Phishing Email Alerts
Catch of the Day: Routine Check Phish
Chef’s Special: Google Finds Thousands of Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
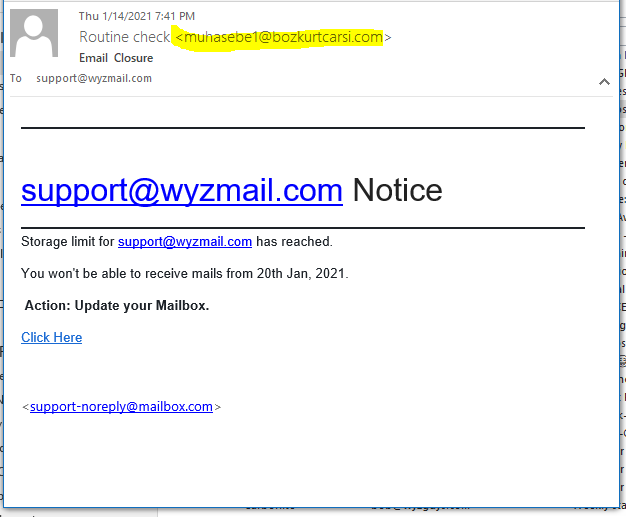
Routine Check Phish
I received this phish the other day. The sender is immediately suspicious. The Click here link resolves to https://sboveelaw.com/ip/u00m/checkpoint/mn/?email=support@wyzmail.com which resolves to https://sboveelaw.com/ip/u00m/checkpoint/mn/v91w7f0lwhizh3btlxq7deap.php?client_id=6C704E93AC9671C37C73418F62C96B7E&response_mode=form_post&response_type=code+id_token&scope=openid+profile&email=support@wyzmail.com&Connect_Authentication_Properties&&nonce=7203888216c704e93ac9671c37c73418f62c96b7e&redirect_uri=&ui_locales=en-US&mkt=en-US.
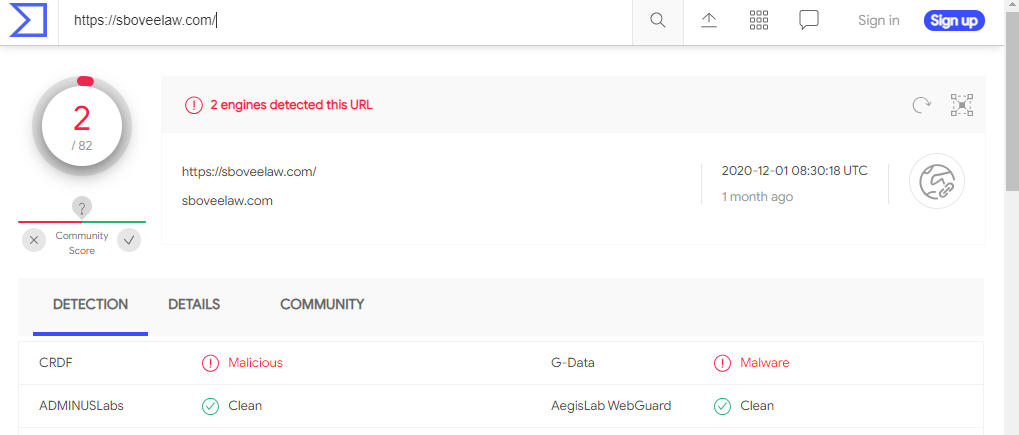
Virustotal identified this as a phishing link.
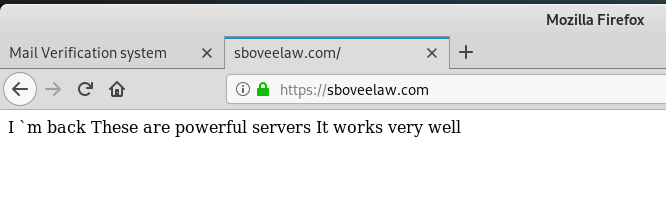
The link sent me to this landing page, and when I submitted a fake password, the error message popped up.
I assumed that the web server and domain (sboveelaw.com) had been hijacked, but my attempts to see the victim’s homepage got me an unexpected result.
So I thought I’d check the WHOIS record, The domain was registered back in 2014, and appears to be legitimately registered to an attorney, (perhaps).
Overall, a run of the mill credential stealing exploit, with the added twist of a missing victim homepage. Perhaps this domain name has been abandoned by the original registrant. Scott Bovee. I reached out to him via LinkedIn, and I will report if anything interesting happens.
