 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Help Desk Phish
Chef’s Special: Norton Invoice Phish
Also serving: Email Cancellation Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Help Desk Phish
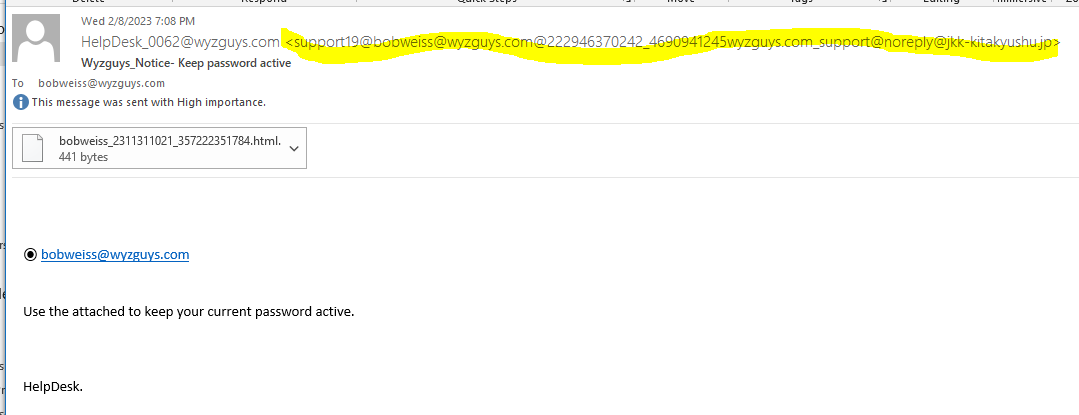
This one got away. By the time I was able to investigate, the second landing page was gone. This email arrived at 7:31 pm last night, and was gone by 8:26 am today. So this exploit was down in less than 13 hours.
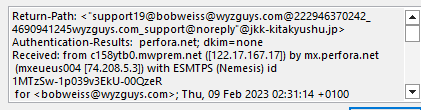
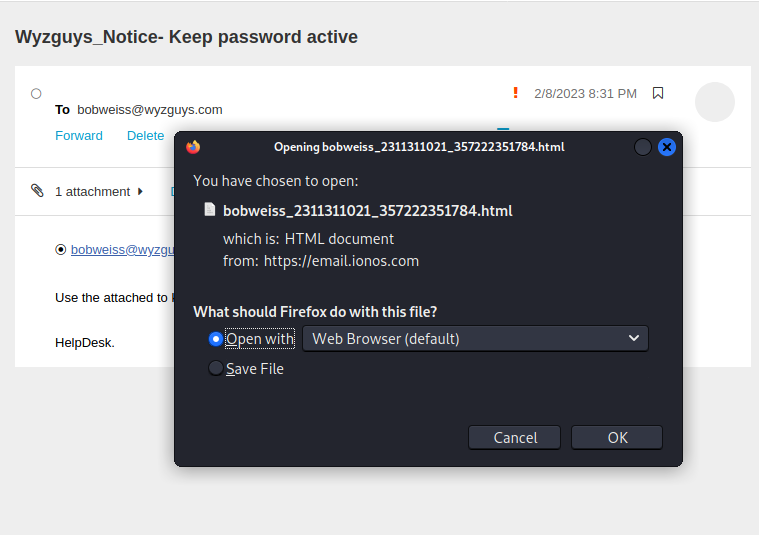
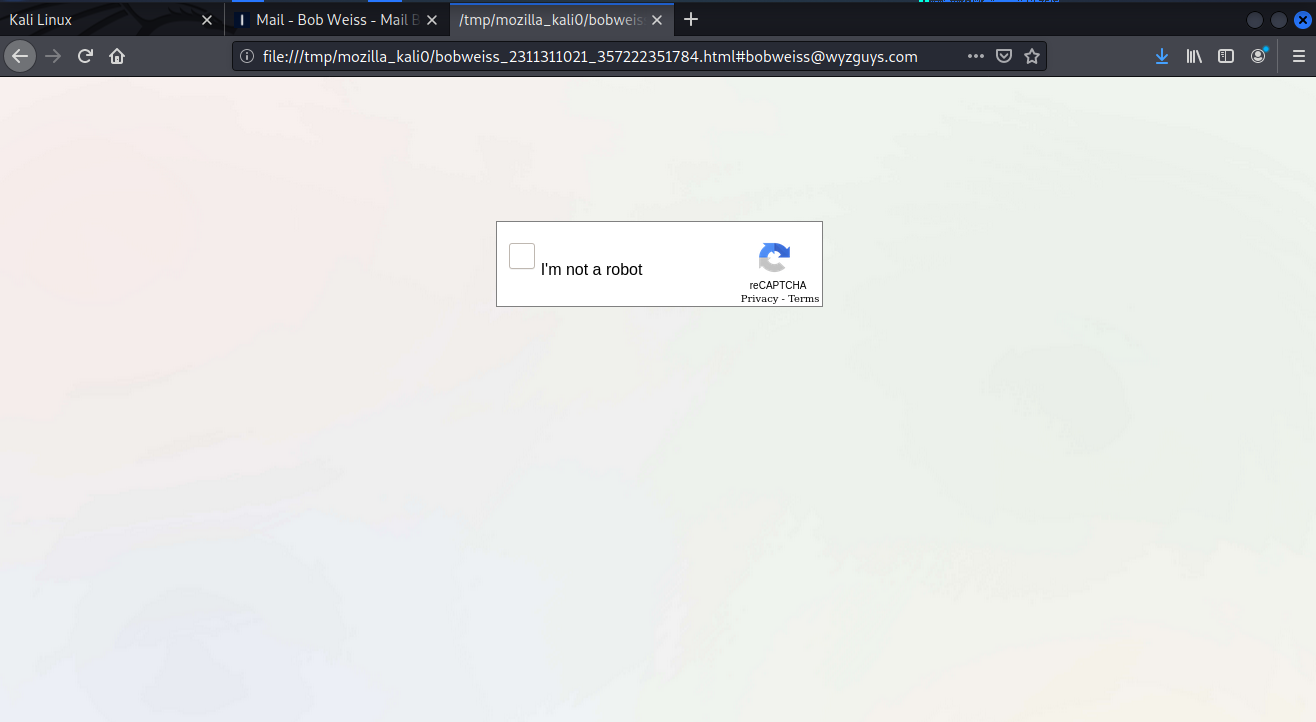
The lengthy sender emaill address is descigned to obscure the Japanese email domain @kk-kitakyushu.jp . The mail link bobweiss@wyzguys.com is just a mailto. The payload is the attached HTML