 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Undelivered Mail Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Undelivered Mail Phish
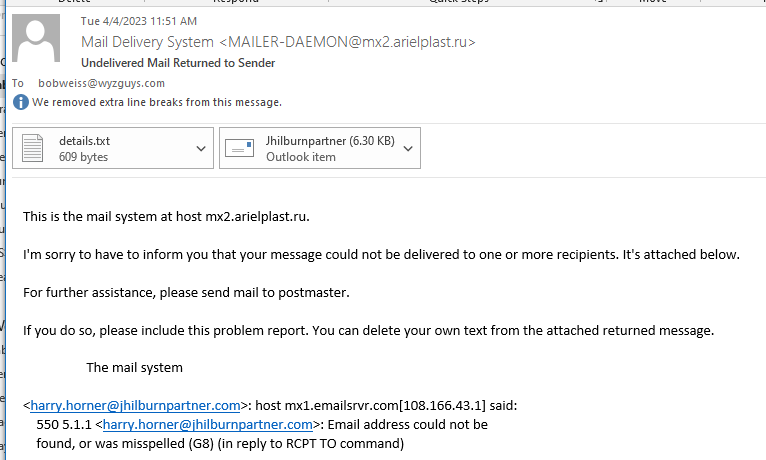
Not sure what this phishing email was trying to accomplish. But there are a lot of interesting parts, starting with the sender email address <MAILER-DAEMON@mx2.arielplast.ru, which is a Russian mail domain.
The mail was supposedly returned to
<harry.horner@jhilburnpartner.com>: host mx1.emailsrvr.com[108.166.43.1] said: 550 5.1.1 <harry.horner@jhilburnpartner.com>: Email address could not be found, or was misspelled (G8) (in reply to RCPT TO command)
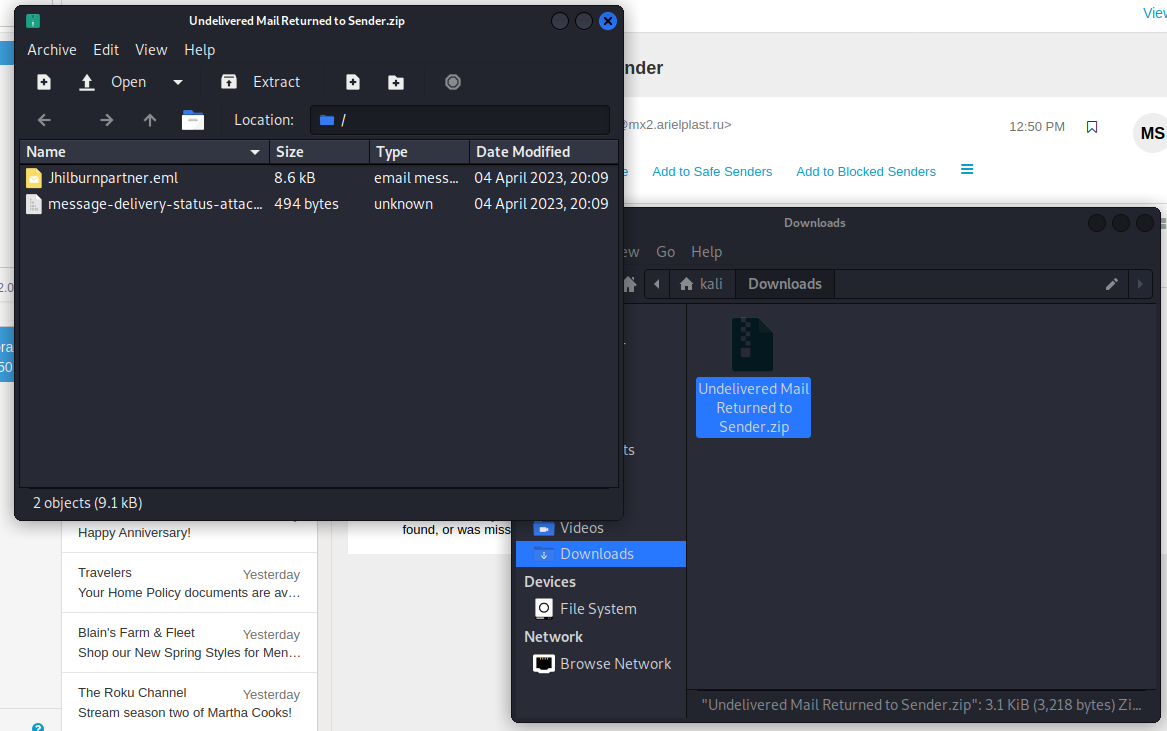
There were two attachments, a TXT file and an EML email document, that I was itching to take a look at
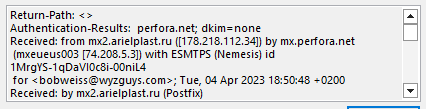
The mail headers confirmed the source was in Russia.
