![]() One of the tactics that I am seeing more often is the clever use of web address spoofing in the web sites and landing pages used in phishing emails. This sort of spoofing has been used successfully even against people who have been training to detect phishing emails, and to check link destinations (using the hover trick) and double check web addresses in the browser address bar.
One of the tactics that I am seeing more often is the clever use of web address spoofing in the web sites and landing pages used in phishing emails. This sort of spoofing has been used successfully even against people who have been training to detect phishing emails, and to check link destinations (using the hover trick) and double check web addresses in the browser address bar.
Here are some techniques that an attacker running a phishing campaign may use. Many of these tricks can be combined. These tactics can be used in the landing web page or the sender address in the phishing email.
Near misspellings. I can register a domain name that is close to the target domain I wish to spoof. Real examples I have seen in my professional like include paypali.com, and 1ond1.com. Or I could register part of a target domain, and combine it with a sub-domain to spoof a web address. For instance, I could register fice365.com and add two letters to get of.fice365.com. Only the extra period would give me away.
The sub-domain. Let’s say, hypothetically, I registered the domain infosecteam.com. I have plans to send a phishing attack to customers of Amazon.com, I can do that by creating a subdomain amazon.infosecteam.com. Emails will look like they came from the information security team at Amazon, and the fake website will be named similarly. This is another method that cyber-criminals use to trick their victims.
The hyphen or underscore. Another trick would be to register a longer version of the target domain by joining new parts with a hyphen or underscore. For example, I could register the domain name security-amazon.com or security_amazon.com. The use of the hyphen or underscore in a domain name is permitted, and allows an attacker to register a clever look-alike domain.
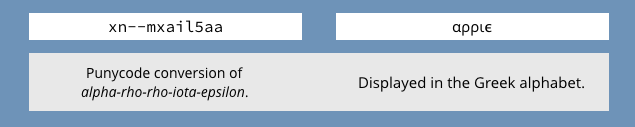
Punycode. We covered this issue in an earlier post. This tactic uses Unicode to create look alike web addresses but in a non-Roman alphabet such as Greek or Cyrillic. The way that criminal phishers would use punycode would be to register a domain name such as xn--mxail5aa. This resolves into the Greek alphabet and displays a series of Greek letters that look like “apple.”
In many browsers, these Greek letters will be re-displayed using ASCII letters, and will show the letters “apple.” ASCII is the Roman alphabet that is used by English.
The IP address. It is possible to use an IP address in a URL directly. So http://www.wyzguys.com and http://74.208.236.136 will work equally well. The way cyber-criminals will use an IP will look something like http://amazon.com.74.208.236.136. Both amazon and com are sub-domains to the IP address.
After the slash. I have seen a landing page used by a phishing scam on a hijacked website (name changed to protect the innocent) with the URL http://www.hijackeddomain.com/scripts/auth/us-bank/Login. This link resolved to a beautiful replica of the US Bank log in screen. The last two parts us-bank and Login are nested directories and pages in the hijacked site, and are there to set the hook.
It is a good practice not to take too much for granted when on the Internet. We have shown you how to read domain names for information and to protect yourself from scammers and spoofers. Vigilance is important, but we have shown how even if you are confirming and double-checking everything, it can still be easy to be tricked.
ShareAUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com