Yet another credential stealing phish
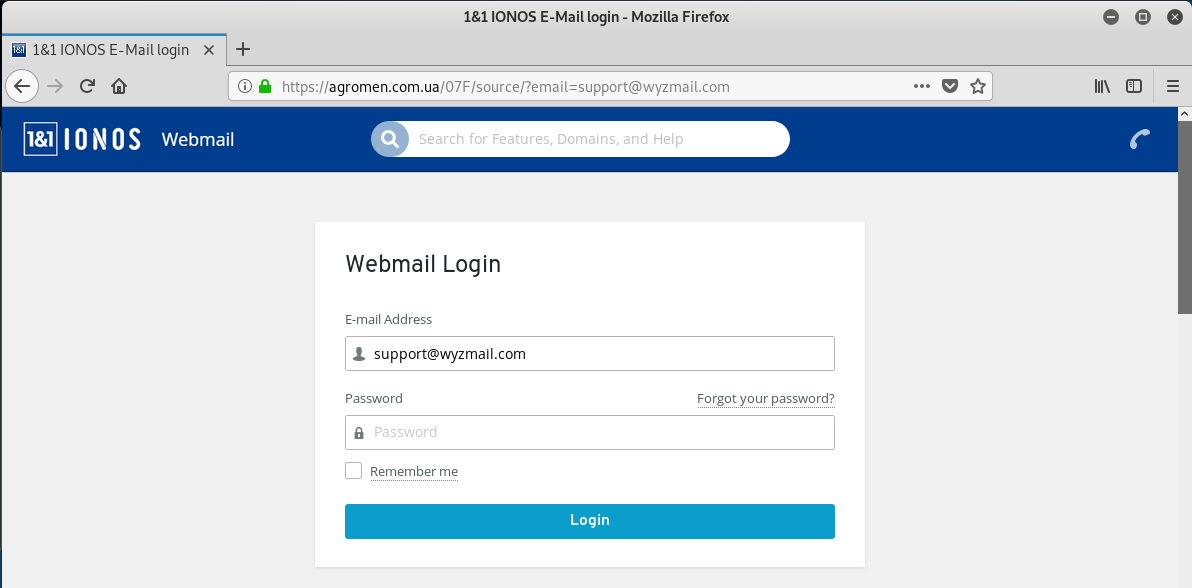
Not going too deep into this one, beyond the email and landing page images. The link https://agromen.com.ua/07F/source?email=support@wyzmail.com was not redirected to a different address, which is unusual. The TLD .ua is for the Ukraine. Check out the homepage of the hijacked website.
Google Finds an Alarming Thousands of Phishing Sites Every Day in 2020
Google discovered a record number of phishing sites in 2020, according to researchers at AtlasVPN. The researchers cite Google’s Transparency Report, which says the search giant detected 2.11 million phishing domains last year. That’s 25% more than the 1.69 million phishing sites discovered in 2019.
On average, Google flagged more than 40,000 phishing sites each week in 2020. The researchers note that the number of malicious sites has been steadily increasing for the past five years.
“Moving back to 2010, Google detected an average of 317 dangerous sites per day,” AtlasVPN writes. “Last year, the number jumped to 5789 websites per day, representing a 1726% surge in a decade. Looking at the last decade year-by-year, the volume of phishing portals grew by 43% on average.
In short, cybercriminals have been ramping up their efforts for the better part of the decade.”
CONTINUED:
https://blog.knowbe4.com/google-finds-an-alarming-thousands-of-phishing-sites-everyday-in-2020
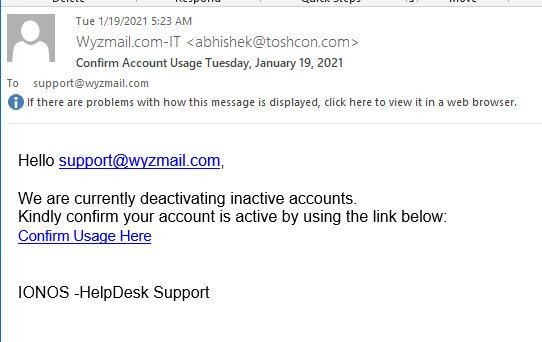
Check the authenticity of an IONOS email
I got this from my email host. An easy way to check for an IONOS phish
Do you doubt the authenticity of an email from IONOS? Find out immediately whether it is a phishing attempt!
Share
JAN








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com