 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Vanity Award Scam – 2020 Best of Business Award
Chef’s Special: Encrypted Message Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox.
Vanity Award Scam – 2020 Best of Business Award
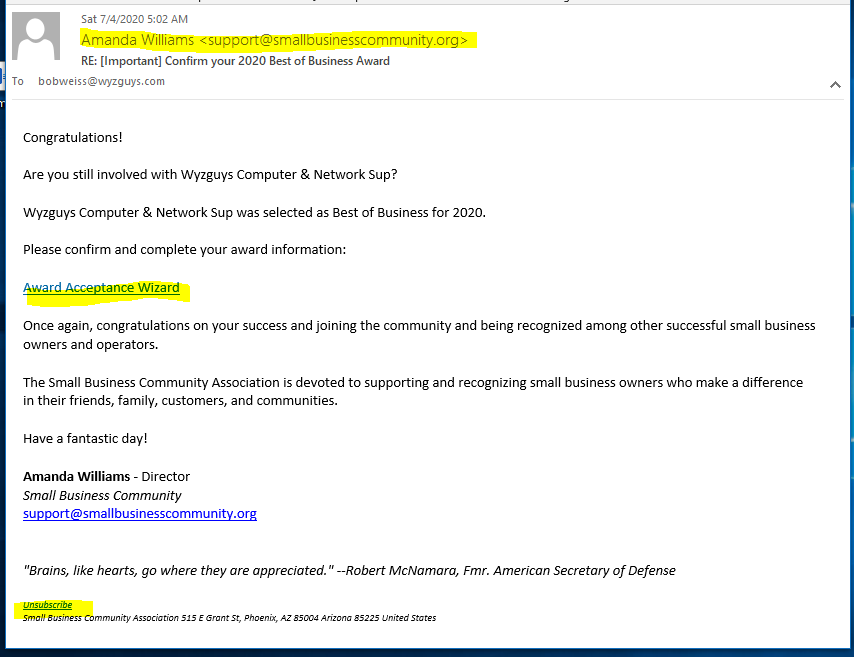
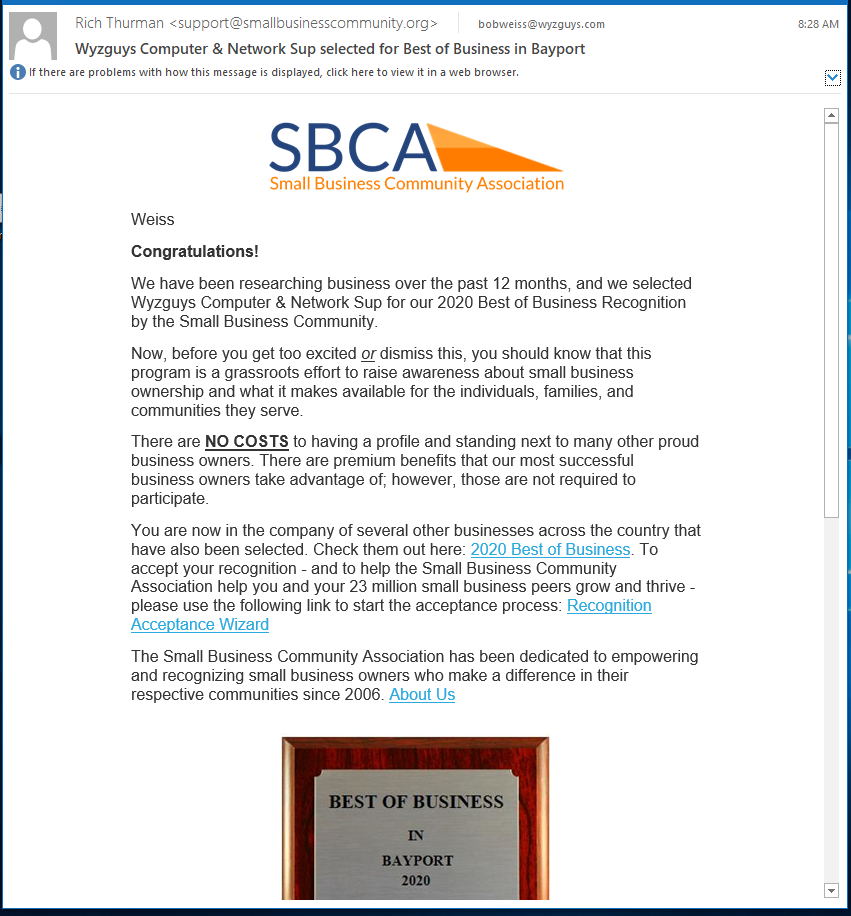
I received an email from the Small Business Community Association announcing that my company had won the 2020 Best of Business Award. These sorts of exploits are called vanity award scams. Unfortunately, there is nothing illegal about these scams, but the Better Business Bureau warns against them on their website. What is the goal?, to get you to buy an award plaque for $97.00. Here is how the scam lays out. The return address email domain, and web page address domains are all legitimate domains of a company headquartered in Phoenix AZ. Even the unsubscribe link is legitimate, as far as I can tell from my testing. VirusTotal did not flag any of these domains.
