Phishing Email Alerts
Catch of the Day: Mailbox Shutdown Phish
Chef’s Special: IRS COVID-19 Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
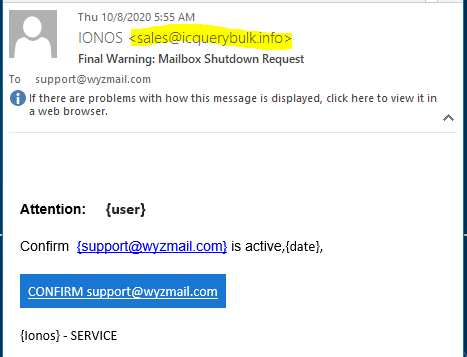
Mailbox Shutdown Phish
Another week with very few phish in the nets. This one is so small and poorly executed, I should really throw it back. This phish starts with the threat of service shutdown. The CONFIRM button resolves to https://floorandwalltiles.co.uk/Vtyh/KOL?email=support@wyzmail.com. The landing page is built on the hijacked website of a UK flooring store, and is a basic credential stealing exploit. Here is the phishing email.
This is the landing page of this email credential stealing exploit.
And here is another victim of this exploit, the owners of this UK tile and flooring store, whose hijack website was used to host the landing page for this attack.
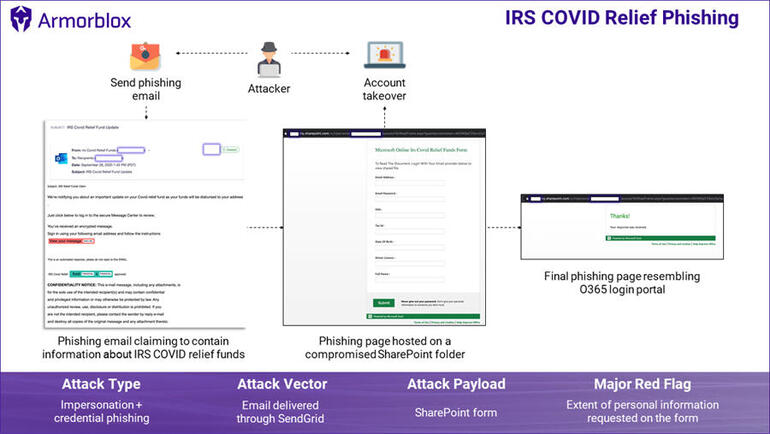
Phishing attack spoofs IRS COVID-19 relief to steal personal data
The phishing page tries to obtain email credentials, Social Security numbers, driver’s license numbers, and tax numbers, says Armorblox. Full story…
Phishing Spreads Emotet Malware
Alert (AA20-280A) – Emotet Malware
Emotet—a sophisticated Trojan commonly functioning as a downloader or dropper of other malware—resurged in July 2020, after a dormant period that began in February. Since August, CISA and MS-ISAC have seen a significant increase in malicious cyber actors targeting state and local governments with Emotet phishing emails. This increase has rendered Emotet one of the most prevalent ongoing threats.
To secure against Emotet, CISA and MS-ISAC recommend implementing the mitigation measures described in this Alert, which include applying protocols that block suspicious attachments, using antivirus software, and blocking suspicious IPs.
Emotet is an advanced Trojan primarily spread via phishing email attachments and links that, once clicked, launch the payload. Emotet is difficult to combat because of its “worm-like” features that enable network-wide infections. Additionally, Emotet uses modular Dynamic Link Libraries to continuously evolve and update its capabilities. Read full story…
Gone phishing: workplace email security in five steps
The latest data from SophosLabs shows that in September 2020, 97% of the malicious spam caught by our spam traps were phishing emails, hunting for credentials or other information.
The remaining 3% was a mixed bag of messages carrying links to malicious websites or with booby-trapped attachments, variously hoping to install backdoors, remote access trojans (RATs), information stealer or exploits or to download other malicious files.
Phishing remains a frighteningly effective tactic for attackers, regardless of the final objective.
This is in part because the operators behind them continue to refine their skills and enhance the sophistication of their campaigns. Full story…
Phishing for Toner: How a Credential Harvesting Attack Cost Companies Millions
Many organizations believe they are not targets for a cyberattack because they “have nothing of value” that criminals would want. Do you have an employee authorized to order office supplies, like printer ink? It turns out, cybercriminals would like that person’s login credentials because they have value. A U.S. federal judge just sentenced a Nigerian national to three years in prison for being part of a phishing ring… Read more
Serious Security: Phishing without links – when phishers bring along their own web pages
How do you “check the URL before you click” if the web page you’re visiting is already on your own computer? Read entire story
Share
OCT







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com