Phishing Email Alerts
Catch of the Day: Phony iPhone Smish
Chef’s Special: Phone Election Smish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
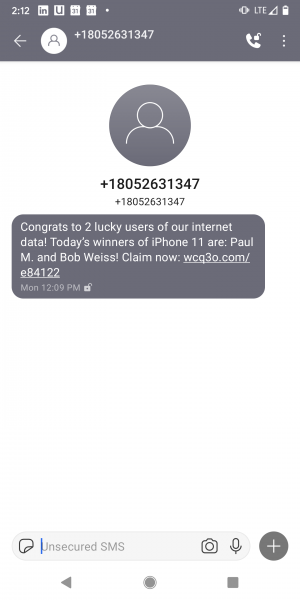
Phony iPhone Smishing Message
You did not win an iPhone 11 and neither did I, but this text seems to suggest that I click on the link to win mine.
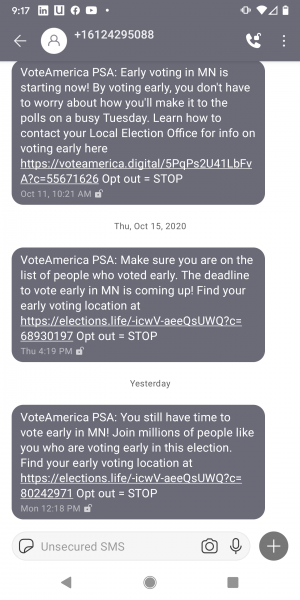
Phony Election Smish
You and I have been subjected to a never ending stream of “Get Out the Vote” SMS messages from Political Action Committees that don’t exist except to make money for cyber-criminals. Don’t click on them either. And certainly make no contributions.
Fake Adobe Doc Phish
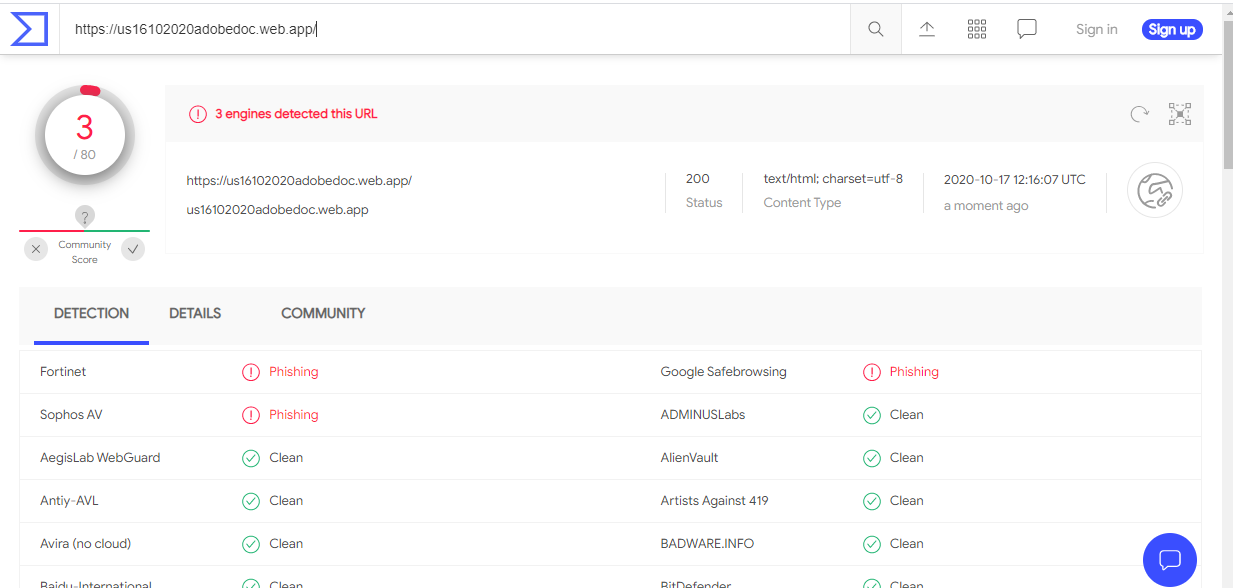
I received an email from a “Trusted Server.” Supposedly someone had left a PDF file message for me. Unfortunately for the attacker, the Retrieve Document button was not functional (points off for that mistake.) But the fall-back link at the bottom worked, and resolved to https://usceoadobedocument.azureedge.net/#bobweiss@wyzguys.com.
