 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: DNSSEC Upgrade Phish. One exploit using many popular brands.
Chef’s Special: Slack Phish. A new phishing vector via the popular collaboration app.
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox.
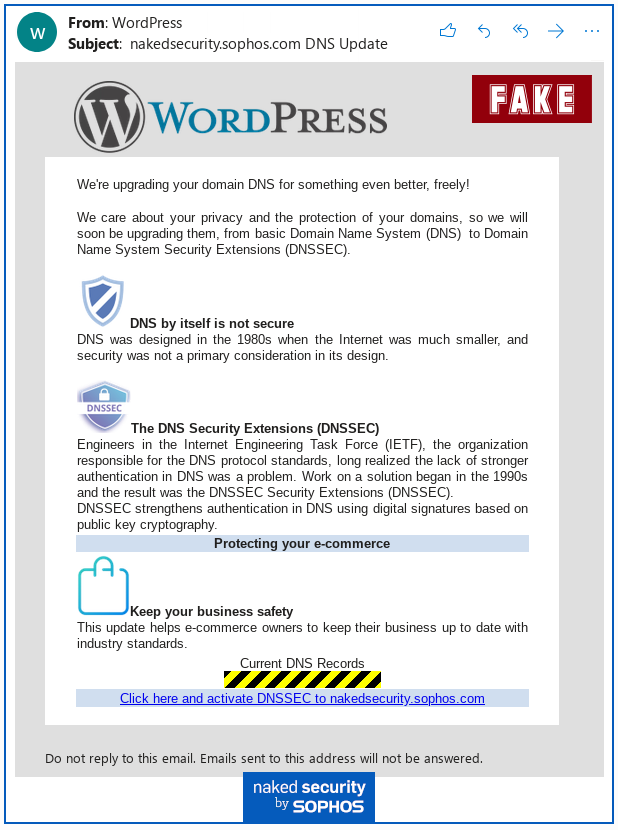
Beware “secure DNS” scam targeting website owners and bloggers
From Sophos Naked Security: I strongly recommend and urge you to click through to the Sophos site to read the full article, and see the animated exploit pages. I’ve included a couple of examples below. These are WordPress examples but “In total, the crooks had 98 different ripped-off brand images ready to go, all the way from Akamai to Zen Cart.” So these sophisticated attacks could be coming dressed in many different brands
