By Bob Weiss
May the Force be with you! It’s May the fourth, Star Wars Day.
I received an email from a CASP+ Student asking for some help with encryption. This is what I sent.
Encryption can be a mind bender. And then like magic, it is not.
If you are up for some outside reading (what! More reading? Sorry) there are a couple of books that helped me
The Code Book, by Simon Singh
Crypto by Stephen Levy
I read them both, but that’s me. Pick one, read it, and if you are still unsure, read the other one.
There are four reasons we might want to use encryption.
1) Confidentiality means we need to keep the message secret by sending it in a form that no one else can read
2) Integrity means that we are certain that they message was not changed in any way since it was created
3) Authentication or Identity Authentication means that we are absolutely positive who sent us the message
4) Non-Repudiation means that the sender cannot later deny having sent the message. If we have Authentication, we pretty much are guaranteed Non-Repudiation. I like to say that Authentication and Non-Repudiation are two sides of the same coin.
Encryption has four parts:
1) The plaintext or clear text – the original unencrypted document
2) The encryption algorithm – a mathematical formula that defines how the plaintext will be obscured or encrypted
3) The encryption key – a unique value usually expressed in hexadecimal (base 16) that is combined with the algorithm to make the output from modifying the plain text unique. The key makes it so we can both use the same encryption algorithm or method, but since we are using different keys, the output will be unique.
4) The ciphertext is the output. When we combine the plaintext, the algorithm and the key we get cipher text, which should be unreadable to anyone who does not have the key
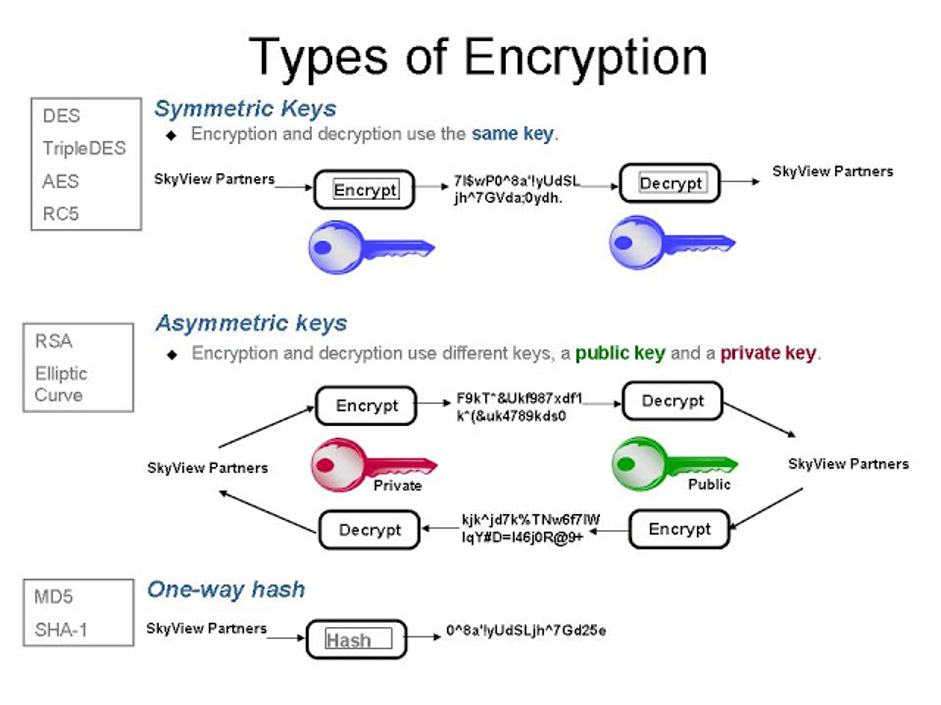
Types of Cryptographic Processes
Encryption Use Cases
Let’s pretend that you and I are wanting to engage in secret communications. The best way to do this is to use Symmetric Encryption. This is because the key length is short enough to make encrypting large documents or data sets quick and efficient. Symmetric keys are usually 128-bits, 256-bits to 512-bits. Symmetric Encryption requires that the sender and recipient each have a copy of the same encryption key. This is called shared key encryption. The same key can be used for encrypting and decrypting the message. The first problem we have is “the key distribution problem.” I have to get a copy of the key to you in a way that cannot be compromised or intercepted. We can meet in person, and I can give you a copy of my key. That may or may not be easy to do. But once the key is exchanged, we can be sure that our communications will be secret as long as neither one of us divulges the secret key. Remember the 4 purposes of encryption? Symmetric shared secret key encryption only provides Confidentiality.
Asymmetric Encryption was developed primarily to fix the key distribution problem, but it also provides some other benefits like Authentication and Non-Repudiation. Let’s look at how it is used in key exchange. To use Asymmetric Encryption you need to purchase a digital certificate from a Certificate Authority. The CA publishes your Public Key, and sends you your Private Key. This is known as the Public Key Infrastructure or PKI. There are types of Asymmetric Encryption that don’t use the PKI, notably Phil Zimmerman’s Pretty Good Privacy.
To complete an encrypted session using Asymmetric encryption you need to use both the public and the private key. They way the keys are used determines what the purpose is. These keys are totally different, but mathematically linked. They are also very large at 2048 or 4096 bits. This is a computational burden that limits the use of Asymmetric Encryption to very small bits of information. A common use for Asymmetric Encryption is to encrypt the small 128, 256, or 512 bit Symmetric Encryption key so it can be securely exchanged.
Going back to our original problem, you and I want to exchange messages secretly. Unfortunately, we cannot meet in person to exchange messages. But we both have registered with a Certificate Authority and have our own digital certificate. Each of us has a Private Key and a Public Key. The Public Key is NOT SECRET, but is published in the Public Key Infrastructure (PKI). The Private Key is a secret, and we must not share our Private Key with anyone ever.
So I want to communicate with you secretly, in a way the keeps the message a secret only you can read. I want to give you my Symmetric Secret Shared Key, but it is impractical for us to meet. I need to encrypt my Symmetric Key in a way that only you can decrypt. So I look up your Public Key, and encrypt the Symmetric Key using your Asymmetric Public Key. Anyone can use your public key to encrypt, but this can ONLY be decrypted by you, using your Private Key. This is how I send you the Shared Symmetric Key in a secure fashion.
This is the most common use of Asymmetric Encryption – to encrypt and decrypted a shared or session key. This is how every HTTPS/TLS website works.
So we still have a couple of things to cover, Authentication/Identification, Non-Repudiation, and Message Integrity. I will work on that post an article next week
ShareMAY







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com