 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: FedEx Delivery Phish
Chef’s Special: Lazarus Spear Phishing
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Coinbase Phish
This looked fraudulent. I have a Coinbase account, but I don’t use it.
The link resolved to http://url7814.iwanacash.com/ls/click?upn {redacted}, and the domain matched the email sender’s. But the link was broken. I find that if I wait even overnight, these links are usually gone. VirusTotal said it was SPAM, not phishing, so maybe this is just an email to get me to switch from Coinbase to Iwanacash.
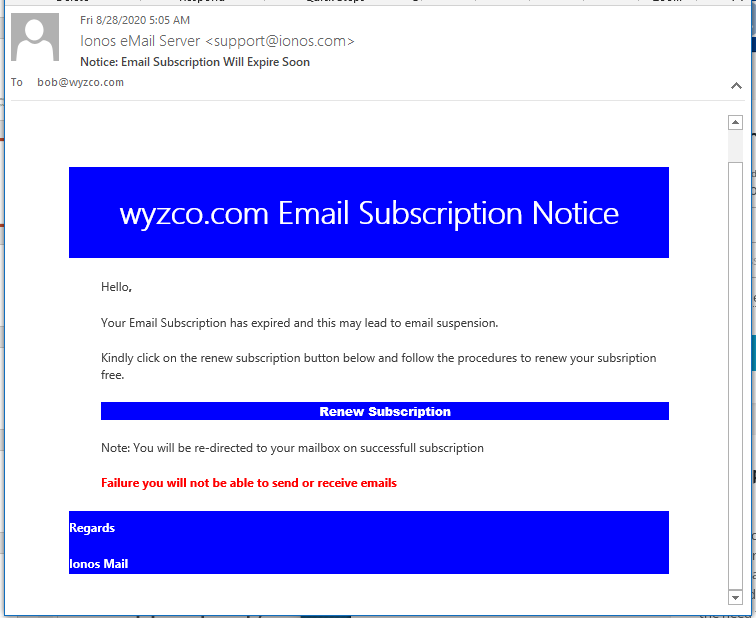
Another Email Account Credential Stealing Phish
Since email account hijacking AKA business email compromise (BEC) are so lucrative for attackers, it should be no surprise that so many phish are targeting your email account password. Here’s another. Let’s look at the elements that make it believable.
First, the sender looks like support@ionos.com. But the email header shows the email originating in Japan from IP address 219.94.163.152. To see email headers in Outlook, from the email message select the File tab, then click on the Properties button.
Return-Path: <support@ionos.com>
Received: from www1512.sakura.ne.jp ([219.94.163.152]) by mx.perfora.net
(mxeueus005 [74.208.5.3]) with ESMTPS (Nemesis) id 1MnJ6G-1kuaaW1TXw-00jGfr