Here is a second email example I received from the same organization.
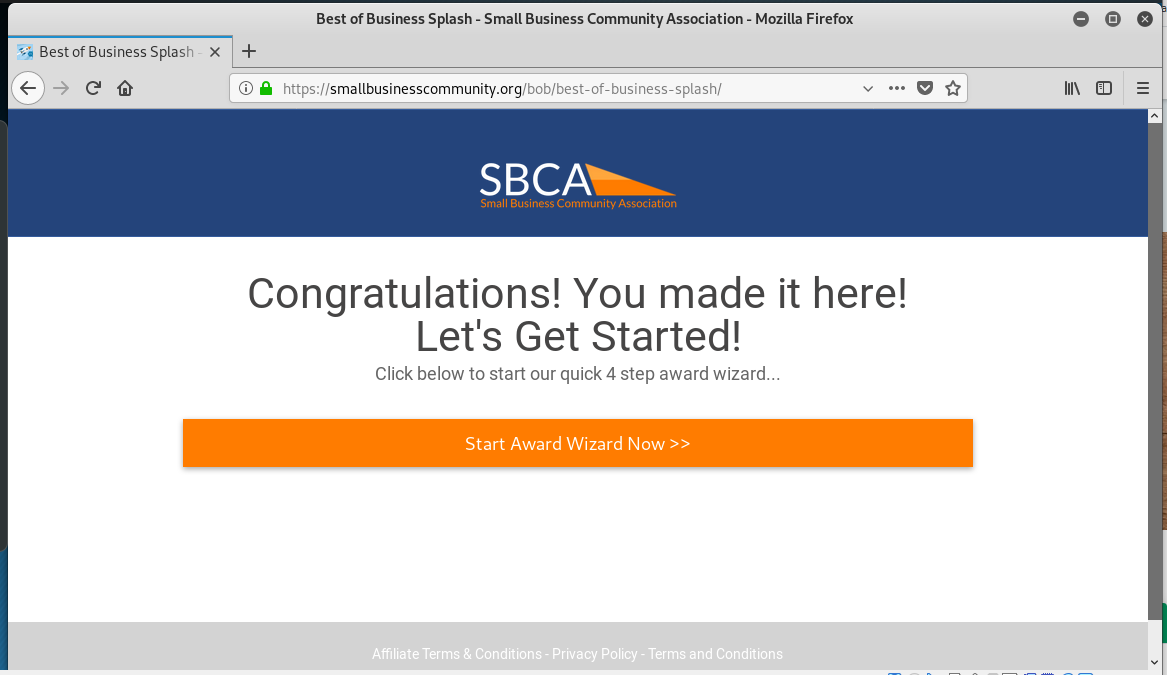