A quick submission to VirusTotal showed that his was in fact a phishing link.
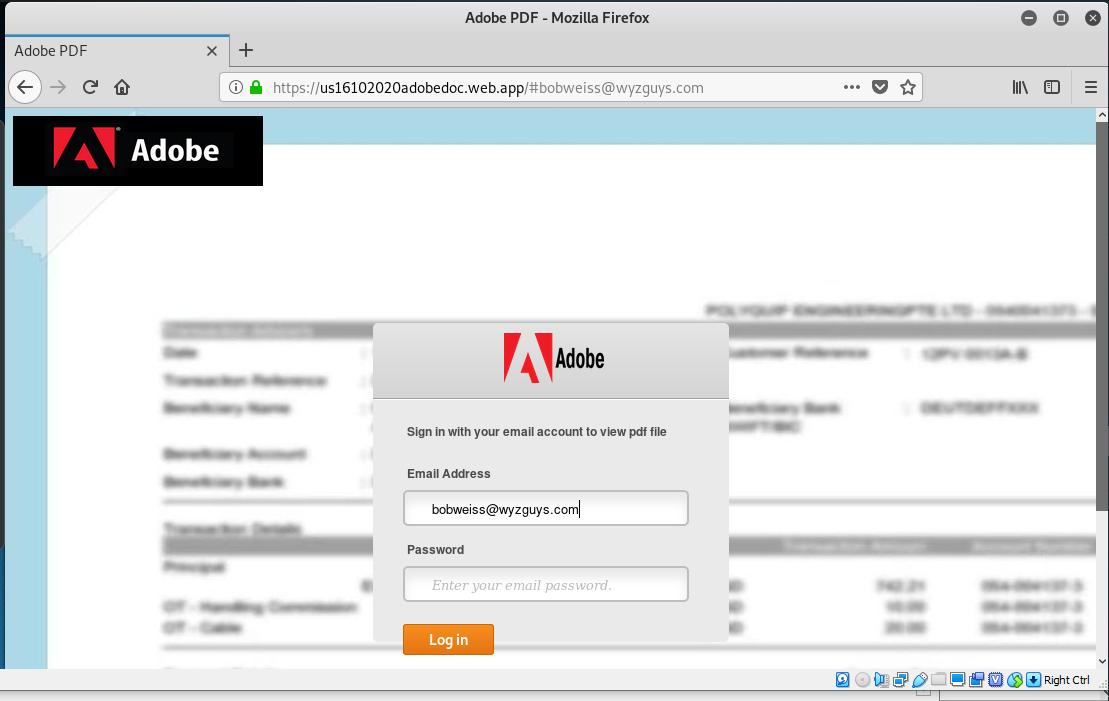
The landing page that was presented appeared to be a genuine Adobe file sharing site, but when I entered a fake password (nowaythisismypassword) the logon attempt was accepted, and I was redirected to a PDF document on a genuine RBC Wealth Management website.
This is a credential harvesting phishing exploit, but the final bounce out to the RBC site might catch the unwary recipient of the original phishing email and let them concluded this is a legitimate email.
Jooble – Spam, Scam, or Phish?
