 When I am investigating an email exploit, I will take a look at the email headers. Email headers in an email are a lot like the html code in a web site. This is information that the machines that create, send, and receive the email use for routing, and for providing other information about the message. As a human, we do not see the headers unless we specifically look for them, and viewing the header information varies depending on the email service or software you are using.
When I am investigating an email exploit, I will take a look at the email headers. Email headers in an email are a lot like the html code in a web site. This is information that the machines that create, send, and receive the email use for routing, and for providing other information about the message. As a human, we do not see the headers unless we specifically look for them, and viewing the header information varies depending on the email service or software you are using.
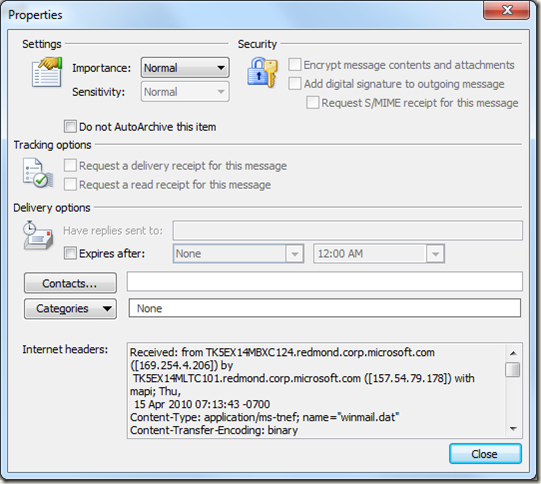
There were four excellent resources that I used for the article, and links to these websites follow. The third one has the best information on finding the mail headers in different mail systems. Here are the instructions for Microsoft Outlook.
A mail header contains a lot of information about how the email was sent and where it originated. The easiest way to analyse a header is to copy it from your mail client and paste it into something like Notepad or Word. That way you can split it up into discrete chunks and add your own notes and findings.
- Return Path: The email address which is used for return email or undeliverable bounces. The mail server will send a message to the specified email address if the message cannot be delivered. While this address may be spoofed, it is typically the email address of the sender
- Envelope: The email address of the recipient.
- Delivery-date: The data the message was delivered.
- Date: The date the message was sent. If there is a lengthy delay between the time when the message was sent and when it was delivered, there may be a problem along the route, or it may indicate some sort of spoofing or exploit.
- Routing information with the full delivery path. This information shows the IP address of the sender, and all the mail server names and the IP addresses of servers used to forward the email to the recipient, as well as the recipients IP address in some cases. This is the information that will be helpful in tracing the origin of an email.
- Message-ID: The ID number of the message. This number is created by the mail server sending the message. This number can be forged.
- X-Mailer: The mail client (mail program) used to send the message
- From: The message sender in the format: “Their Name” <email@address.tld>
- To: The message recipient in the format: “Your Name” <email@address.tld>
- Subject: The message subject line.
- Message Body: The content of the email message.
The last 4 items (From, To, Subject, Message) are typically the only information displayed on an email we see in our inbox.
There may be some additional information that is used to verify the sender or deal with spam.
- DomainKeys Identified Mail (DKIM) – “Domain Keys Identified Mail (DKIM) is a method for associating a domain name to an email, thereby allowing an organization to take responsibility for a message in a way that can be validated by a recipient.” … from Wikipedia.org. This means that the sending organization has digital xigned the message as evidence of its authenticity. This should prove that the message is not spam or a phishing attack.
- Sender Policy Framework (SPF) – The Sender Policy Framework SPF is a method deliveoped to prevent sender address forgery. This is a record that you usually can create with the company that hosts your domain name. This system verifies which mail server is authorized for sending emails for the domain name. See also: How to enable Sender Policy Framework (SPF) for domain/email.
- SpamAssassin – SpamAssassin is a anti-spam software, which is installed on many mail servers. A X-Spam-Score below 5 means the message is likely to not be spam. Over 5 the message may be spam. Greater than 15 means this is almost certainly spam. Depending on the rules set up in your mail server, spam might get deleted immediately or moved to the junk mail folder. Some systems add [SPAM] to the subject, so that these messages can be easily identified by a user. They could be moved to the junk folder in the mail client by using a rule.
The way to find the original sender is by looking for the X-Originating-IP header. This header is tells you the IP address of the computer that sent the email. If you cannot find the X-Originating-IP header, then you will have to check the Received headers to find the sender’s IP address. In the example above, the originating IP Address is 169.254.4.206.
Once you have the sender’s IP address, you can look it up at http://www.arin.net/. You will get results telling you which ISP (Internet Service Provider) or web hosting company the IP address belongs to. If you are tracking a spam or phishing email, you can send a complaint to the owner of the originating IP address. Include all the headers of the email when filing a complaint.
Investigating email is not as hard as it might first appear, once you understand what information is being displayed in the mail headers. For more detail, we encourage you to check out the links below.
More information:
- Understanding An Email Header
- How to Read and Analyze the Email Header Fields and Information about SPF, DKIM, SpamAssassin
- Trace an email with its full headers – a shorter article, but with instruction for finding the header in different mail systems.
- Delayed Emails?
Share
SEP




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com