 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Outlook Phishing
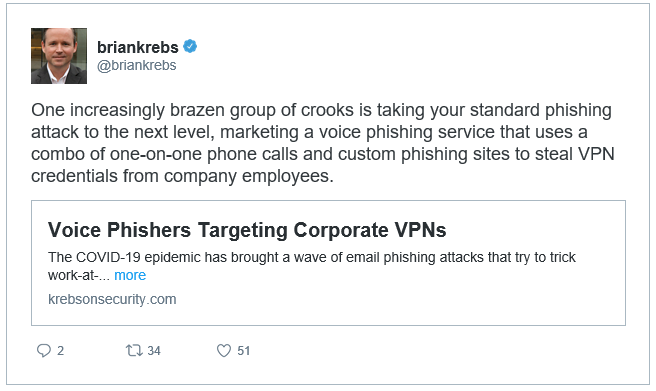
Chef’s Special: VPN Vishing
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
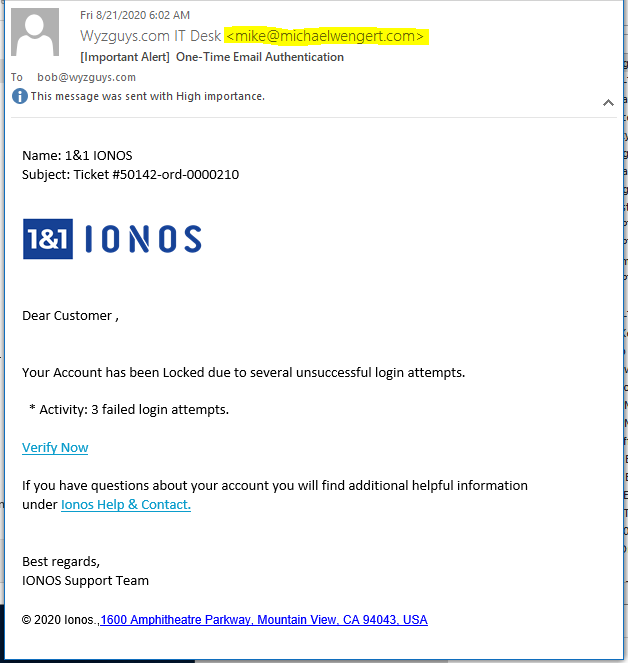
IONOS Phish
Here’s another credential stealing attempt. “My Account Has Been Blocked,” yet it is still receiving and sending emails – hmmmm.
Verify Now resolves to https://aphrx.ca/1_1webmail/index?email=bob@wyzguys.com%2F&sa=D&sntz=1&usg=AFQjCNHoixkuUyYfVJ6qoZ4zmvhzMyBv-g
Ionos Help and Contact resolves to https://www.google.com/url?q=https%3A%2F%2Fahmedgarmentsindustry.com%2Fdvs%2F&sa=D&sntz=1&usg=AFQjCNHoixkuUyYfVJ6qoZ4zmvhzMyBv-g and was redirected to https://ahmedgarmentsindustry.com/dvs/, but this link was already broken
Address link resolves to https://www.google.com/maps/search/1600+Amphitheatre+Parkway,+Mountain+View,+CA+94043,+USA?entry=gmail&source=g and resolves to a Google Maps location.
