 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Amazon Warning
Chef’s Special: Domain Name Offer Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are send by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
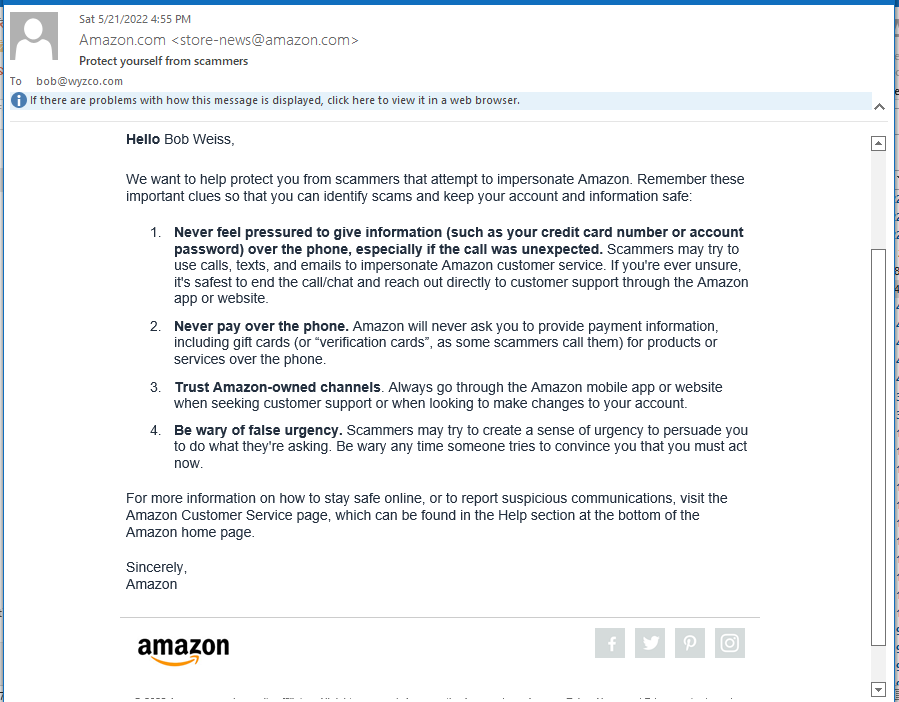
A Warning from Amazon
This arrived over the weekend. Good advice, which is why I am posting it
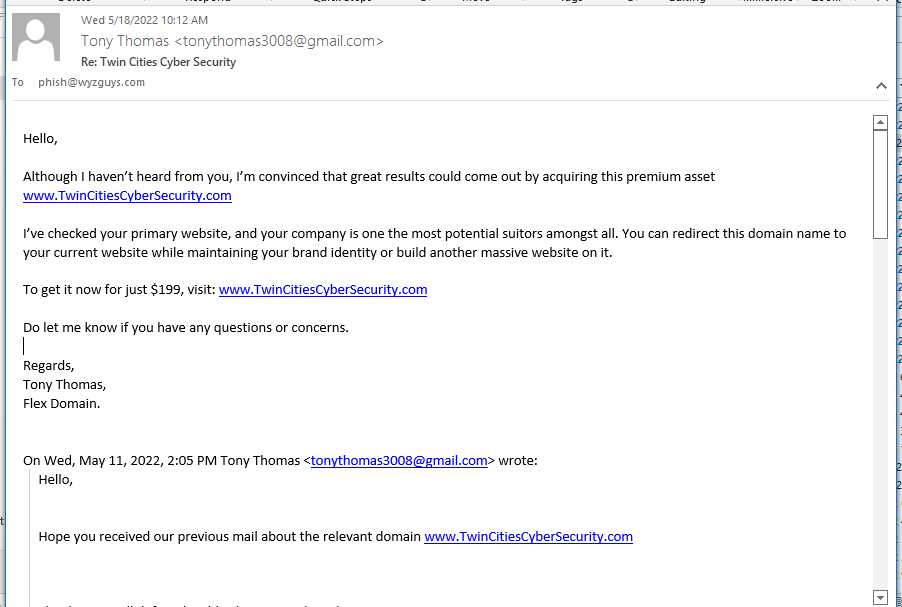
Domain Name Offer Phish
Pretty sure this is not a Phish, just a solicitation for an overpriced domain name. To be fair, if I was still working as a cybersecurity consultant, I could be tempted. I “own” (if you can own a domain name) or control an easy dozen domains. TwinCitiesCyberSecurity.com would be great for me. I am not about to put $200 into this domain name.
As you can see, this guy has presented this domain to me on at least two other occasions, once in an open ended sort of way that did not mention a price, the the second time, he offered it to me to $299. Then $250. Today it is $199. If we ever get to $49, I might give it a go.