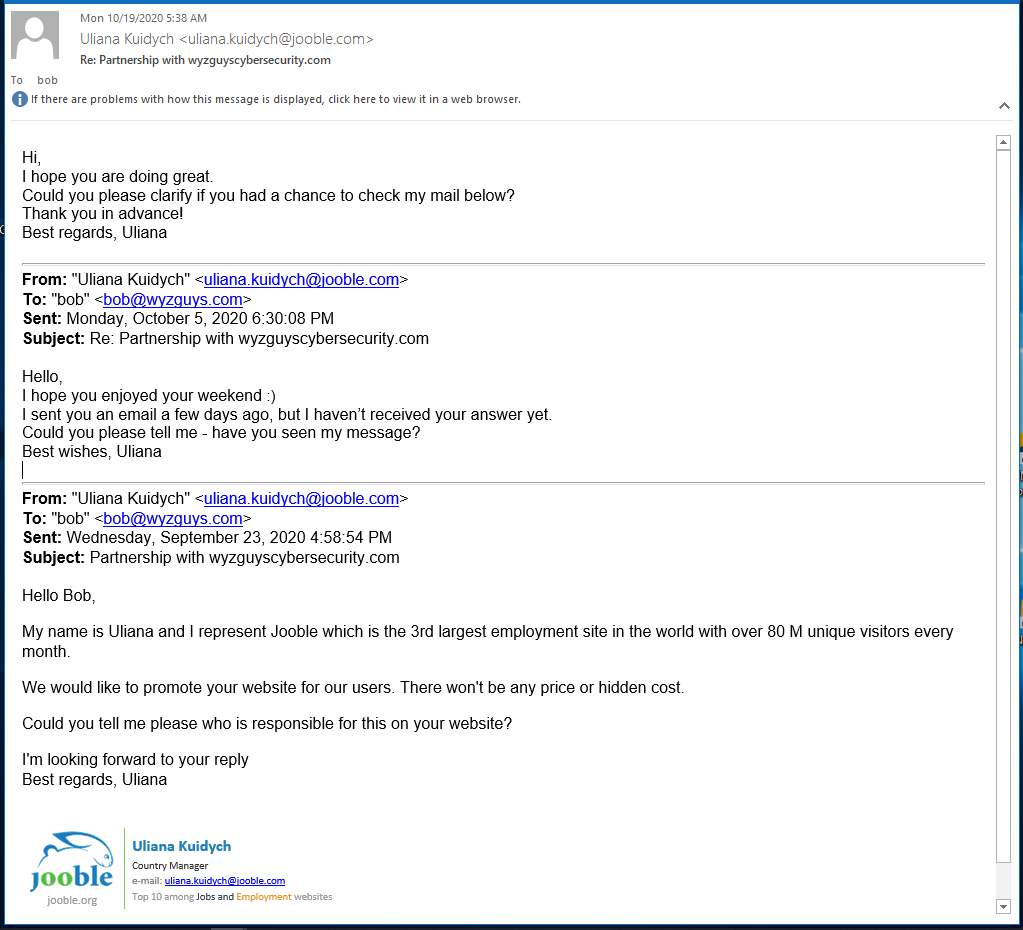
I have been ignoring a “partnership” request to join an international job board aggregator named Jooble.com. I had never heard of them, and was just ignoring their requests. But they were offering to “promote” my website “without any hidden fees” so I decided to look into them a bit.
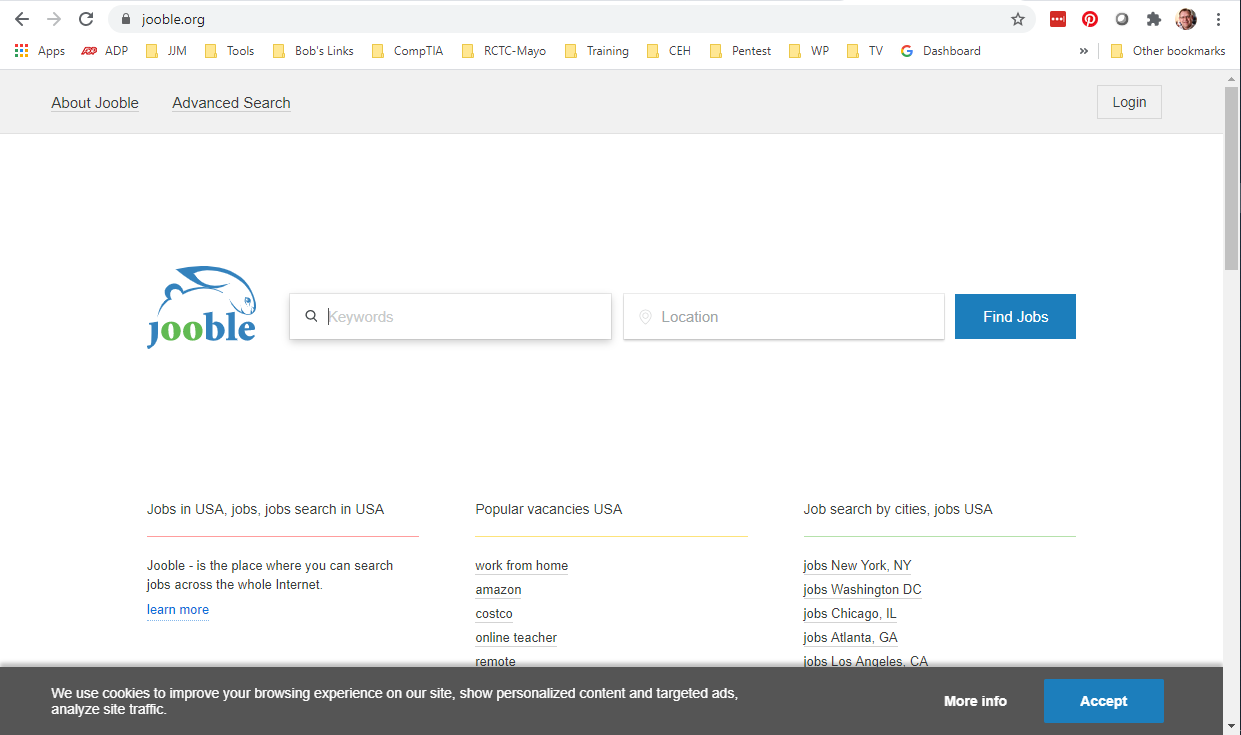
I started with a quick check of the domain jooble.com on VirusTotal, and it came back clean. Then