 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Product Order Phish
Chef’s Special: IBM Phishing Report
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
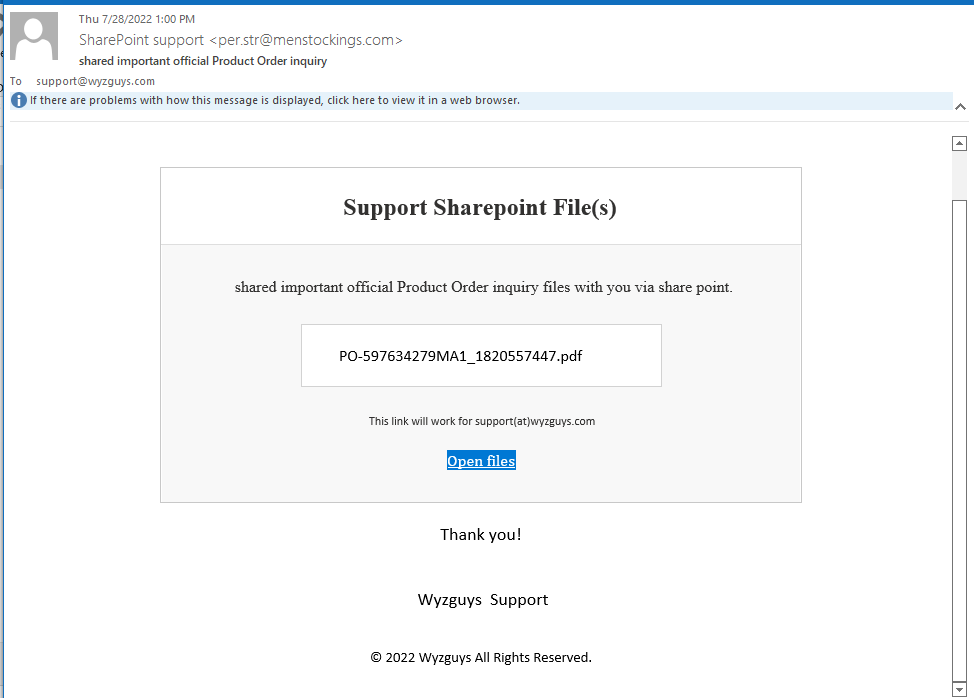
Product Order Phish
So this email has some problems from the get go. The sender email from SharePoint support <per.str@menstockings.com> looks like it might be an order for men’s stockings.
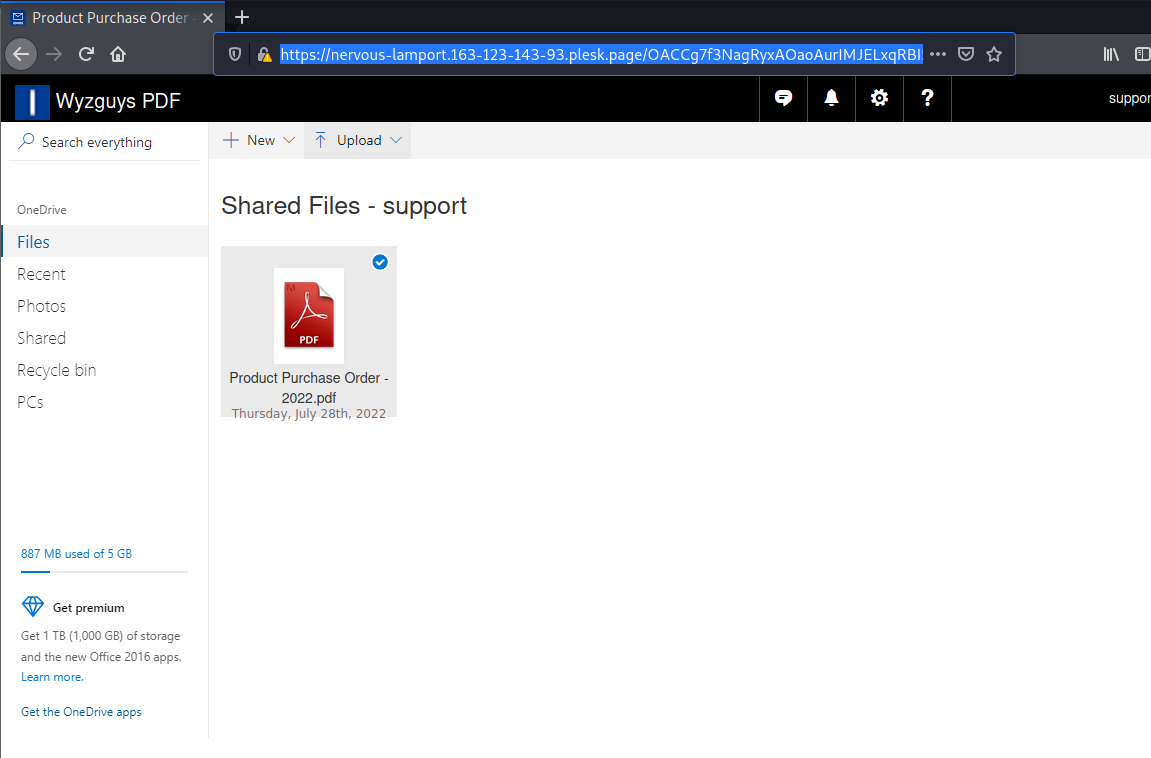
The Open Files button should take us to SharePoint files, but resolves to a