“Over the weekend we received a message that was a bit more believable than the rest. This scam pretended to come from WordPress itself, and claimed that DNS security features would soon be added for our domain:”
“The landing page of this scam is surprisingly believable, as you see here, which is what we received when we clicked through for our “free” DNSSEC upgrade:”
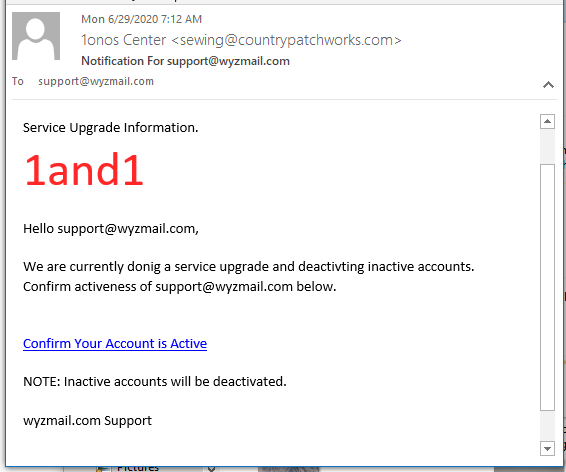
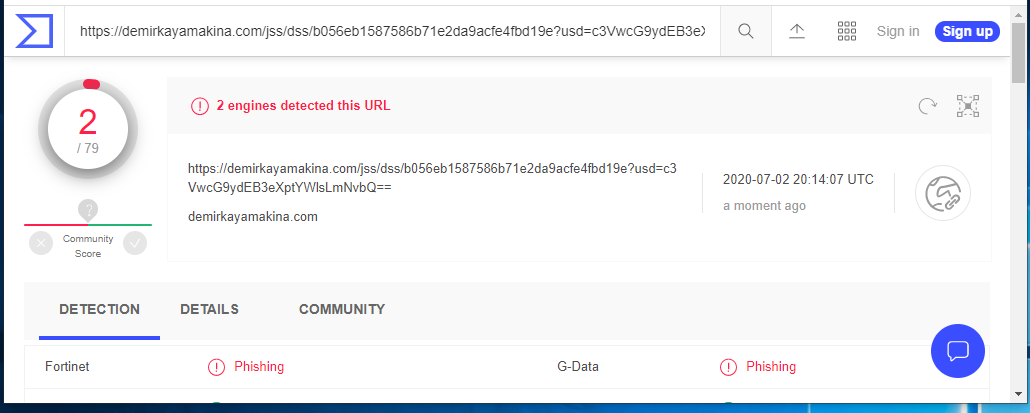
Another IONOS phish
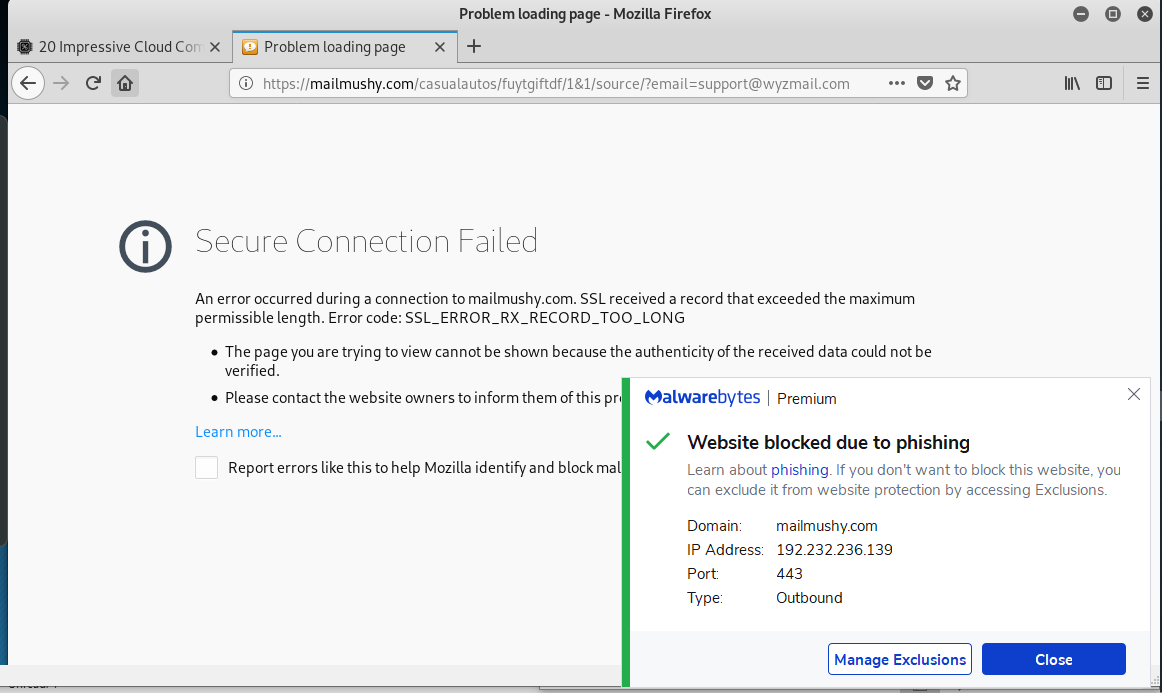
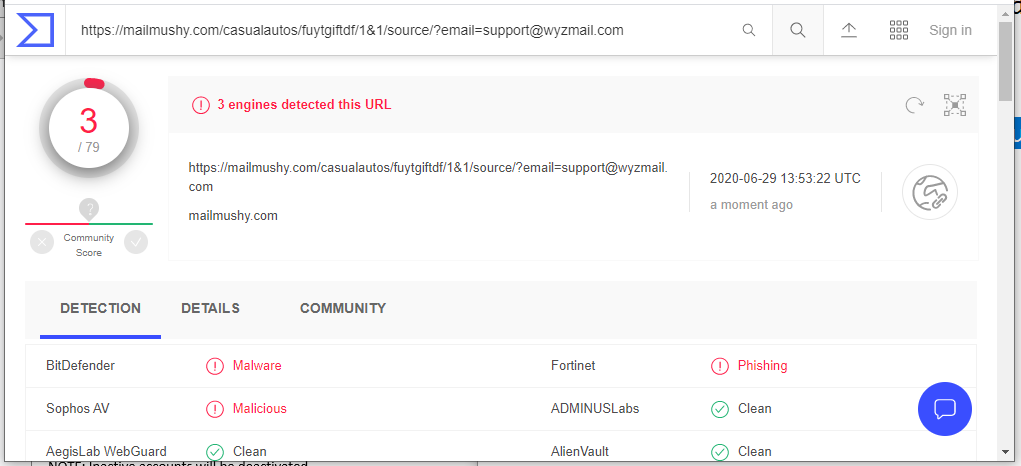
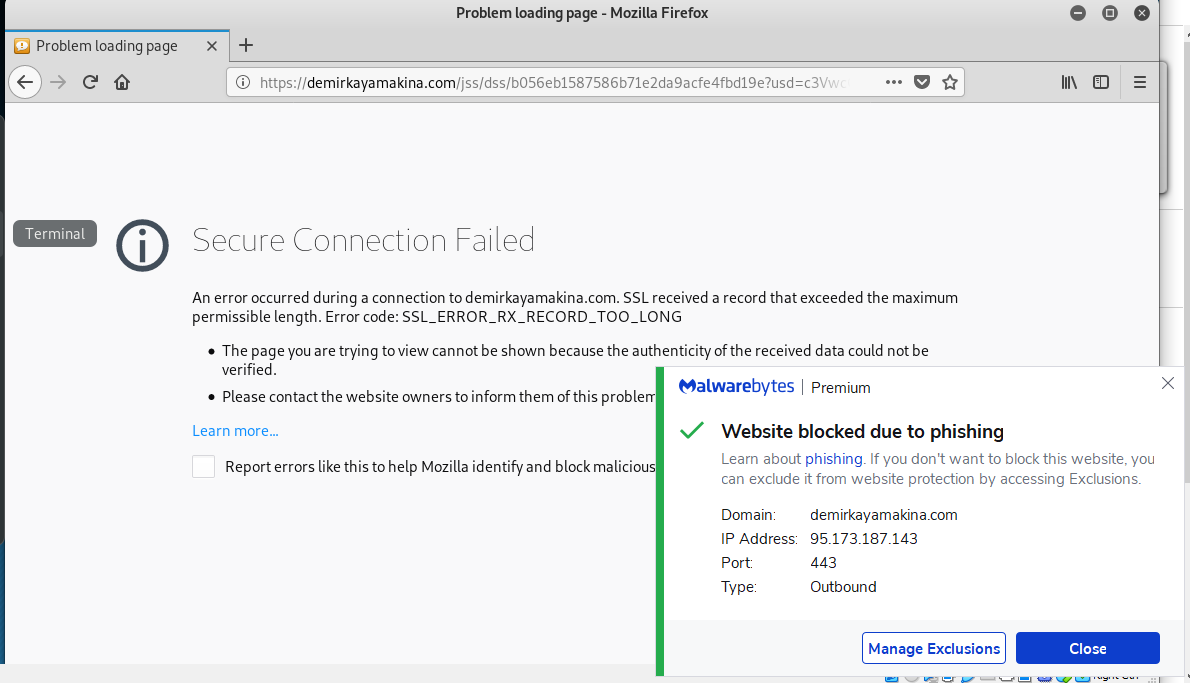
I know I said no more of these, but there are some features to point out about this poor executed phish. The sending e-mail address is 1onos Center <sewing@countrypatchworks.com>. Notice the leading number one instead of capital I. Another appearance by countrypatchworks.com. The link resolves to https://mailmushy.com/casualautos/fuytgiftdf/1&1/source/?email=support@wyzmail.com. This address was blocked by Malwarebytes and VirusTotal reported it as a malware distribution page.
Release Delayed Messages Phish
Another variation on a them for email account credential stealing. What follows are images of the phishing email, with the usual suspicious sender email address, a Virustotal report on the link address, and the error message I got when I tried to go to the landing page.
How Do Cyber-attackers or Phishers Take Over a Website?