I checked out the website. It appeared to be what it claimed to be, a job board search site.
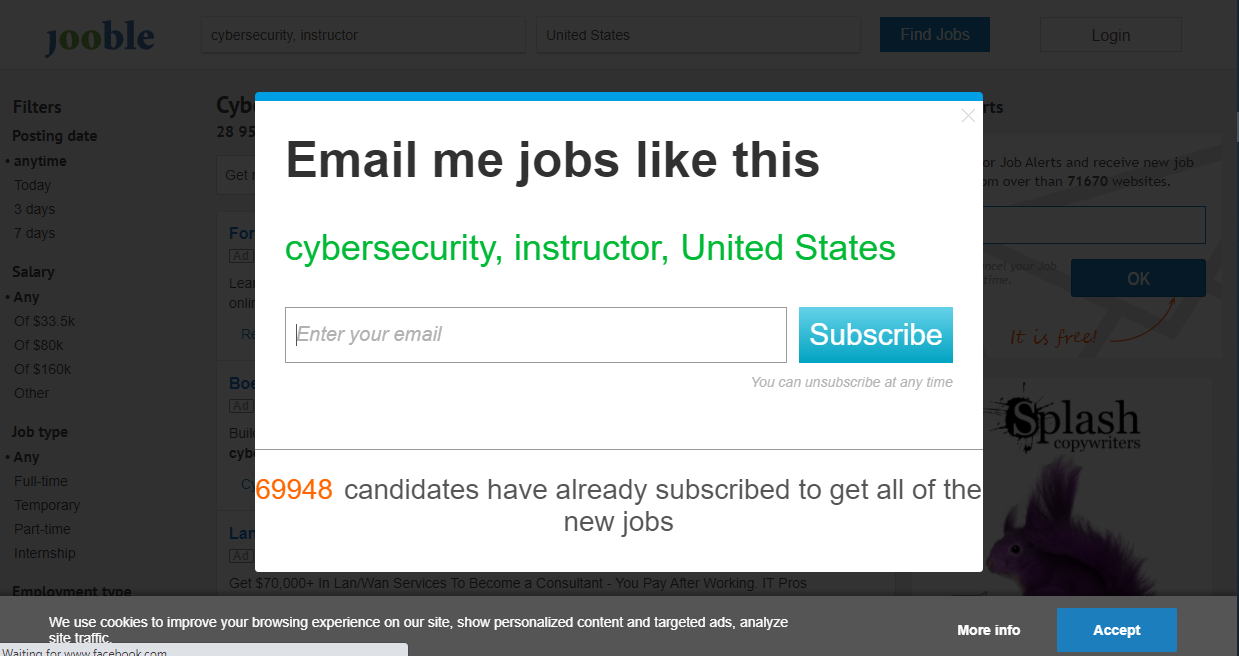
When I tried to search for a job, I was encouraged to register with my email, and I had to confirm that address in the next step, as well as create a password. All fairly typical for sites like this, but the result is they have my email address, and the password I created for this site. Supposedly I can “unsubscribe at any time.”