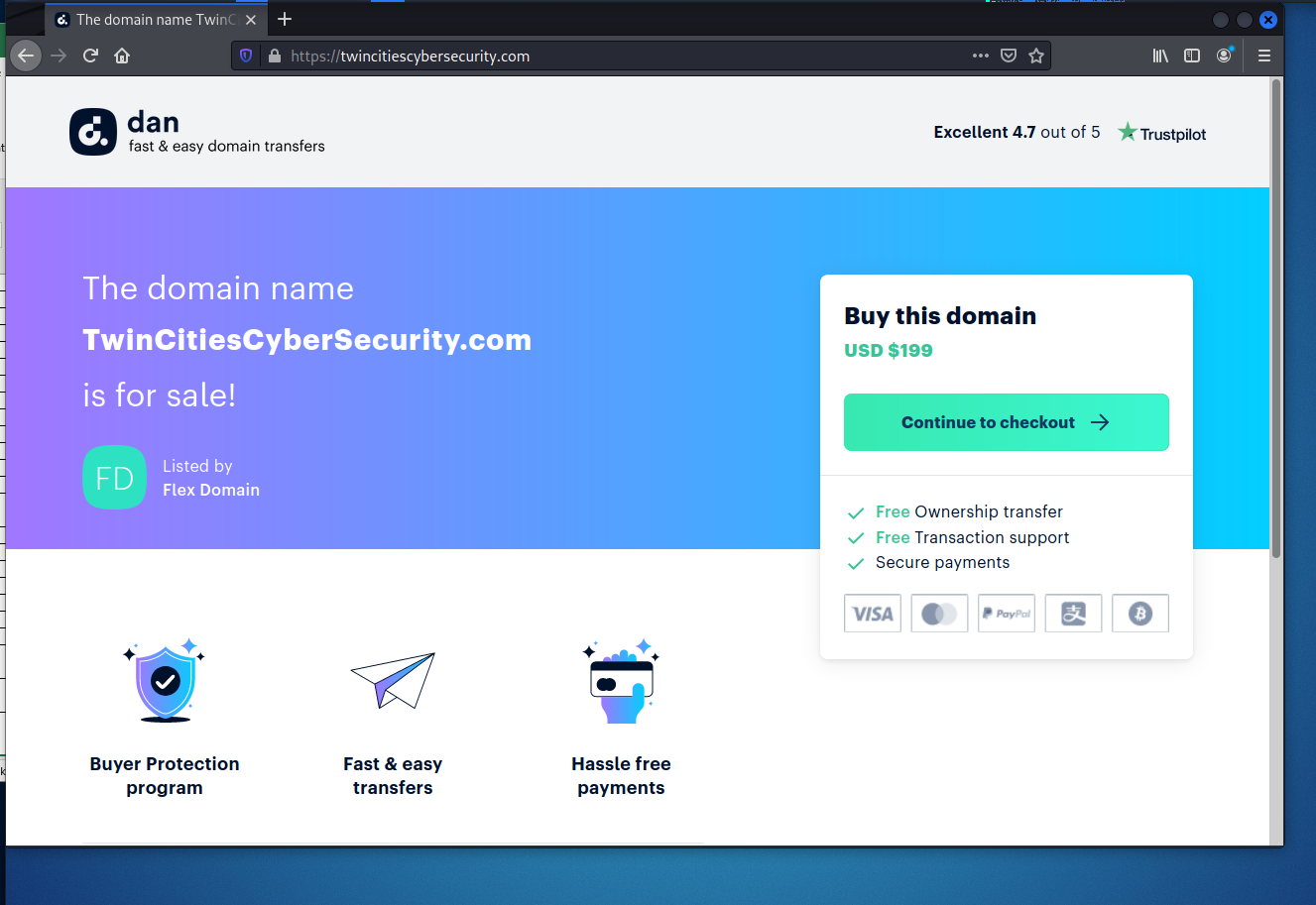
Is this a scam? It doesn’t look like it, but here are the salient concerns. If I buy a domain name, I would want to transfer it immediately to my own registrar, IONOS. Easier to manage all my domains in a single location, and the annual renewal fee is only $15.00. But I could just end up stuck with whoever this registrar is paying $199 or more every year for this domain.
