Catch of the Day: Voice Message One Phish (Again)
Chef’s Special: Voicemail Message 2 Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Voice Message Phish
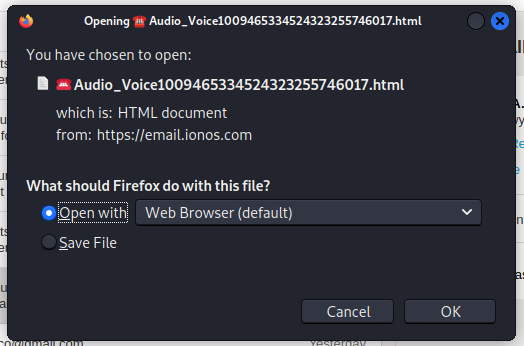
Here’s another variation on the voice message phish. My first comment is if this was a legitimate voice message, the file extension for the attachment would be WAV or MP3 or another audio format, not HTML. HTML is going to give me a web page every time.
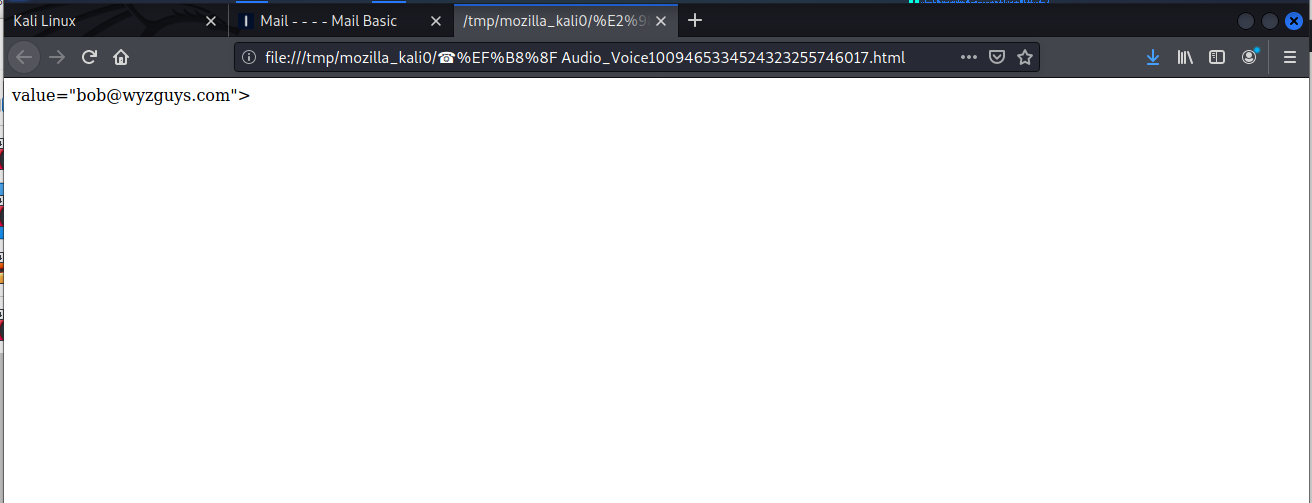
Plus this locally hosted web page is broken. I should be getting a login screen, but it never gets that far. Here’s the images.
This was the entire email, just the delivery block and the attachment. No story at all.
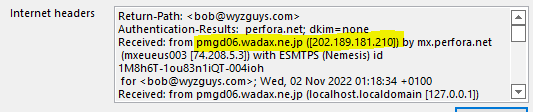
The email headers show this was sent from a mail server in Japan from the .JP country code
I opened the attachment, and got to the dead end below. One of the charms of locally hosted web pages is that the attacker doesn’t need to hijack a separate wen server, but just opens the page locally in your own web browser.
I am assuming this is a feeble first effort by a newbie cyber-crook. Better luck next time.
