 Phishing Email Alerts
Phishing Email Alerts
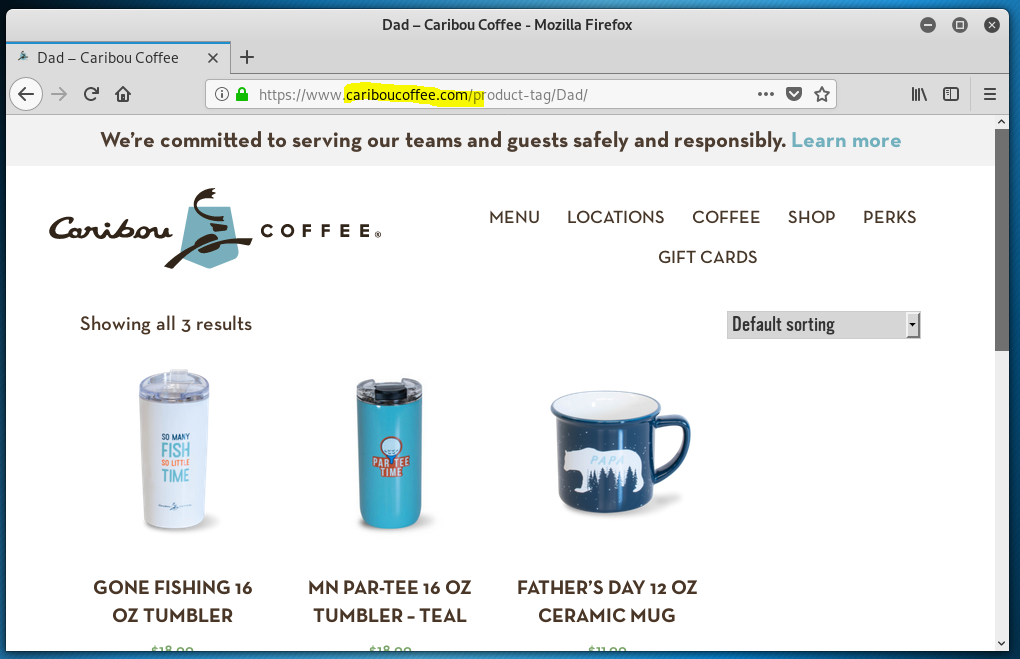
Catch of the Day: Real Caribou Email (How can you tell?) Looked like a phish but was really Caribou!
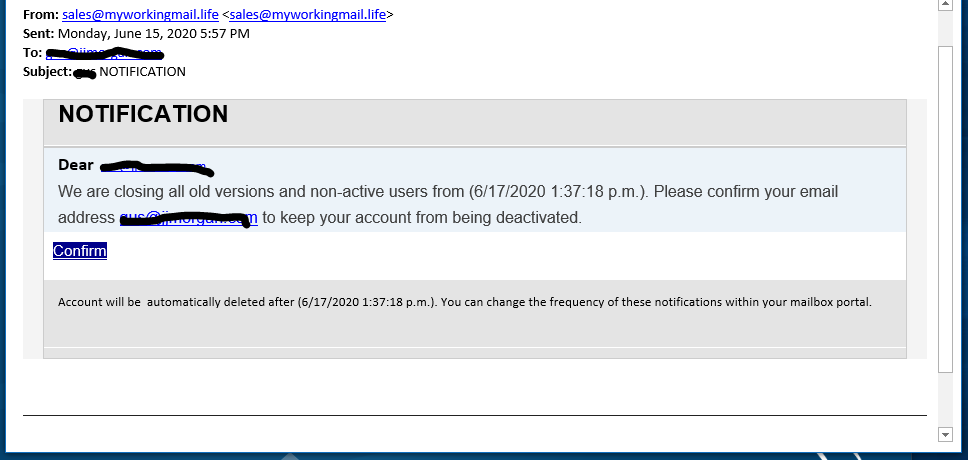
Chef’s Special: Surf and Turf – Inactive Account Phish with Trojan Horse
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox.
Fake or real, how can you tell?