Here’s the email and the landing page,
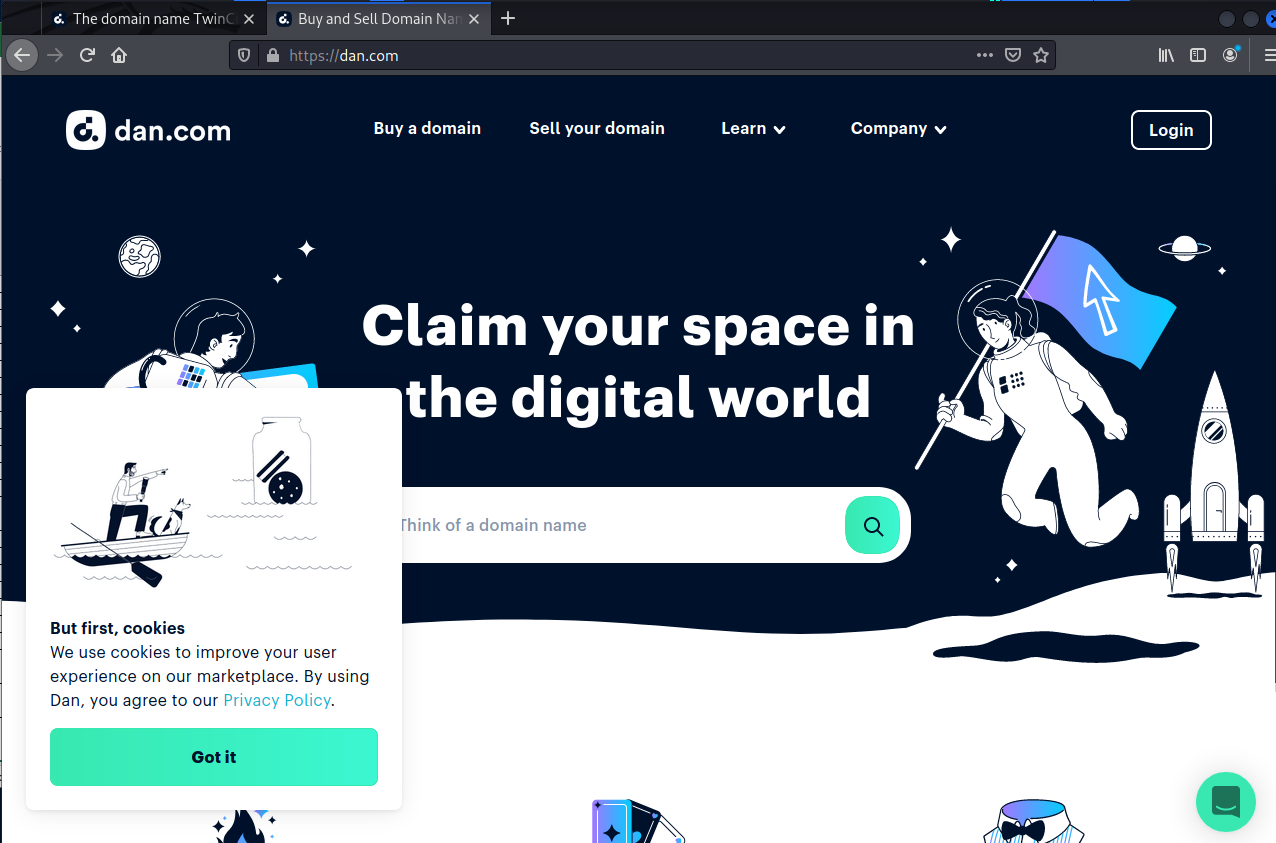
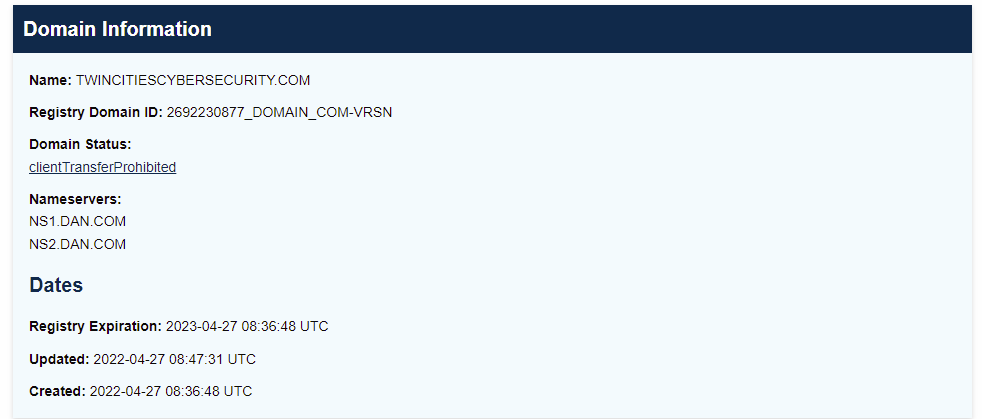
ICANN WHOIS shows this to be registered to a company dan.com. Here is their home page, and they look like a domain registrar or reseller.
This was just registered on April 27, 2022, just before the solicitations began. Hopefully this guy is presenting this domain to a few other cybersecurity companies in the Twin Cities.
