 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Microsoft fixes a zero-day – and two curious bugs that take the Secure out of Secure Boot
Is Secure Boot without the Secure just “Boot”?
Attention gamers! Motherboard maker MSI admits to breach, issues “rogue firmware” alert
Stealing private keys is like getting hold of a medieval monarch’s personal signet ring… you get to put an official seal on treasonous material.
Windows CLFS Vulnerability Used for Ransomware Attacks
CVE-2023-28252 is an elevation of privilege vulnerability in the Windows Common Log File System (CLFS) Driver that could provide an attacker with SYSTEM privileges. Qualys director of vulnerability and threat research noted that the flaw, which has a CVSS score of 7.8, is already being used by cybercriminals to deploy Nokoyawa ransomware.
Dark web forum whac-a-mole
Law enforcement organizations across the globe notched a series of wins over the past few weeks against online forums for cybercriminals.
On March 23, the FBI announced it disrupted the online cybercriminal marketplace BreachForums, known for being a place where users could buy and sell stolen user information. They also arrested a 20-year-old suspected of being the site’s founder and main administrator.
Then last week we had “Operation Cookie Monster” in which several international agencies worked together to take down Genesis Market, a similar dark web forum, arresting dozens of suspected users and administrators.
These arrests and network operations are important in that they disrupted sites that were known for highly sensitive information and served as a place for some of the most prolific cyber criminals to make money. The U.S. Department of Justice estimated that Genesis Market was responsible for the sale of data on more than 1.5 million compromised computers around the world containing over 80 million account access credentials. And the U.K.’s National Crime Agency (NCA) said credentials were available for as little as 70 cents to hundreds of dollars depending on the stolen data available.
But the user base for these sites was also huge (after all, someone had to be buying those credentials). At the time of its takedown, BreachForums had 340,000 members, according to the FBI. And reporting on Operation Cookie Monster stated that Genesis Market had 59,000 registered users.
So while it’s great that these sites have been disrupted, I can’t help but assume that two more sites are going to pop up to service these cyber criminals. It’s impossible for any agency to arrest 340,000 people, so even if a handful of administrators are restricted from accessing the internet for a while, the other 339,000 people are going to be looking for a new home.
Some of the same agencies celebrated in March 2021 that they disrupted Emotet, one of the most infamous botnets ever. As anyone who follows security news will know, Emotet didn’t actually go anywhere and was recently rebooted as recently as last month, according to our research.
RaidForums, a forefather of BreachForums, was also disrupted in April 2022, along with the arrest of several administrators and accomplices.
All of this is not to discount the great strides made in the past few weeks in disrupting these marketplaces and taking them offline. But a lot of these headlines are sounding familiar to me after a few years, so it’s important to remember that we as a security community can’t take our foot off the gas and assume that because there were a few big wins that dark web forums are just going to go away forever.
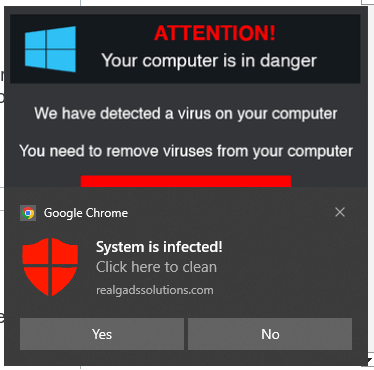
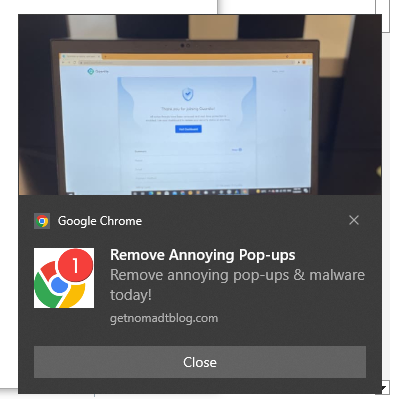
Fake Anti-Virus Pop-Ups
Haven’t seen this in YEARS, and somehow it took over my laptop for part of a day. I think I accidently clicked on an ad while reading an article from the Smithsonian. Thanks a lot guys, maybe you should do a better job vetting your advertisers!!!
Hit me at the end of the day around 9:30 pm. The next morning I tackled eradicating the little buggers. Malwarebytes and a set of Windows Updates (fixing some critical zero-days) and it APPEARS I may have exterminated them. We shall see. By the way, the link in the following image DOES NOT remove pop-ups. I must have seen a dozen variations of this scam before I finally got my system back under control.
Car Thieves Hacking the CAN Bus
By Bruce Schneier
Car thieves are injecting malicious software into a car’s network through wires in the headlights (or taillights) that fool the car into believing that the electronic key is nearby.
FBI Advising People to Avoid Public Charging Stations
By Bruce Schneier
The FBI is warning people against using public phone-charging stations, worrying that the combination power-data port can be used to inject malware onto the devices:
Avoid using free charging stations in airports, hotels, or shopping centers. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices that access these ports. Carry your own charger and USB cord and use an electrical outlet instead.
How much of a risk is this, really? I am unconvinced, although I do carry a USB condom for charging stations I find suspicious.
News article.
What is a USB Condom?
Better to have USB data protection and not need it, than need it and not be prepared.
Gaining an Advantage in Roulette
By Bruce Schneier
You can beat the game without a computer:
On a perfect [roulette] wheel, the ball would always fall in a random way. But over time, wheels develop flaws, which turn into patterns. A wheel that’s even marginally tilted could develop what Barnett called a ‘drop zone.’ When the tilt forces the ball to climb a slope, the ball decelerates and falls from the outer rim at the same spot on almost every spin. A similar thing can happen on equipment worn from repeated use, or if a croupier’s hand lotion has left residue, or for a dizzying number of other reasons. A drop zone is the Achilles’ heel of roulette. That morsel of predictability is enough for software to overcome the random skidding and bouncing that happens after the drop.”
Share
APR





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com