 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Mega Millions Lottery Phish with a side of Nigerian Prince
Chef’s Special: IONOS Mail Update Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
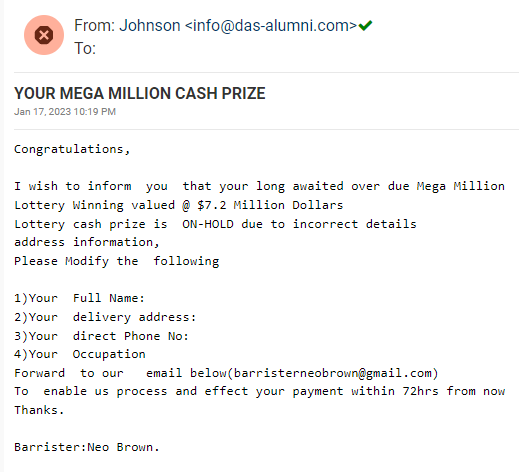
Mega Millions Lottery Phish
This lottery phishing scam is taking advantage of the recent $1,348 billion Mega Millions jackpot won in Maine on Friday Jan 13. It is extremely low tech, a simple plain-text phishing email without links or attachments. The instructions are designed to get you to part with some personally identifying information (PII), and to open an email dialog with some scam artist who will require some kind of advance fee or banking routing information. This falls into the category of a typical Advance Fee, 419, or Nigerian Prince type of scam, but is using actual events as a hook. Didn’t win the big prize? Maybe you won a smaller but still significant prize!.
Here’s the email:
The sender email address (info@das-alumni.com) is dodgy. The big tip-off is the title “Barrister.” In American we call them attorneys. Barrister is a term that applies to legal council in the UK or other countries that were colonies of the British Empire. And really – Neo Brown? The scammer must be a Matrix fan, and located in the UK or a former British colony
This email was actually captured by my Spamdrain email filter, so for me it was handled correctly
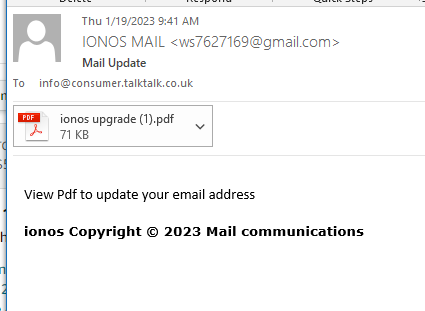
IONOS Mail Update Phish
I know I show a lot of these fake IONOS phish, and you may be wondering about the significance of these sorts of phishing exploits in your cybersecurity environment. Well, IONOS is my domain name registrar and web host; hosting this website and most of my email accounts. In your world these emails will appear with the graphics and trade dress of the domain registrars, web hosts, and email host you work with. This would be companies such as GoDaddy, Bluehost, HostGator, DreamHost, InMotion Hosting, and other web service providers, the companies you may be working with.
This email came from a Gmail account, which would not be used by a legitimate business. In this case the email sender should be using the ionos.com email domain.
This email was send to a group distribution address info@consumer.talktalk.co.uk, which is also unusual for a legitimate business.
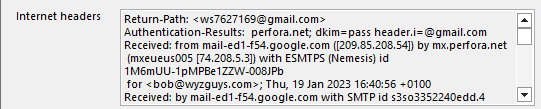
The email came from a google.com email server, which is also wrong. Google and IONOS compete in the web hosting space.
The email serves address is 209.85.208.54 which looks like Google facilities located in Finland.
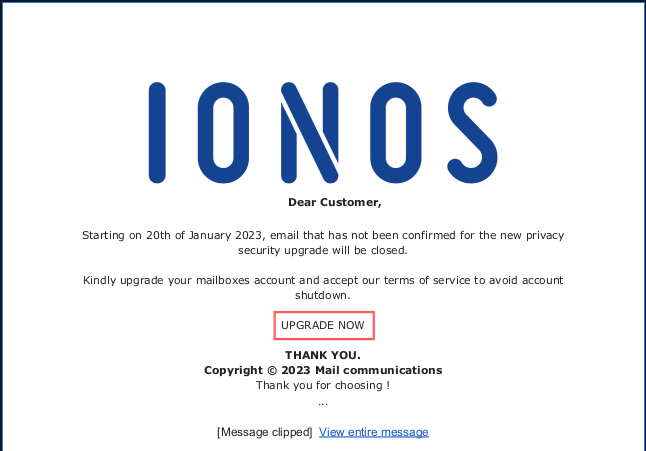
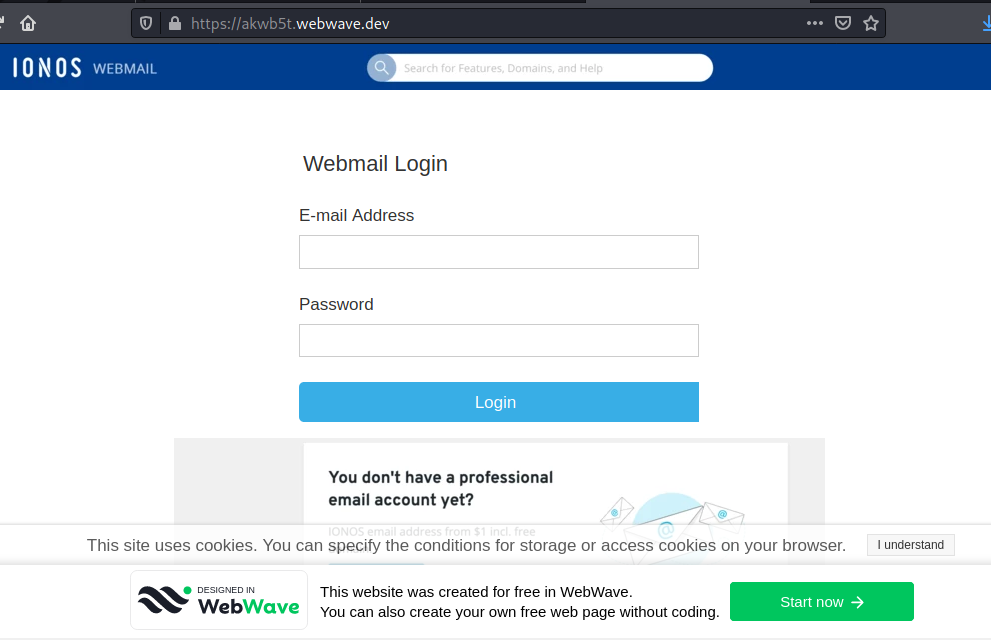
The attached PDF file is shown below. The Upgrade Now but is anchor text for an active web link at https://akwb5t.webwave.dev. Webwave.dev is a Polish web services provider.
