 It has been a couple of weeks since the Google Docs hoax spread across the Internet like wildfire. What have we learned about this exploit?
It has been a couple of weeks since the Google Docs hoax spread across the Internet like wildfire. What have we learned about this exploit?
Originally this appeared to be a phishing campaign, but phishing emails are spoofed clever replicas. These emails were the genuine article, and were sent from Google mail servers, from the hijacked Google accounts of people you were likely to know. This made the exploit difficult to detect, and is one of the reasons it spread so easily. This is what makes this exploit especially interesting to cybersecurity investigators and reporters. Lets take a look at some of the important revelations.
- The code author of this exploit used the Google API (application program interface) to create a web application called “Google Docs.” Google permitted this use of their API (and branded product name) with out properly vetting the author or the app.
- The emails that were sent came from actual Google accounts, using Google email servers. The senders, in most cases, appeared to be someone known to the recipient.
- When the recipient accepted the invitation by clicking on the blue button, the bogus “Google Docs” application asked for permission to read, send, delete, and manage your email, and manage your contacts. This took advantage of a weakness in the OAuth open authentication service.
- If the recipient allowed those permissions, a new round of emails were send to the members of their contact list, thereby spreading the exploit to a new group of targets.
- This behavior makes this exploit a WORM, not a phishing campaign. A worm is a virus that spreads itself automatically. This is why the exploit spread so quickly to so many users, and why many people received more than one or two of these emails. We have not seen a worm with this level of impact in a very long while, which also makes this attack especially interesting.
- A person going by the name Eugene Popov took to Twitter to claim responsibility and offer an apology. Popov claimed the exploit was a project for a graduate degree final at Coventry University. The University disavowed Popov and said that no one by that name was currently attending or have ever attended the school.
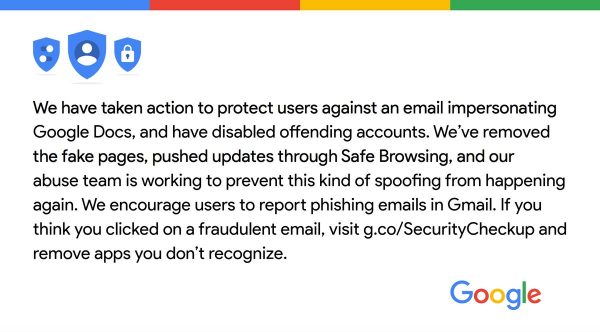
- Google took immediate action to take down the component parts of the exploit.
We heard from an associate that the end-game was to gain access to Google Wallet in the compromised accounts, but we have not been able to verify that story, and we have not seen it reported anywhere.
Nevertheless, this exploit does open up the affected Google accounts to misuse. In my particular case, this affects not only my Gmail and Docs accounts, but also my Android smart phone, Google Authenticator 2FA security app, Google Voice, Google+, Google Analytics for my websites, Google Adwords, and other Google service I use. I don’t use Wallet myself, but access to Google Wallet may be possible.
Here are some potential targets of this attack:
- Business Email Compromise or Email Accout Hijacking, where an email sent from what appears to be the CEO to CFO authorizing payment to a third party
- Crypto-ransomware or “malware free” ransom attacks.
- Other malware downloads and installations permitting remote access and control, or adding systems to a bot-net.
- Identify with other domains a company has been using to share documents.
- Exfiltration of documents, corporate espionage.
- A targeted inside information stock trading exploit relying on upcoming M&A or funding activities and information.
What can you do? If you clicked on the blue button in the email and granted the permission to the bogus app, you should:
- Log into your Google account
- Change your password
- Update the password on all affected devices
- Check and possibly change your recovery method and questions
- Check the list of applications that have been granted permission, and remove the fake Google Docs app, and any others you do not recognize.
More information:
- US-CERT Google Docs Alert
- Google Account Security Page
- Google Docs Twitter feed
- Naked Security May 4 article
- Naked Security May 5 article
- Barkly article
- Wikipedia article about OAuth
MAY




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com