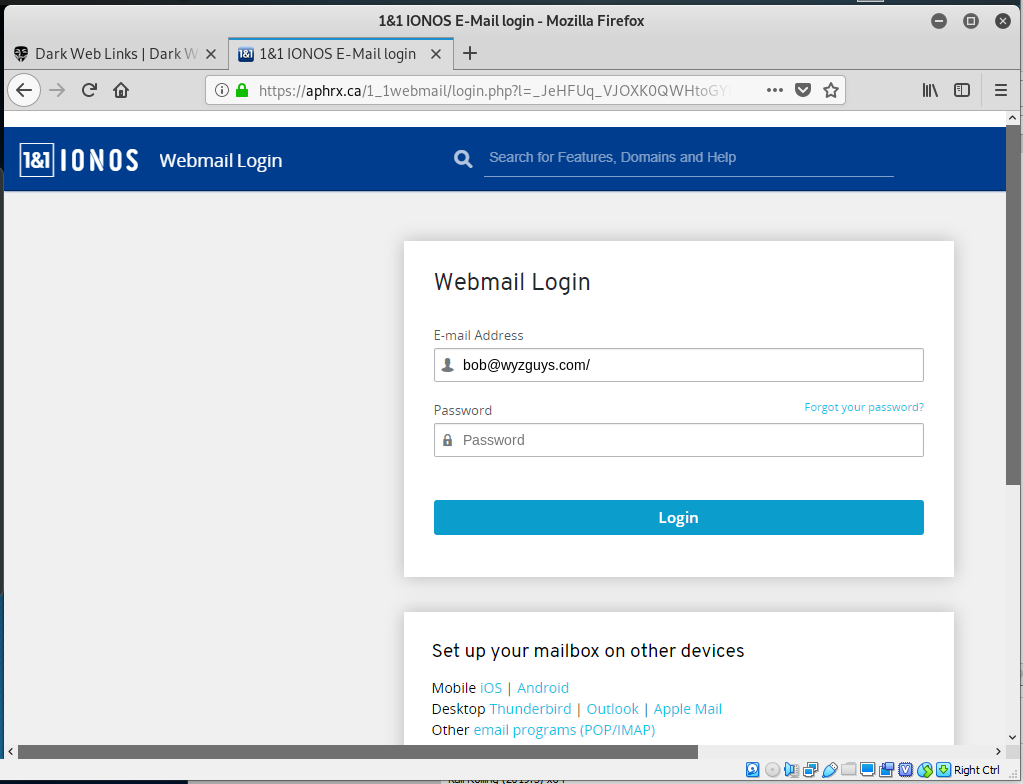
Here is the landing page for the first link
We’ve seen many examples like this one. Common sense would tell you that if your email is working, then this email is fake. Also, I received several of these over the course of a single day. Another hallmark of a phish.
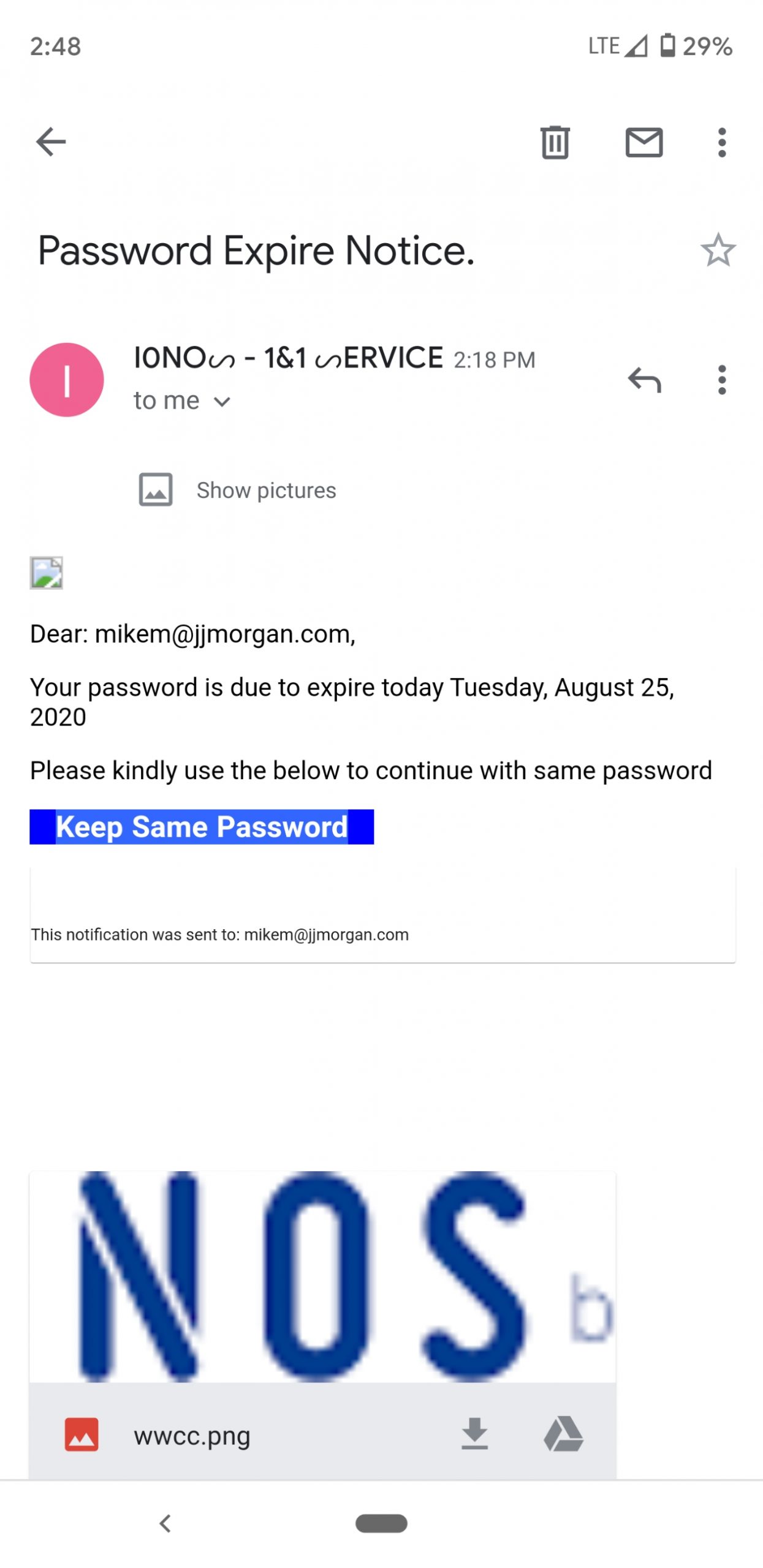
Keep Your Same Password Phish
This is a novel effort submitted by a client. The problem with credential stealing is if the victim changes their password, the cyber-crook has nothing. I thought the offer to keep your existing password was novel. When has ANYONE in a computer support role offered to let you KEEP YOUR PASSWORD? Never? Nothing I’ve ever seen before. And the novel use of characters for the letter S is good too.
Screenshot from a phone, so nothing to chase here, just another example to be wary of.
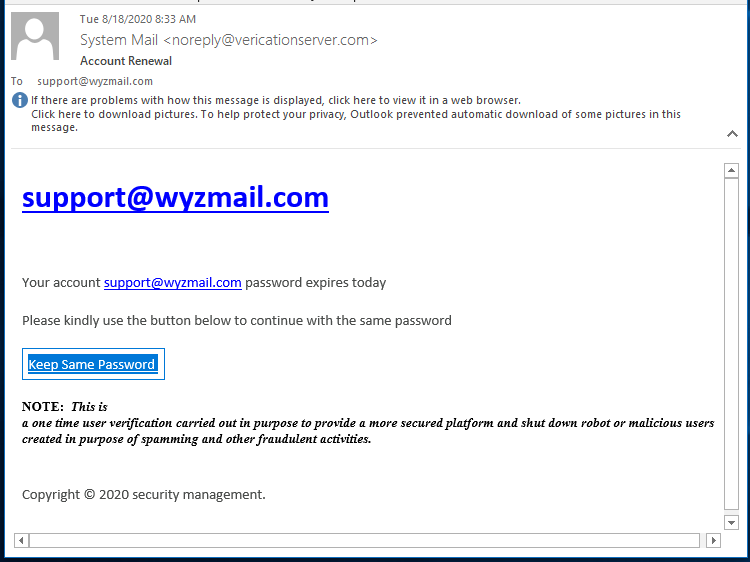
As I looked deeper in my own inbox, I found a similar phishing email. One this one the link was broken already, but it was another sendgrid address.
Outlook Phishing example from Sophos
Here’s a phish that our own security team received themselves. Full article at this link
Apart from some slightly clumsy wording (but when was the last time you received an email about a technical matter that was plainly written in perfect English?) and a tiny error of grammar, we thought it was surprisingly believable and worth writing up on that account, to remind you how modern phishers are presenting themselves.
Out are the implied threats, the exclamation points (!!!) and the money ($$$) you might lose if you don’t act right now; in are the happy and unexceptionable “here’s a problem that you can fix all by yourself without waiting for IT to help you” messages of a sort that many companies are using these days to reduce support queuing times.