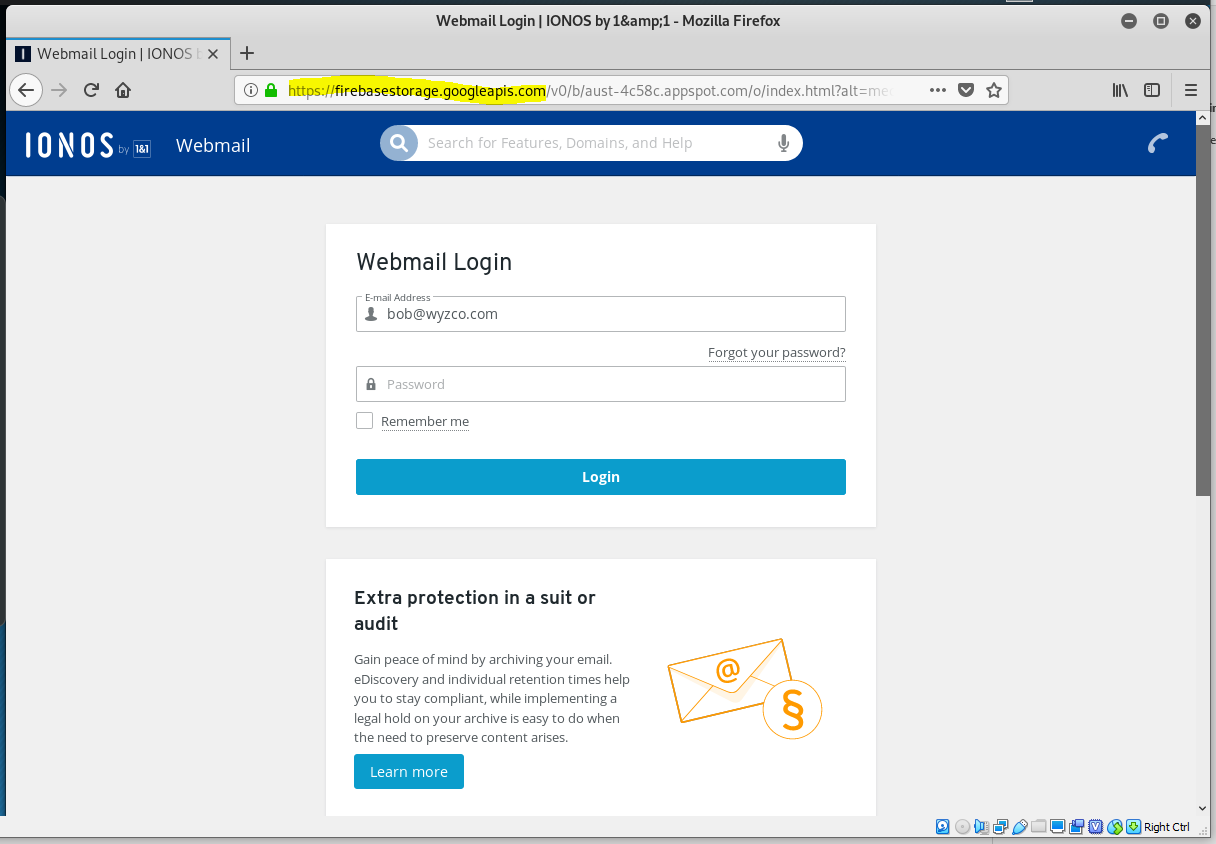
The bad grammar in the Failure warning is a clue this is fake. The Renew Subscription link resolves to a firebasestorage.googleapis address that has been popping up a lot lately.
https://firebasestorage.googleapis.com/v0/b/aust-4c58c.appspot.com/o/index.html?alt=media&token=66e80628-8380-4887-87da-5f922473bba6#bob@wyzco.com
The part at the end #bob@wyzco.com is the bit of code that personalizes the landing page. In fact this entire link is very much like a browser cookie. The additional “offer” on the web page is a nice touch that improves the apparent validity of the page. But the firebase address in the address box should be a warning.
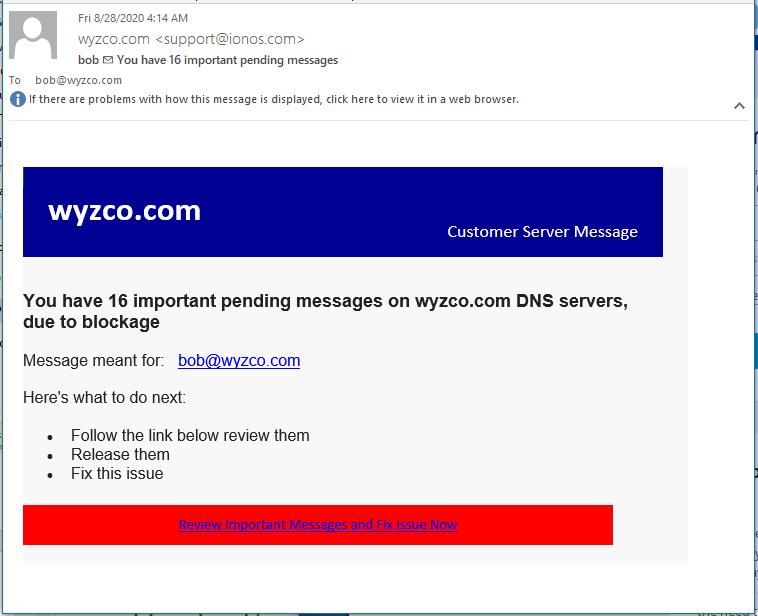
And Yet Another Email Account Credential Stealing Phish
Same tactics, same firebase destination. This comes under the social engineering category of “technical gobble-dee-gook.” If you can’t dazzle them with your brilliance, baffle them with your bullshit! The DNS system has nothing at all to do with sending or receiving email messages. DNS helps humans resolve friendly domain names humans like with the IP addresses that Machines need. Alright, you techy people, the DNS does hold the MX record that identifies the mail server your domain is using. But the DNS sytem is never holding messages for you.
Here’s the email.