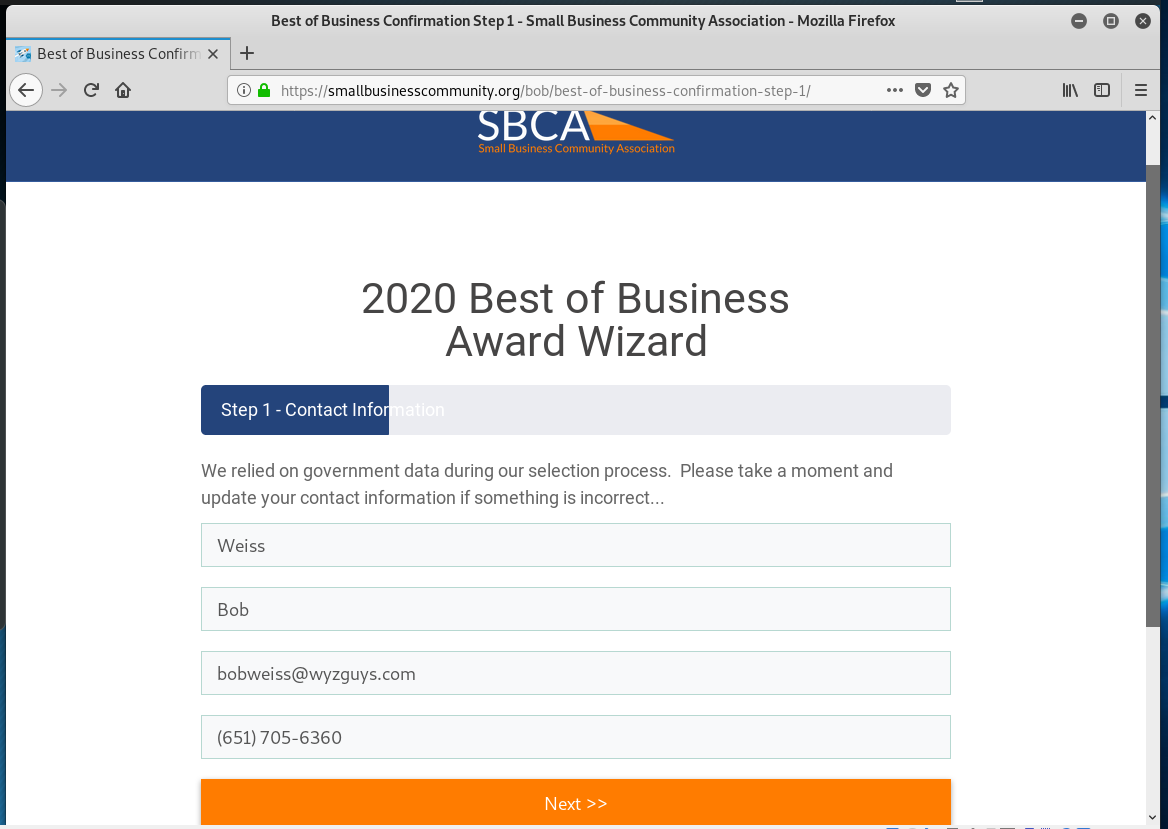
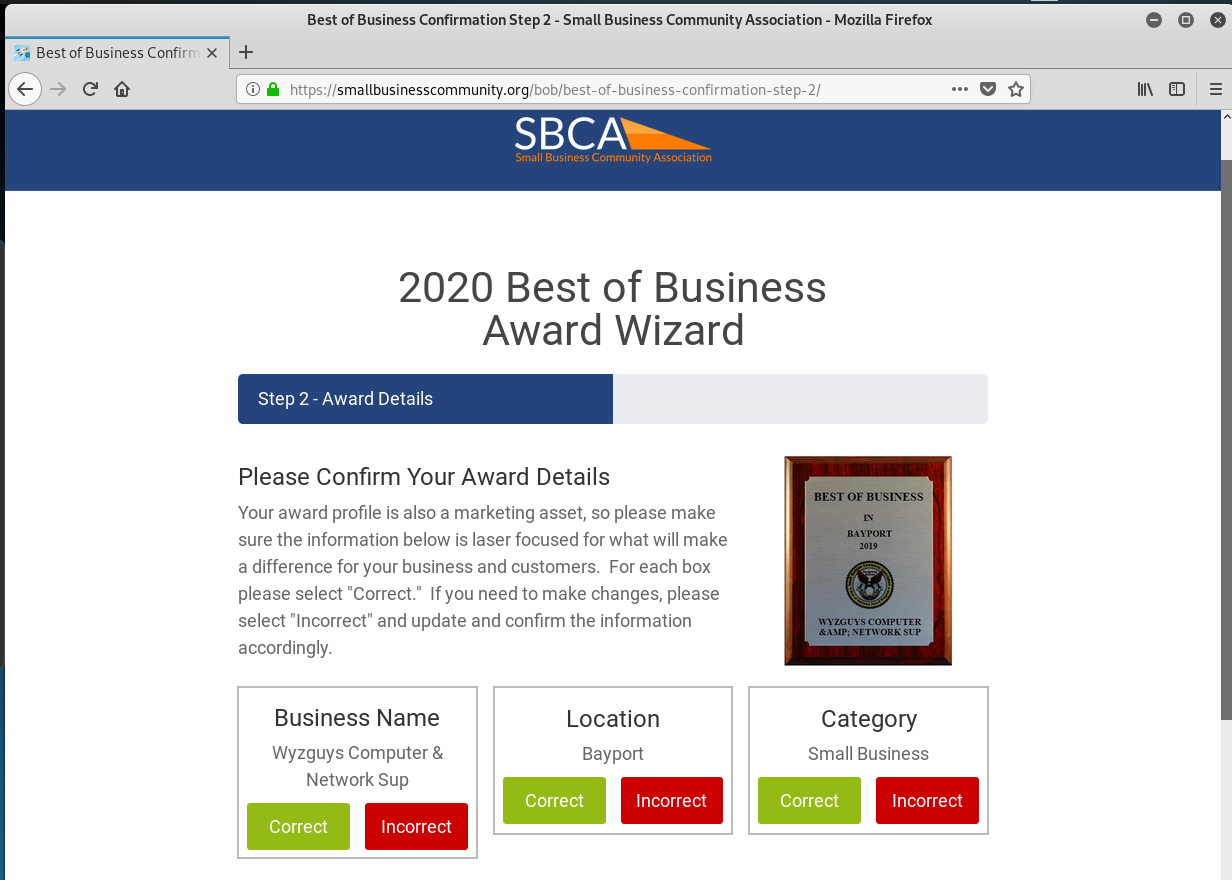
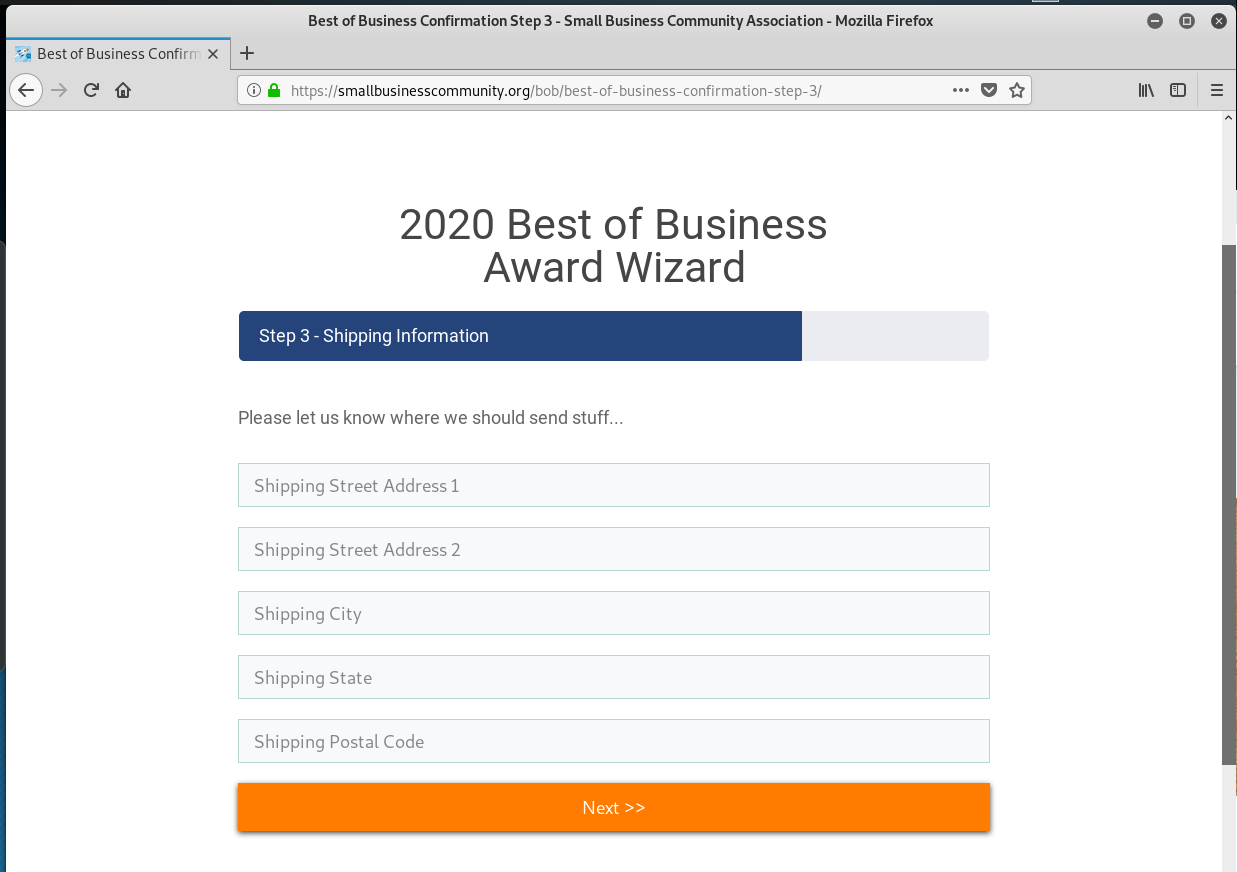
Here is the landing page for the Award Acceptance Wizard link, and the subsequent enrollment pages.
