Catch of the Day: Email Update Phish
Chef’s Special: Another Geek Squad Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
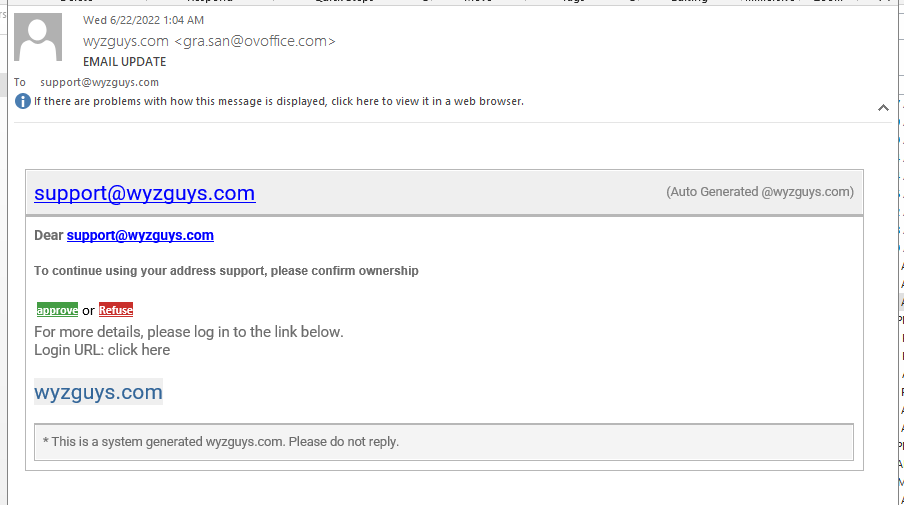
Email Update Phish
This email sender wyzguys.com <gra.san@ovoffice.com> is designed to look like it is coming from one of my own domains. The message is trying to entice me to verify my email address support@wyzguys.com. The approve or Refuse links resolve to https://donhxns.web.app/ch2mx/index.html?e=support@wyzguys.com
Here is the email:
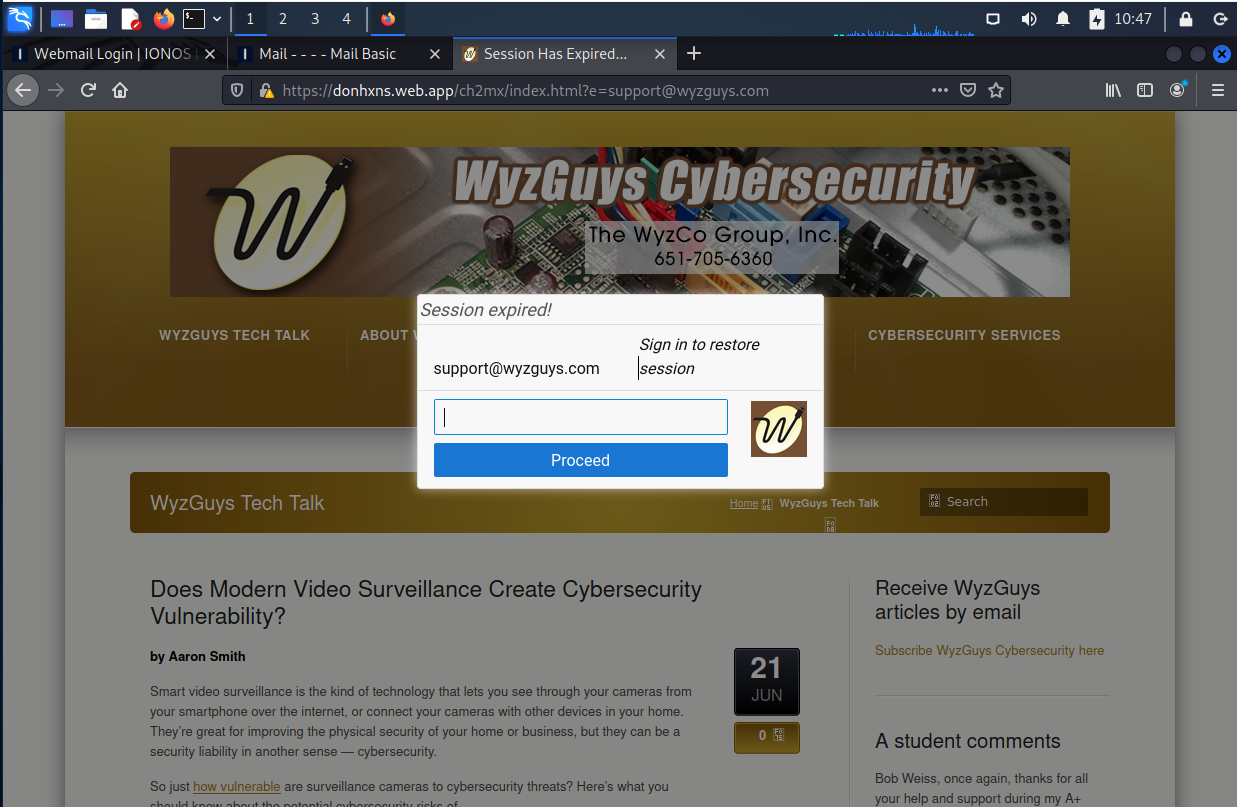
The link resolved to landing page at donhxns.web.app and what was interesting about this page is that it reflected my actual home page of my own website.