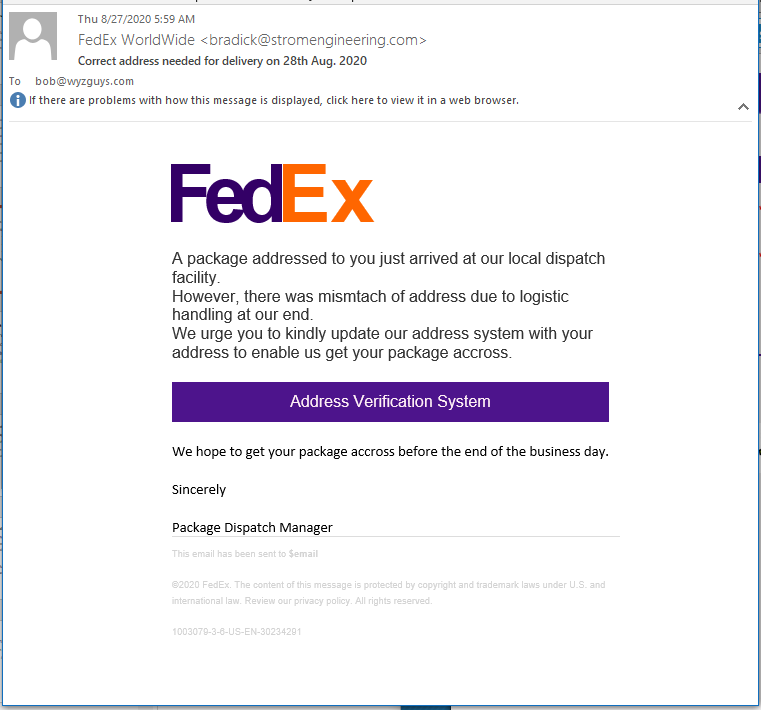
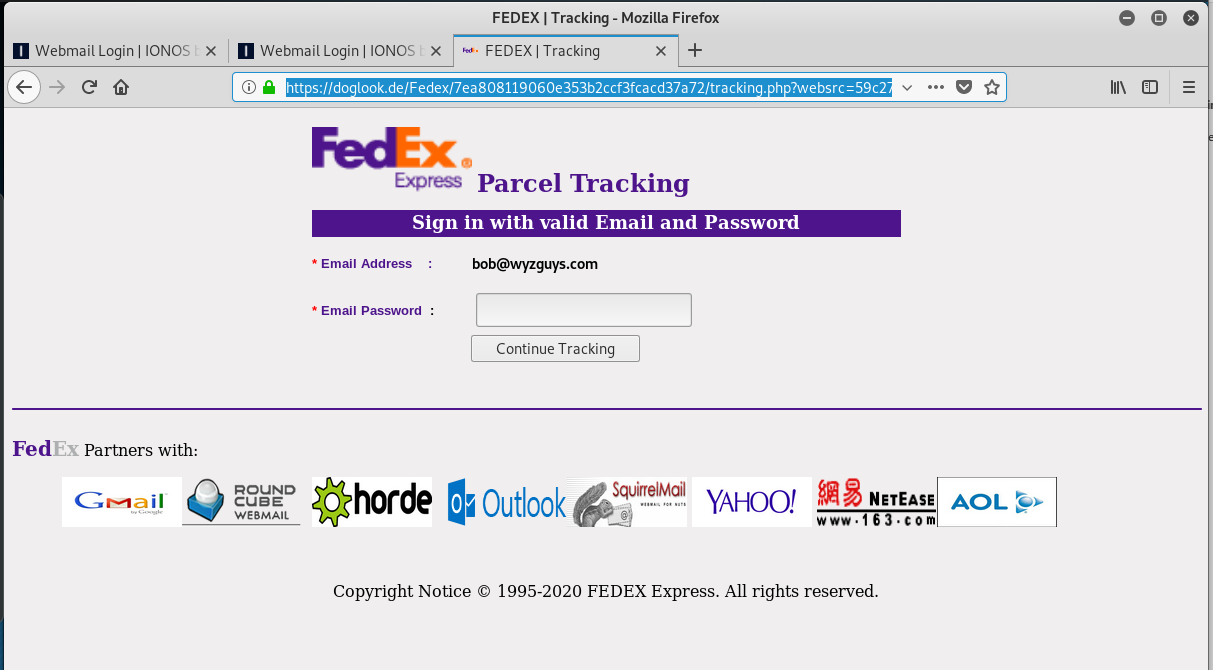
FedEx Delivery Phish
Here’s a fake FedEx phish. The sender email address is from Strom Engineering, which is wrong, of course. The Address Verification System link actually bounced me a total of four redirections, which makes this a bit more interesting than the average phish. Here they are:
https://0704801.us17.list-manage.com/pages/track/click?u=6026c34f032cb5adbeeded15b&id=f6376d6244/#Ym9iQHd5emd1eXMuY29t
https://leadigniter.ca/account/confirm/MTU5ODYyMjg2MjY0MTZjMDlhOTQ1Yzg0YzJlOGZlMzI1MzdiNWRlNDFmMjk4MmM0MmM6Ym9iQHd5emd1eXMuY29t
https://lapressechezvous.fr/#Ym9iQHd5emd1eXMuY29t
https://doglook.de/Fedex/7ea808119060e353b2ccf3fcacd37a72/tracking.php?websrc=59c275dc2e97dd3b896ed4ff2b82a8fd&dispatched=90&id=2515256756&email=bob@wyzguys.com#&^#&&787778377vhefhhgfnvshnHBsZS5jb20vc2hvcHwxYW9zNGJjMKJHlkgiutgKHklgklu66GY4MTI3ZGZhMWKJHKLGHGDJHKJNvbS9zaG9wL2FjY291bnQvc2V0dXAvc3RhcnQ_c=
The second URL is going through something called “lead igniter”. I am assuming that this scammer is getting paid every time traffic hits that URL, so this exploit has several income streams.