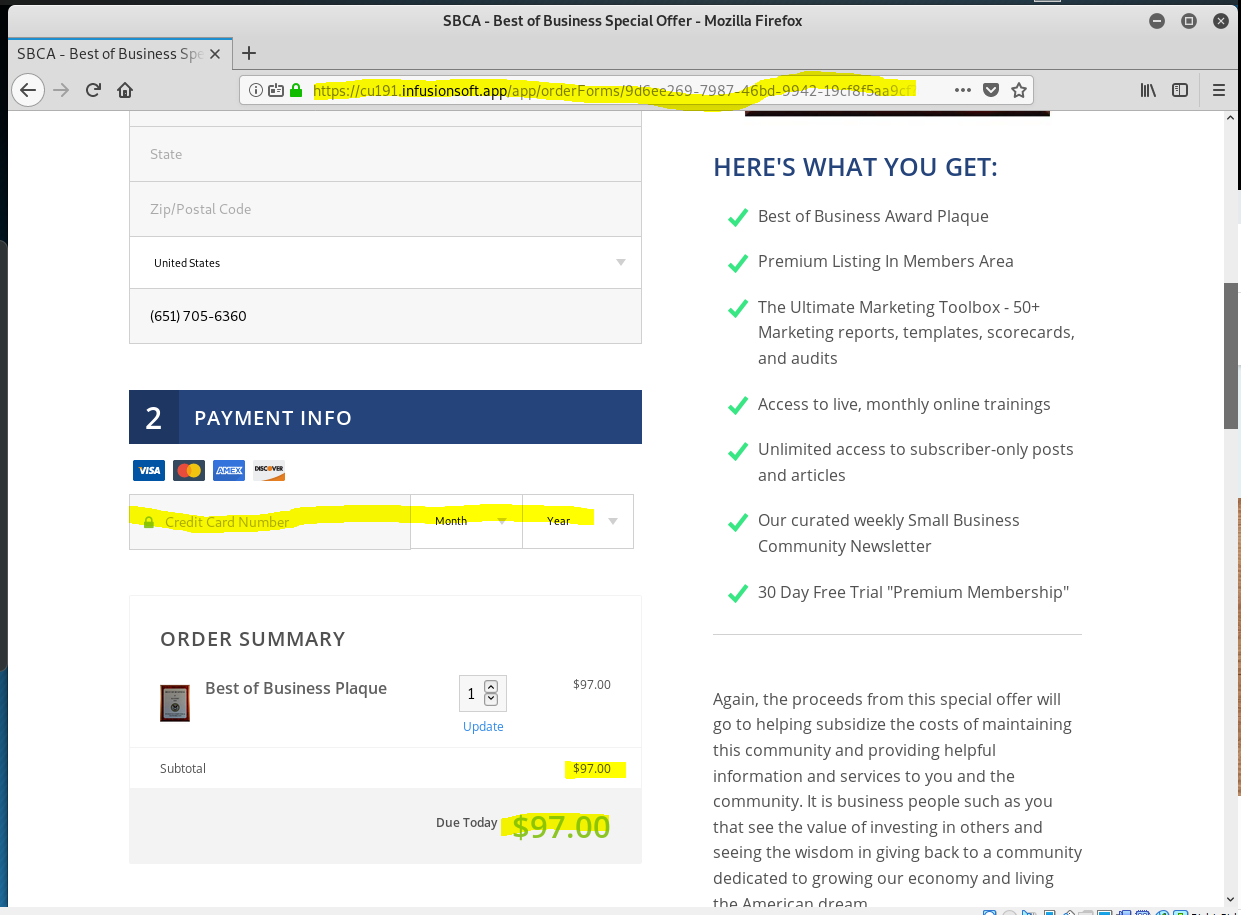
And now the hook – This call all be yours for the low price of $97. Notice that the website address changing to an e-commerce credit card payment page.