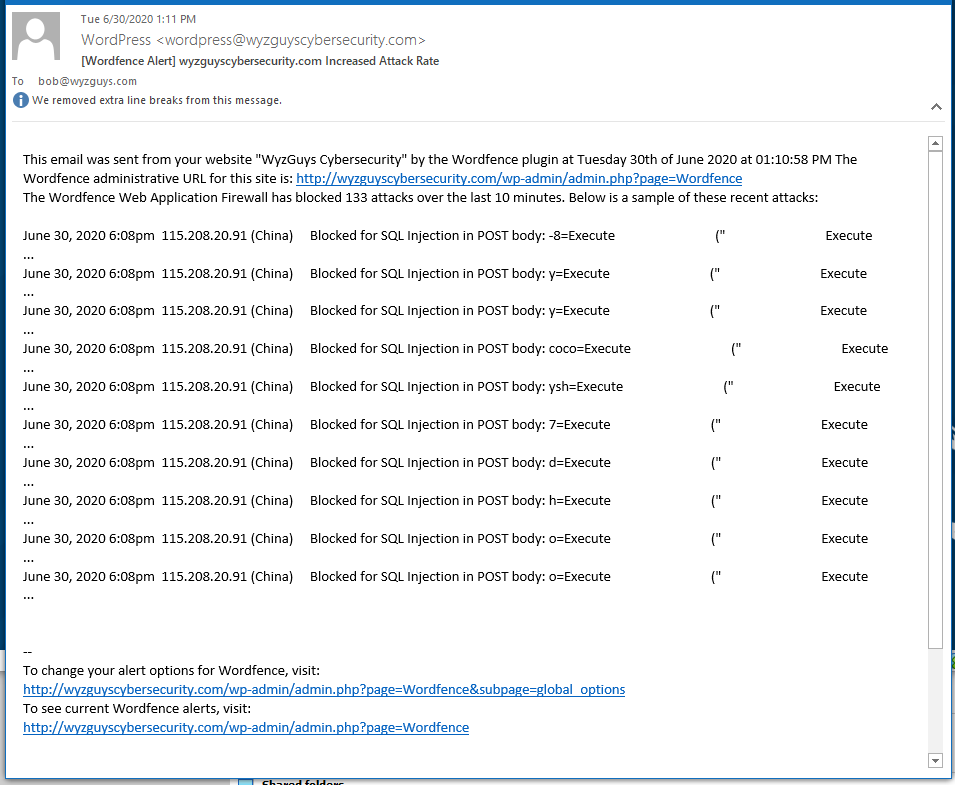
In many of the examples we dissect here on the Friday Phish Fry, often there is a website of an innocent victim that has been hijacked, and is being used to host the phising exploit landing pages. This is often accomplished using an exploit called a SQL injection. An attacker will attempt to gain access to the SQL database that is part of the website structure by entering commands into a web form. This could be a login form, or any other form that calls to your website’s data base.
The Open Web Application Security Project (OWASP) lists SQL injection as the top vulnerability in most websites or web applications. (See below)
Top 10 Web Application Security Risks
- Injection. Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
My website recently suffered an extended automated SQL injection attack. I was detected, blocked, and reported by my WordFence plugin. Here is one of the email alerts. If you are running a website, you need to be securing your website against this type of attack as well. Running WordPress? Then give a look to WordFence Security.
How Slack Phishing Works – The Latest Tricky Attack Vector
People need to be able to use their instincts in order to spot new phishing techniques, according to Ashley Graves, a Cloud Security Researcher at AT&T Alien Labs. On the CyberWire’s Research Saturday podcast, Graves described a phishing technique that abuses webhooks in Slack to fool users into granting an attacker access to their Slack data.
A webhook is a feature that allows third-party apps to send messages to a specific Slack channel via a unique URL. Anyone can send a message to the Slack channel if they know this URL, so it’s important that the URL be kept secret. If an attacker discovers a leaked webhook URL, they can craft a phishing message and send it directly into a Slack workspace to trick a user into installing a malicious app. This app can then exfiltrate data from the targeted workspace.
Graves emphasized that this attack doesn’t have any visible warning signs, since the communication comes directly from Slack through a legitimate service.
“The only indication that exists would be the person’s gut feeling that it doesn’t seem right, that this app should not be requesting this level of data,” she said.
Graves said part of the solution is improved awareness around what attackers can do with certain information. “So, I think some people legitimately don’t understand how much access an attacker can gain when credentials are leaked, and even more so when a webhook secret is leaked,” Graves explained.
“On the other side of it is understanding what you’re giving third parties access to. So, knowing to read those OAuth scopes, understanding how the application that you’re using might use that access. Like, it wouldn’t make sense – to me, at least – for a webhook to need access to my documents.
So, that’s something that they have to look over and have some sort of understanding around whether it’s some self-learning, whether it’s included in security awareness training or something like that.”
Graves noted that anyone can be fooled by social engineering, so companies need to ensure that users know when they should be cautious and ask for assistance before taking an action.
“But again, we’ve seen in similar attacks in the past that users can be easily tricked and that it’s not stupidity,” she said. “It’s not even ignorance. It’s just that this is very new technology to a lot of people, and the prompts are not always clear, and there is a lot of small text about how they work. So I think that companies need to, I suppose, make as much effort as possible to help people understand the impact of their actions.”
Attackers will never stop coming up with new ways to dupe people into granting them access. New-school security awareness training can give your employees a healthy sense of suspicion to enable them to stop social engineering attacks.
The CyberWire has the story:
https://thecyberwire.com/podcasts/research-saturday/140/transcript
Share
JUL






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com