 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Proactive Prompting: Unleashing the Power of Google Bard Translations
We have a long way to making AI inclusive future, especially in how interconnected the world has become. It is all made possible due to how technology has made language translation and communication a more seamless experience.
Previously, we discussed how Bard has emerged as a game-changer in the field of translation and how you can use its feature to leverage your translation process.
So let’s take a closer look at how you can use prompts for Bard, discuss the concept of proactive prompting, and explore how Google Bard can be harnessed to enhance translation and localization processes. More…
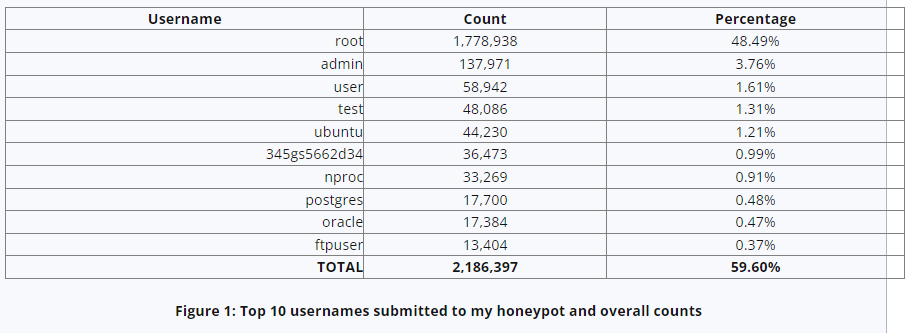
Common usernames submitted to honeypots
Based on reader feedback, I decided to take a look at usernames submitted to honeypots. The usernames that are seen on a daily basis look very familiar. They tend to come from default user accounts, such as “administrator” on Windows systems or “root” on Linux systems. The knowledge of a default user account can help in brute force attacks. If the username is already known, only the password needs to be guessed. This shouldn’t be too much of a problem to users as long as strong passwords are chosen or other authentication methods such as public key authentication is used. Setting up public key authentication is also referenced in our DShield setup instructions for a Raspberry Pi [2]. More…
Smart lightbulb and app vulnerability puts your Wi-Fi password at risk
Posted: by
New research highlights another potential danger from IoT devices, with a popular make of smart light bulbs placing your Wi-Fi network password at risk. Researchers from the University of London and Universita di Catania produced a paper explaining the dangers of common IoT products. In this case, how smart bulbs can be compromised to gain access to your home or office network. More…
Teenage members of Lapsus$ ransomware gang convicted
A wave of video game developer compromises has come to a conclusion in court, ending in several convictions for those responsible.
Where Did the QWERTY Keyboard Come From?
From laptops to iPhones, the first successful typewriter’s keyboard layout lives on.
There’s some dispute over how and why Sholes and Glidden arrived at the QWERTY layout. Some historians have argued that it solved a jamming problem by spacing out the most common letters in English; others, particularly more recent historians, hold that it was designed specifically to help telegraphists avoid common errors when transcribing Morse code. Regardless, after around 30 test models, Sholes and Glidden settled on QWERTY—and changed the world.
SEP




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com