Return of the Nigerian Princess Phish
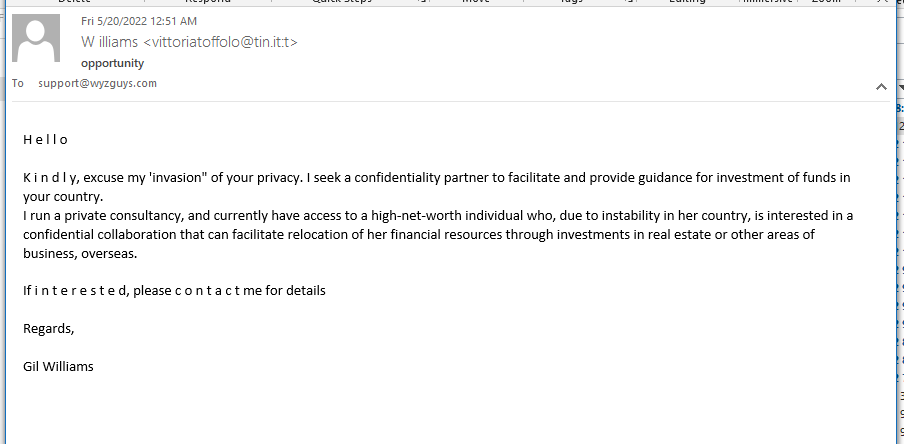
It is unfair of me to attribute this exploit to Nigeria, when it really originated in Italy. A “high net worth” female want’s to invest in my business to reallocate her funds due to “instability”. Maybe she is a Russian oligarch on the sanctions list. Who knows. I am sharing this simply to show that sometimes the old ways are the best ways.
The Phish:
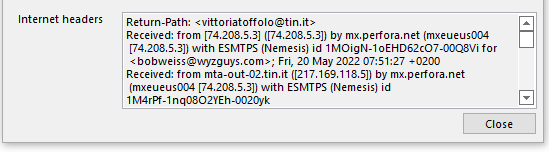
The email headers show the point of origin to be Milan, Italy from mta-out-02.tin.it (217.169.118.5)
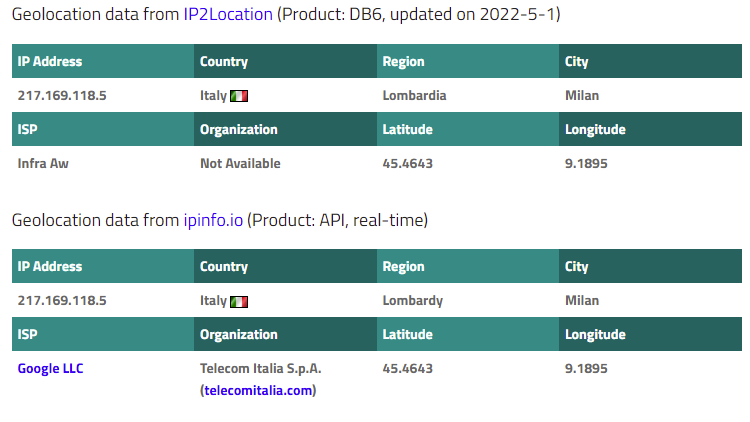
Using an IP location website we get this information
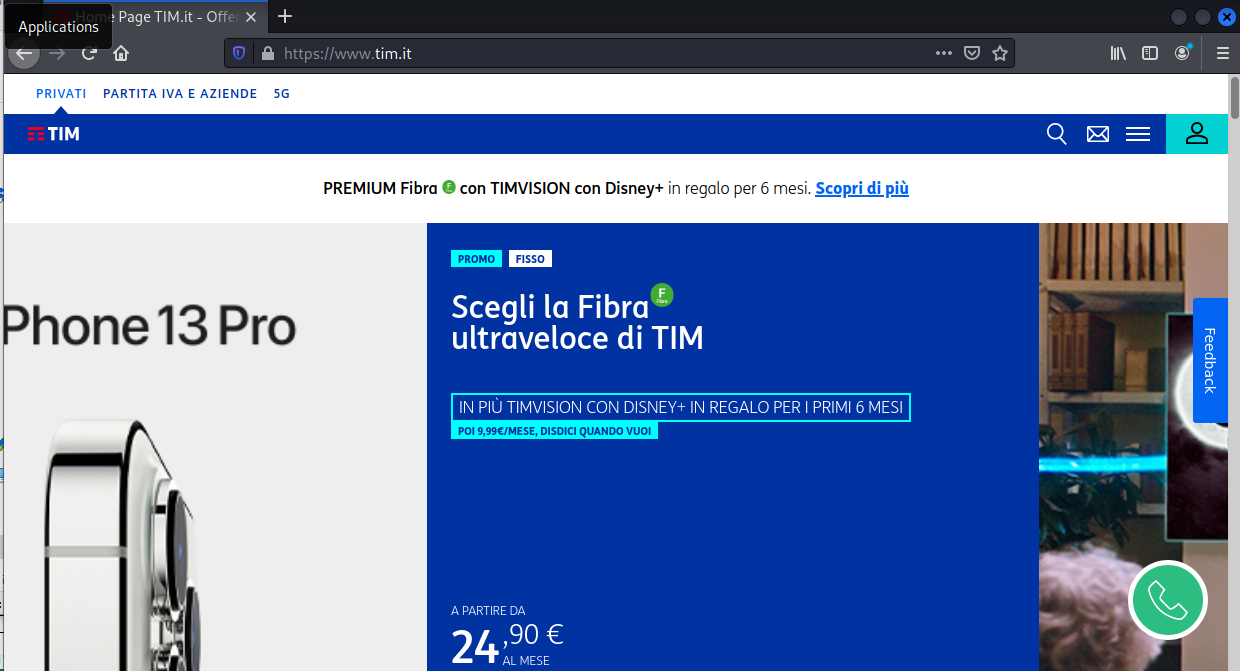
The domain tin.it redirected me to https://www.tim.it/. This just seems to exist to thwart investigators like me.
