Phishing Email Alerts
Catch of the Day: IONOS Credential Stealing Phish
Chef’s Special: IONOS Password Update Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
IONOS Credential Stealing Phish
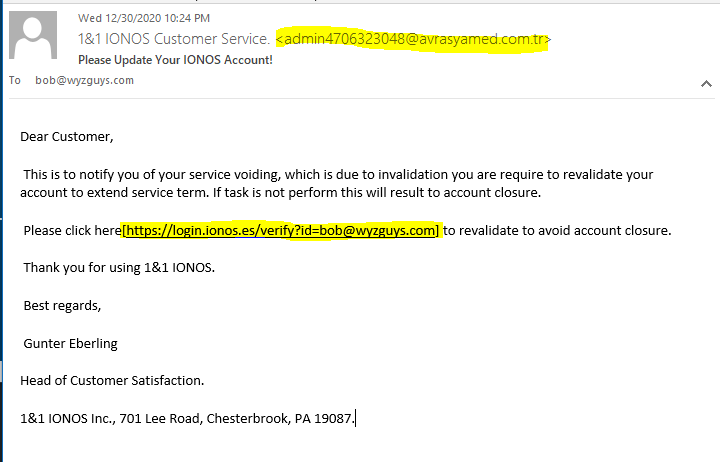
Here is another example of the popular credential stealing exploit. There are a couple clues in the email to warn the wary away. First, the email’s sender address is not on the IONOS domain, but on the domain of a Turkish medical supply company. I have to assume that this company’s mail server has been compromised so the attackers could create the email identity <admin4706323048@avrasyamed.com.tr>. Here is the email.
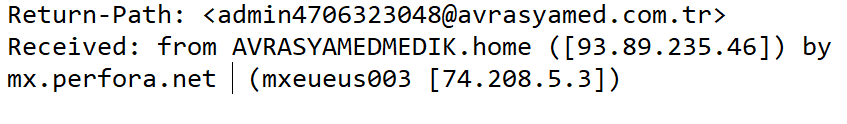
The email headers show that this email was sent from the hijacked mail server in Turkey.
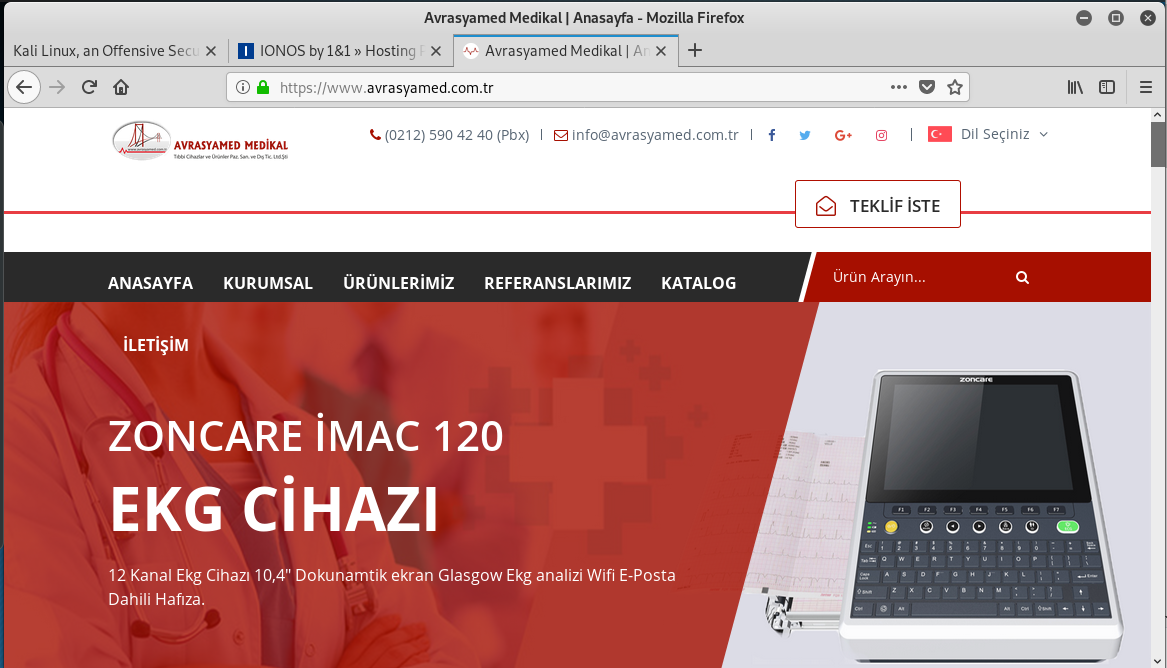
Here is the home page of the Turkish domain name used in the email address.