None of this is illegal in the slightest degree, and simply is a play on our desires for recognition. If you want a plaques like the one shown, you can get a better plaques for less money by designing your own, and ordering it from a local awards and trophy company.
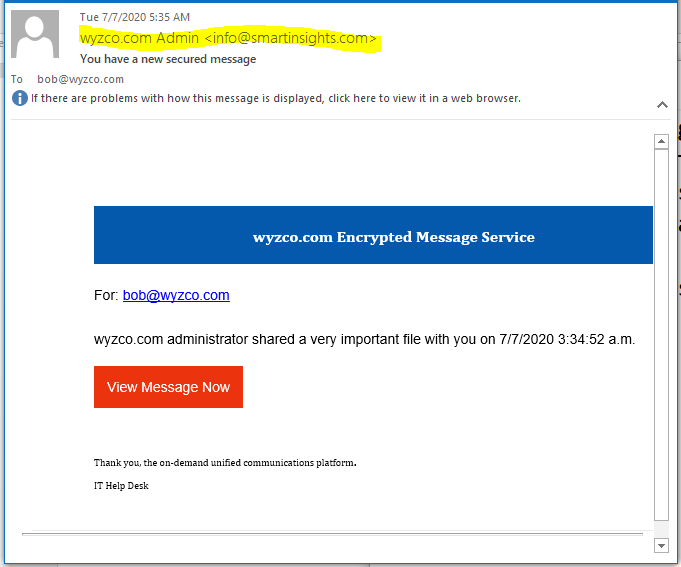
Encrypted Message Phish
This phish landed in my inbox appearing to be an encrypted message advice. There is the typical shenanigans with the sendersd email address that flags this as a phish. The View Message Now button resolved to http://j.secureft.host/#bob@wyzco.com, which was redirected to https://wyzco-com-dot-ionospg.wl.r.appspot.com. Virustotal found the first secureft address to be clean, but the redirect came back as a phishing site. Also notice the use of HTTPS in the second address. The phish:
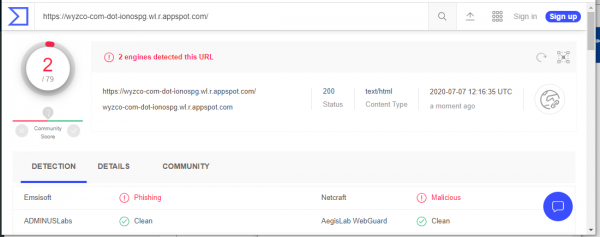
This VirusTotal report shows the redirected address is a phishing landing page, but the original link address was CLEAN.
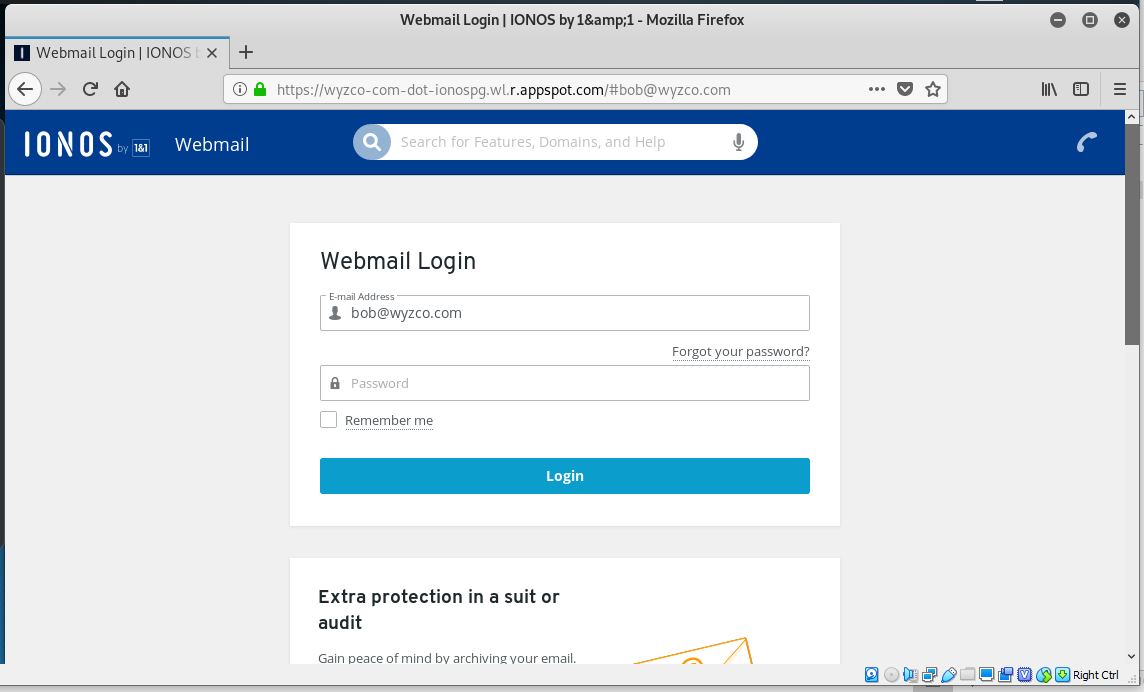
The first landing page. Notice the use of HTTPS in this exploit. Also the use of the legitimate Google domain appspot.com.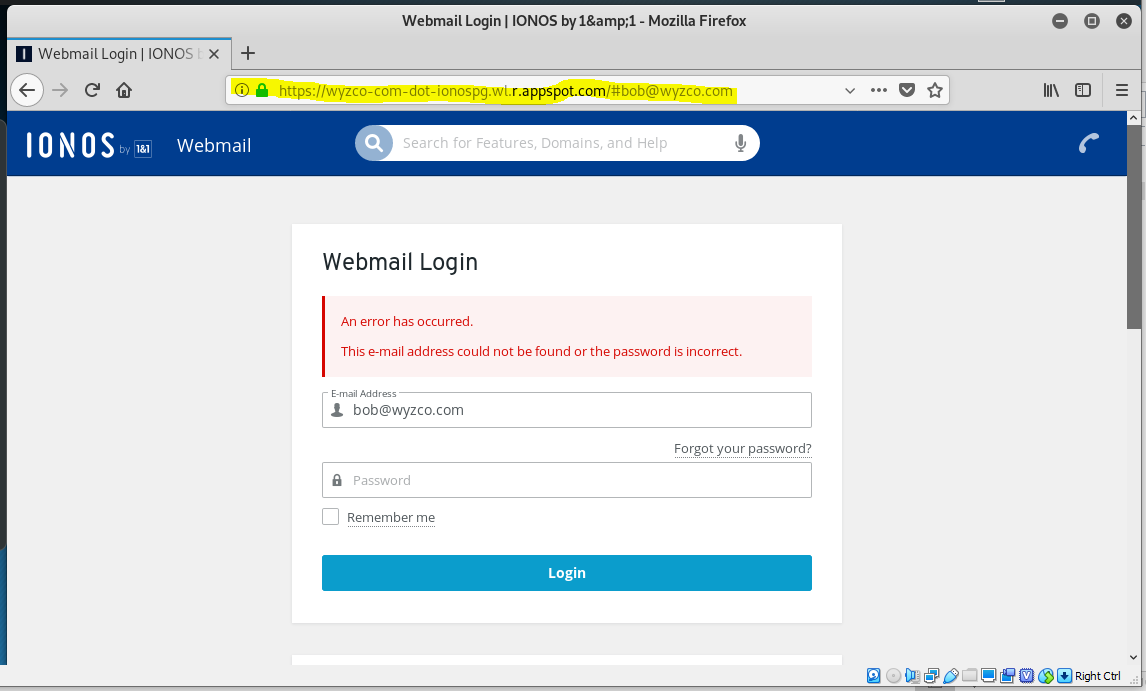
Attempting to supply the requested password spawned this error page.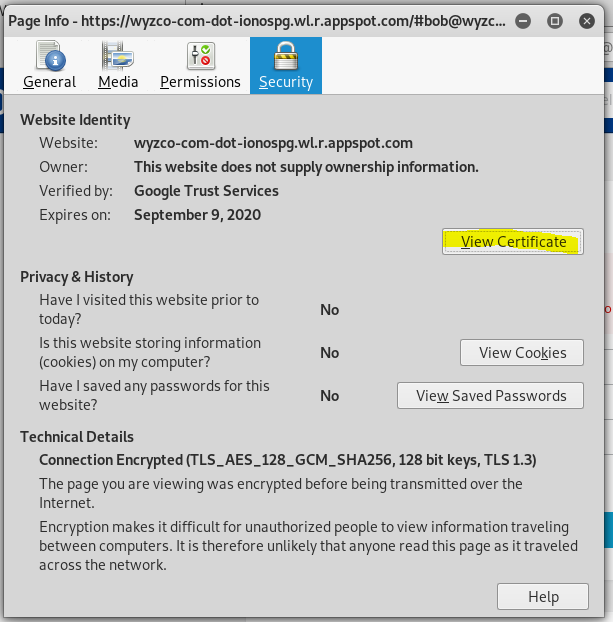
Investigating the security certificate…
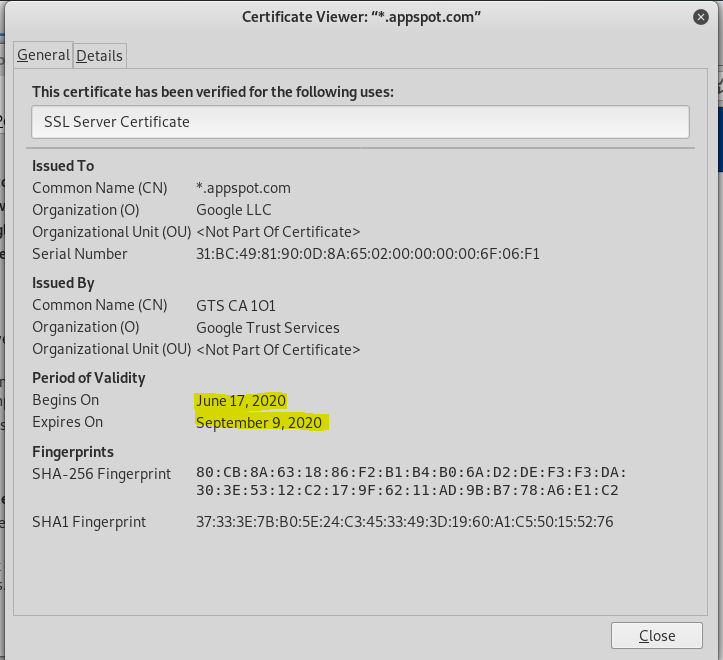
…reveals this to be a relatively recent registration, which adds to the certainty that this is a phish.