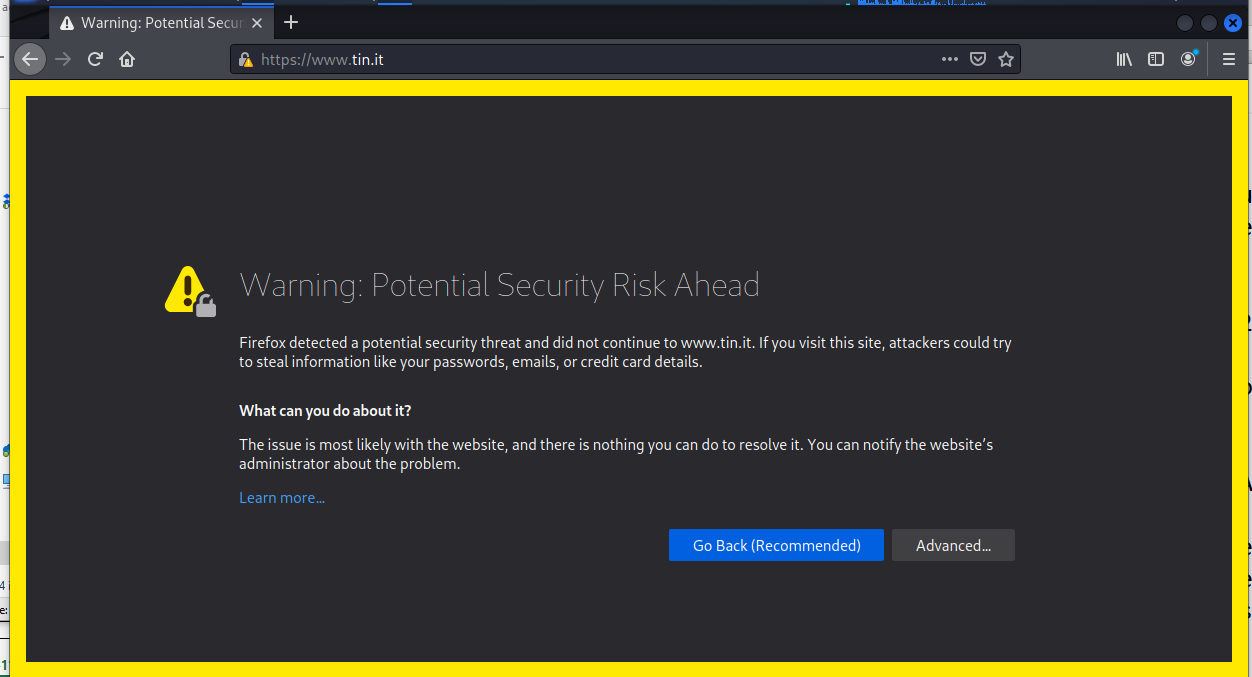
When I retyped the address in the address bar, we got to the real website and this warning.