Plesk page: https://distracted-wilson.163-123-143-93.plesk.page/ODkxMDIwNDU4ibmxcG8tcGFnZXgtMTc1ODE3NjA4NmlmZXRjaHhzdXBwb3J0aXNlY3VyZWR4d3l6Z3V5cy5jb20= This was redirected to a different Plesk location at: https://nervous-lamport.163-123-143-93.plesk.page/OACCg7f3NagRyxAOaoAurIMJELxqRBI5ibmxcG8tcGFnZXgtODQ2cHNiNGQ4NDZwc2I0ZDg0NnBzYjRkODQ2cHNiNGQ4NDZwc2I0ZC1kb2Mtc3VwcG9ydC1yZXgtd3l6Z3V5cy5jb20=
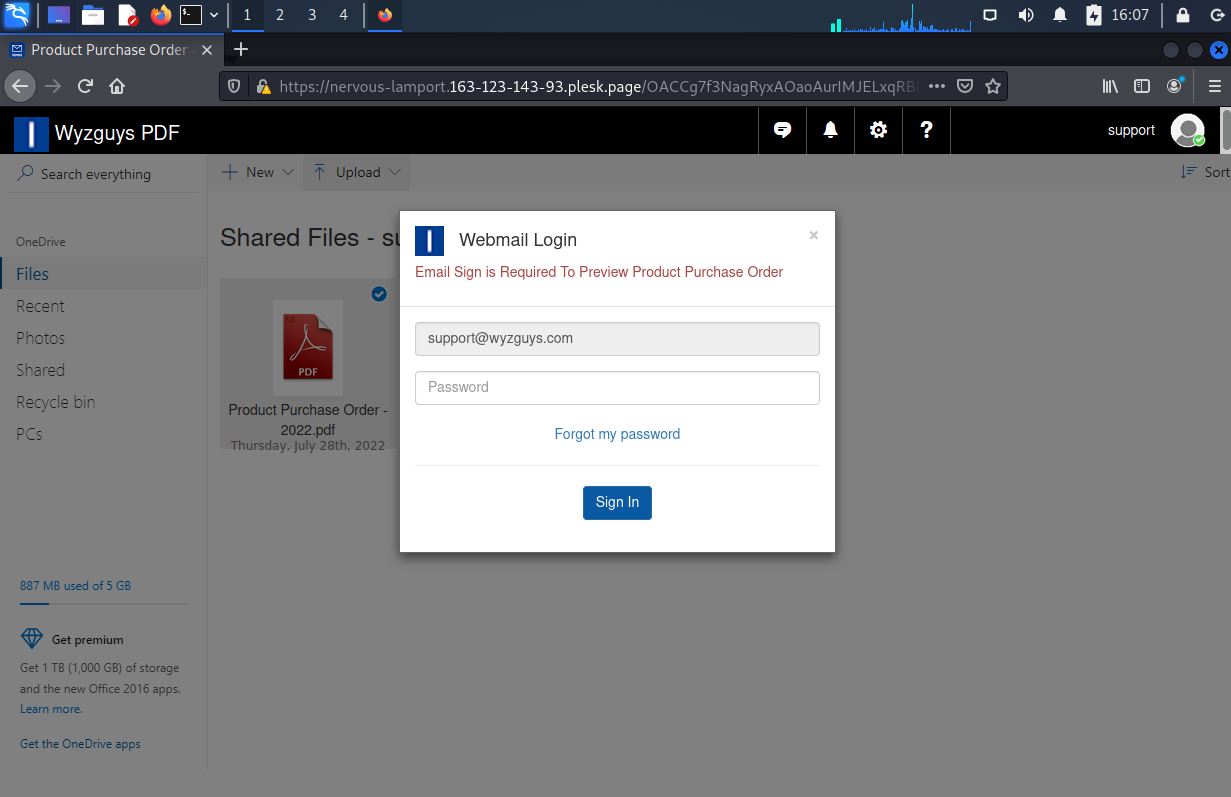
Looks like we have a PDF file, but when we click on it, a password box opens.