A quick check at VirusTotal.com showed the link in the email https://login.ionos.es/verify?id=bob@wyzguys.com was “clean” but the link resolves to https://dictatecompact.com/js/vendor/home/. VirusTotal reported this as a phishing link. This is another example of obscuring a malicious link beneath a benign link.
Another clue is that the link on the email would resolve to an Estonian website at login.ionos.es. Typically I log into US servers when I authenticate to my IONOS account, not servers in Estonia.
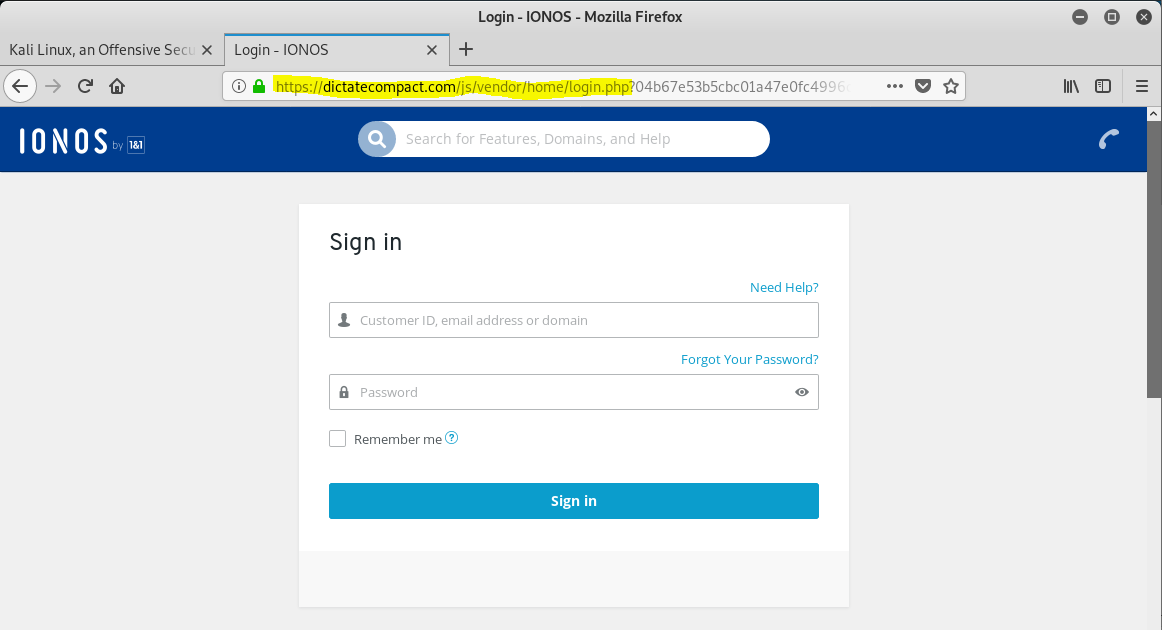
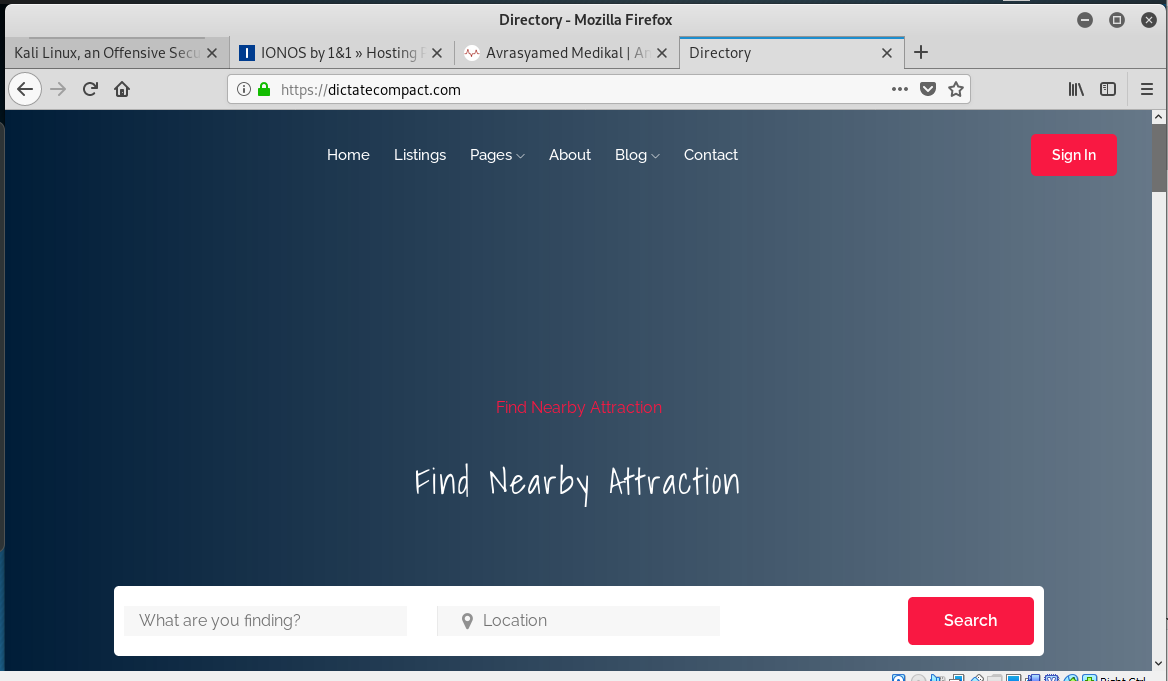
Using my Kali Linux virtual machine, I clicked on the link and was redirected to this fake IONOS login page. You will notice the address for this page is NOT IONOS.com, but for another hijacked web server at https://dictatecompact.com.