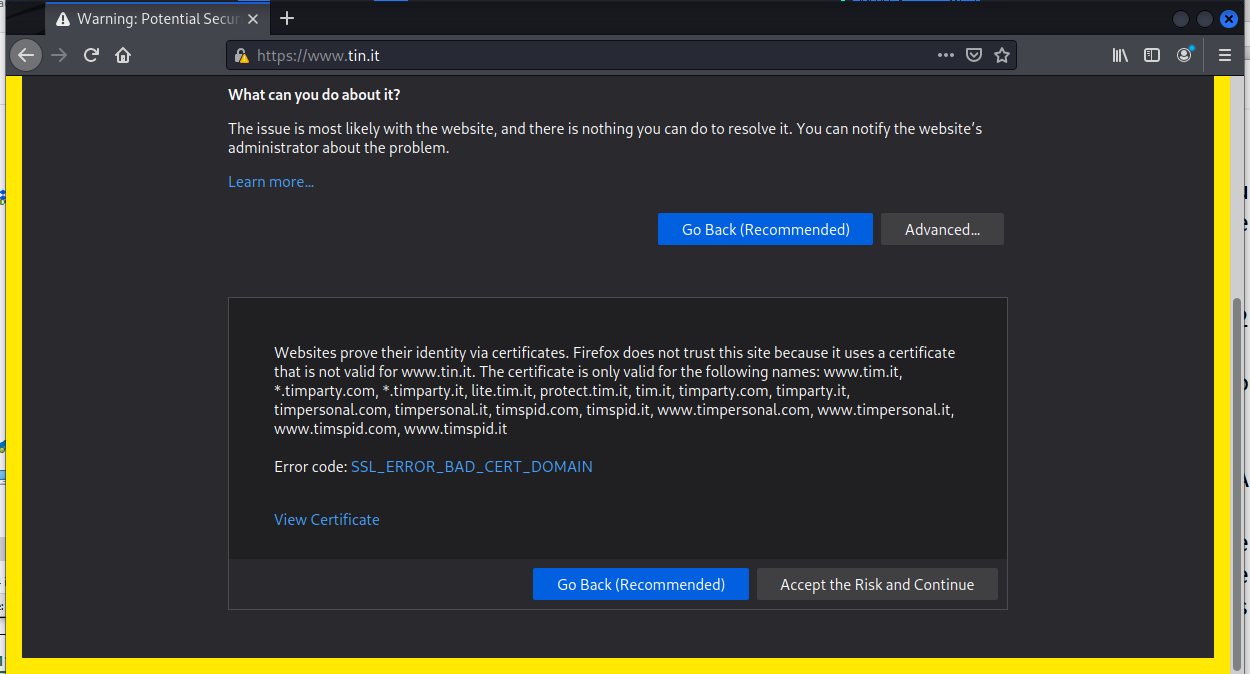
What is the fun in going back? So I fired up Kali and completed the tour.
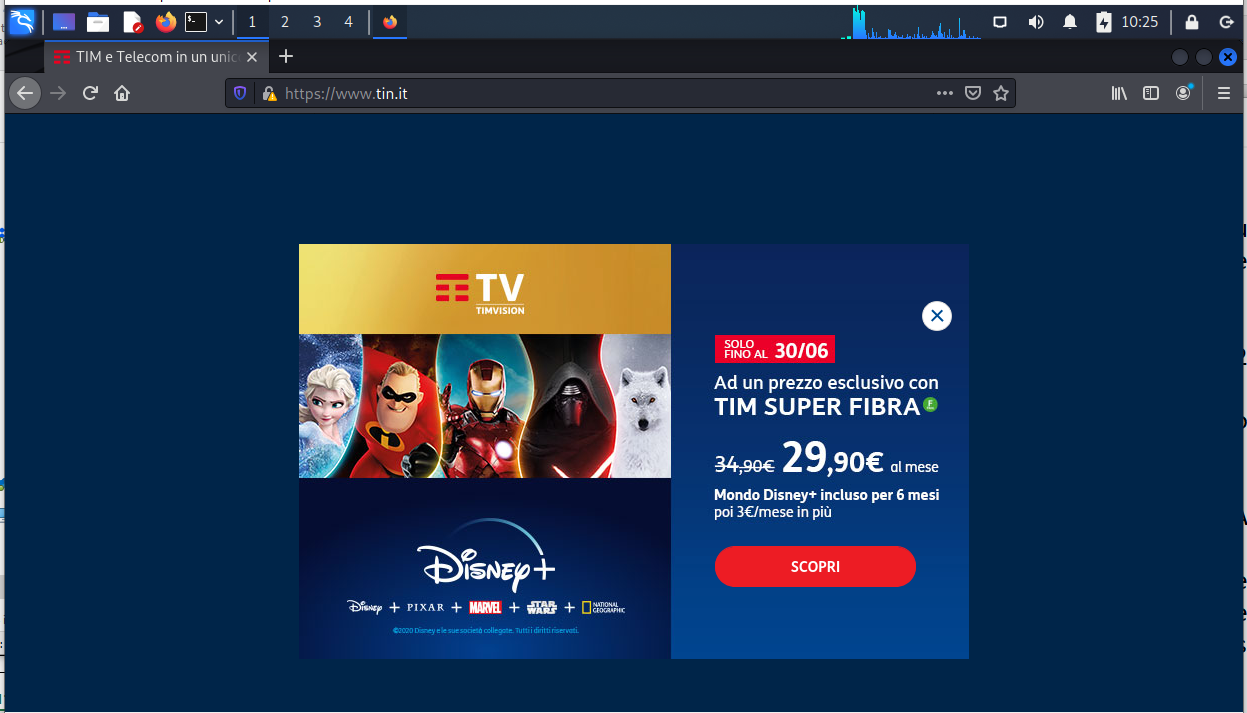
Accepting the risk and continuing brought me to another site that may have been set up to support future parts of this exploits, or it is a legitimate sign that has been compromised and/or hijacked.
