 From the Department of Homeland Security website: “October is National Cyber Security Awareness Month which is an annual campaign to raise awareness about cybersecurity. We live in a world that is more connected than ever before. The Internet touches almost all aspects of everyone’s daily life, whether we realize it or not. National Cyber Security Awareness Month (NCSAM) is designed to engage and educate public and private sector partners through events and ...
From the Department of Homeland Security website: “October is National Cyber Security Awareness Month which is an annual campaign to raise awareness about cybersecurity. We live in a world that is more connected than ever before. The Internet touches almost all aspects of everyone’s daily life, whether we realize it or not. National Cyber Security Awareness Month (NCSAM) is designed to engage and educate public and private sector partners through events and ...
SEP

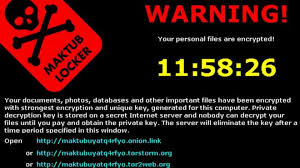 Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at ...
Encryption ransomware can be a devastating event if it happens to your or your company. The three solutions are basically pay the money, restore from backup, or accept your losses and move on. All are expensive, and some can be severe enough to drive a business out-of-business.Monday we gave you several ways to prevent, or at least prepare a response to a crypto-ransomware exploit. Today we are going to look at ... On Wednesday we discussed the many, many ways your smartphone is vulnerable to attack. Today we will look at solutions. Smart mobile devices need to be secured just as you would a laptop or desktop computer The small size and easy portability of smartphones and tablets make them easier to steal or lose. Some of our recommendations:
On Wednesday we discussed the many, many ways your smartphone is vulnerable to attack. Today we will look at solutions. Smart mobile devices need to be secured just as you would a laptop or desktop computer The small size and easy portability of smartphones and tablets make them easier to steal or lose. Some of our recommendations: Last Friday we dove down the WordPress Security bunny hole to chase the Aethera botnet and the other attack platform that WordFence reported. Today we are looking a their new
Last Friday we dove down the WordPress Security bunny hole to chase the Aethera botnet and the other attack platform that WordFence reported. Today we are looking a their new  If you are in high school (or junior high) or college, attracted to technology, and looking for a career with a future, then you should give serious consideration to the field of Cybersecurity. A recent press release from
If you are in high school (or junior high) or college, attracted to technology, and looking for a career with a future, then you should give serious consideration to the field of Cybersecurity. A recent press release from  This should really be called “anti-social” engineering. A good definition is “social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.”
This should really be called “anti-social” engineering. A good definition is “social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.”