 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Finally Got Subnetting Down!
I finally figured it out. For those who are having a hard time trying to figure out the network, first/last host, broadcast, next subnet, and number of addresses in a subnet, I recommend www.subnetipv4.com. There are 7 fairly short videos with examples to break it down and there’s a subnetting practice program as well.
The best part I like about this training is that the subnetting chart is very easy to remember and writing it down doesn’t take a lot of time (which is good when doing your certification exam). I watched several other videos on subnetting and I’ve found subnetipv4.com’s to be the easiest for me. Hope this someone as much as it’s helped me!
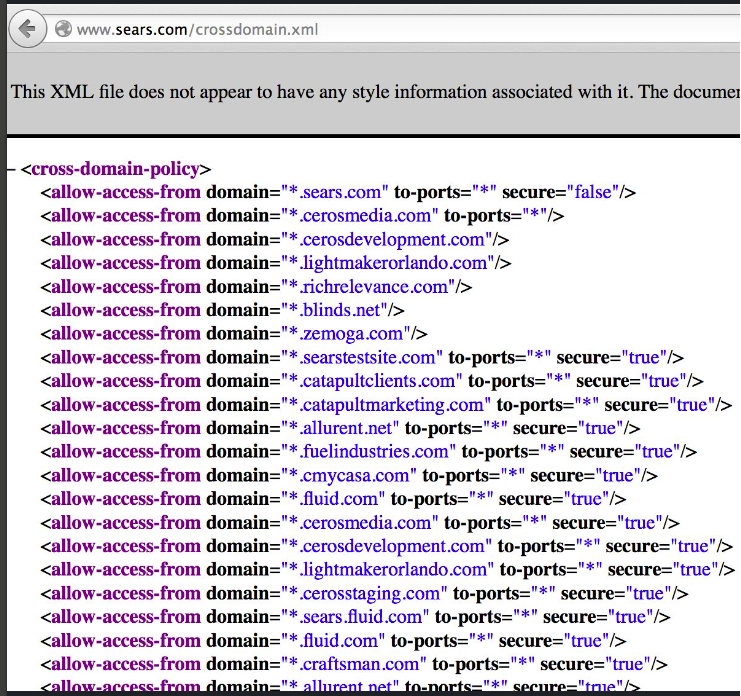
Hacking crossdomain.xml
Senior Hacker | OSCP | eWPTX | eCPPT | DEFCON Black Badge Holde
While hacking web apps, I’m sure most of you will check for common files like robots.txt, sitemap.xml, and web.config. But do you check for crossdomain.xml?
The file crossdomain.xml is used within Flash and Silverlight applications to determine what outside domains can view the content of server responses. Think of it like the Flash equivalent of #CORS (cross-origin resource sharing).
An overly permissive crossdomain.xml file can allow a threat actor to retrieve sensitive information from a website on behalf of an authenticated user. For example, let’s say we have the below policy:
<cross-domain-policy>
<site-control permitted-cross-domain-policies=”all”/>
<allow-access-from domain=”*” secure=”false”/>
<allow-http-request-headers-from domain=”*” headers=”*” secure=”false”/>
</cross-domain-policy>
The policy allows outside requests from *, meaning any outside domain.
A threat actor can generate a malicious .swf file on their (attacker) domain, manipulate a logged in user into accessing the file, and automatically generate a request to steal the contents of the server response. Let’s say the server response contains a CSRF token. We could then use that to initiate another request and takeover the account!
If you want to test this out, bWAPP has a Cross-Domain Policy File module that can be used for practice. In their module, they have you steal the contents of /bWAPP/secret[.]php on behalf of a logged-in user.
Genesis Market Takedown
An unprecedented law enforcement operation involving 17 countries has resulted in the takedown of Genesis Market, one of the most dangerous marketplaces selling stolen account credentials to hackers worldwide. As a result of an action day on 4 April, this illegal service was shut down and its infrastructure seized.
Google CEO says ChatGPT AI rival is coming
Google plans to add a natural language artificial intelligence chatbot to its search engine to keep up with rivals such as ChatGPT, Google and Alphabet. The tech giant may also move its DeepMind and Google Brain divisions closer together to increase their processing power.
ChatGPT cheat sheet: Complete guide for 2023
Get up and running with ChatGPT with this comprehensive cheat sheet. Learn everything from how to sign up for free to enterprise use cases, and start using ChatGPT quickly and effectively.
What To Do About AI
By Mark Maunder, CEO of Defiant (WordFence)
I’ve published a data-driven piece on how to adapt to the coming AI revolution if you’re a creator or a developer. It’s based on my own journey of adapting my capabilities and that of our team, along with many conversations I’ve had with technologists in several countries over the past months.
This thing is about to hit society like a freight train and this is my attempt to equip you with tools to deal with it, to adapt, and to thrive. It’s not a fluff piece. I’ve included my view on the pitfalls I’m seeing, what steps you should take, and several spectacular resources that can get you up to speed without a Ph.D. or strong math background. I hope you enjoy it. I’ll be in the comments in case there’s any discussion. You can find the full post here.
Share
APR





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com