The actual home page of the hijacked web server is below.
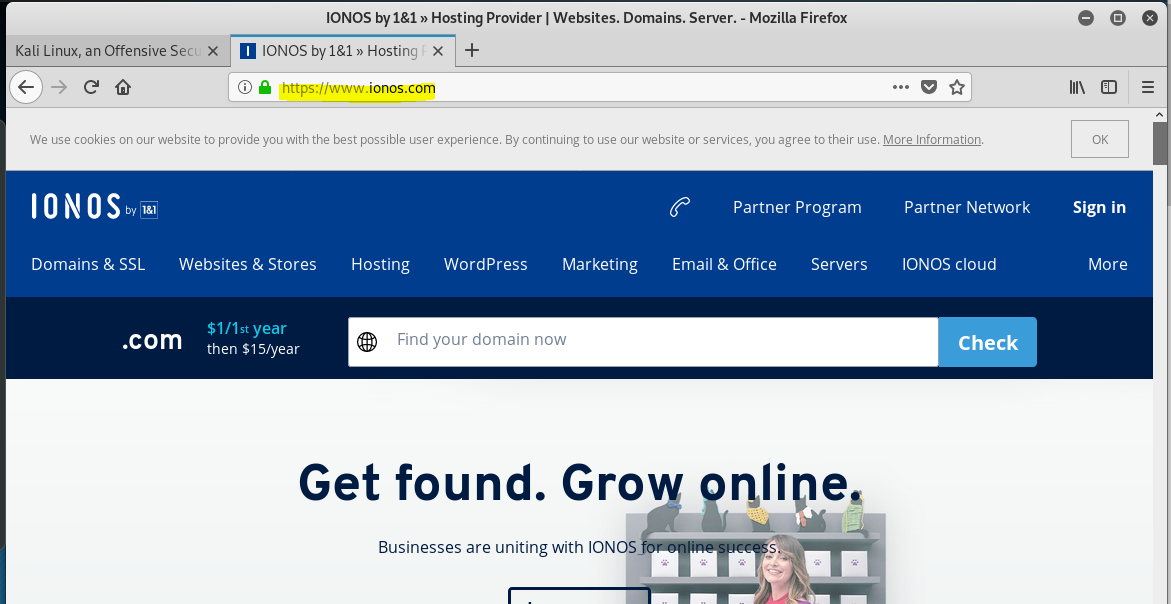
I entered fake user and password information into the form, and clicked the Sign In button. This sent my fake credentials to the phisher crew. What was special is that the click redirected me to an authentic IONOS login screen at a US based IONOS.com address. This is a nice touch, and reinforces the apparent legitimacy of the request in the original email.
All in all, a reasonably well-crafted effort by this phisher.
IONOS Password Update Phish
This email has been sitting in my inbox for 15 days, I forgot I had collected it, and failed to analyze it. The link has expired, or more correctly, has been taken down either by the phishing crew or more likely by cybersecurity analysts for for the company whose website was hijacked (RLB Trading), or one of the many cybersecurity companies.