file. Opening the file displayed a CAPTCHA. And clicking on the CAPTCHA directed us to a page that was missing. This had the hallmarks of a credential stealing exploit.
The email headers confirmed the JP sender address
Opening the HTML attachment in Firefox on Kali
The HTML attachment created this CAPTCHA page, which is hosted by the local machine (my laptop). No need to secure a web server. The CAPTCHA redirected us to https://wse-834363904639-com.sbs/
And this is where our investigation ended. I was curious about the sbs top level domain. This is what I found on Google:
Norton Invoice Phish
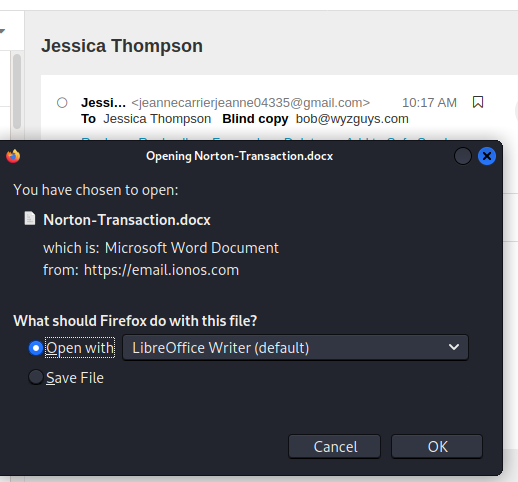
Here is a simple phishing exploit that uses a call center hook. From the email it looks like I just paid for a $492.00 Norton subscription.