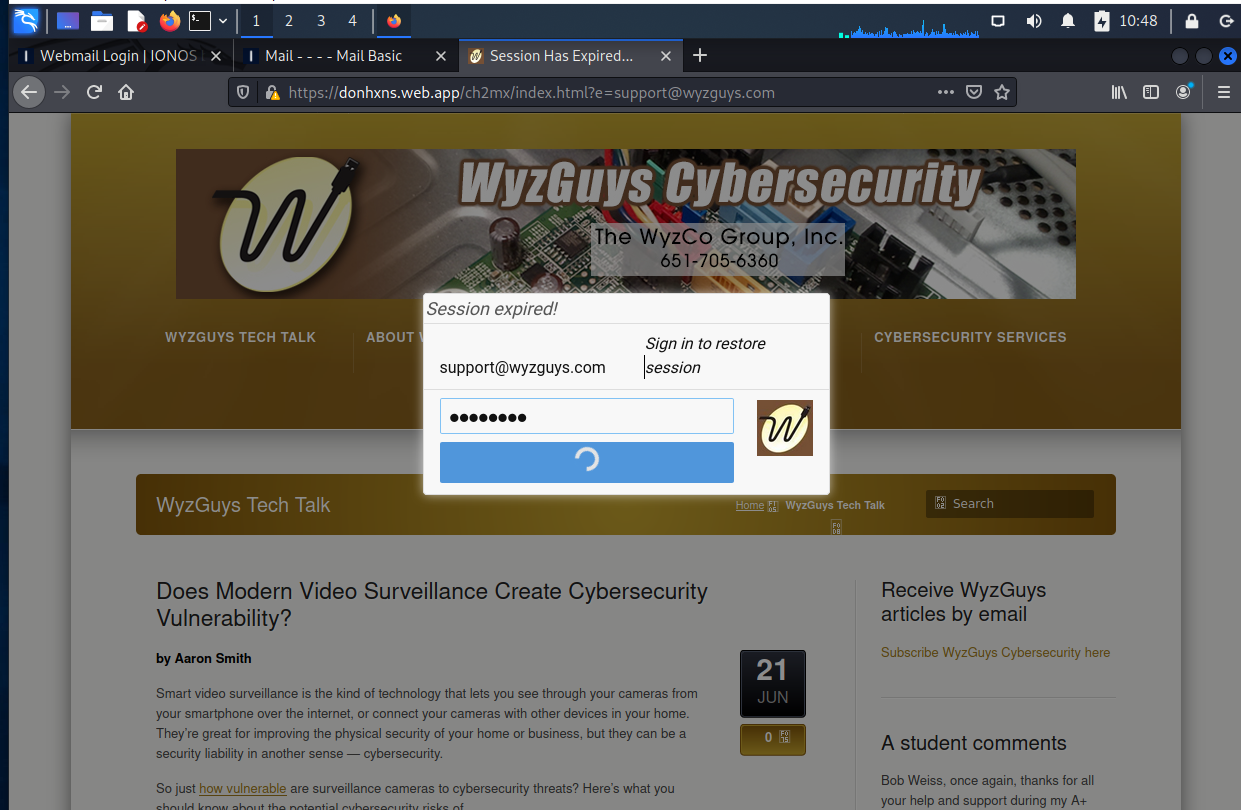
I entered the usual password and of course completed the credential harvesting mission.
The landing page then got stuck with a progress circle, and never went any further.