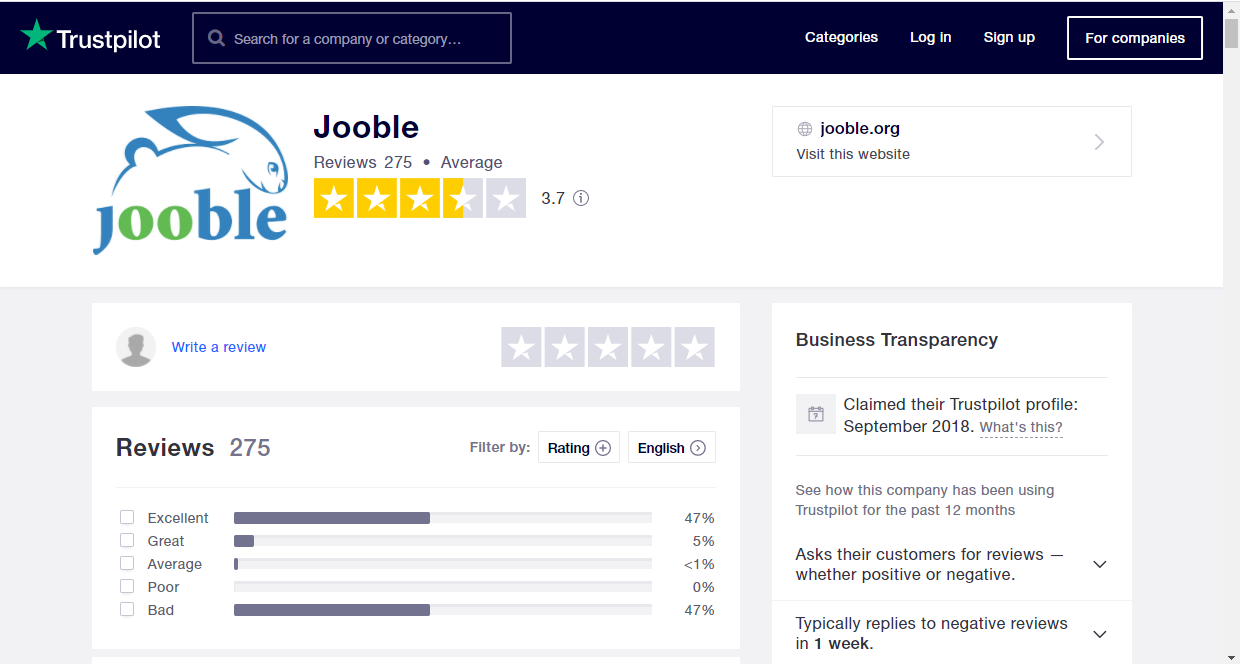
I decided to check out the online reviews for this company, and found some interesting tidbits. The first site I checked was Trustpilot. Good and bad reviews were evenly split at 47%. Legitimate companies typically invest more energy in keeping their online reviews positive.
