 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Voicemail Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
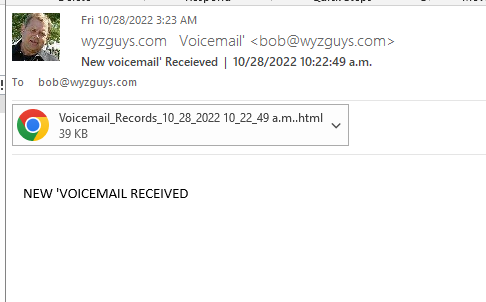
Voicemail Phish
Another credential stealer using a self-hosted (locally hosted in my computer) web page. Here we go.
The email has an HTML attachment, and appears to come from my email account.
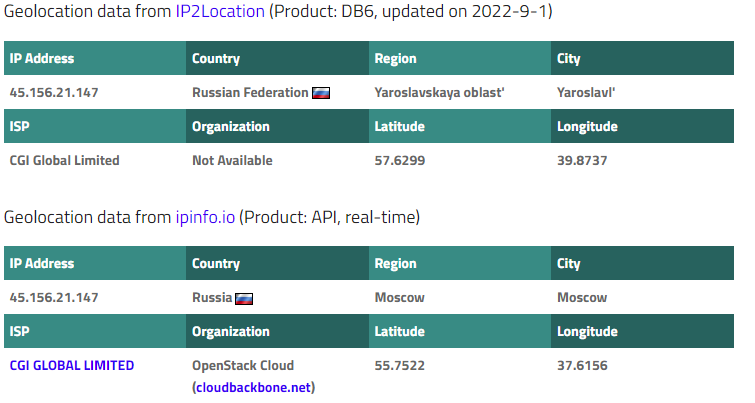
But a review of the email headers shows that the email originated in Russia. The geolocation information below proves it.
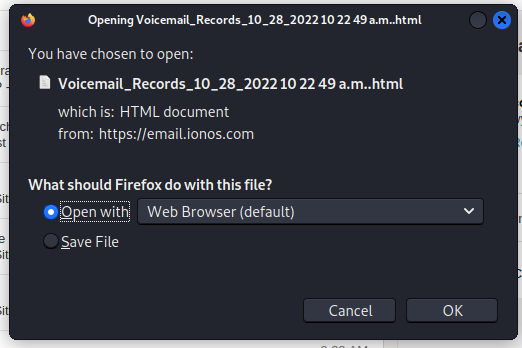
Here’s the attachment.
And here is the web page that opens when I launch the attachment. This credential stealing logon page is targeting my Microsoft account.
[INFOGRAPHIC] KnowBe4 Top-Clicked Phishing Email Subjects for Q3 2022
KnowBe4’s latest quarterly report on top-clicked phishing email subjects is here. We analyze “in the wild” attacks reported via our Phish Alert Button, top subjects globally clicked on in phishing tests, and top attack vector types.
Business-Related Phishing Attempts Still Trending
Business phishing emails have always been effective and continue to be successful because of their potential to affect a user’s workday and routine. This quarter’s results reveal that 40% of email subjects are HR related, creating a sense of urgency in users to act quickly, sometimes before thinking logically and taking the time to question the email’s legitimacy.
We also see that the top attack vector for this quarter is phishing links in the body of an email. These combined tactics can have destructive outcomes for organizations and lead to a multitude of cyberattacks such as ransomware and business email compromise.
My Take…
As phishing emails evolve and become more sophisticated, it is imperative that organizations prioritize security awareness training for all employees, now more than ever. Phishing emails that disguise themselves as internal communications are especially concerning since they are sure to grab the attention of users and typically incite action.
New-school security awareness training for employees helps combat phishing and malicious emails by educating users on what to look out for. It is the key to creating a healthy level of skepticism to better protect an organization and build a stronger security culture.
Q3 2022 Top-Clicked Phishing Emails
In Q3 2022, we examined “in-the-wild” email subject lines that show actual emails users received and reported to their IT departments as suspicious. We also reviewed tens of thousands of email subject lines and categories from simulated phishing tests, and top attack vector types in both categories.
[CONTINUED] The list with results and an infographic you can download are on our blog:
https://blog.knowbe4.com/knowbe4-top-clicked-phishing-email-subjects-for-q3-2022-infographic
[Eye Opener] Work in IT? You Get Attacked Much More Than Other Employees
We received an interesting email from Elevate Security you need to be aware of. Their recent research showed: “Social engineering attacks are growing more sophisticated every day, victimizing your workforce users and triggering security breaches. The worst part? Social engineering attacks are on the rise. And your IT engineers and developers are being attacked more often than other organizational departments.”
July 2022, IT engineers were targeted 8x more often than non-engineers
They continued: “Since April 2022, social engineering attacks on IT engineers, on average, have increased 142% from 5.79 times per month to 8.25 times per month. In fact, in July 2022, IT engineers were targeted 8x more often than non-engineers. They published an infographic that illustrates this increased risk.”
Elevate Security notes that although engineers are not inherently riskier than other workforce users, this increased frequency of attacks raises their likelihood of unintentionally triggering a security breach, regardless of their behavior.
They invited us to check out their infographic, The Rise of Social Engineering Attacks: An Overview of the State of Cybercrime to explore the state of cyber crime and social engineering attacks as they stand today, and they even mentioned Kevin Mitnick, our Chief Hacking Officer. Recommended.
Blog post with links:
https://blog.knowbe4.com/eye-opener-work-in-it-you-get-attacked-much-more-than-other-employees
Stolen Devices and Phishing
Researchers at Cyren describe a phishing attack that resulted from the theft of a stolen iPad. The iPad was stolen on a train in Switzerland, and briefly appeared on Apple’s location services in Paris a few days later. The owner assumed the iPad was lost for good, but sent a message to the iPad with her phone number just in case.
More than six months later, the owner received a text message claiming to be from Apple Support, claiming that her iPad had been found. The message included a link to a spoofed iCloud website that asked for her Apple login details. Fortunately, she didn’t fall victim to this attack.
Cyren’s researchers then tied this attack to a sophisticated phishing kit designed to spoof multiple Apple services. The attacker receives the stolen data via a custom-made Telegram bot.
“A Telegram bot is useful for this purpose since it allows for easy broadcast via the cloud – in technical terms, a http API,” the researchers write. “It’s surprisingly easy to set up a Telegram bot for this purpose, the process can be done in about one minute. After creating a bot, you receive an authentication token.
“The authentication token allows you to control the bot and send messages. The reason that the attackers are using it is because Telegram has an HTTP-based interface which allows bot owners to send messages just using a HTTP request that includes the token of the bot, a chat id, and the message. This is all completely free of charge and the bot owner doesn’t need their own separate server to handle the communication. It is also user friendly for the attacker as he conveniently receives the victim info in a telegram chat.”
After stealing the credentials and logging into the victim’s account, the phishing kit will automatically remove the linked iCloud account from the device. This allows the attacker to “reset the stolen devices and set them up as new devices so they can be sold.”
Blog post with links:
https://blog.knowbe4.com/stolen-devices-and-phishing
Share
NOV






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com