This story is interesting because it shows just how powerful a Trojan Horse program can be. Trojans make up over two-thirds of all malware infections, and the reason is that Trojan Horse programs are small, easy to conceal in another program like a game, or easy to install using a drive-by download from a compromised web site. These programs allow the attacker to remotely access and control the computer at a later date, and install other malware applications such as spam mailing software, password cracking software, key loggers, and to do other things such as turning on your web cam, and watching and/or recording whatever happens in the field of view.
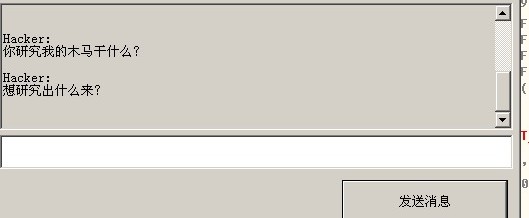
As reported in TechDirt Daily, AVG was in the process of reviewing the code of a Trojan Horse, when the author opened a chat window, which was a feature of his malware, and asked them what they were doing.
Hacker: What are you doing? Why are you researching my Trojan?
Hacker: What do you want from it?
As you can see, the malware author is Chinese, which is not a surprise to those of us working the computer security field. China is the world leader in malware writing at the moment. The Chinese (government?) are hacking everything they can and transferring as much proprietary, industrial, military, and scientific research information that they can lay their hands on.
The amusing and somewhat scary part of this exchange was that the malware writer shut down the AVG research lab’s computer at the end of the chat session.
ShareJUL




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com