I opened the attachment
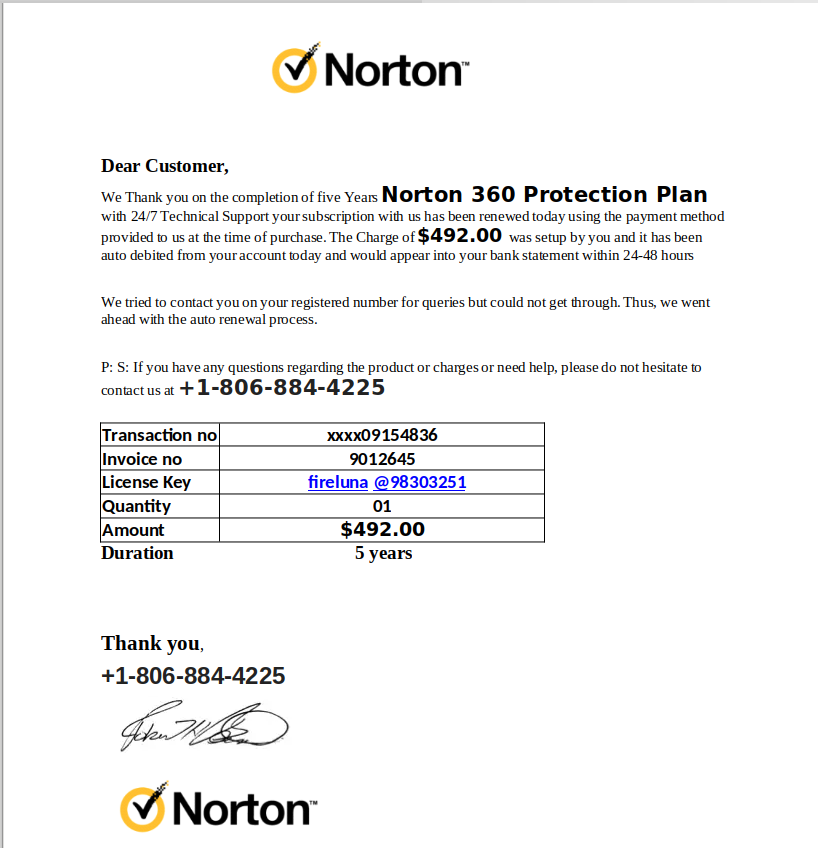
Here is the invoice, which the helpful phone number. At this point, you may believe that someone has charged your credit card fraudulently, but if you checked with the credit card company, this transaction would not exist – yet.
The goal of this attack is to get you to call the number and dispute the charges. The friendly support person will be happy to help, but they will need your credit card number to process the refund. Now there will be some real charges on your card.
If you want to dispute a charge, do it through your credit card company.