Sudden Rise in Email-Based Ransomware Attacks Detected
Phishing emails are increasingly being used to launch ransomware attacks against organizations. This includes a newly discovered family, or strain, called Avaddon. Throughout June, security researchers noticed an increase in email-based ransomware attacks. Proofpoint’s Security Brief on the uptick notes how broad this shift has been: “Daily volumes ranged from one to as many as 350,000 messages… Read more
60% of Organizations Are Hit by Cyberattacks Spread by Their Own Employees
From Knowbe4 Cyberheist News
The “unwitting participant” appears to be alive and well, based on new data from security vendor Mimecast. With employees being the source of attack surface expansion, what’s an org to do?
When you think of cyberattacks, the assumption is that it’s a simple matter of “the bad guy sends an email, the user gets fooled, the user clicks malicious content, and the badness happens.” But the State of Email Security 2020 report from Mimecast sheds some light on some of both the how and why attacks are still successful.
According to the report:
- 51% of organizations have been impacted by ransomware in the last 12 months
- 58% saw phishing attacks increase
- 60% have seen an increase in impersonation fraud
- 82% have experienced downtime from an attack
These numbers aren’t good. Way too many organizations are feeling the pain of email-based cyberattack, despite knowing the problem is only getting worse. So, why are organizations proving to be such easy targets for email-based cyberattacks?
According to the report, it’s a problem-riddled combination of issues involving your people, processes and technology. In essence, the lack of sufficient presence of all three play a role.
From the report:
- 60% of orgs have experienced their own employees being responsible for spreading a malicious email (People)
- 55% of orgs don’t provide security awareness training on a regular basis (Process)
- An average of 41% of orgs don’t have a system in place to monitor for and detect malicious content in emails (Technology)
With 60% of orgs believing they will be the victim of an email-borne attack in the coming year, organizations need to be taking steps to protect themselves with a security strategy that addresses all three issues. Putting a layered security strategy in place that detects malicious content before it ever reaches your users is imperative.
But, because 7-10% of malicious emails make it through your filters, it’s equally as important to ensure users are continually educated using security awareness training. By doing so, you will improve your organization’s security posture, and keep users from participating in the spread of malicious emails.
Share
JUL




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com