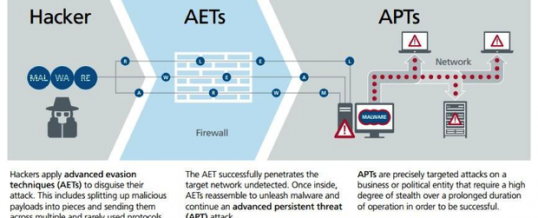
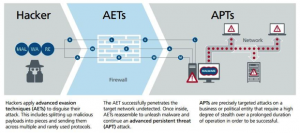
Here is another contribution from Aaron Miller and the people at Miller Auto Repair in Somerset Wisconsin.
Fighting competition
The shopkeeper was dismayed when a brand new business much like his own opened up next door and erected a huge sign which read BEST DEALS. He was horrified when another competitor opened up on his right, and announced its arrival with an even larger sign, reading LOWEST PRICES. The shopkeeper was panicked, until he got an idea. He put the biggest sign ...
Continue Reading →OCT


 I just learned that my credit- and debit-card information was part of a data breach. What should I do?
I just learned that my credit- and debit-card information was part of a data breach. What should I do?