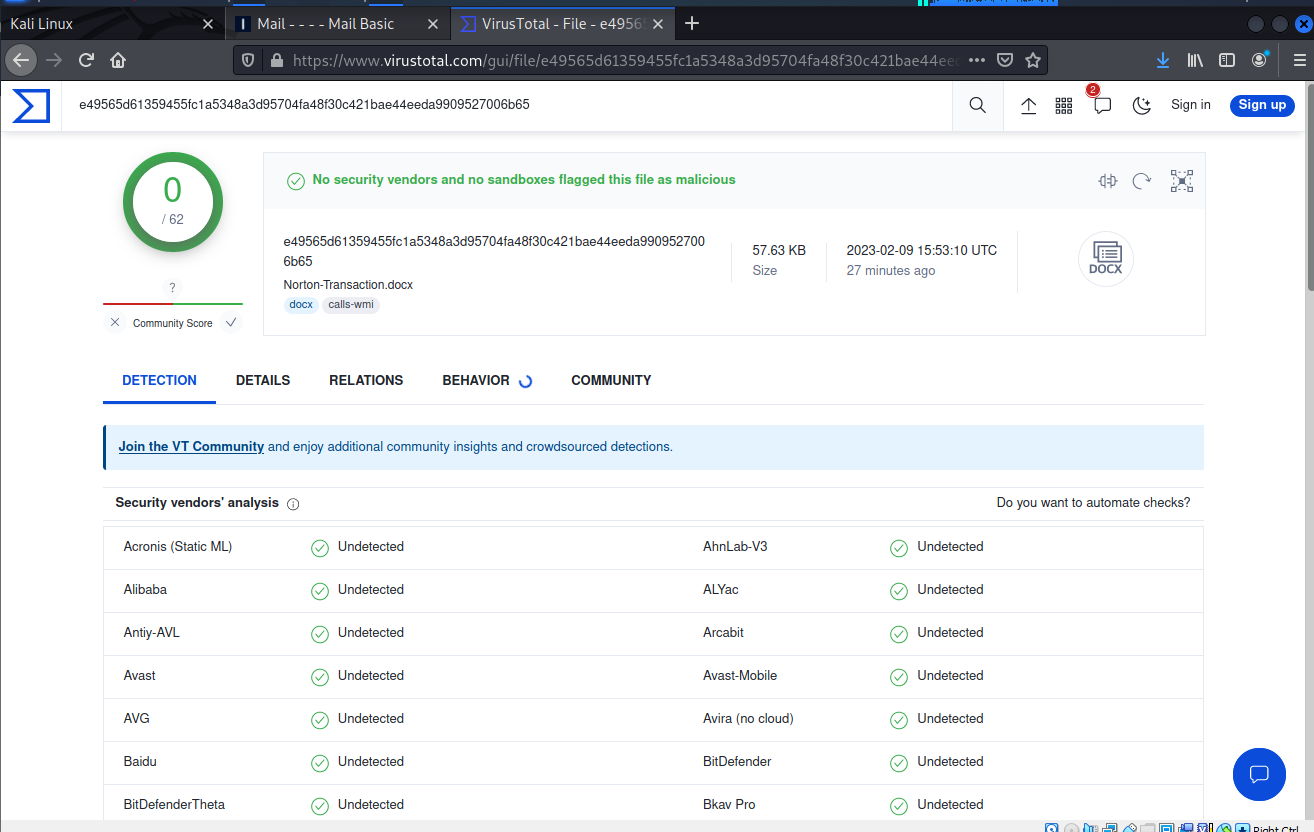
I decided to check and see if the Word document was using a macro-virus or had embedded malware, but VirusTotal gave it a clean bill of health.
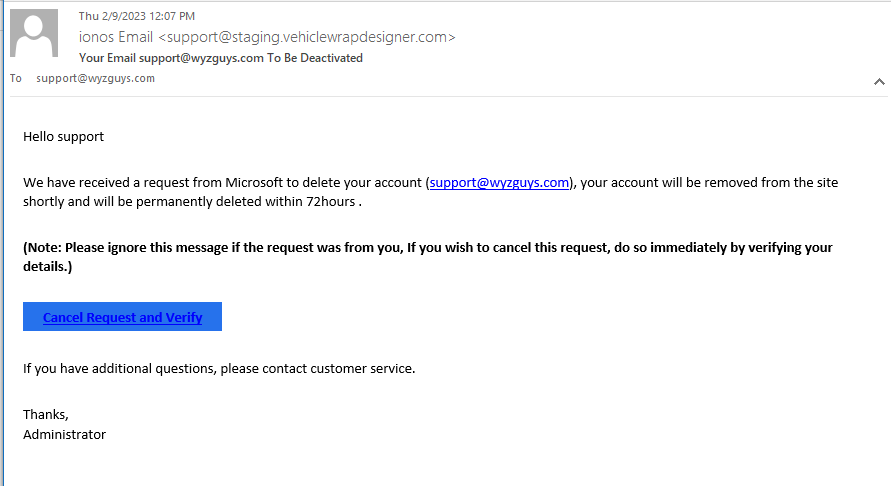
Email Cancellation Phish
Microsoft wants my web host to delete one of my email accounts! Horrors!! And totally bogus. The Cancel Request and Verify link go to https://srv64.hostserv.co.za/~alkarelectricalc/wp-admin//remove/autolink.php?email=support@wyzguys.com a server with a South African TLD in the URL
The link took me to a Forbidden notice. This exploit also was taken down in record time.