Webwave.dev is being used to host the landing page below. I entered an email address I use for testing purposes and a made-up password. When I clicked on Login I was actually bounced to the authentic IONOS webmail login interface. I am assuming that this is another credential harvesting exploit.
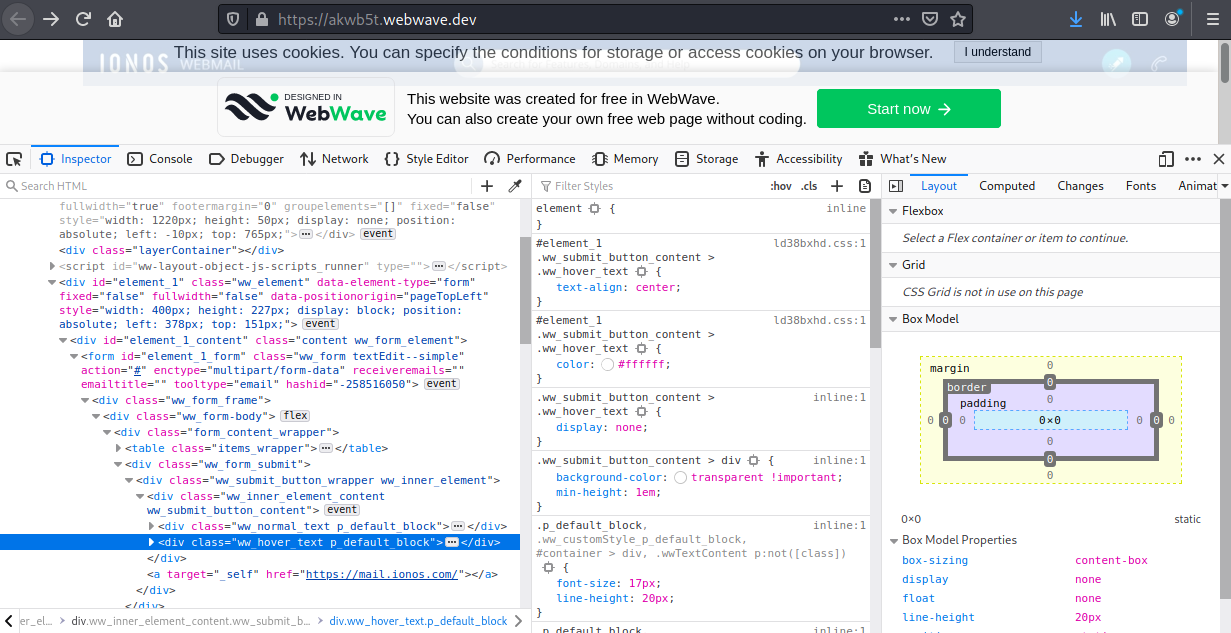
I decided to take a look under the hood and look at the exploit code. I am not going to take a lot of time explaining what all this is, but there is a script call that is probably used to send the form entry to the attacker’s C2 server, or maybe just to a small database on Webwave. If you look too rows below the blue bar, you will see the command that sent me to the legitimate IONOS login page.
So this phishing exploit pulled together a Google email from Finland and a hosting provider in Poland to provide infrastructure for this exploit. I will take a look in a day or two to see if Webwave pulls down this exploit or not. Stay tuned…
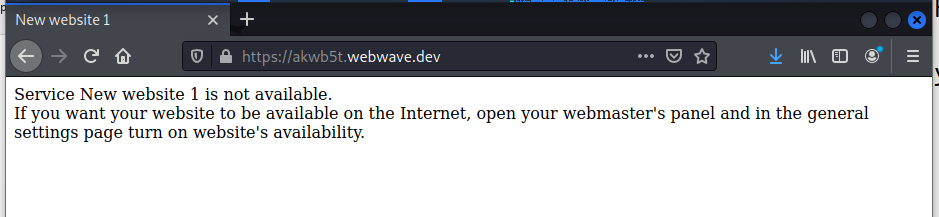
And one day later the exploit landing page is gone. Probably cleaned out by the host Webwave after notification from a cybersecurity firm or governmental cyber agency.
Share
JAN





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com