Email account hijacking is a serious, growing problem. It has become the number one way that cyber-criminals make money. What makes it so insidious is the ease with which the hijacker can impersonate the owner of the email account.
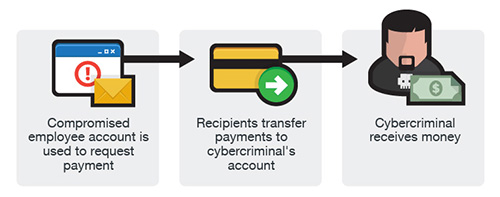 What this means to you is this – that email you got from your boss, a close friend, a coworker, a supplier or customer may be a forgery. What makes this difficult to detect is that the forged email is arriving from the legitimate account for the person being impersonated. These emails often contain a request for a wire transfer of funds, or the payment of an invoice, or other request for payment. You need to be extra vigilant for these sorts of attacks, or you may find yourself sending your hard-earned cash to fraudsters
What this means to you is this – that email you got from your boss, a close friend, a coworker, a supplier or customer may be a forgery. What makes this difficult to detect is that the forged email is arriving from the legitimate account for the person being impersonated. These emails often contain a request for a wire transfer of funds, or the payment of an invoice, or other request for payment. You need to be extra vigilant for these sorts of attacks, or you may find yourself sending your hard-earned cash to fraudsters
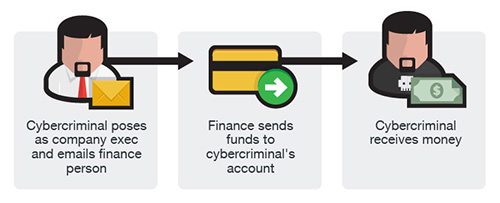 The Naked Security blog posted an article with an interesting example of how this scam works. A grape grower in New Zealand had her email account hijacked. The hijacker sent a payment request for $90,000 to a vintner who the hijacker knew (from reading her emails over time) owed her the money. The impersonated email claimed there was a problem with the regular bank. Would the vintner please send the payment to her “new” bank. The vintner noticed some differences in the email that were unusual for the grape grower, and phoned her to confirm the request.
The Naked Security blog posted an article with an interesting example of how this scam works. A grape grower in New Zealand had her email account hijacked. The hijacker sent a payment request for $90,000 to a vintner who the hijacker knew (from reading her emails over time) owed her the money. The impersonated email claimed there was a problem with the regular bank. Would the vintner please send the payment to her “new” bank. The vintner noticed some differences in the email that were unusual for the grape grower, and phoned her to confirm the request.
Here is a list of things to notice when you are reading emails from people you know. These may be an indication that the sender’s email account has been hijacked, and the email sent by an impostor.
- A request for money, whether in the form of wire transfer, invoice, or EFT payment. even if you know the charge is legitimate, you may want to call the sender to confirm the details. Replying by email won’t work – the hijacker is reading the inbox, remember! Pick up the phone or send a text message.
- A change in banks may be another clue that there is some chicanery afoot. This is another detail that ought to be confirmed by phone call
- A change in diction, language, or writing style should be a clue. We all have a style when we are communicating. Changes in style can indicate a fraud. Look to see if your sender is unusually stiff or formal, or suddenly a little more casual than usual. Are they using longer or different words, or longer or shorter sentences? Any unusual spelling errors? Strange grammatical choices? These are good ways to detect an impersonation.
- Changes in habits can be another red-flag. Does the sender usually CC a partner, colleague or assistant? Is that CC missing on your email? Do they usually sign their email a certain way, or use emojies?
- Changes in format may indicate a problem. Is there a change in font size or typeface? Is a logo or other form of trade dress missing from the message? This may be an email from an imposter.
The point here is that when you get an email from someone you know well, it should be fairly obvious that there are unusual differences between the fake email and the dozens of emails from the sender you have read before. Pay attention the the warning signs and the cyber-criminal will not be able to take advantage of you.
Share
OCT




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com