Bad news – your small business network is easy for an attacker to access, and for most of you there are two or more exploitable attacker vectors. A recent report from Positive Technologies analyzed the results of 22 penetration tests on companies from finance, transportation, retail, and even information technology. All of the companies were breached with little difficulty. The two easiest methods of unauthorized network access were not terribly surprising: Wi-Fi networks, and company employees.
Wi-Fi networks were easy to exploit for several reasons. Easy to guess dictionary passphrases were common. Most wireless networks do not utilize user isolation, so once the attacker accesses the wireless network, they can scan the network for other computers to attack. Breaching a Wi-Fi network does require the attacker to be in close proximity, close enough to connect to the network. But most wireless networks broadcast their signal beyond the wall of the building, providing a local attack vector to the company network.
Company employees were still the easiest way to gain unauthorized network access. Social engineering ploys in the form of phishing emails, phone calls, and even in-person impersonation exploits (“I’m from Comcast and I’m here to work on your Internet connection.”) often work surprising well, even after employee cyber awareness training. A quarter of employees will click on a link in a phishing email, with half of those employees (13%) giving away their user ID and password on the fake login form on the phishing landing page. 15% will open malicious file attachments in a phishing email. 12% are susceptible to phone calls and messaging exploits.
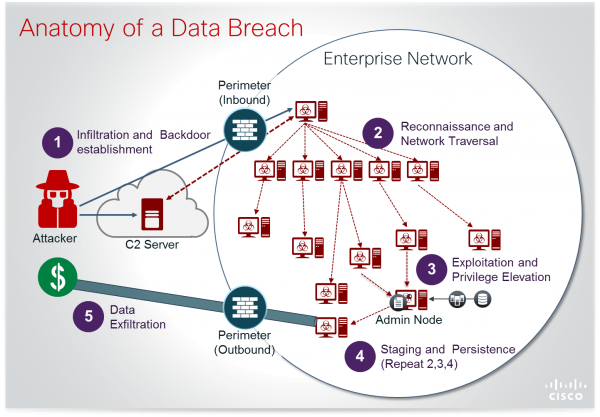
Once the attacker gains a foothold on a single computer system, they can use it as a platform to perform vulnerability scans and look for out of date operating systems, unpatched Windows computers and servers, and other exploitable vulnerabilities. They can use a software tool to extract and crack the encryption on the user IDs and passwords associated with each system they visit. Eventually they amass a list that includes a domain administrator account, and once that happens they have full access to every system on the network. At that point data exfiltration or some other money making enterprise is launched against the victim company, such as email account compromise, banking fraud, or even crypto-mining activities.
You can protect your network by taking advantage of the following security controls:
- Two-factor authentication is your best defense against stolen passwords. Without the 2FA token or app, access to the network is impossible.
- Limit administrative privileges to those employees who need it. Avoid giving all employees be administrative privileges.
- Enforce strong passwords that are at least 12 characters or longer. Forget about complexity and periodic password change requirements, they offer no protection from automated brute-force password cracking.
- Patch operating systems and software applications and make sure they are fully-supported current versions. Many servers can be breached by exploiting out of date versions of the operating system, old versions of SQL, an old CMS web program, and software or web applications.
- Employee cyber training including simulated phishing exercises has been shown to improve employee resistance to social engineering attacks and phishing exploits. On-going training is more effective than annual training events without follow-up activities.
Defending your computer network is a process that requires constant vigilance and tactical changes that keep pace with the threat environment. Using the recommendations above will help with that process.
More information:
ShareAUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com