Catch of the Day: Mail Delivery Phish
Chef’s Special: Top Scam Phish
Also serving: Spear Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Mail Delivery Phish
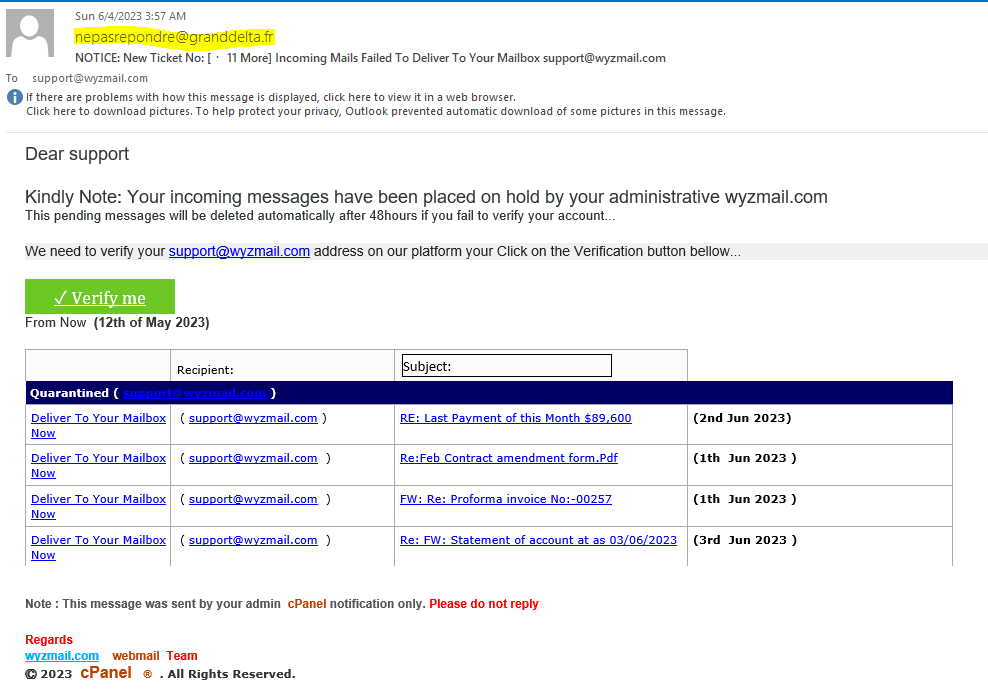
I received this email delivery alert phish on Sunday June 4 at 3:57 am, and by the time I got to analyzing it at 7:24 am, it was already partially taken down. Here is the email
The Verify me button resolved to https://link.tmr04.com/c?q=lbD5GWGoGQzevhjHIJAR5AZF2gBraHR0cHM6Ly9pcGZzLmlvL2lwZnMvUW1ZQ05qR01Eb2JrRnhWaHRvd2RaWnpaVXlWVUZzWnozVFB1R0dYZWFKb0o2Yj9maWxlbmFtZT1ibGF6ZS5odG1sI3N1cHBvcnRAd3l6bWFpbC5jb22sZEJSZ5kysV-YF24HrGR8UcHksDTjrlr2Xa5saW5rLnRtcjA0LmNvbQ and that redirected to https://ipfs.io/ipfs/QmYCNjGMDobkFxVhtowdZZzZUyVUFsZz3TPuGGXeaJoJ6b?filename=blaze.html#support@wyzmail.com.
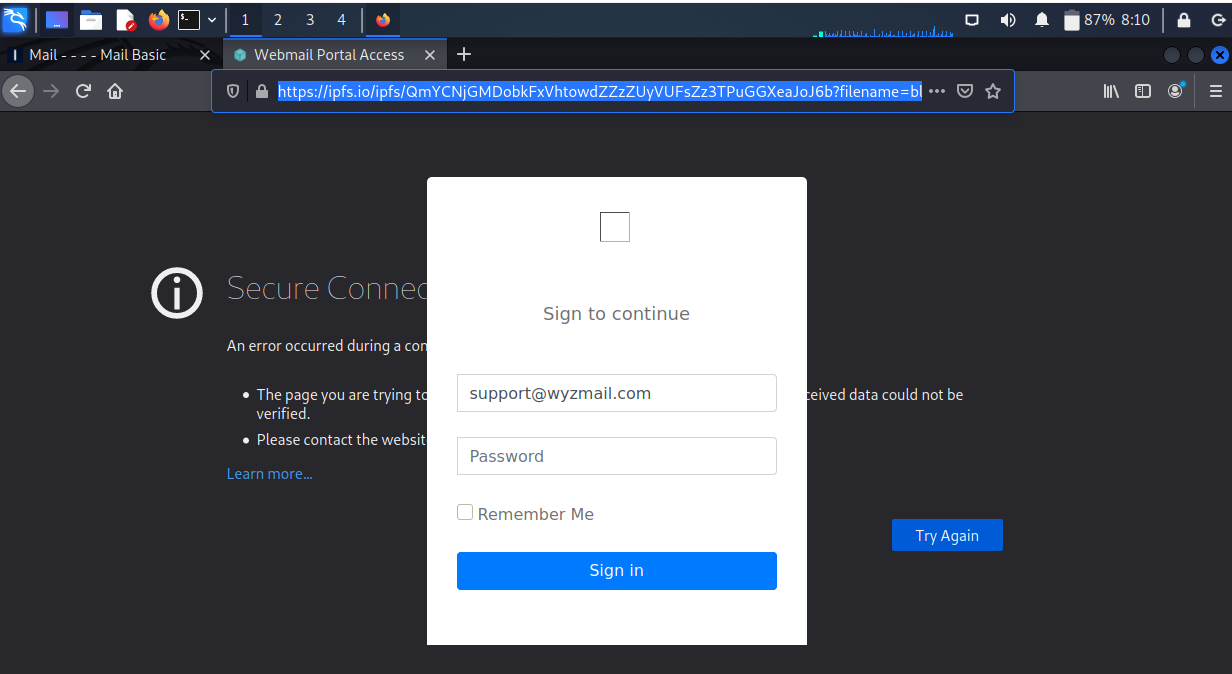
Here is the landing page. The login window still appears, even though the rest of the page is displaying an error message.
This is yet another credential stealing exploit. The addition of technical information on the email possibly makes it more plausible. Never enter your logon credentials from a link in an email,such as this one.
The Q1 2023’s Top-Clicked Phishing Scams | INFOGRAPHIC
KnowBe4’s latest reports on top-clicked phishing email subjects have been released for Q1 2023. We analyze “in the wild” attacks reported via our Phish Alert Button, top subjects globally clicked on in phishing tests, top attack vector types, and holiday email phishing subjects.
IT and Online Services Emails Drive Dangerous Attack Trend
This last quarter’s results reflect the shift to IT and online service notifications such as laptop refresh or account suspension notifications that can affect your end users’ daily work.
Cybercriminals are constantly increasing the damage they cause to organizations by luring unsuspecting employees into clicking on malicious links or downloading fake attachments that seem realistic. Emails that are disguised as coming from an internal source, such as the IT department, are especially dangerous because they appear to come from a trusted place where an employee would not necessarily question it or be as skeptical.
Building up your organization’s human firewall by fostering a strong security culture is essential to outsmart bad actors. The report covers the following:
- Common “In-The-Wild” Emails for Q1 2023
- Top Phishing Email Subjects Globally
- Top 5 Attack Vector Types
- Top 10 Holiday Phishing Email Subjects in Q1 2023
This post has a full PDF infographic you can download and share with your users:
https://blog.knowbe4.com/q1-2023-top-clicked-phishing
Share
JUN





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com