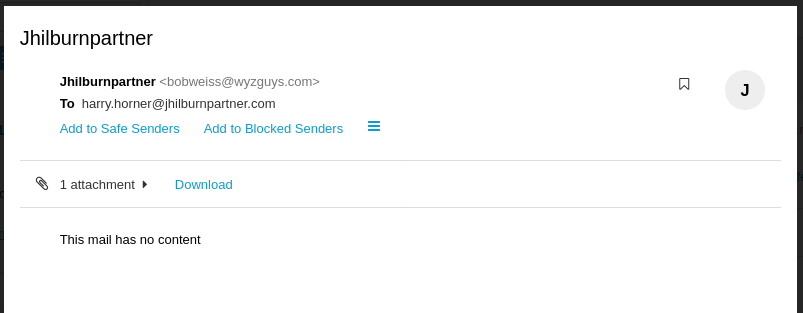
I opened the email in Firefox in my Kali Linux virtual machine. The EML attachment had no content
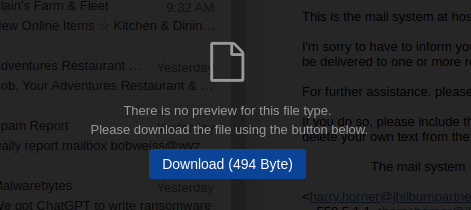
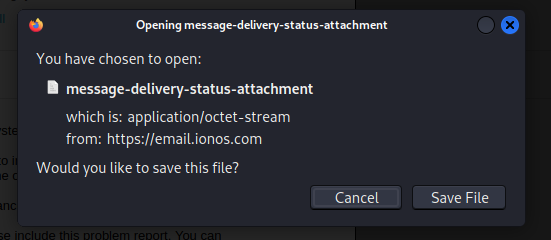
And the TXT file gave me this warning from Firefox
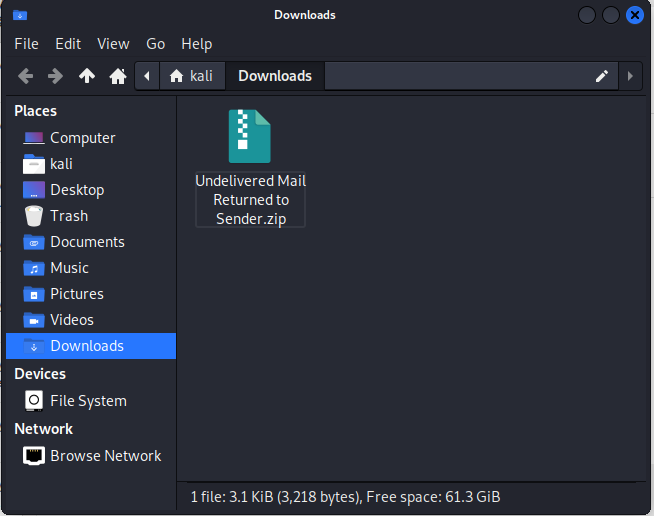
I downloaded the ZIP file
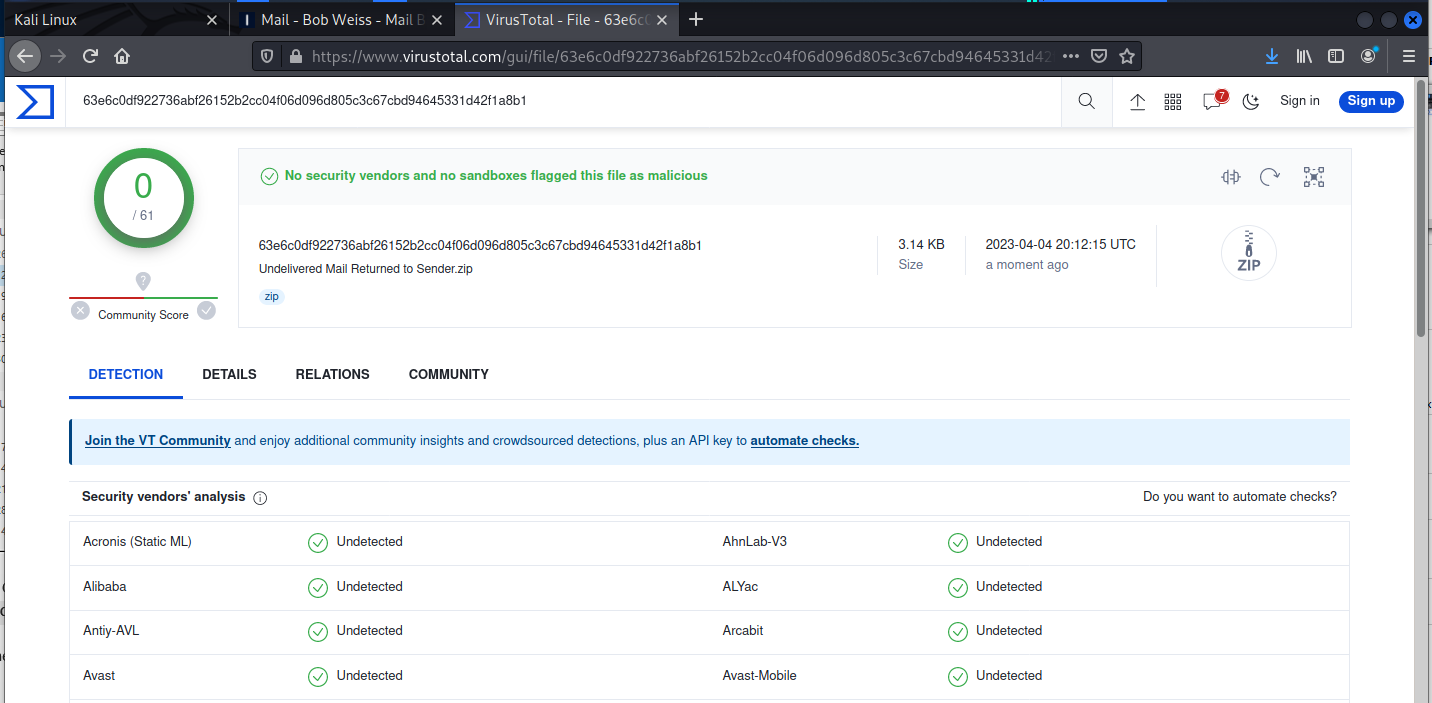
And I uploaded it to Virustotal.
Then I unzipped the ZIP file and uploaded both of these files to VIrustotal.
Unfortunately, these documents did not generate a malicious report. So disappointing. And so I am left wondering what this was all about. It could be a trial run testing a new exploit kit, and perhaps I will see more phishing emails like this one. Return Email messages are not generally blocked by spam filters, so this might be an attempt at proving the ability to bypass spam filtering. We shall see.