I received a Father’s Day promotional email from Caribou. Having created a very successful phishing-awareness training email with a coffee theme myself, this was immediately suspicious to me. The links in the email all resolved to a long web address at https://click.pxsweb<dot>com. Virustotal gave it a clean bill of health, but I opened my trusty Linux virtual machine to test the link safely.
This came back as legitimate.
But a note to all my happy marketeers out there: I wish you would stop using phishy looking marketing domains for your email campaigns. When I get promotional mail from a company, I want the links to resolve to something on your own domain name. I know you have to run the responses through an analytics engine to measure results. Find a way that uses the clients email domain. I have to imagine that most of the email gateways and filters in the world filter out these marketing blasts anyway, which must limit the effectiveness of this type of marketing campaign.
Surf and Turf – Inactive Account Phish with Trojan Horse
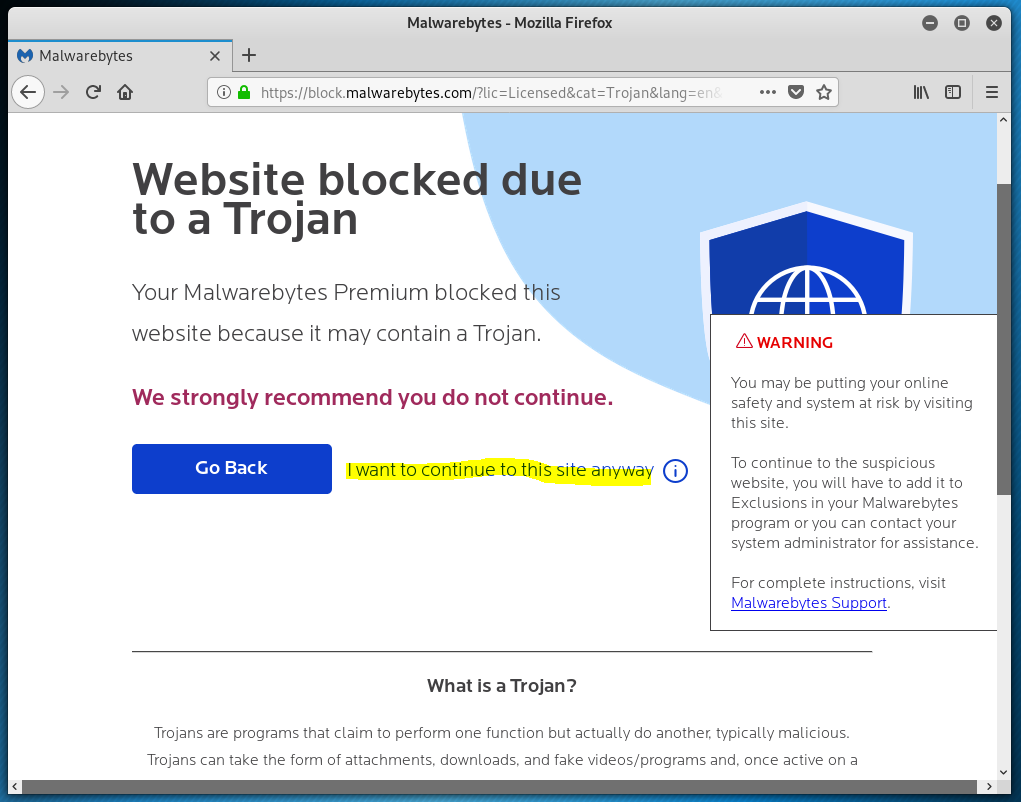