The landing page just looks like a FedEx credential stealing exploit.
New Lazarus Spear Phishing Attack on Crypto Organizations Uses a LinkedIn Job Posting as Its Front
What better way to gain complete control over a crypto organization’s network than to target their sysadmin with a Job Posting and then spear phish them?
It’s a brilliant and elegant attack. The Lazarus group (North Korean APT), formerly responsible for WannaCry, is jumping on the cryptocurrency-as-the-target bandwagon. We’ve seen prominent twitter accounts being hacked with crypto as the endgame, as well as recent vishing attacks on financial organizations to eventually gain access to high net worth customers’ cryptocurrency accounts.
According to security researchers at F-Secure, in this latest attack from Lazarus, a legitimate LinkedIn ad is posted looking for a sysadmin for a blockchain technology company. The ad targets current sysadmins at cryptocurrency orgs. Once a candidate sysadmin engages via the ad, they are sent a Word document as part of the process, complete with the claim that the document is protected under GDPR and requires macros to be enabled.
Once enabled, a series of malicious actions occur including the conducting of system checks and downloading system-specific malware payloads. Credential harvesting, deletion of security log entries, and lateral movement are all part of the attack.
Despite the sophistication of the attack, there is one common, non-technical element that determines whether this campaign works or not – the human.
The success or failure of this attack rests solely with the sysadmin; if they don’t fall for the macro enabling and realize this is probably a scam, the whole thing falls apart.
This is why I recommend that everyone – from the mailroom to the boardroom step through new-school security awareness training and educate employees on common tactics that are not just used, but often required as part of a phishing attack.
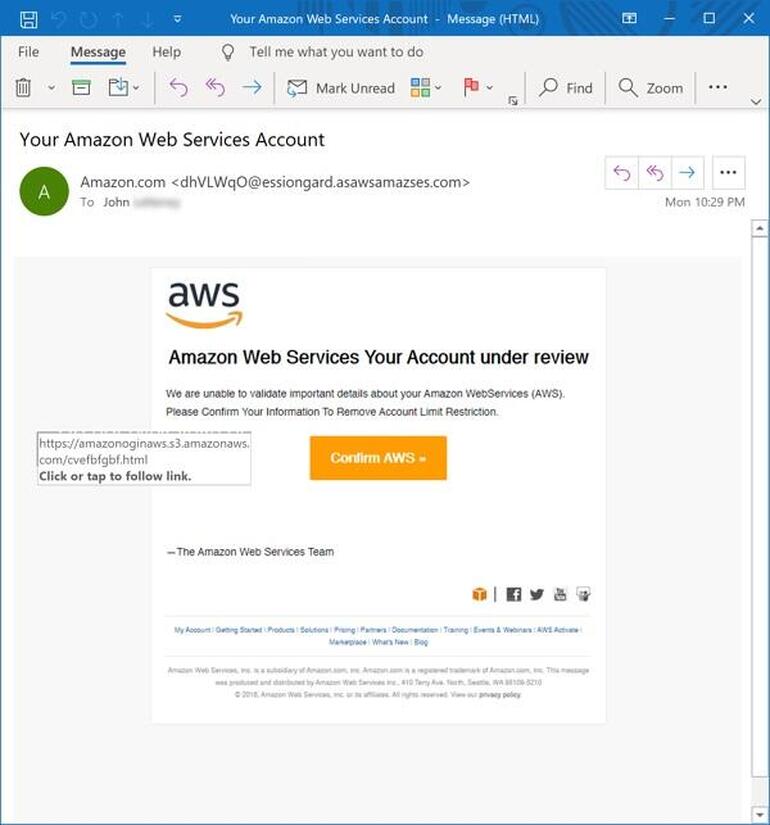
How phishing attacks have exploited Amazon Web Services accounts
Phishing campaigns could compromise business data and use Amazon’s cloud platform to launch further attacks, says KnowBe4.
Share
SEP






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com