Voicemail Phish #2
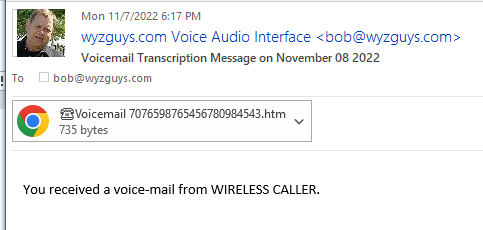
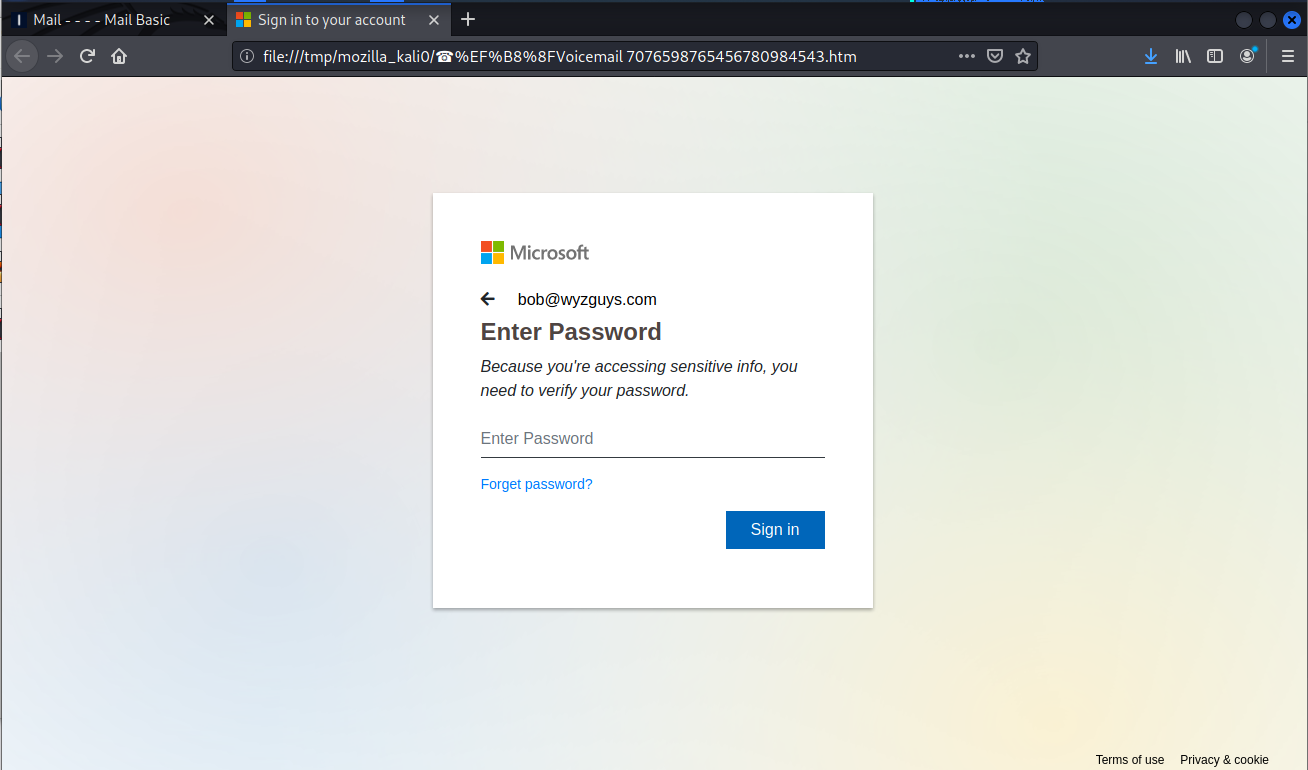
Here’s what the previous phishing landing page SHOULD HAVE looked like. Notice the message was received on November 7 at 6:17 pm, but the email message is dated for Nov 8. Evidently this cybercrook can time-travel! Impressive.
And here is a decent example of a self-hosted or locally hosted web page. This is served to your browser from a temp file on your computer’s hard drive.
This landing page is for stealing your Microsoft account credentials, grabbing your email account, and impersonating you in emails that are sent from your actual email account.
[Scam of The Week] New Phishing Email Exploits Twitter’s Plan to Charge for Blue Checkmark
Michael Kan at PCMag had the scoop: A hacker is already circulating one phishing email, warning users they’ll need to submit some personal information to keep the blue verified checkmark for free.