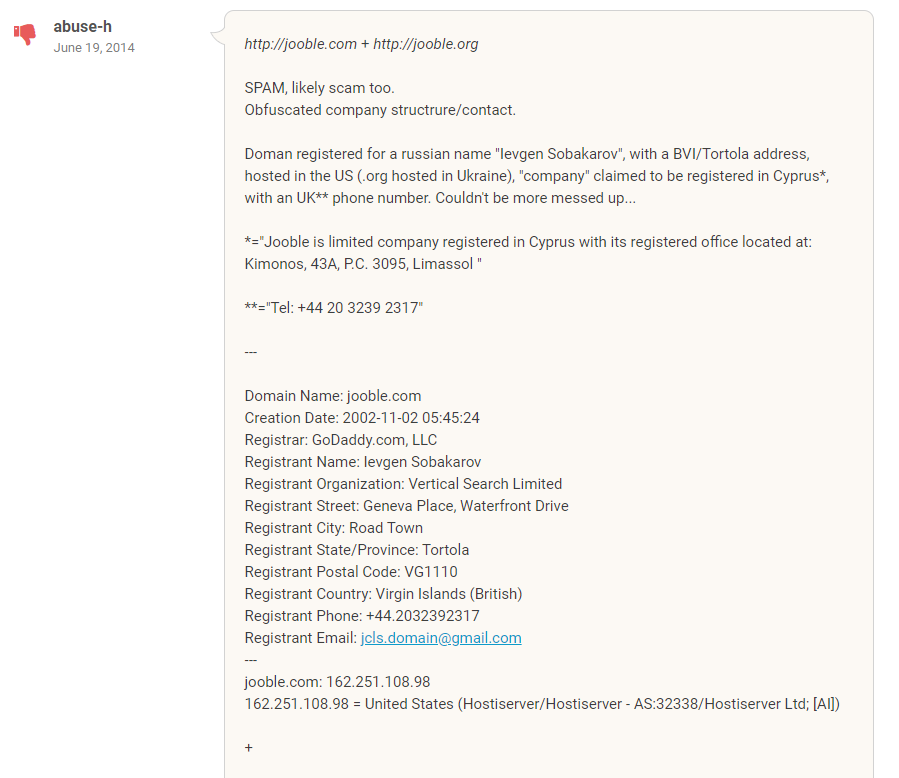
My next review site was Easycounter. I ran into an interesting longer comment complete with research, which I am including below. The most interesting content is at the beginnning of the review:
“http://jooble.com + http://jooble.org
SPAM, likely scam too.
Obfuscated company structure/contact.
Doman registered for a Russian name “Ievgen Sobakarov”, with a BVI/Tortola address, hosted in the US (.org hosted in Ukraine), “company” claimed to be registered in Cyprus*, with an UK** phone number. Couldn’t be more messed up…
*=”Jooble is limited company registered in Cyprus with its registered office located at: Kimonos, 43A, P.C. 3095, Limassol “
**=”Tel: +44 20 3239 2317″
 At this point I am not feeling too positive about this company, but one of the search results for Jooble is a comprehensive article on Wikipedia. It is quit possible that this article was created and submitted by Jooble staff. Nevertheless, the references section is chock full of links to other articles about this company, and a perfunctory look at several of them confirms that these article links are valid.
At this point I am not feeling too positive about this company, but one of the search results for Jooble is a comprehensive article on Wikipedia. It is quit possible that this article was created and submitted by Jooble staff. Nevertheless, the references section is chock full of links to other articles about this company, and a perfunctory look at several of them confirms that these article links are valid.
So the result of this research? I am inclined to play along a bit more and see what this “partnership” opportunity is all about. There may be another part to this story down the road a bit.
So this email I am chalking up as a marketing email, albeit a fairly aggressive one. Not SPAM, possibly a scam, but definitely not a phish, unless you count the collection of my email address. The company is based in the Ukraine, and if you use this search engine, understand that your information is being stored overseas somewhere. Can’t endorse these guys, but at least they appear to be legit.
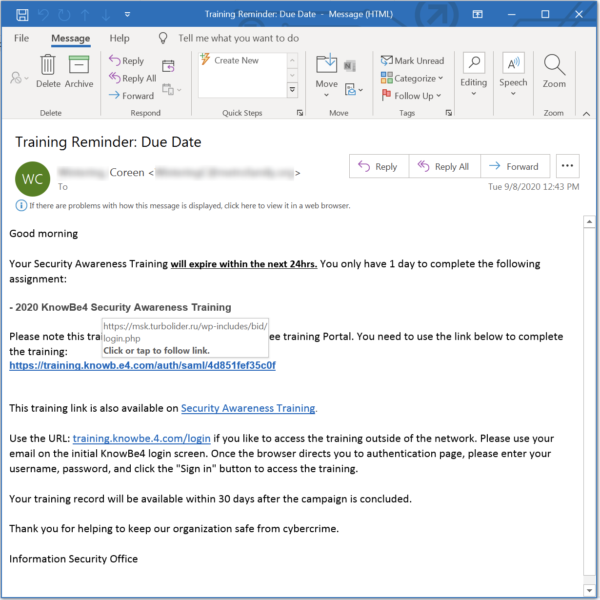
Phishers spoof reliable cybersecurity training company to garner clicks
It’s safe training employees about cybersecurity, right? Perhaps not, given that criminals are pretending to be known cybersecurity experts and luring teams to click on bogus training courses. Keep reading
Share
OCT







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com