When I tried my fake password, I got an error message. Again, another variation of the popular user name and password credential stealing exploit.
IBM: Phishing Is the Most Common Way to Gain Access to Victim Networks and the Data Breach Costs Soar to $4.91 Million
These two reports from IBM this week about phishing are great ammo for your budget.
New research from IBM shows four reasons why phishing attacks are still effective and remain the primary attack vector in 41% of cyberattacks. Phishing has been around since the 1990’s and yet it still works today. And despite security solutions blocking most phishing emails, the ones that do get through to the Inbox remain an effective tool for threat actors.
According to IBM Security, there are four reasons why phishing continues to prevail today:
- Remote work heightens email’s use as a primary communication medium
- Cybercriminals are using email in conjunction with voice to increase message believability and scam credibility
- Cybercrime-as-a-Service is booming, giving even the least experienced cybercriminal professional access, tools and malware to accomplish their attacks
- Current security training efforts aren’t frequent enough and simply aren’t getting it done
CONTINUED at the KnowBe4 blog:
https://blog.knowbe4.com/ibm-phishing-is-the-most-common-way-to-gain-access-to-victim-networks
Fresh data on data breach costs from IBM show phishing, business email compromise and stolen credentials take the longest to identify and contain.
There are tangible repercussions of allowing your organization to succumb to a data breach that starts with phishing, social engineering, business email compromise or stolen credentials – according to IBM’s just-released 2022 Cost of a Data Breach report.
Phishing and social engineering go hand-in-hand, with business email compromise and stolen credentials being outcomes of attacks, used as launch points for further malicious actions.
According to the IBM report, the average cost of a data breach in 2022 is $4.35 million, with an average of 277 days to identify the breach and contain it. That’s actually the good news. Why you ask? Because when you factor in the initial attack vector, it gets worse. According to IBM, the following are the average data breach costs based on the initial attack vector:
- Phishing – $4.91 million
- Business Email Compromise – $4.89 million
- Stolen Credentials – $4.50 million
- Social Engineering – $4.10 million
This is the second post detailing the cost per data breach:
https://blog.knowbe4.com/phishing-based-data-breaches-take-295-days-to-contain-as-data-breaches-soar-to-4.91-million
Large-Scale AiTM Attack targeting enterprise users of Microsoft email services
Summary
ThreatLabz has discovered a new strain of a large-scale phishing campaign, which uses adversary-in-the-middle (AiTM) techniques along with several evasion tactics. Similar AiTM phishing techniques were used in another phishing campaign described by Microsoft recently here.
In June 2022, researchers at ThreatLabz observed an increase in the use of advanced phishing kits in a large-scale campaign. Through intelligence gathered from the Zscaler cloud, we discovered several newly registered domains that are used in an active credential-stealing phishing campaign.
This campaign stands out from other commonly seen phishing attacks in several ways. It uses an adversary-in-the-middle (AiTM) attack technique capable of bypassing multi-factor authentication. There are multiple evasion techniques used in various stages of the attack designed to bypass conventional email security and network security solutions.
The campaign is specifically designed to reach end users in enterprises that use Microsoft’s email services. Business email compromise (BEC) continues to be an ever-present threat to organizations and this campaign further highlights the need to protect against such attacks.
In this blog, we describe details of the tactics, techniques and procedures (TTPs) involved in the campaign.
Since the campaign is active at the time of blog publication, the list of indicators of compromise (IOCs) included at the end of the blog should not be considered an exhaustive list.
Share
AUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com