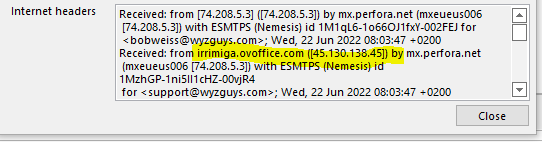
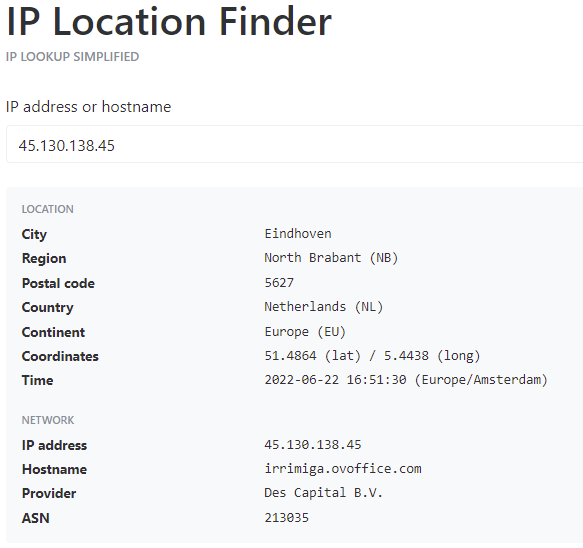
The email headers showed an IP address of the sending mail server at 45.130.138.45.
Which is a location in Eindhoven, Netherlands, for irrimiga.ovoffice.com. My efforts to find out anything useful about irrimiga.ovoffice.com or ovoffice.com did not reveal any useful information, so my assumption is that irrimiga.ovoffice.com or ovoffice.com are Dark Web services offered in some Malware as a Service marketplace.
Again, my warning is simple. Do not click on links in emails. If you actually have an account, go there directly by typing the URL or using a trusted browser bookmark that you have created in the past, and use regularly without incident.
Another Geek Squad Phish
I got one of these last week but if you missed it, here’s another version. Tip offs on this phish are the Gmail email address, (I’m sure the Geek Squad uses geeksquad.com or bestbuy.com email addresses), and the Geek S Consumer Handling Dept. This is not written the way a Geek Quad marketing employee would write this notice.. Also – no links, but there’s that toll free number.
Do not call these guys, because you will just be conned into sharing your credit card number so they can send a full refund.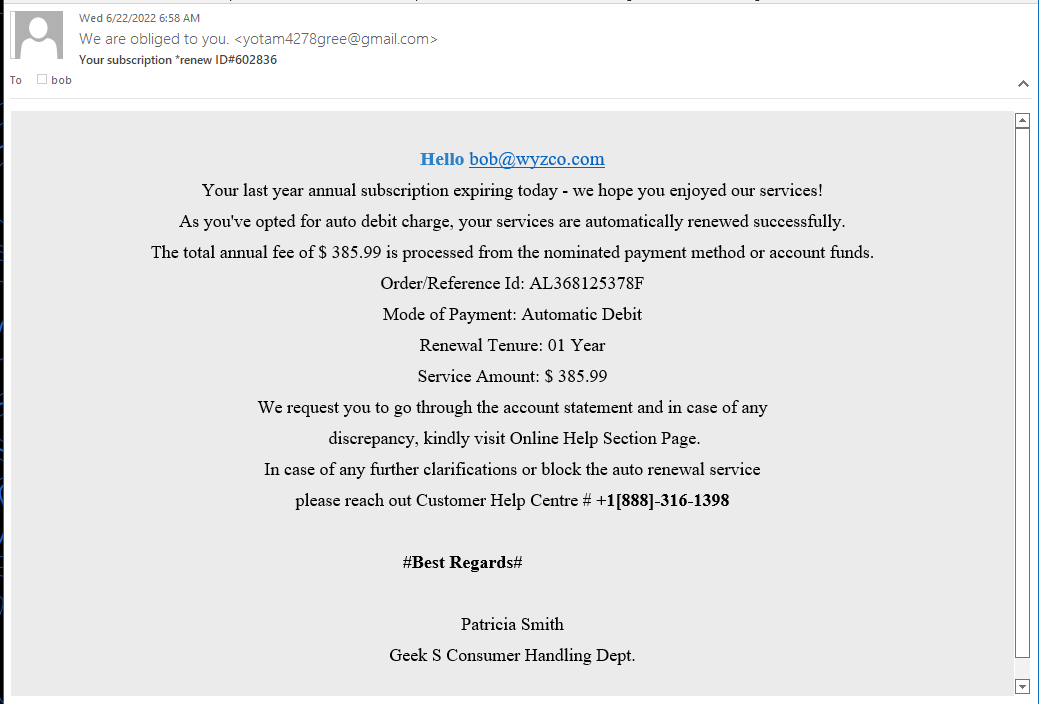
Share
JUL





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com