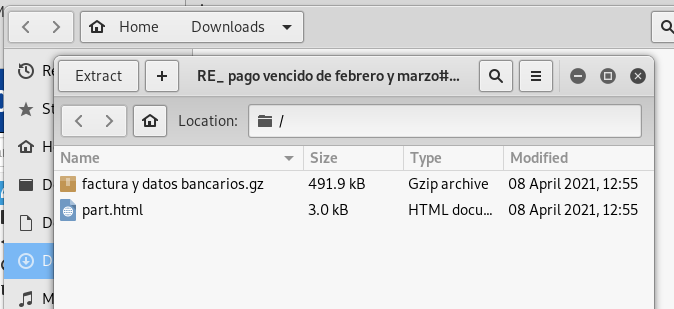
Following the theme of “found money,” here is an email from the “new accountant” who wants to pay off some past due invoices. There is a ZIP file attachment again, instead of a suspicious link. Opening the file archive did not reveal much that could be useful in this exploit, no fake invoices or self-serve web pages, just an HTML copy of the email text in the file part.html. This exploit is not very well executed. See below:
14 real-world phishing examples — and how to recognize them
Check out this slide show by Roger Grimes from KnowB4, on CSO Online.
Phishing Remains the Most Common Form of Attack
Phishing attacks are “by far” the most common vector for data breaches, according to a new survey by the UK’s Department for Digital, Culture, Media, and Sport (DCMS). The situation is not much different everywhere else in the world.
“Among those that have identified breaches or attacks, around a quarter (27% of these businesses and 23% of these charities) experience them at least once a week,” the report states. “The most common by far are phishing attacks (for 83% and 79% respectively), followed by impersonation (for 27% and 23%). Broadly, these patterns around frequency and threat vectors are in line with the 2020 and 2019 results.”
The DCMS says most of the respondents observed a noticeable increase in phishing attacks since the beginning of the pandemic. More…
Recent Phishing Scams That Managed to Bypass Email Security Filters
Researchers at Armorblox describe several recent phishing scams that managed to bypass email security filters. The first attempted to gain access to users’ Facebook accounts.
“Recently, the Armorblox threat research team observed an email impersonating Facebook attempt to hit one of our customer environments,” Armorblox says. “The email was titled ‘Reminder: Account Verification’ with the sender name ‘Facebook’ and the sender domain ‘noreply@cc[.]mail-facebook[.]com’.
The email informed victims that their account usage had been restricted due to some security concerns, and invited victims to verify their account activity to restore full access to their Facebook account.”
The email contains a link to a spoofed Facebook login page designed to steal the user’s credentials. More…
Share
APR





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com