 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
War could spur state-sponsored cyberattacks, experts warn
Experts expect cyberattacks related to the ongoing Israeli-Hamas war to escalate as the fighting intensifies — hackers have already begun small-scale activities. “We should expect state-sponsored threat actors to intensify their information operations through various means,” SentinelLabs’ Tom Hegel said.
Full Story: CyberScoop (10/24)
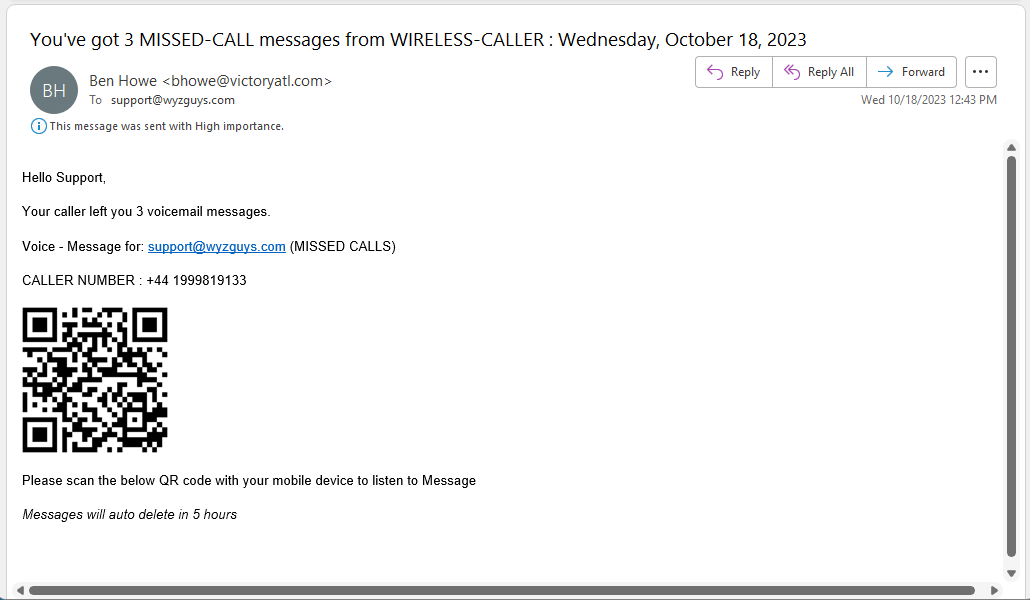
Explained: Quishing
Posted: by
Quishing is phishing using QR (Quick Response) codes. QR codes are basically two-dimensional barcodes that hold encoded data, and they can be used to work as a link. Point your phone’s camera at a QR code and it will ask you if you want to visit the link.
The use of QR codes in malicious campaigns is not new, and because they can provide contactless access to a product or service they grew in popularity during the Covid-19 pandemic. More...
Bob says: Here is an example that arrived in my inbox last week
How to Prevent Malware: 15 Best Practices for Malware Prevention
Here are 15 important controls and best practices for preventing malware.
Google Brings Generative AI to Search: Here’s What SGE Can Do
Google is rolling out its new Search Generative Experience, which allows users to generate images with AI. Find out what else it can do.
On Technologies for Automatic Facial Recognition
by Bruce Schneier
[2023.09.15] Interesting article on technologies that will automatically identify people:
With technology like that on Mr. Leyvand’s head, Facebook could prevent users from ever forgetting a colleague’s name, give a reminder at a cocktail party that an acquaintance had kids to ask about or help find someone at a crowded conference. However, six years later, the company now known as Meta has not released a version of that product and Mr. Leyvand has departed for Apple to work on its Vision Pro augmented reality glasses.
The technology is here. Maybe the implementation is still dorky, but that will change. The social implications will be enormous.
Share
OCT




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com