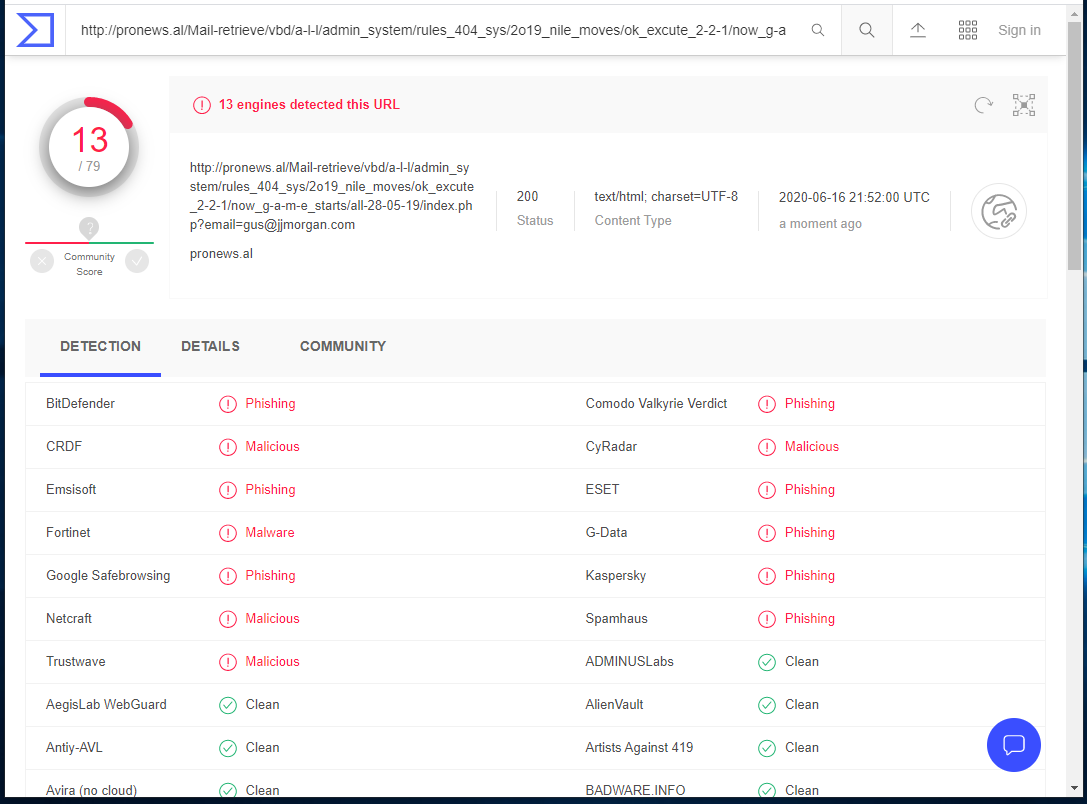
This one will download and install a Trojan horse from the landing page, according to Malwarebytes. It lit up a Christmas tree at Virustotal as well.
The phish:
Do not click on the link button on this phishing email. It resolves to http://pronews.al/Mail-retrieve/vbd/a-l-l/admin_system/rules_404_sys/2o19_nile_moves/ok_excute_2-2-1/now_g-a-m-e_starts/all-28-05-19/index.php?email=gus@jjmorgan.com which is a web page that downloads a Trojan horse.
My attempt to get to the landing page were blocked by Malwarebytes, which I don’t have loaded on my virtual machine, but it must have been blocked by Malwarebytes on the host machine. I even tried to click on the highlighted link. No dice. I decided Not to risk it this time.
And here is the Virustotal readout.
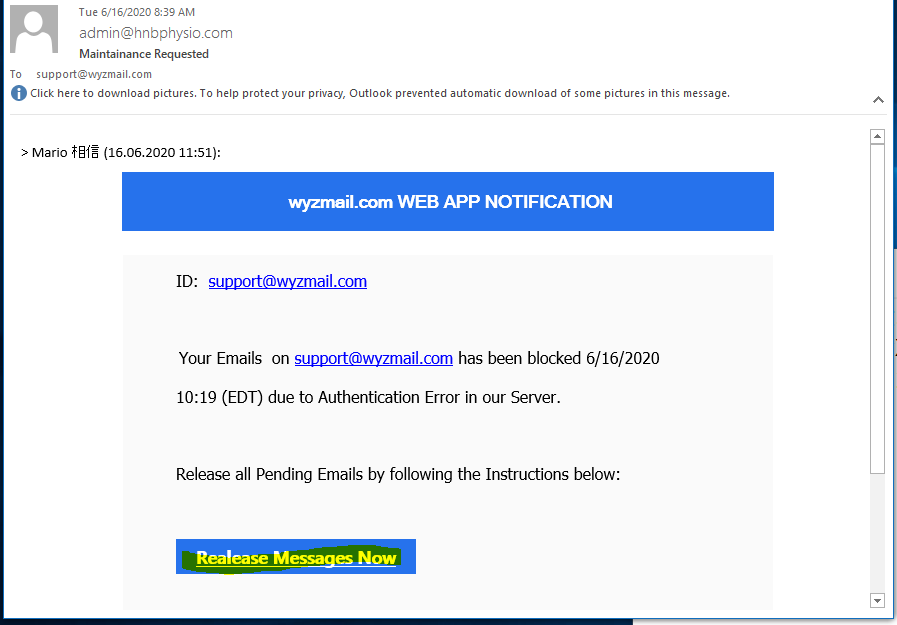
Maintenance Requested Phish
This looks a bit like a continuation of the IONOS phish I caught last week, but only the color blue connects it. The email domain hnbphysio.com of the sender has just been registered, which is suspicious.