Yes, you ought to be suspicious of emails like this. No, you shouldn’t click through even out of interest. No, should never enter your email password in circumstances like this.
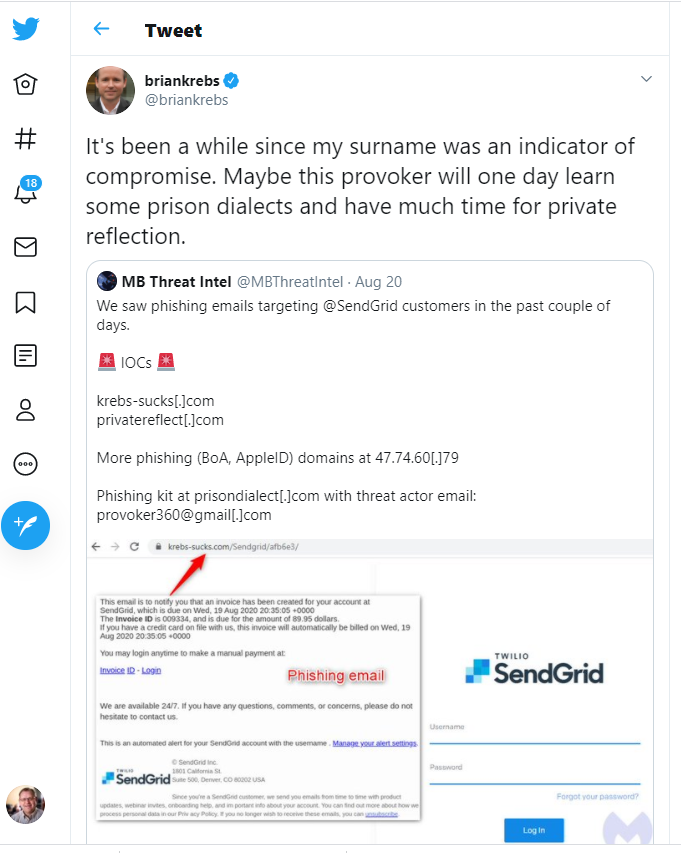
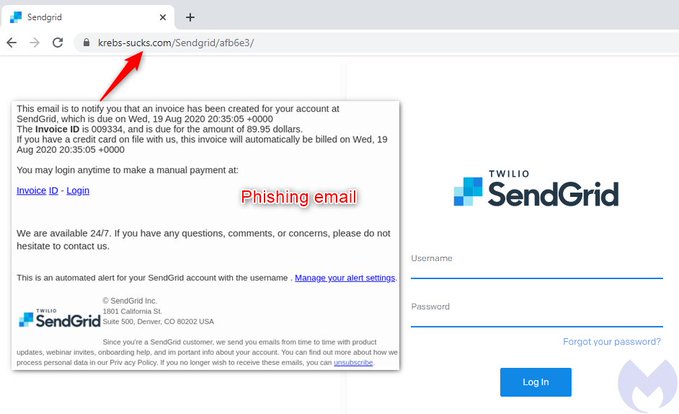
Brian Krebs Name Used in Phishing Exploit
Even well-known security researchers like Brian Krebs are occasionally selected for special treatment by a cyber-thug.
Krebs indication of compromise (IoC)
Alert from Brian Krebs about VPN Vishinig Scam
The Phishing Golden Hour
Roger Grimes wrote: “In emergency healthcare settings, the “golden hour” is the time between when a patient suffering a life-threatening event (e.g., heart attack, stroke, aneurysm, etc.) is most likely to recover with the best possible outcome if treated within a certain period of time by the appropriate therapies. Healthcare workers wishing to best help the most people are taught they need to quickly diagnose the right illness or injury and begin the right healing therapies. Every minute of delay further risks a patient’s positive outcome.
Cybersecurity researchers have applied the same idea to phishing attacks in their recent whitepaper entitled, Sunrise to Sunset: Analyzing the End-to-End Life Cycle and Effectiveness of Phishing Attacks at Scale. Looking at the behavior of 4.8 million successful phishing attack victims who got tricked into visiting over 400,000 unique phishing URLs, they gleaned some interesting facts.
This revealing post is too long for this newsletter and continued here:
https://blog.knowbe4.com/phishing-golden-hour
Share
AUG





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com