 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: IONOS Update Phish
Chef’s Special: IcedID Phishing
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
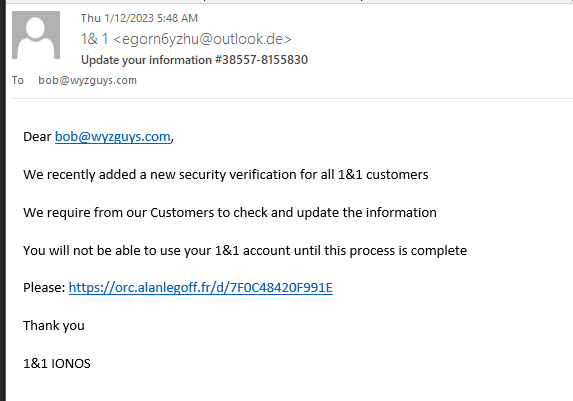
IONOS Update
Here is another example of an exploit that targets not only logon credentials, but othe types of PII as well. I received this on a Thursday, and by the time I has time to look at this, it was Sunday, the the hosted bits had already been removed.
Here’s the email
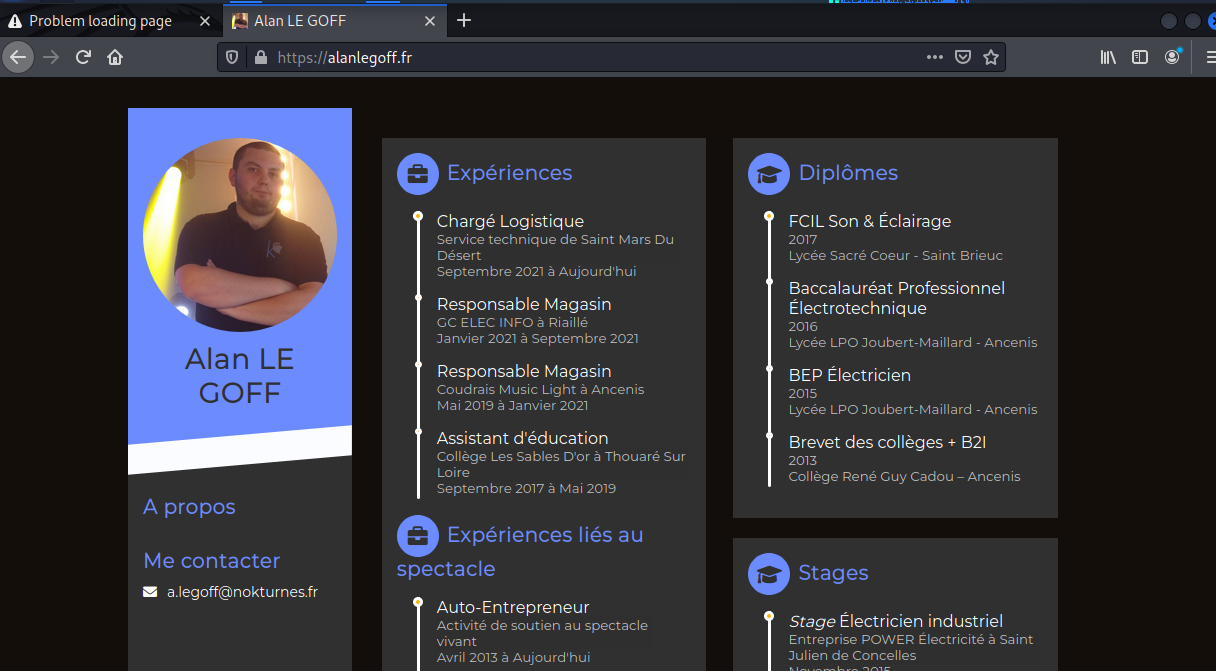
The link resolves to a hidden subdomain on the personal web page of Alan Le Goff. The exploit landing pages have been removed or disabled. Exploits like this one have a short life span, there are so many eyes watching for this kind of illicit activity that they are cleaned up in two – three days time.
Here is the home page of the previously hijacked website. It looks like it may be a WordPress site, although my attempt to confirm that were not definitive. Maybe a Joomla or Drupal site
Alan is a sound and light technician, and has been employed as a store manager. This looks like an on-line resume. I haven’t seen an exploit using a hijacked site in a while, which is why I decided to include this example even though the exploit pages are gone.
[Heads Up] Phishing Attacks Are Now the Top Vector for Ransomware Delivery
Phishing attacks are now the top vector for ransomware delivery, according to researchers at Digital Defense. Phishing emails can be highly tailored to specific employees in order to trick them into downloading malicious files.
“Phishing emails are easy to send and lure the unsuspecting victim in with minimal awareness of an attack,” the researchers state.
“The carefully crafted device of a social engineering scheme, the emails are customized to specific targets and appear to be from legitimate, even familiar, senders.
“Faced with unmanageable email volumes, even many once-careful users fail to scrutinize incoming mail and note small changes that would otherwise be suspicious red flags. Once the victim opens an email from their ‘bank’ or ‘internet service provider’ and confirms a few account details – or even just clicks into the malicious fake site – the payload detonates and the work of stealing and/or encrypting sensitive data begins. Once this work is completed, users are locked out and a ransom note appears.”
Full blog post with links:
https://blog.knowbe4.com/heads-up-phishing-attacks-are-now-the-top-vector-for-ransomware-delivery
IcedID Phishing: Threat attackers can own your data in just two days
What is the IcedID malware threat?
IcedID is a banking Trojan that has been actively used by cybercriminals since 2017 and shared part of its code with another widely used malware family known as Pony, whose source code leaked in 2015.
While mostly distributed via spam emails built to infect users, IcedID was also delivered in the beginning of 2023 by a phishing campaign pretending to spread a Zoom software update.
IcedID has also frequently been distributed as payload, spread by the infamous Emotet and Trickbot infrastructure, and to run ransomware attacks, as exposed by the FBI.
IcedID: Initial point of compromise
In this attack campaign, users receive and open a password protected archive containing an ISO file. Once the ISO file is clicked on, it creates a virtual disk. If the user navigates and clicks on the only visible file, a Link File Format file, the LNK file starts the infection process by launching a batch file.
This drops a Dynamic Link Library file that is executed in a temporary directory. The DLL file then downloads the IcedID payload from a remote server and loads the payload into the process. More…
For the rest of this article on Tech Republic click here.
For a full description of the Zoom phishing TPPs and IOCs read this article on Cyble.
Share
JAN






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com