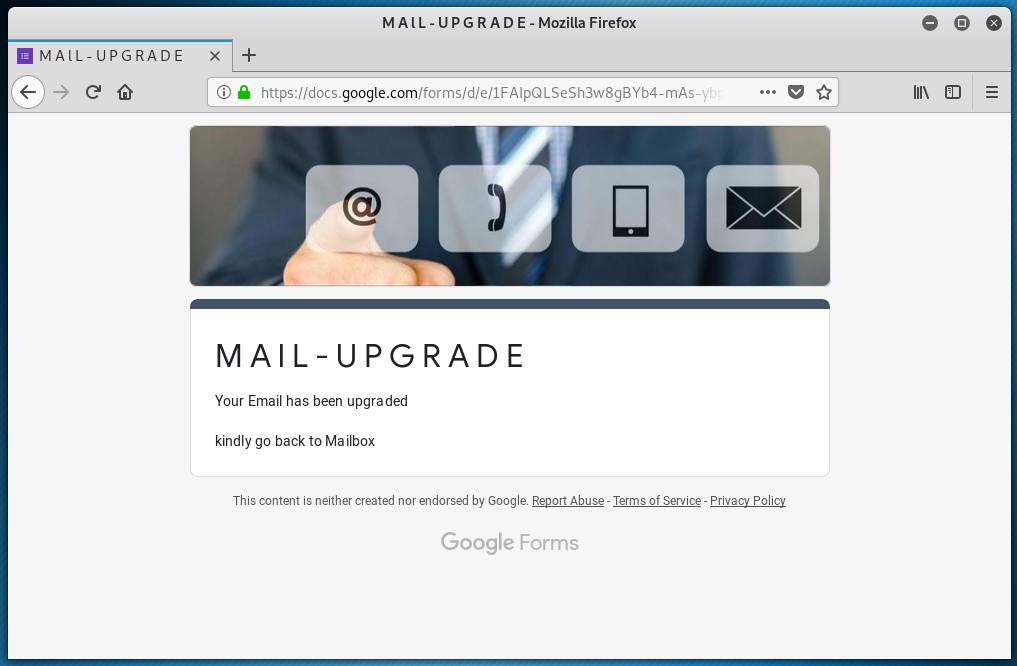
The button text is misspelled Realease Messages Now, and it resolves to a Google Docs address of https://docs.google.com/forms/d/e/1FAIpQLSeSh3w8gBYb4-mAs-ybpUEVY22HpFLvYTyX_x_8NdLqu9susA/viewform?usp=pp_url&entry.2005620554=support@wyzmail.com. This leads us to another credential stealing fake page. The passwords are not obscured, as is usual. I like to use fake passwords on these fake login pages. 
Note the warning “Never submit passwords through Google Forms.” If incorrect passwords do not cause an error, then this means the login page is a fake. The fake passwords worked fine. Here is the response page.