No good can come from believing a TOTAL STRANGER WANTS TO GIVE YOU MONEY. Hey, people that KNOW YOU don’t want to give you money, why would a stranger?
Mailjet Renewal Phish
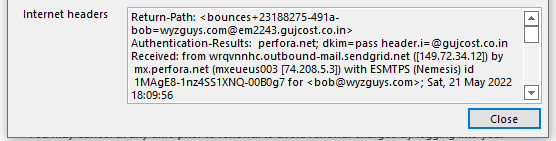
I do not subscribe to this mass email marketing service, so the renewal invoice I knew was bogus. But here’s what I found. First, the phishing email.
And the email headers. The source was from an account in the Denver, Colorado, United States
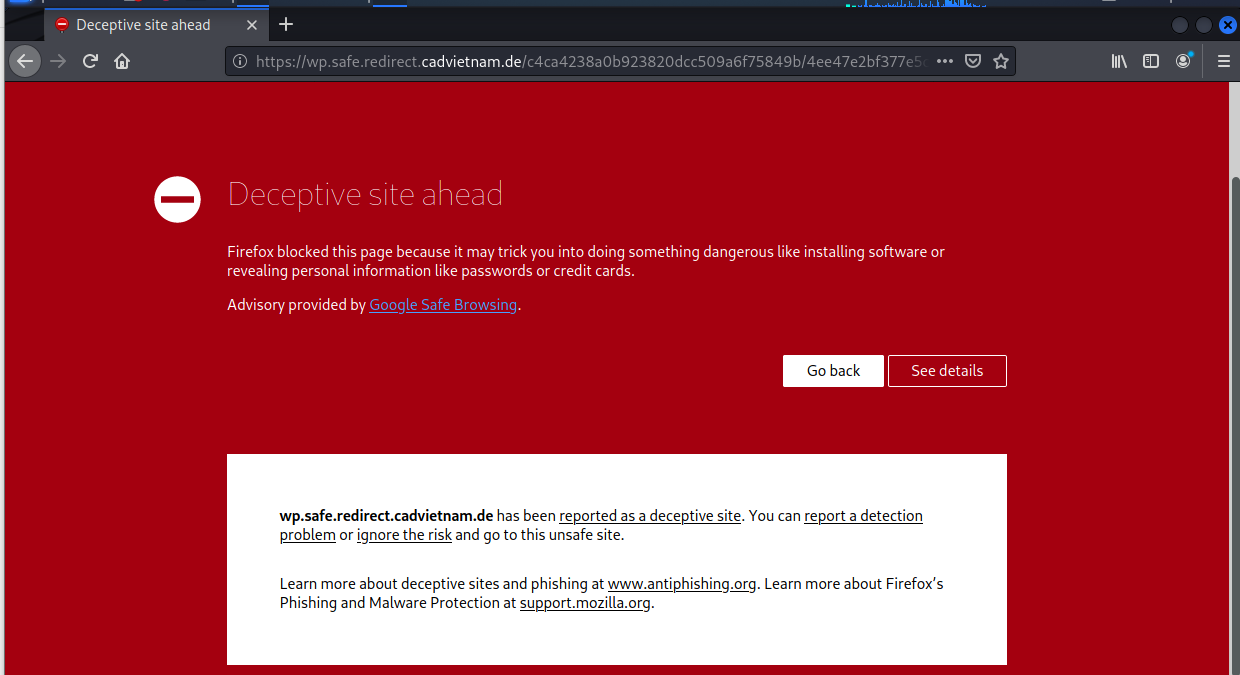
The link resolved to https://wp.safe.redirect.cadvietnam.de/c4ca4238a0b923820dcc509a6f75849b/4ee47e2bf377e5ce74e29b5ae56173c1/a000caafcc214ae6d2a230fe31f42be9/ffc5e01f578535fd6f95f889cb31939d This turned out to be a known deceptive site
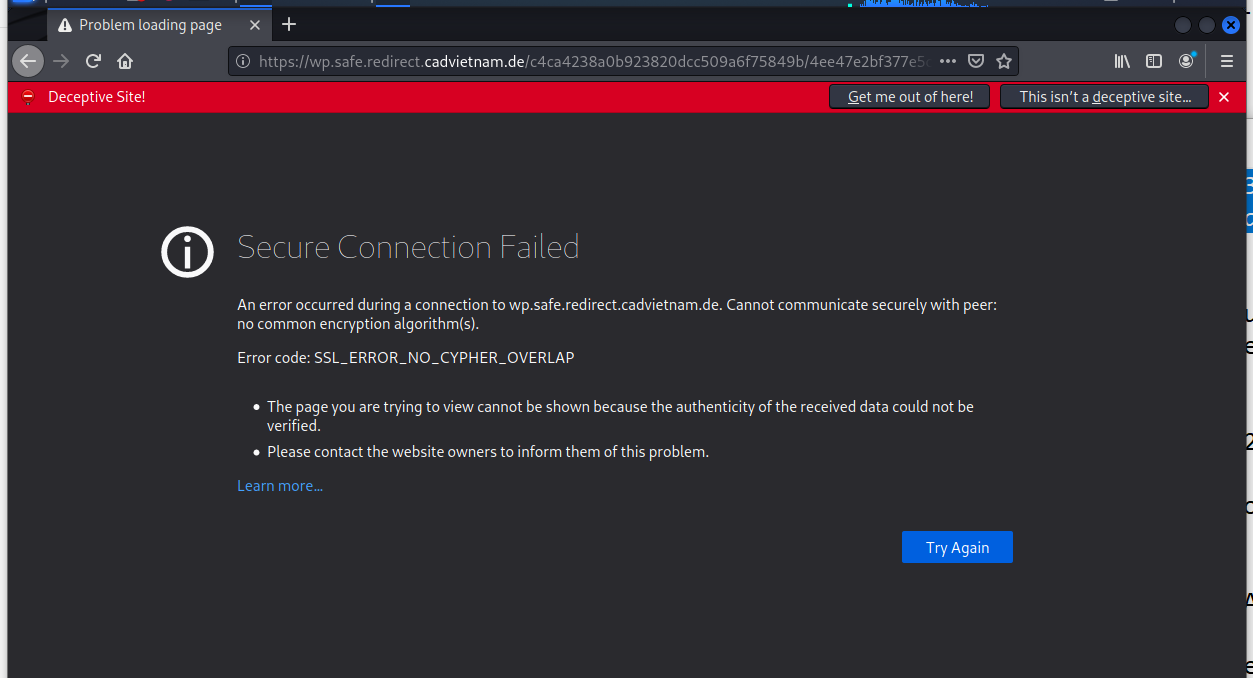
Forging on, I came to a dead end. This site appears to have been taken down already.
Now You Need to Watch Out for Spoofed Vanity URLs…
[Bob says: I have a couple of URLs that I use for phishing tests, and I have seen this sort of exploit alot.]
Researchers at Varonis warn that attackers are using customizable URLs (also known as vanity URLS) on SaaS services to craft more convincing phishing links. The attackers have used this technique for links created through Box, Zoom, and Google Docs and Forms.
“While vanity URLs provide a custom, easy-to-remember link, Varonis Threat Labs discovered that some applications do not validate the legitimacy of the vanity URL’s subdomain (e.g., yourcompany.example[.]com), but instead only validate the URI (e.g., /s/1234),” the researchers write.