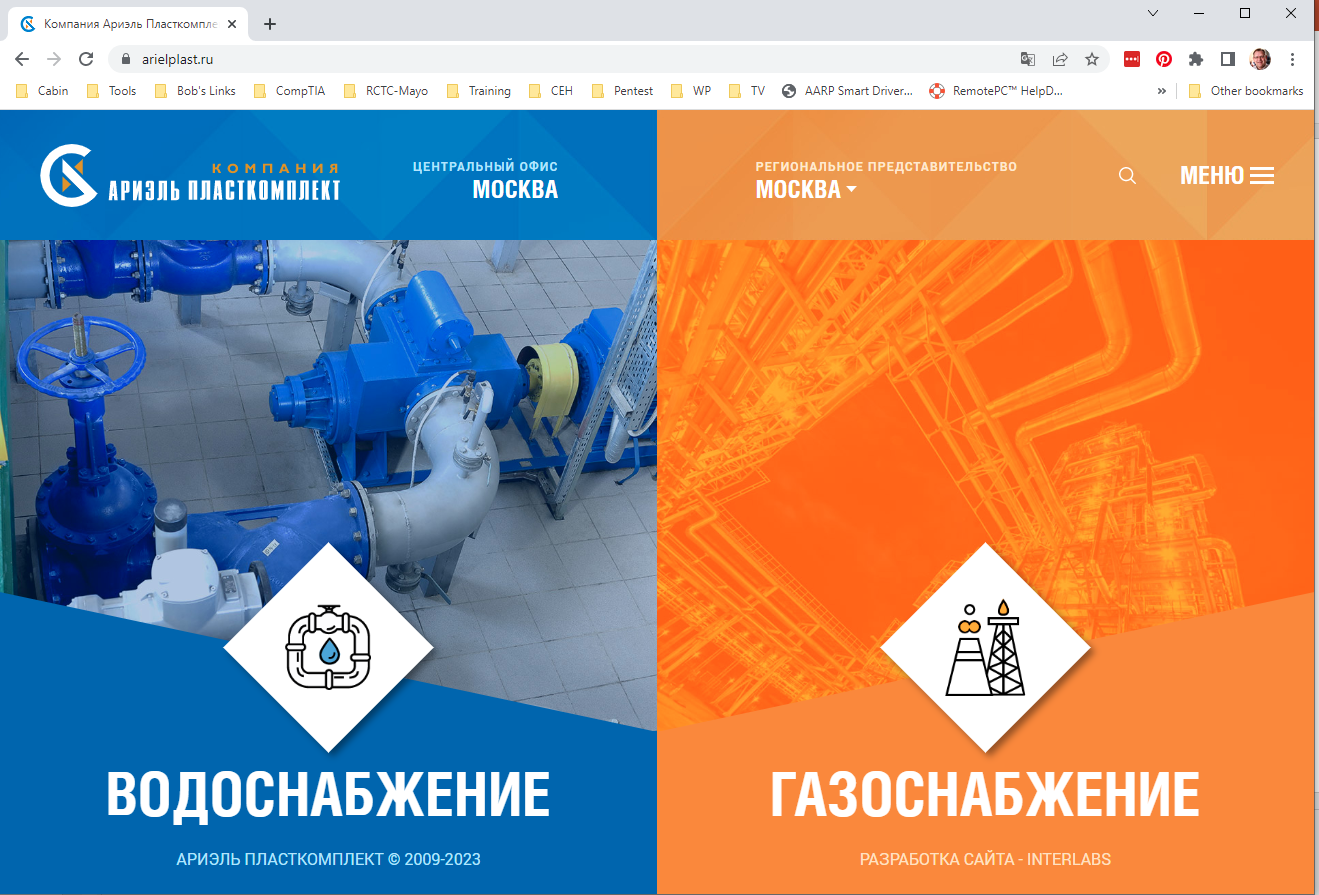
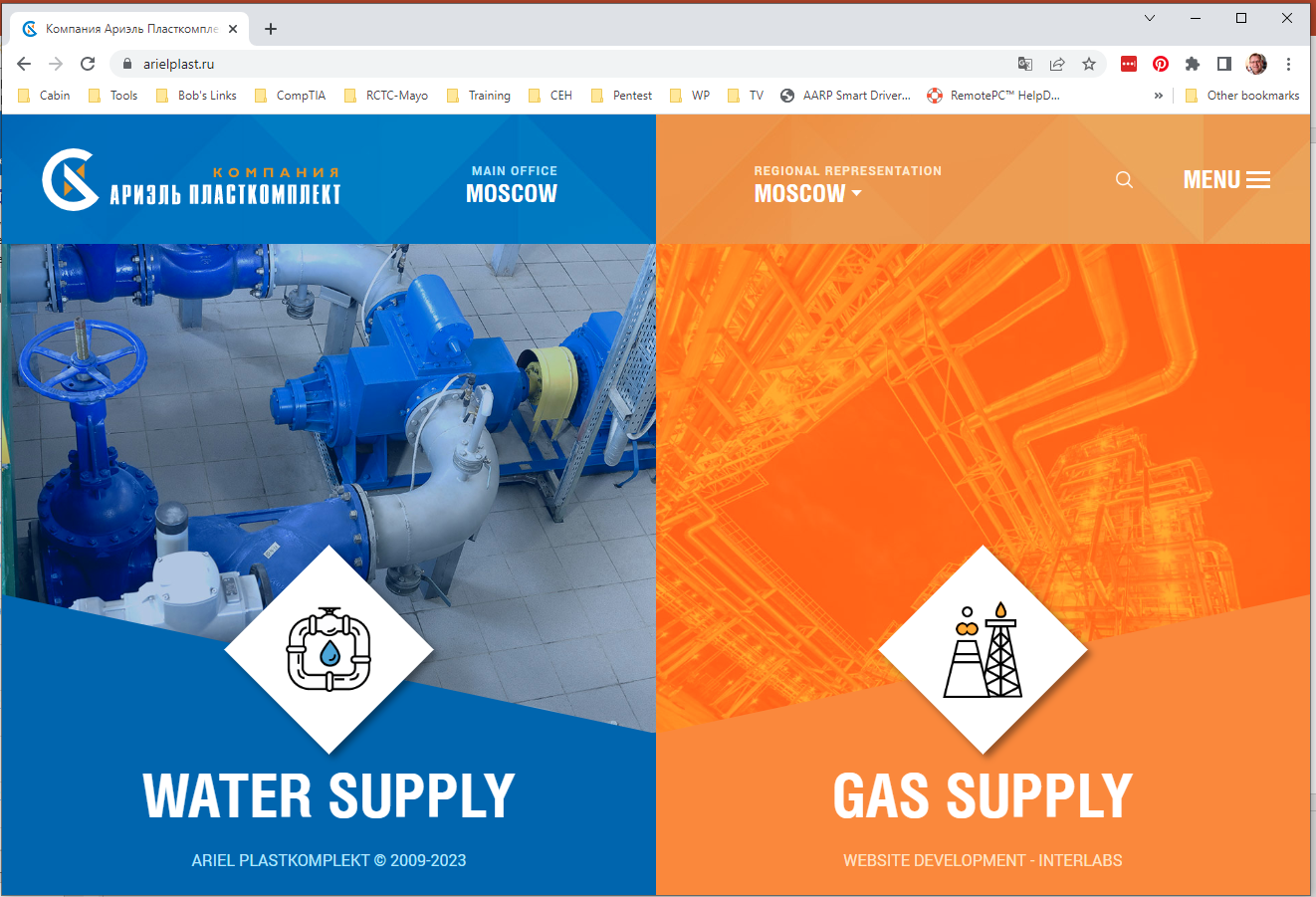
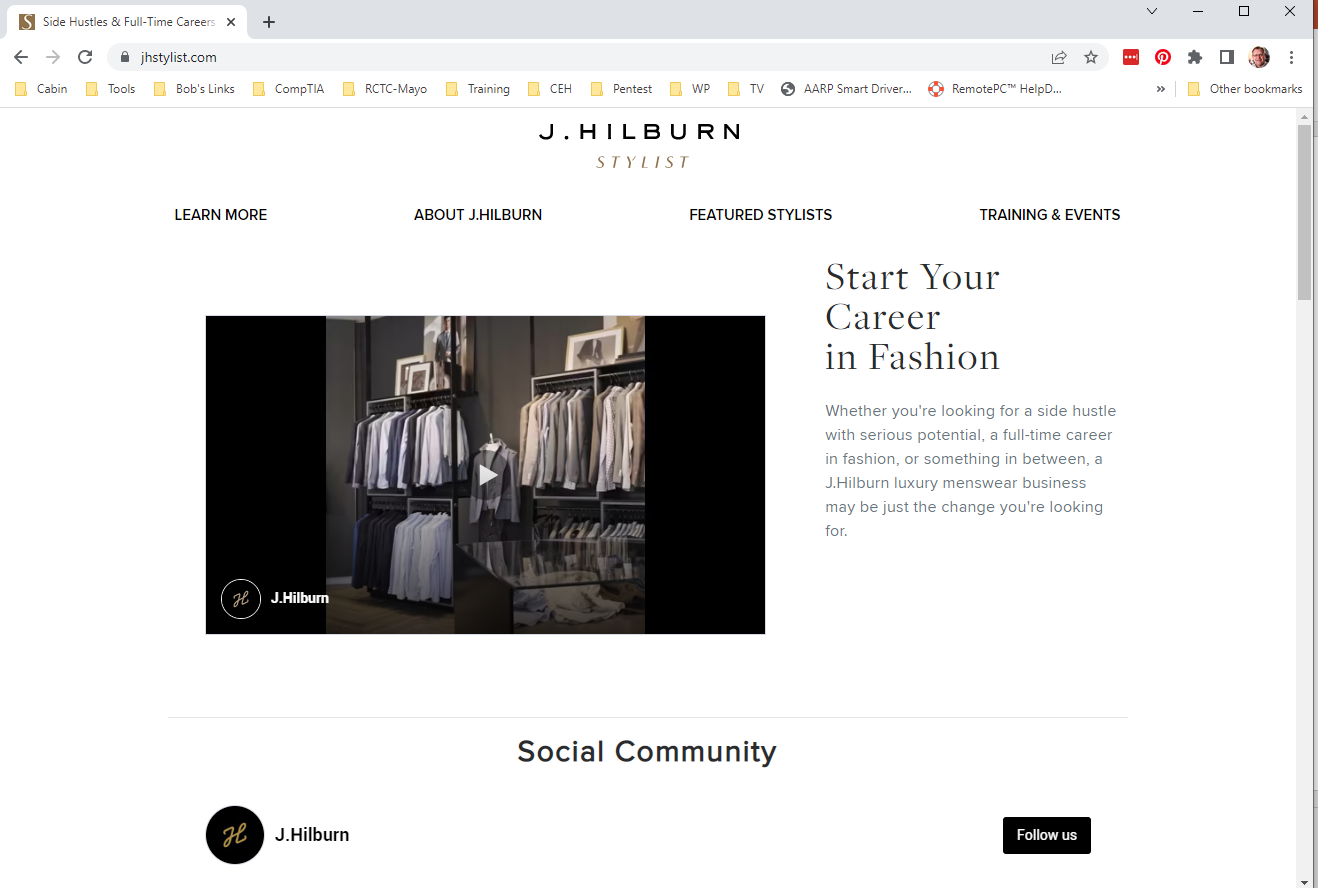
I checked out the two email domains arielplast.ru and jhilburnpartner.com, and found the following web site home pages. This did nothing to alleviate the mystery. Clearly a Russian web site
After a little work by Google Translate
And just how a haberdashery fits in here is anyone’s guess. If you have ideas about this one, please share then with me by leaving a comment below.
Share
APR




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com