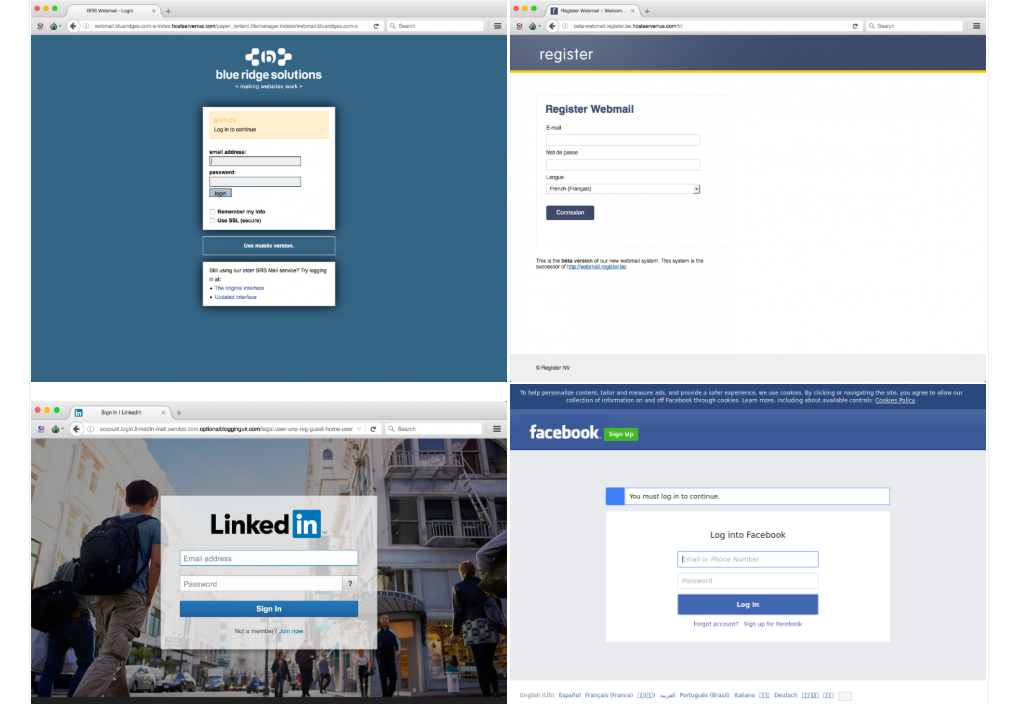
Another example of phishing emails to avoid.
Global Hack-for-Hire Service Caught Phishing Hundreds of Organizations
This is the story of a hacker-for-hire scheme that targeted hundreds of organizations and thousands of individuals across North America and five other continents. Clients hired the perpetrators to phish and hack their way across an amazing array of industry verticals like banking, education, energy, law, media, and government. And there’s something quite peculiar about these attacks: they almost always focused on organizations and people involved in controversial legal proceedings, business deals, or advocacy campaigns. The University of Toronto’s Citizen Lab uncovered the campaign, dubbed “Dark Basin,” and says it reveals intrusion services “at a scale not previously detected… Read more
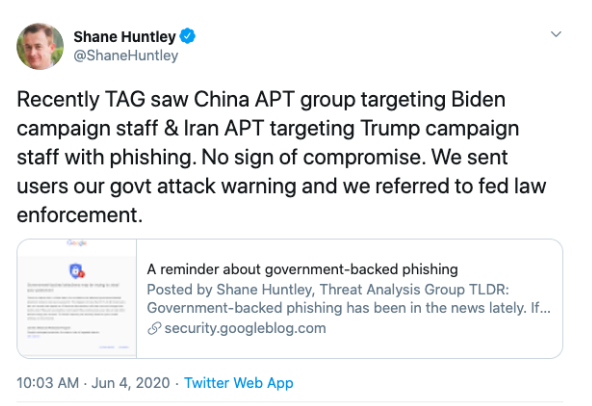
Chinese and Iranian Nation-State Actors Phishing Trump and Biden Campaigns
Chances are, the concept of “a foreign government interfering in an American election” sounds pretty commonplace to you. Not that this reality is a good thing. But over the last four years, it has started to feel like the norm. And according to Google’s Threat Analysis Group (TAG), it’s happening again in 2020. Google TAG recently uncovered some vital security intel regarding the 2020 U.S. presidential election… Read more
Share
JUN





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com