Russian and Iranian Spear Phishing Campaigns
The U.K.’s National Cyber Security Centre (NCSC) has described two separate spear phishing campaigns launched by Russia’s SEABORGIUM threat actor and Iran’s TA453 (also known as Charming Kitten). The NCSC says both threat actors have targeted entities in the U.K., including “academia, defence, governmental orgs, NGOs, think-tanks, as well as politicians, journalists, and activists.”
The threat actors first conduct reconnaissance on their targets by researching social media and other open-source information. After this, they’ll make contact under the guise of a journalist, colleague, or someone else the victim would be likely to respond to.
“Having taken the time to research their targets’ interests and contacts to create a believable approach, SEABORGIUM and TA453 now start to build trust,” the report says. “They often begin by establishing benign contact on a topic they hope will engage their targets.
“There is often some correspondence between attacker and target, sometimes over an extended period, as the attacker builds rapport.” The threat actors then send the victim a link disguised as something related to their previous conversations.
“Once trust is established, the attacker uses typical phishing tradecraft and shares a link, apparently to a document or website of interest,” the NCSC says. “This leads the target to an actor-controlled server, prompting the target to enter account credentials. The malicious link may be a URL in an email message, or the actor may embed a link in a document on OneDrive, GoogleDrive, or other file-sharing platforms.
“TA453 has even shared malicious links disguised as Zoom meeting URLs, and in one case, even set up a Zoom call with the target to share the malicious URL in the chat bar during the call. Industry partners have also reported the use of multi-persona impersonation (use of two or more actor-controlled personas on a spear-phishing thread) to add the appearance of legitimacy.”
New-school security awareness training enables your employees to make smarter security decisions every day and spot these attacks for what they are.
Blog post with links:
https://blog.knowbe4.com/russian-iranian-spear-phishing-campaigns-in-uk
Travel Themed Phishing Attacks
New analysis of December and January emails shows massive spikes in attacks aimed at stealing personal information and credit cards under the guise of once-in-a-lifetime travel deals.
Who wouldn’t want a free airline ticket, or a ton of frequent flyer points in exchange for little-to-no effort? That’s exactly the sentiment attackers are going for, according to new analysis by email security vendor BitDefender’s Antispam Lab. Nearly 10% of all spam was travel themed within the timeframe of December 20 through January 10, with a little more than half (53%) of it targeting the United States.
Many of these scams focus on credential theft. According to the findings, travel rewards programs and gift cards are the most often used subjects, as the personal details held within those programs include birthdates, social security numbers, etc. that can be monetized by selling them on the dark web. BitDefender offered up a few examples of these emails – notice how legit they look:
[CONTINUED] Blog post with screenshots and links:
https://blog.knowbe4.com/travel-themed-phishing-attacks-lure-victims
HTML Smuggling: The Hidden Threat in Your Inbox
Last October, Trustwave SpiderLabs blogged about the use and prevalence of HTML email attachments to deliver malware and phishing for credentials. The use of HTML smuggling has become more prevalent, and we have since seen various cybercriminal groups utilizing these techniques to distribute malware.
HTML smuggling employs HTML5 attributes that can work offline by storing a binary in an immutable blob of data within JavaScript code. The data blob, or the embedded payload, gets decoded into a file object when opened via a web browser. Threat actors take advantage of the versatility of HTML in combination with social engineering to lure the user into saving and opening the malicious payload. More…
Share
FEB







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com