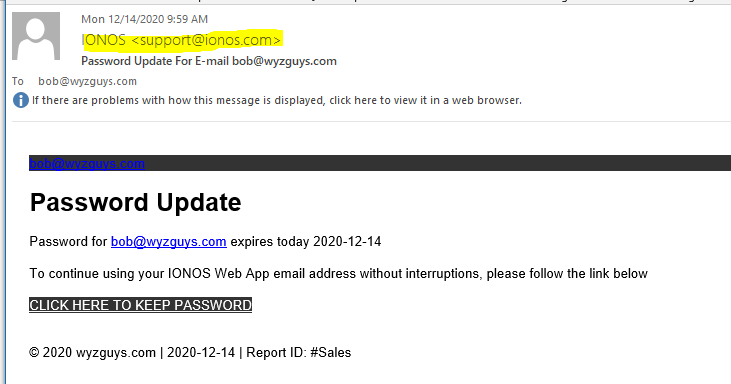
The email does a great job of spoofing an actual IONOS return address, and the email header shows the mail properly sent from IONOS mail servers.
The password update link (https://rlbtrading.co.uk/owa/?email=bob@wyzguys.com) is obviously wrong for the sender, though. The redirection link is gone. Attempts to follow the link met with a Malwarebytes security warning.
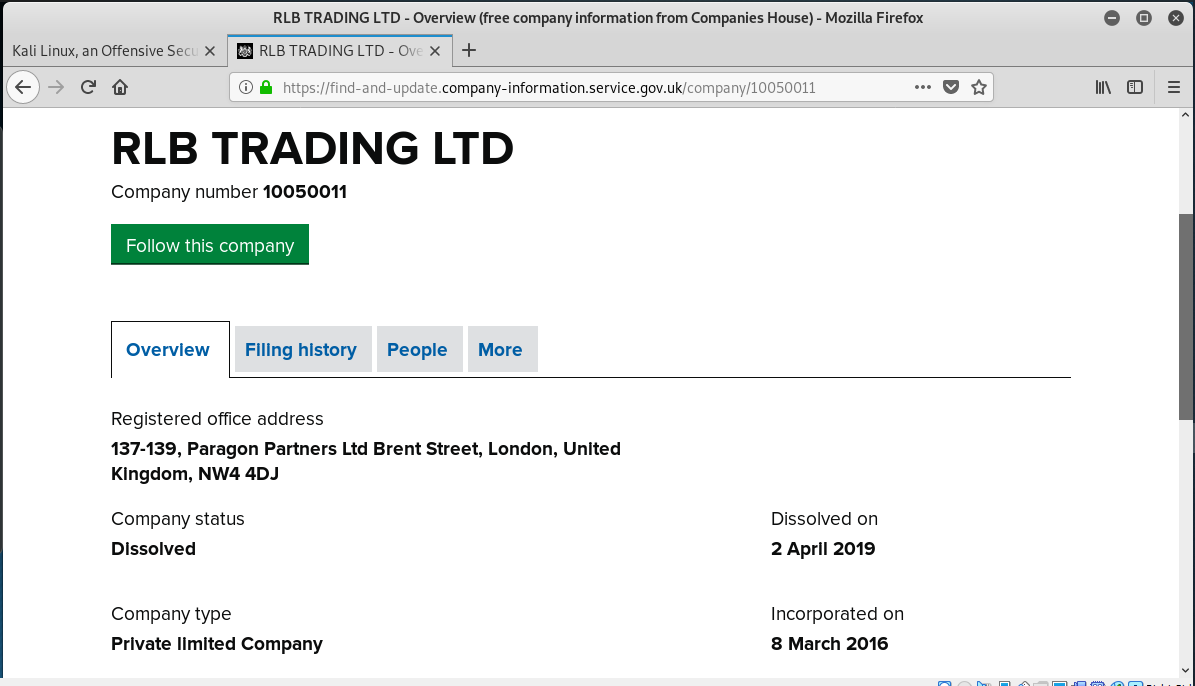
A search for information on RLB Traders shows the company was dissolved in 2019.
So the website that was hijacked must have been a site that was abandoned when the company was dissolved. This is one of the issues with the digital age, people and companies expire, but the data lives on, at least to the point when the service needs to be renewed.
Virus Detected
The right email host can make a lot of difference when it comes to malware detection, phish filtering, and spam blocking. Make sure your email filtering settings are set to at least a Medium setting, or better yet, High. You may have to spend a couple weeks checking your Junk Mail folder for wanted emails that may have been flagged, and training your mail system about which emails to permit into your Inbox, but in the end, it will be worth it.
Phishing emails with RAT targeting corporate users
“In November 2020 Doctor Web virus analysts detected a phishing attack targeting corporate users. The emails in question contained trojan malware that covertly install and launch Remote Utilities software — a tool for remotely accessing another computer.”
JAN








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com