“As a result, threat actors can use their own SaaS accounts to generate links to malicious content (files, folders, landing pages, forms, etc.) that appears to be hosted by your company’s sanctioned SaaS account. Achieving this is as easy as changing the subdomain in the link.
“These spoofed URLs can be used for phishing campaigns, social engineering attacks, reputation attacks, and malware distribution.” The researchers explain that this technique can fool security technologies as well as humans.
CONTINUED at the KnowBe4 blog with links and an INFOGRAPHIC about ROGUE URLS you can share with your users: https://blog.knowbe4.com/spoofed-vanity-urls
New phishing technique lures users with fake chatbot
Cybercriminals are finding new ways to trick users into providing their credit card data. A new technique makes use of a fake chatbot to build trust with victims. Learn more about this threat and how to protect yourself from it.
Phishing Campaign Impersonates Shipping Giant Maersk
Researchers at Vade Secure warn of a large phishing campaign that’s impersonating shipping giant Maersk to target thousands of users in New Zealand. Note, cyber criminals often beta-test their campaigns in “good-candidate” small countries before they roll them out globally, so treat this as a heads up.
“Several waves of phishing emails impersonating Maersk have targeted more than 18,000 recipients, 13,000 recipients, and 5,000 recipients respectively between January 2022 and May 2022, exploiting the global supply chain crisis affecting millions of businesses around the world,” the researchers write.
Blog post with links: https://blog.knowbe4.com/phishing-campaign-impersonates-maersk
ShareMAY





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com