He wrote: “One hacker is already exploiting Twitter’s reported plan to charge users for the verified blue checkmark by using it as a lure in phishing emails.
“On Monday, journalists at TechCrunch and NBC News received phishing emails that pretended to come from Twitter, and claimed they had to submit some personal information in order to keep the blue checkmarks on their Twitter accounts.
“‘Don’t lose your free Verified Status,’ the phishing email says. Twitter itself has yet to officially announce any changes about the blue checkmark. Nevertheless, the phishing email tries to exploit the news by claiming that some verified users, particularly celebrities, will need to pay $19.99 per month after Nov. 2 to keep the status.
“The email then tries to create a sense of urgency. ‘You need to give a short confirmation so that you are not affected by this situation,’ it says. ‘To receive the verification badge for free and permanently, please confirm that you are a well-known person. If you don’t provide verification, you will pay $19.99 every month like other users to get the verification badge.’
“The email provides a button labeled ‘Provide Information.’ However, a closer look at the message reveals it was sent from a fictitious Gmail address, instead of an official Twitter domain—a clear red flag the message is a fake.”
Step your users through new-school security awareness training before they fall for timely and smart social engineering attacks like this.
Blog post with links:
https://blog.knowbe4.com/scam-of-the-week-new-phishing-email-exploits-twitters-plan-to-charge-for-blue-checkmark
[EYE OPENER] Phishing Attacks Up 61% Over 2021. A Whopping 255 Million Attacks This Year So Far…
Security Magazine wrote this week about the recent eye opening SlashNext State of Phishing report. “SlashNext analyzed billions of link-based URLs, attachments and natural language messages in email, mobile and browser channels over six months in 2022 and found more than 255 million attacks —a 61% increase in the rate of phishing attacks compared to 2021.
“The SlashNext State of Phishing Report for 2022 findings highlights that previous security strategies, including secure email gateways, firewalls, and proxy servers, are no longer stopping threats, especially as bad actors increasingly launch these attacks from trusted servers and business and personal messaging apps.” More…
LinkedIn Phishing Attack Bypassed Email Filters Because It Passed Both SPF and DMARC Auth
Researchers at Armorblox have observed a phishing campaign impersonating LinkedIn. The emails inform the user that their LinkedIn account has been suspended due to suspicious activity.
“The subject of this email evoked a sense of urgency in the victims, with a subject reading, ‘We noticed some unusual activity,’ the researchers write. “At first glance, the sender looks to be LinkedIn, the global brand used for connecting with colleagues and individuals around the world.
“However, when looking closer it is clear that the sender name reads Linkedin (an improper spelling of the brand’s name) and the email address is not associated with LinkedIn. Upon further analysis, the Armorblox Threat Research team found the domain name is fleek[.]co, created March 6th of this year––in preparation for attackers to execute targeted email attacks such as this one.”
The phishing emails and the phishing site convincingly spoofed LinkedIn’s branding.
“The email looks like a notification from LinkedIn, notifying the end user about suspicious activity on his or her account,” the researchers write. “The email included a LinkedIn logo at the top and bottom in order to instill trust in the recipient (victim) that the email communication was a legitimate business email notification from LinkedIn – instead of a targeted, socially engineered email attack.
Attack bypassed Google email security because it passed both SPF and DMARC auth
“The body of the email contains information about a sign in attempt: device used, date and time, and location; notifying the end user that this attempt has resulted in limited account access due to the potential fraudulent activity. The victim is prompted to ‘Secure my account’ to avoid the LinkedIn account from being closed.”
Armorblox notes that the phishing messages were able to bypass email security filters. “The email attack bypassed native Google email security controls because it passed both SPF and DMARC email authentication checks,” Armorblox says. “Attackers used a valid domain to send this malicious email, with the goal to bypass native email security layers and exfiltrate sensitive user credentials. Even though the sender domain received a reputation score of high risk, email security layers such as Google that rely on email authentication checks for legitimacy would not catch this targeted email attack.”
Blog post with links:
https://blog.knowbe4.com/linkedin-phishing-attack-bypassed-email-filters-because-it-passed-both-spf-and-dmarc-auth
Share
NOV






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com